Risk Based Vulnerability Management
Strobes RBVM simplifies vulnerability management with its all-in-one platform, streamlining the process of identifying, prioritizing, and mitigating vulnerability risks across various attack vectors. Through seamless automation, integration, and comprehensive reporting, organizations can proactively enhance their cybersecurity posture.
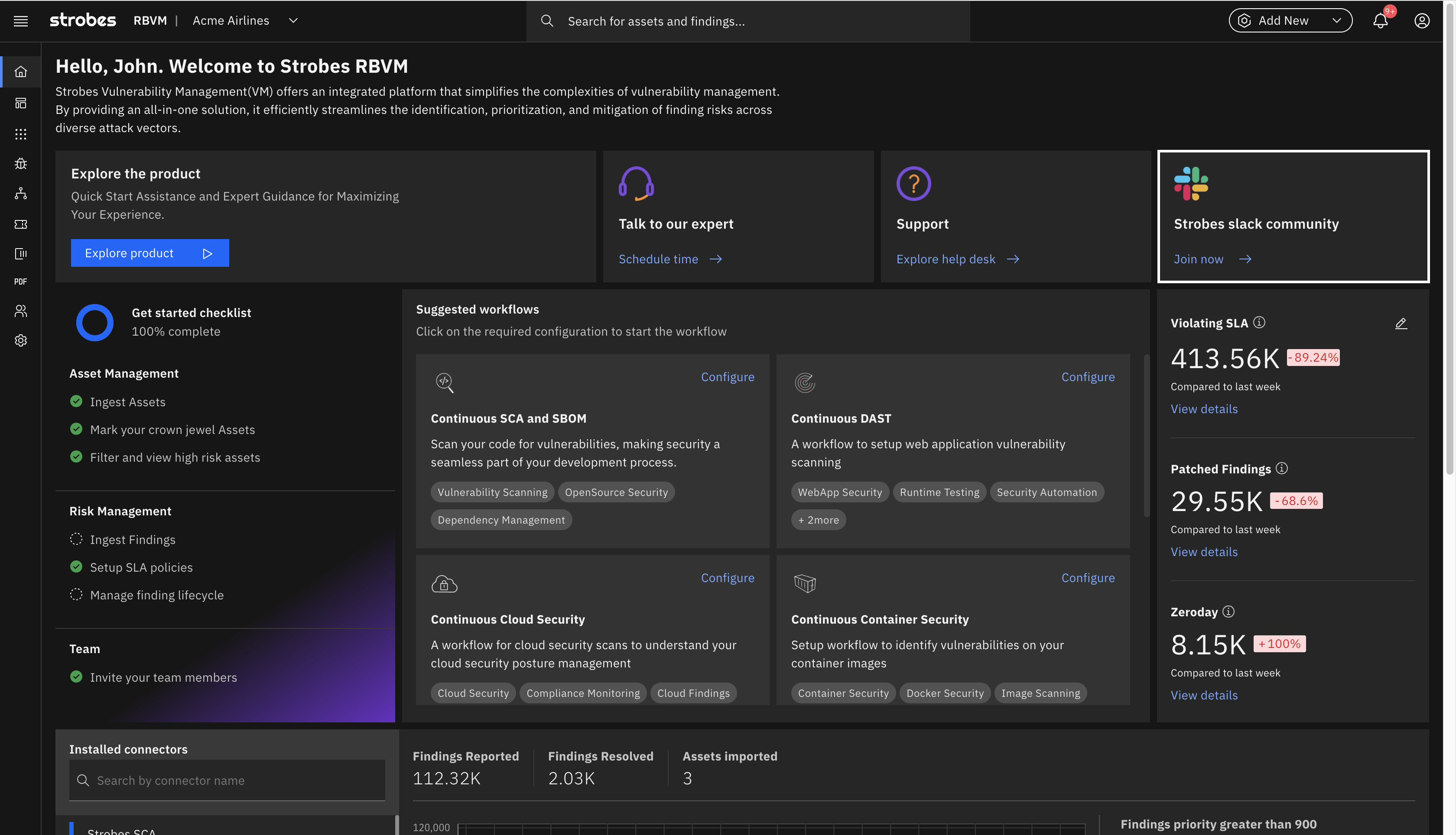




Aggregate & Prioritize Vulnerabilities
Integrate multiple security scanners, threat intel, & IT ops tools to aggregate thousands of vulnerabilities but only end up patching the most important ones by using our advanced prioritization techniques.
Vulnerability Aggregation
Going beyond a vulnerability scanner
Strobes Risk Based Vulnerability Management software goes beyond the capabilities of a standalone vulnerability scanner by aggregating from multiple sources, correlating with threat intel data and prioritising issues automatically.
End-to-End Lifecycle Management
VM software encompasses the complete vulnerability management process, from initial discovery to remediation, tracking, and reporting.
Threat Intelligence
RBVM software offers risk-scoring mechanisms that consider various factors beyond just the severity of vulnerabilities, such as exploitability and potential impact.
Workflow Automation
RBVM software automates many aspects of vulnerability management: scanning, ticketing, notification, and even patching. This reduces manual effort, accelerates response times.
Integrations
RBVM software integrates with various security tools and IT systems, allowing for seamless data sharing and improved collaboration between different teams involved in the vulnerability management process.
Remediation tracking
While vulnerability scanners primarily identify vulnerabilities, RBVM software tracks the status of each vulnerability’s remediation efforts ensuring accountability and providing insights into the progress of fixing vulnerabilities.
Adaptation to New Threats
RBVM software can incorporate threat intelligence and provide recommendations based on emerging threats, ensuring that vulnerabilities associated with the latest attack vectors are quickly addressed.
We Are Built To Scale
Our commitment to cybersecurity excellence isn’t just a promise but a quantifiable reality. At Strobes, our mission is clear: to not only enhance your security posture but to do so with tangible, measurable results. It’s not just about namesake security; it’s about smart, efficient cybersecurity that translates into a 25% cost reduction. Our achievements are more than statistics; they’re a testament to the genuine impact Strobes has.
2
Assets Managed
10
Vulnerabilities Ingested
60
Faster Compliance
35
Reduction In Operations Cost
Aggregate, Enrich & Prioritize
Multi-Source Vulnerability Consolidation
We understand that every organization invests in security differently, with unique environments, ecosystems, and requirements. To cater to these diverse needs, we provide over 100+ connectors that cover your entire security stack. From Vulnerability Scanners (SAST, DAST, Network) to Internal Security Teams, External Security Vendors, Bug Bounty Programs, and more.
Secure Your Entire Asset Ecosystem
While daily, weekly, and monthly scans are crucial, the risks posed by third-party vendors, subsidiaries, and external entities should not be overlooked. Strobes Risk Based Vulnerability management enables you to uncover the entire threat landscape and discover vulnerabilities across your entire ecosystem. Onboard business units, assets, and vulnerability report to correlate and secure all elements of your organization.
All Your Favorite Tools, One Powerful Platform
Strobes offers 120+ integration with a wide range of your favorite tools, whether it’s your code repository, automation tools, SAST, DAST, cloud, infrastructure scanners, or ticketing and messaging platforms.









