At Strobes, we understand the critical importance of securing your APIs. Our API Penetration Testing services are designed to identify and address potential security weaknesses in your API infrastructure. Our team of skilled and certified security professionals will meticulously assess your APIs, ensuring they are robust, reliable, and protected against potential threats.
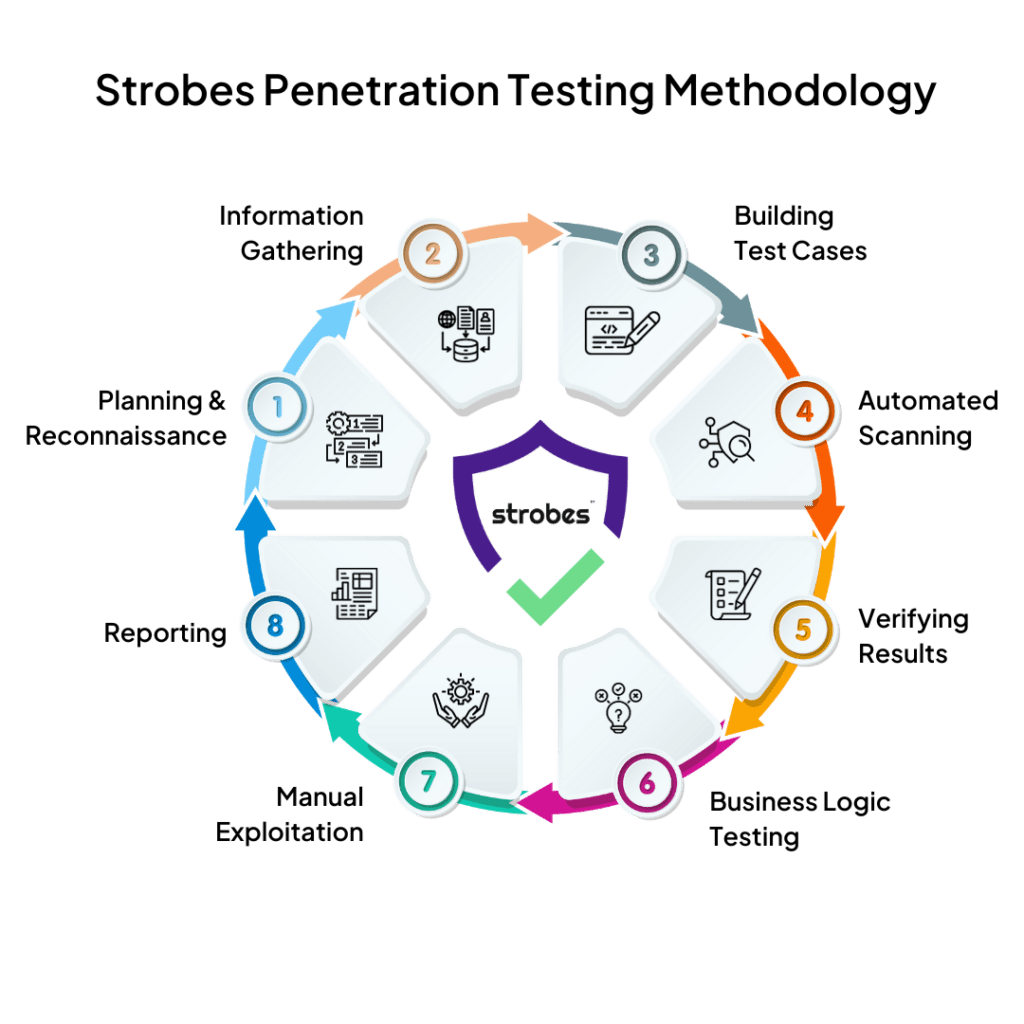
The Methodology
APIs simplify the process of accessing the functionalities you provide for companies and teams, eliminating the need for them to develop these features independently. However, because your APIs are openly accessible, any vulnerability could potentially affect every application that depends on them. Such API security vulnerabilities have the potential to damage your reputation. Our approach involves the deployment of different tools commonly utilized by attackers, allowing us to assess your API as if it were under real-time threat.
Malicious manipulation of input parameters to execute unauthorized commands or access sensitive data in APIs.
Weak or improper access controls lead to unauthorized access or privilege escalation in APIs.
Improperly configured access controls enable unauthorized actions and data exposure through APIs.
Direct exposure of internal object references leading to unauthorized data access in APIs.
Assessing the app for vulnerabilities that could allow RCE, LFI, SQL etc.
Execution of untrusted data in APIs, exposing users to session hijacking or data theft.
Vulnerability to injection attacks and buffer overflows in APIs due to improper input validation.
APIs returning excessive or unnecessary data inadvertently exposing sensitive information.
Vulnerability to injection attacks and buffer overflows in APIs due to improper input validation.
Unencrypted data transmission in APIs prone to interception, tampering, or theft.
APIs are susceptible to mass assignment attacks allowing unintended data modifications.
Best at customer support
Multiple reports for your needs
We offer an array of meticulously crafted reports that cater to diverse stakeholders, ensuring everyone stays in the loop with a clear understanding of your application’s security.
Executive Summary Report
Technical Report
Remediation Report
Compliance Report
Business Impact Analysis
Recommendations and Best Practices

Penetration Testing Requirements Covered by Strobes
At the core of our unwavering dedication to top-tier security standards are our certified experts. Embodying excellence through prestigious certifications like CREST, OSCP, CISSP, and CEH, our team stands as the bedrock of unparalleled security expertise.
Where Automation Meets Human Brilliance
Your success is our priority, and we believe that achieving it should never be a compromise between automation and human touch. With Strobes, you get the best of both worlds, ensuring that every decision you make is guided by efficiency and expertise. Say goodbye to inefficient manual reviews as we lead the way to a future where you can save time and resources, with up to an 80% reduction in manual processes.










