Attack Surface Management
An all-encompassing solution providing unparalleled visibility over your digital footprint. Identify all your IT assets and monitor them for vulnerabilities, Zero-days and configuration weaknesses.




Learn How It Works
We combine multiple techniques that involve a scalable yet efficient way to discover assets, vulnerabilities, misconfigurations and more.
Find everything that belongs to you on the internet.
Find everything that belongs to you on the internet.
Asset Discovery
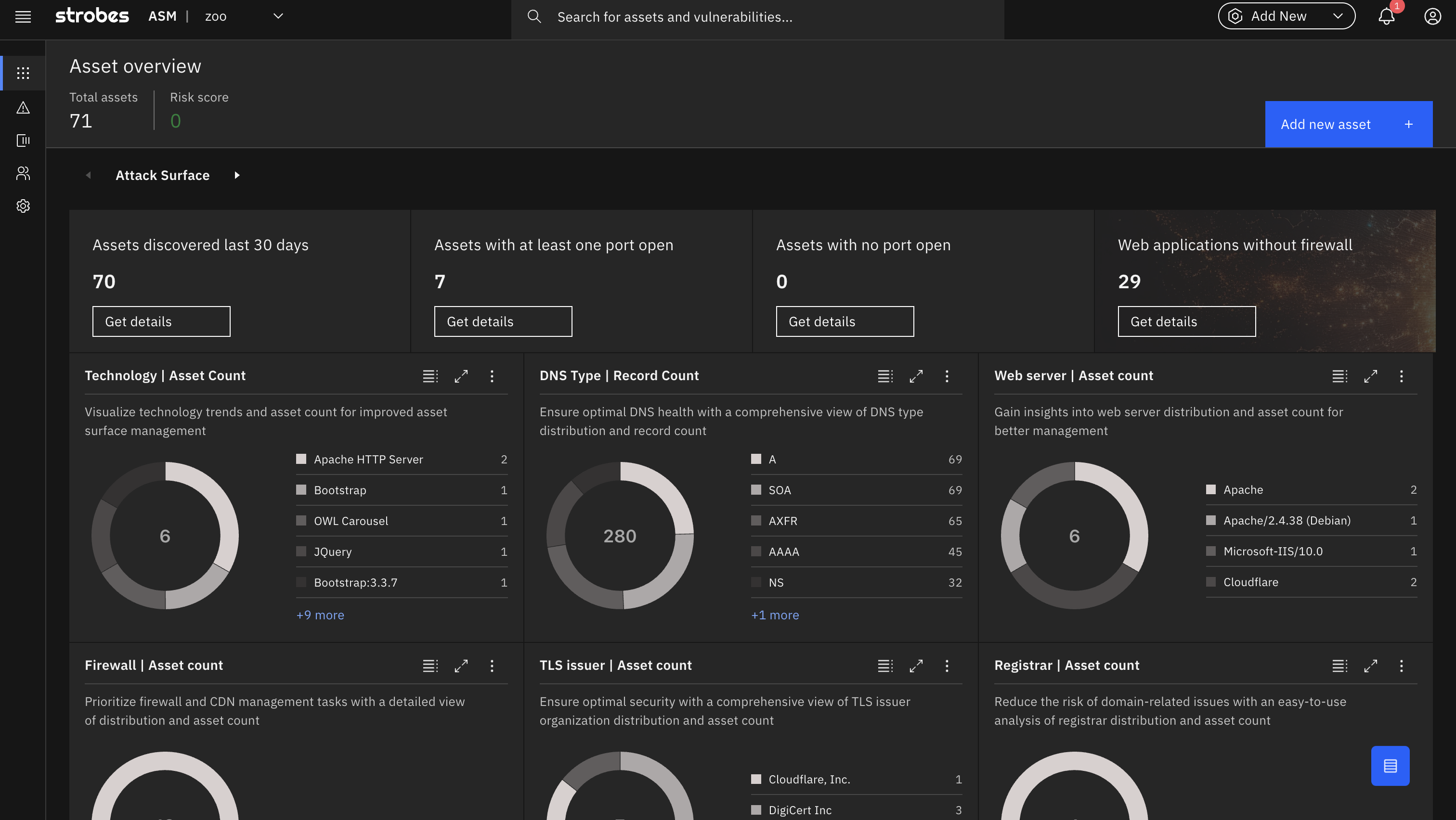
All security journeys begin with asset discovery & intelligence. with Strobes ASM get a 360° view of your organization’s digital presence, including domains, IP addresses, digital certificates, email IDs, cloud services, open ports, and technologies. By continuously monitoring and cataloging these assets, you can maintain an up-to-date inventory and ensure airtight protection.
Domain Protection
Domain Protection focuses on ensuring the security and integrity of an organization’s domain. It involves monitoring domain registration details, DNS configurations, and associated web services to identify potential vulnerabilities or misconfigurations that could be exploited by attackers.
Vulnerability Scanning
Strobes vulnerability scanning bolsters your digital infrastructure against a wide spectrum of cyber threats. Identify outdated and ageing technologies, Unearth threats like XSS, misconfigurations, and SQL injections, identify exposed services and potential entry points, Stay updated with the latest CVEs and zero-day threats and more.
Phishing & Malware Detection
Phishing & Malware Detection focuses on identifying and mitigating threats that aim to deceive users or deliver malicious software. This involves continuous monitoring of digital assets for signs of fraudulent activity, malicious code, or deceptive content intended to exploit individuals and systems.
Setup Strobes ASM In 3 Easy Steps
Add Keywords
Provide information like domain names, ASN, Organization names etc.
Visualize
Look into different type of alerts like phishing, malware, DNS Squatting, vulnerabilities and more.
Patch
Start closing and patching the threats according to their severities.
Discover how Strobes efficiently manages attack surfaces, mitigates risks, and enhances your cybersecurity posture. To delve into the specifics, check out the official datasheet.
Checkout How Strobes Attack Surface Management Works
Assets Discovered
3
Vulnerabilities Identified
100
Domains Monitored
10
Hours Saved
1000
What Makes Strobes Attack Surface Management Different?
Strobes ASM stands out in the crowded asset management market for its intuitive interface, real-time scanning capabilities, and comprehensive data insights. Unlike many solutions that offer static, outdated views, Strobes ensures users get up-to-date information on their assets. With advanced features like vulnerability scanning and dynamic widgets tailored to unique use cases, users gain not just visibility but actionable insights.