Discovering vulnerabilities in your web applications is crucial to maintaining robust security in today’s digital landscape. Strobes offers the leading Penetration Testing as a Service, empowering you to fortify your web apps and protect your valuable data from any potential cyber threats.
The Methodology
With an impressive track record of over 6000+ successful web application penetration tests in the last 7 years, we wield an unparalleled level of expertise in swiftly assessing the full spectrum of vulnerabilities. Our rigorous and battle-tested process, firmly rooted in the industry-standard OWASP methodology, seamlessly integrates web application security into the very fabric of your organization’s DNA.
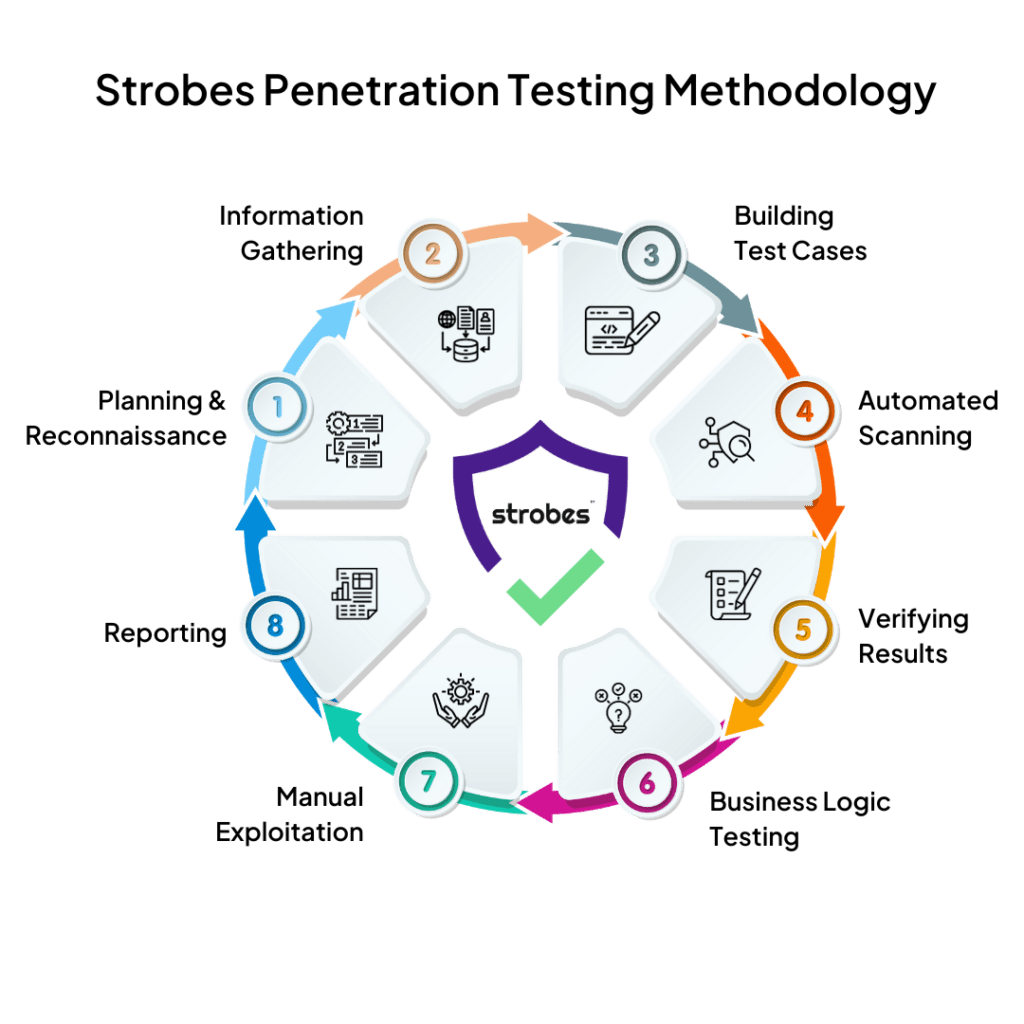
Strobes covers the full range of application-based vulnerabilities, from well-known threats to obscure loopholes. Our meticulous approach ensures that every potential avenue for exploitation is thoroughly investigated and fortified. With a focus on industry best practices and battle-tested methodologies, our cutting-edge platform reveals a comprehensive range of vulnerabilities, including the OWASP Top 10.
Best at customer support
Multiple reports for your needs
We offer an array of meticulously crafted reports that cater to diverse stakeholders, ensuring everyone stays in the loop with a clear understanding of your application’s security.
Executive Summary Report
Technical Report
Remediation Report
Compliance Report
Business Impact Analysis
Recommendations and Best Practices

Penetration Testing Requirements Covered by Strobes
At the core of our unwavering dedication to top-tier security standards are our certified experts. Embodying excellence through prestigious certifications like CREST, OSCP, CISSP, and CEH, our team stands as the bedrock of unparalleled security expertise.
Where Automation Meets Human Brilliance
Your success is our priority, and we believe that achieving it should never be a compromise between automation and human touch. With Strobes, you get the best of both worlds, ensuring that every decision you make is guided by efficiency and expertise. Say goodbye to inefficient manual reviews as we lead the way to a future where you can save time and resources, with up to an 80% reduction in manual processes.