Enterprises today operate in environments where their digital footprint grows faster than their ability to secure it. As cloud adoption, API integrations, remote work, and third-party partnerships expand, attack surface analysis is now critical for gaining full visibility, uncovering hidden risks, and closing security gaps before attackers strike.
According to recent research, 62% of organizations reported an increased attack surface over the past two years due to third-party connections, IoT, and public cloud usage. Even more concerning, nearly 70% faced at least one cyberattack originating from unknown or poorly managed internet-facing assets.
To tackle this, you first need to know what’s driving the attack surface explosion in 2025.
What Is Attack Surface Analysis and Why It’s Different?
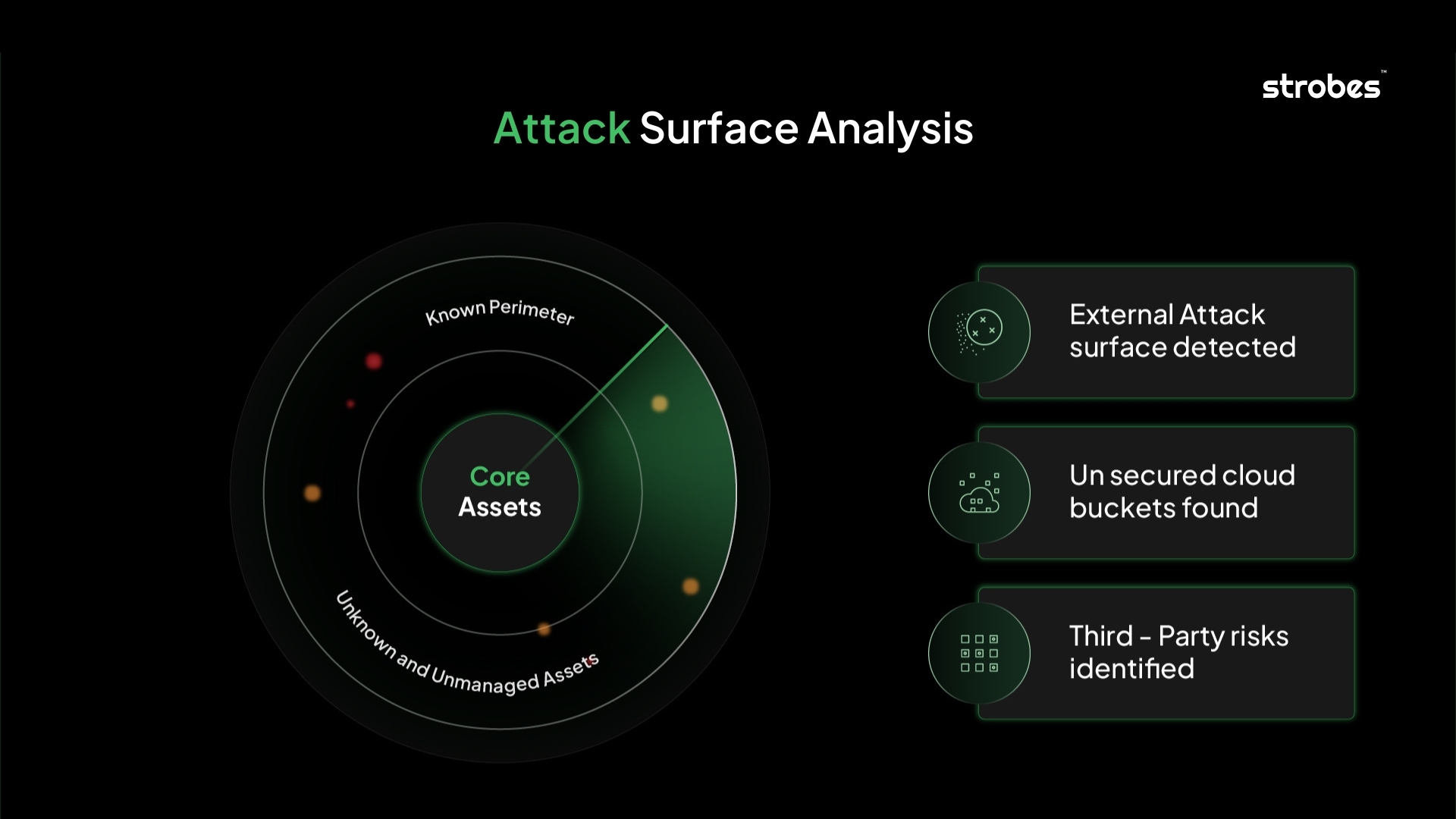
Attack surface analysis is the process of identifying, mapping, and monitoring every internet-facing asset that could become an entry point for attackers. It’s more than just listing assets, it’s about understanding their exposure, context, and the risks they introduce to your organization.
Traditional vulnerability assessments often focus on known systems within controlled environments. But today’s digital ecosystems are far from static. Shadow IT, cloud workloads, APIs, and third-party integrations create a constantly shifting attack surface. This demands a new approach.
Attack Surface Analysis vs. Traditional Vulnerability Scanning
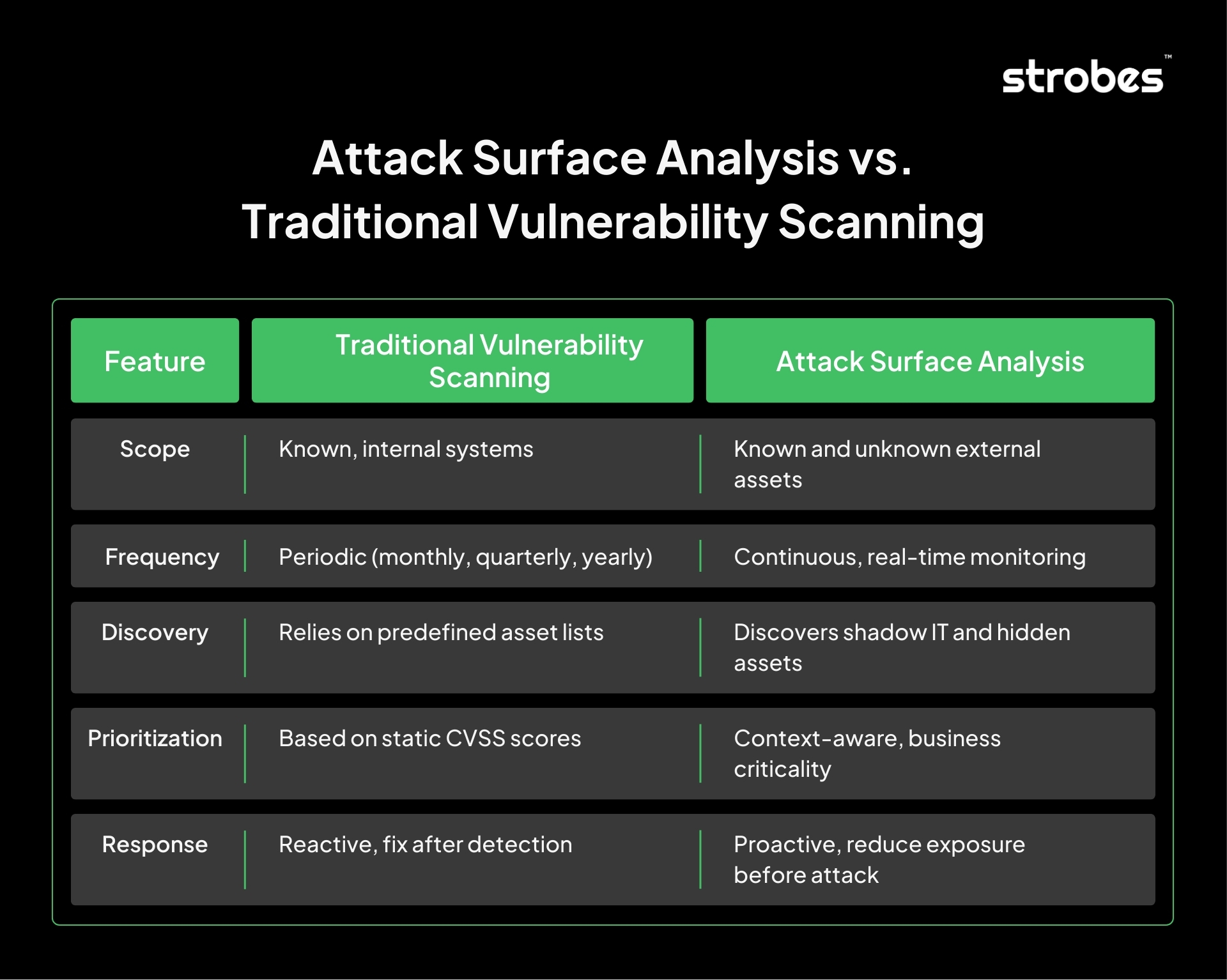
Unlike static scans, attack surface analysis:
- Discovers unknown assets – From forgotten subdomains to unprotected APIs and misconfigured cloud services.
- Provides real-time visibility – Continuously updates as new assets are added or configurations change.
- Prioritizes by context – Focuses on business-critical systems rather than treating all vulnerabilities equally.
This shift matters because attackers no longer rely on sophisticated exploits alone. They often succeed by targeting overlooked, unmanaged, or poorly secured assets that lie outside the traditional vulnerability management scope.
With attack surface analysis, security teams gain a live inventory of their external footprint and the insight needed to take action before attackers find a way in.
Why You Need a Quantitative Attack Surface Score?
This growing complexity is not just harder to manage. It is harder to measure. Without a clear view of how large and risky your attack surface really is, prioritizing defenses becomes guesswork. This is where a quantitative attack surface score changes the game.
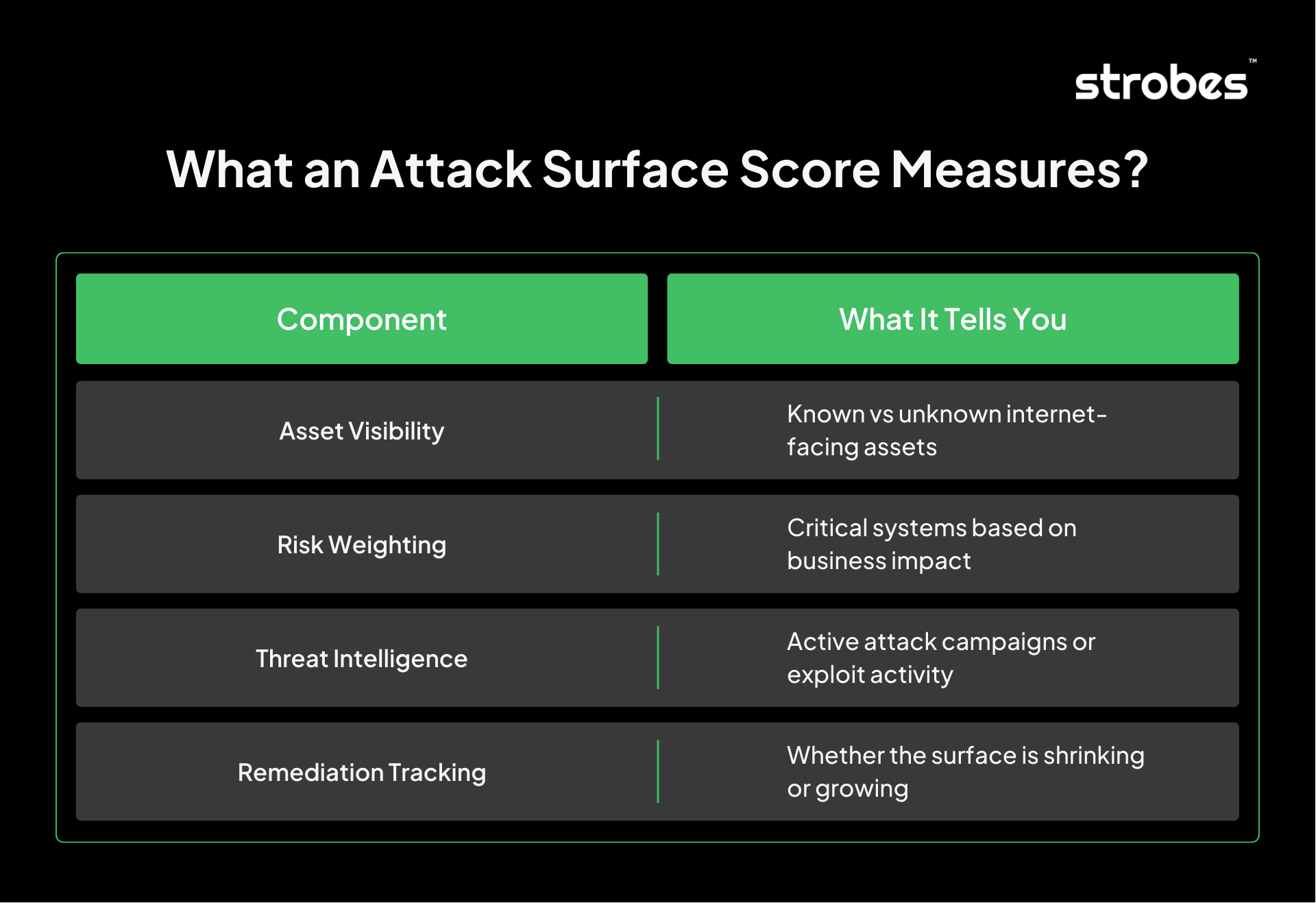
An attack surface score is a single metric that reflects the size and risk level of your external exposure. It considers the number of known and unknown assets, their criticality, and their vulnerability to active threats. This score allows teams to monitor security posture over time and compare environments, business units, or geographies.
It helps teams answer critical questions like:
- How exposed are we right now?
- Are our efforts to reduce risk making an impact?
- Which areas need the most attention based on business value and threat level?
What an Attack Surface Score Measures?
This approach shifts teams from reactive vulnerability lists to proactive, measurable outcomes. It also gives executives a clear, board-level view of cyber risk tied directly to business operations.
According to one study, only 29% of organizations have extensively automated attack surface reduction activities, while 54% report significant progress in building this capability. The same study found that organizations with strong ASA automation achieved nearly 3x better outcomes in managing external risk.
These gains were achieved through uncovering shadow IT, decommissioning unused cloud instances, and securing misconfigured APIs, all without adding headcount.
The key benefit of an attack surface score is focus. It gives teams clarity on where to act first, allowing them to prioritize high-risk areas and monitor progress over time.
The Right Approach to Attack Surface Analysis in 2025
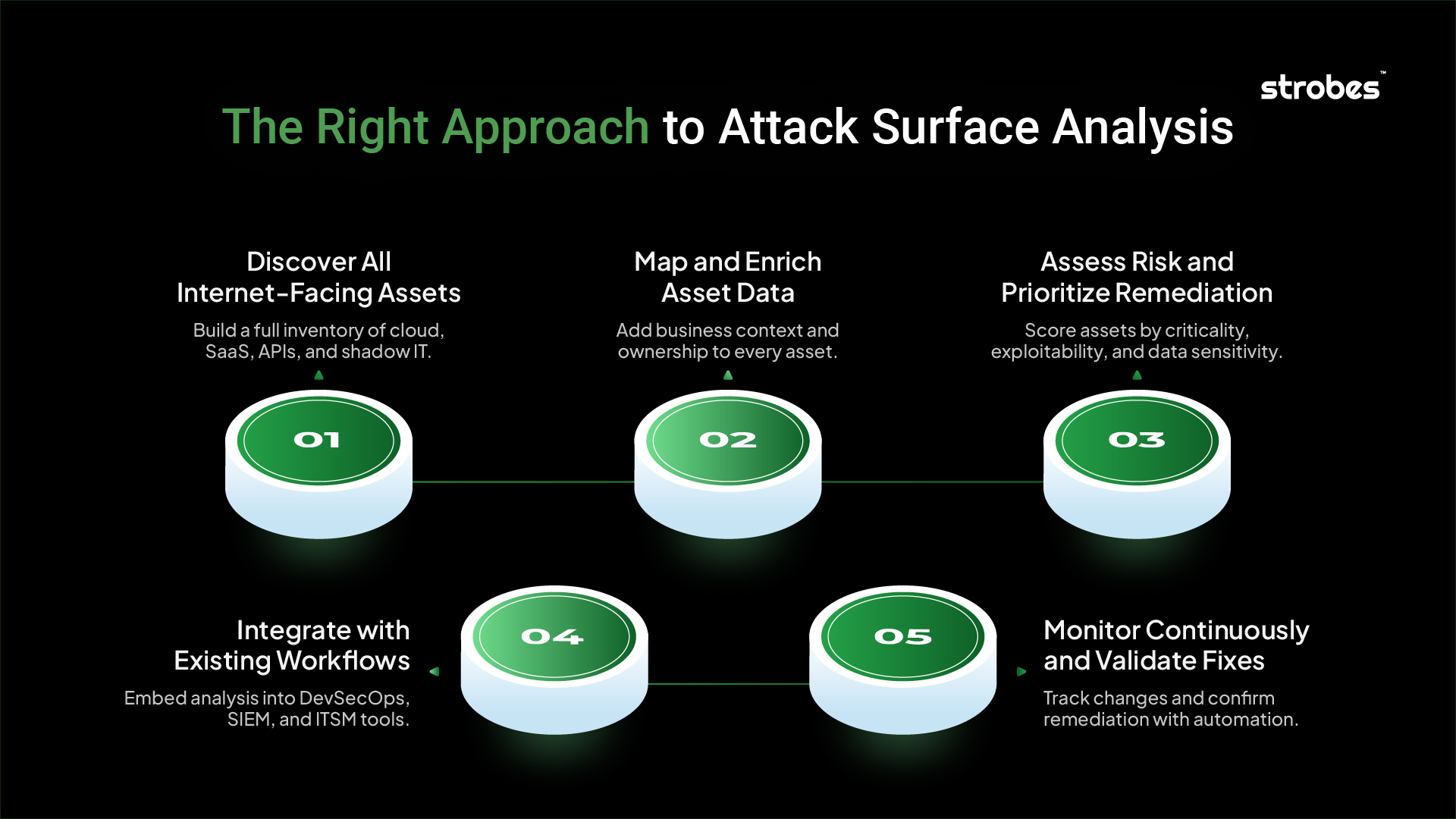
Building an effective attack surface analysis process starts with visibility. But visibility alone isn’t enough. To manage growing complexity, security teams need a repeatable workflow that discovers, prioritizes, and continuously monitors every external-facing asset.
Here’s how modern teams are approaching it:
1. Discover All Internet-Facing Assets
Start by creating a complete inventory of your digital footprint. This includes:
- Cloud workloads across AWS, Azure, and GCP
- SaaS platforms and third-party integrations
- APIs, domains, subdomains, and mobile endpoints
- Shadow IT and orphaned assets from past projects
Tools like external attack surface management (EASM) platforms, cloud security posture management (CSPM), and passive DNS can automate much of this discovery.
2. Map and Enrich Asset Data
Once assets are identified, add context to understand their importance and risk. This includes:
- Business criticality of each asset
- Owner or responsible team
- Historical vulnerability and exposure data
- Connections to other systems or vendors
A well-mapped inventory creates the foundation for prioritizing risks.
3. Assess Risk and Prioritize Remediation
Not every exposed asset carries the same level of risk. Use a scoring framework that factors in:
- Asset criticality to business operations
- Exploitability based on threat intelligence
- Sensitivity of data handled by the asset
- Exposure duration and external accessibility
This helps teams focus remediation efforts on the areas most likely to be targeted.
4. Integrate with Existing Workflows
Effective attack surface analysis isn’t a standalone task. It must integrate with:
- DevSecOps pipelines for pre-deployment checks
- SIEM and SOAR tools for continuous monitoring
- ITSM platforms (like Jira or ServiceNow) for ticketing and tracking
This ensures findings are addressed as part of existing security and IT operations.
5. Monitor Continuously and Validate Fixes
Attack surfaces change daily with new deployments, vendor updates, and configuration changes. Set up continuous monitoring to detect new assets and exposures as they appear. Automated validation tools can retest fixed issues to confirm remediation.
This structured approach transforms attack surface analysis from a one-time project into an ongoing process. It equips security teams with the visibility and control they need to adapt to fast-changing environments and stay ahead of attackers.
Want to understand the bigger picture?
Read Attack Surface Management: What Is It and Why Do You Need It? to see how it ties into reducing risks.
The Role of AI in Modern Attack Surface Analysis
Continuous monitoring alone cannot keep pace with the speed at which modern attack surfaces expand. As environments become more cloud-native and API-driven, attack surface analysis needs intelligence that adapts in real time.
This is where AI and machine learning transform the process. They automate discovery, enrich asset context, and deliver actionable insights faster than manual workflows ever could. Security teams gain the ability to focus on exposures with the highest potential impact. Here’s how AI enhances attack surface analysis:
Faster Asset Discovery
AI-powered tools analyze DNS records, SSL certificates, cloud APIs, and network traffic patterns to identify unknown assets in real time. This includes shadow IT, orphaned subdomains, and rogue APIs often missed by traditional scanners.
Dynamic Risk Scoring
Machine learning models assess asset risk using factors like business criticality, exposure level, attack data, and exploit availability. Teams can prioritize critical issues without drowning in alerts.
Also Reads: CVSS Score: A Comprehensive Guide to Vulnerability Scoring
Threat Correlation and Predictive Analysis
AI links threat intelligence feeds with your asset inventory to surface emerging risks. Predictive analytics flag assets likely to be targeted based on attacker behavior.
Noise Reduction
AI reduces false positives by learning from validation data. It filters out low-risk findings, allowing teams to focus on high-impact vulnerabilities.
AI is no longer a supporting feature. It is becoming a core capability for attack surface analysis in dynamic, large-scale environments.
Key Metrics for Monitoring Your Attack Surface
Attack surface analysis is only as effective as the metrics that drive it. In dynamic environments where cloud workloads, APIs, and third-party integrations evolve daily, traditional asset counts and vulnerability totals no longer provide enough insight. Security teams need advanced indicators that measure exposure in real time and evaluate the effectiveness of their remediation strategies. Here are the top metrics you must track –
- External Asset Discovery Rate
Measures how quickly new internet-facing assets are identified after deployment. In highly automated environments, this reflects the integration of ASA tools with CI/CD pipelines and cloud APIs for near-instant visibility. - Shadow IT Coverage Ratio
Calculates the percentage of previously unmanaged or unknown assets now under continuous monitoring. This is critical in multi-cloud and SaaS-driven organizations where shadow IT introduces hidden attack vectors. - Mean Time to Detect Exposures (MTTD-E)
Tracks the average time between an asset’s deployment and the detection of associated exposures like misconfigurations, open ports, or unprotected APIs. Lower MTTD-E indicates better alignment between ASA and cloud-native operations. - Mean Time to Remediate (MTTR)
Reflects how efficiently security and IT teams resolve critical exposures. This metric highlights the maturity of workflows and integration between ASA platforms and ITSM tools such as ServiceNow or Jira. - Exposure Criticality Index (ECI)
A weighted metric combining business criticality, data sensitivity, and live threat intelligence. ECI helps prioritize remediation efforts where they will have the greatest impact on reducing organizational risk. - Monitoring Coverage Percentage
Represents the proportion of the external attack surface under active, automated monitoring. Higher coverage means fewer blind spots and reduced time for attackers to exploit new exposures.
Avoid these common gaps. Request a Strobes Demo to see how your team can reduce exposures before attackers exploit them.
Why These Metrics Matter in Attack Surface Analysis?
Modern attack surfaces are highly fluid. Every code deployment, vendor onboarding, or cloud provisioning action creates potential exposures. These advanced metrics help security teams understand not just the size of their attack surface, but the urgency and business impact of securing it.
By combining these indicators with an attack surface score, organizations can:
- Prioritize remediation based on context and business risk.
- Measure progress toward reducing external exposure over time.
- Communicate actionable insights to technical and executive stakeholders.
- Validate investments in automation and AI-enhanced ASA solutions.
This level of visibility transforms attack surface analysis from a static exercise into a continuous, outcome-driven practice.
Why Attack Surface Analysis Fails and How to Fix It?
Even with robust metrics in place, many organizations struggle to operationalize attack surface analysis effectively. In dynamic environments, these challenges often lead to blind spots attackers are quick to exploit.
Static Inventories in Dynamic Environments
Treating attack surface analysis as a periodic activity leaves teams with outdated asset data. Cloud deployments, API integrations, and SaaS adoption create new exposures daily. Without real-time discovery and updates, critical assets often remain untracked.
Continuous discovery integrated with CI/CD pipelines and cloud provider APIs keeps inventories current and aligned with frequent changes in modern infrastructures.
Gaps Left by Traditional Vulnerability Scanning
Legacy scanners miss unmanaged assets such as shadow IT, orphaned subdomains, and misconfigured SaaS tools. These blind spots often become entry points for attackers.
Modern attack surface analysis platforms extend beyond scanning by using external asset discovery, passive DNS analysis, and certificate transparency logs to map the full external footprint.
Ignoring Third-Party and Supply Chain Risks
Vendor systems and partner APIs extend organizational attack surfaces. Excluding these assets leaves organizations exposed to supply chain attacks that exploit weaker external links.
Incorporating vendor-owned infrastructure into attack surface analysis programs, along with continuous monitoring of third-party APIs and portals, helps reduce this exposure.
Prioritization Without Context
Static severity ratings often lead teams to focus on low-impact issues while leaving critical exposures unresolved. Business context, data sensitivity, and live threat intelligence must guide remediation priorities.
Platforms offering context-aware risk scoring, similar to what Strobes provides, enable teams to focus on exposures with the highest operational and business impact.
Disconnected Security Workflows
Attack surface analysis findings that stay siloed delay response and create duplication across teams. Without integration into ITSM systems, SIEM/SOAR tools, and DevSecOps pipelines, valuable insights often fail to trigger timely remediation.
Seamlessly integrating attack surface analysis outputs into security operations workflows ensures findings move quickly from discovery to resolution.
Manual Workflows in Large-Scale Environments
Manual asset tracking and risk validation cannot scale in environments with frequent deployments and high alert volumes. Teams risk operational fatigue and missed exposures.
AI-powered attack surface analysis tools automate discovery, analysis, and validation processes, maintaining visibility and control even in dynamic multi-cloud environments.
By addressing these operational gaps, organizations can turn attack surface analysis into a dynamic, adaptive process.
Making Attack Surface Analysis Work for Your Organization
Attack surface analysis is not a one-time assessment. In 2025, with cloud adoption, API growth, and third-party integrations increasing external exposure, organizations need a strategy that adapts to constant change.
The focus must shift from static inventories and periodic scans to continuous discovery, context-driven prioritization, and integration with existing security workflows. This approach reduces blind spots, aligns remediation efforts with business impact, and strengthens overall security posture.
Platforms such as Strobes support this shift by providing automation, real-time insights, and seamless integrations. These capabilities help security teams manage complex and fast-changing environments more effectively.
Book a free demo to map unknown assets, prioritize critical exposures and reduce external risks with precision.
Related Reads:
- Attack Surface Management: What is it? Why do you need it?
- Integrating Attack Surface Management and Penetration Testing as a Service
- Understanding External Attack Surface Management: Strobes EASM
- Cloud Attack Surface Management(CASM): What is it? How does Strobes CASM help you with cloud security?
- How to Tame Your Multi-Cloud Attack Surface with Pentesting
- Solution: Attack Surface Management







