Application Security Posture Management
Build secure applications from the start by scanning code, analyzing open-source dependencies, and generating SBOMs automatically. Findings are prioritized, remediation is accelerated, and compliance reports are always ready.







Start Your Strobes ASPM Journey In Five Simple Steps
Integrate Your SDLC Ecosystem
Connect tools and processes to ensure uninterrupted visibility and oversight.
Map Context and Criticality
Prioritize assets and vulnerabilities based on business impact and operational risk.
Enable Automated Security Analysis
Apply guardrails within the SDLC to quickly detect issues early without delays.
Harness Custom Insights
Create queries, dashboards, and reports to support accurate security decisions.
Continuous Security Improvement
Set benchmarks, track progress, and refine security posture each cycle.
Transform Your DevOps into DevSecOps
The Strobes ASPM Advantage
- Immediate efficiency boosts for both security and development teams, thanks to streamlined processes and clear visibility.
- Cost-effective security management, achieved through advanced automation and enhanced process visibility.
- Environment-specific risk prioritization, ensuring that security efforts are aligned with your unique risk landscape
- Quick risk mitigation, supported by automated guardrails and sustained compliance efforts.
- Improved cross-departmental collaboration, fostering a culture of security and efficiency.
Continuously Lower Your Application Security Risk
Real-time visibility across applications, pipelines, SDLC systems, and teams, ensuring no blind spots in your security posture.
Identification of security gaps, offering targeted insights for full-spectrum defense strategies.
SDLC security automation, simplifying the enforcement of security best practices and guardrails.
Comprehensive software supply chain threat protection, safeguarding against emerging vulnerabilities and attack vectors.
42
65
23
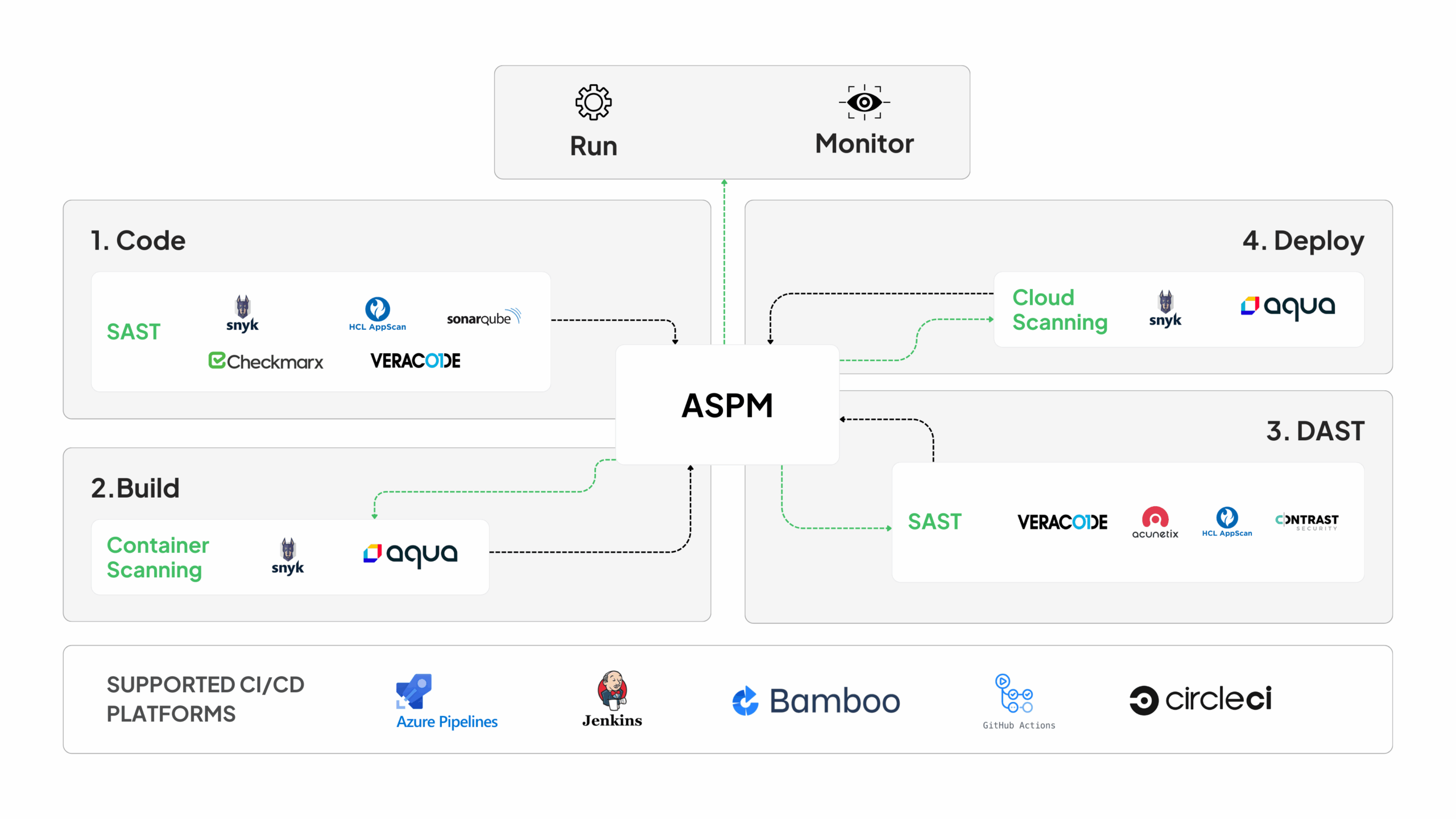
Aggregate Data from all your Favorite Tools
Strobes offers 120+ integration with a wide range of your favorite tools, whether it’s your code repository, automation tools, SAST, DAST, cloud, infrastructure scanners, or ticketing and messaging platforms.
VIEW INTEGRATIONSWhy Strobes ASPM
Compliance Made Easy
Simplify meeting industry standards and regulations. ASPM demonstrates your proactive approach to application security, reducing compliance burdens.
See It All, Secure It All
Gain constant visibility into your applications’ security posture. Identify and fix vulnerabilities before they can be exploited by attackers.
Reduce Your Risk Profile
Proactively address security weaknesses. ASPM minimizes your attack surface and reduces the risk of data breaches.
Automate the Grind
Streamline vulnerability management. Automated workflows prioritize threats and efficiently remediate issues.
Bridging the Gap
Foster seamless collaboration between security and development teams. ASPM ensures faster, more effective application security by streamlining communication.
Streamline Security Resources
Focus on what matters most. ASPM helps prioritize critical vulnerabilities and automates manual tasks, optimizing your security resources.