Traditional asset inventory and vulnerability management software can’t keep up to date with the growing attack surface and morphing vulnerabilities. Contrary to other cybersecurity software, Attack Surface Management software operates from a hacker’s perspective which brings the SOCs and security teams to establish a proactive offense strategy.
Organizations are gravitating toward Attack Surface Management (ASM) due to the escalating complexity of their digital ecosystems and the dynamic nature of cybersecurity threats. The proliferation of web applications, APIs, and interconnected devices has expanded the attack surface, prompting a need for comprehensive visibility and risk mitigation.
ASM offers a proactive and continuous strategy, enabling organizations to identify vulnerabilities, and prioritize risks, and efficiently allocate resources.
What is an Attack Surface Management(ASM) Software?
The idea behind all ASM software is that “You can’t fix what you can’t see!”. An Attack Surface Management allows a user to get a real-time view of all the attack vectors in the organization(known, unknown, rogue) and continuously monitor and analyze them for any zero days/vulnerabilities and misconfiguration.
How does an ASM Work?
Attack Surface Management consists of the following components-
1. Asset Discovery
In the world of cybersecurity, the term “attack surface” refers to the total number of points or ‘vectors’ where an unauthorized user can try to enter data or extract data from an environment. This is akin to the number of doors and windows in a building; the more openings you have, the more opportunities there are for an intruder to break in.
In the digital space, these openings can be anything from active ports to outdated applications, unpatched vulnerabilities, or even erroneous configuration settings that can be exploited. Understanding the various categories of assets is crucial in managing an organization’s attack surface effectively. Let’s break down each category,
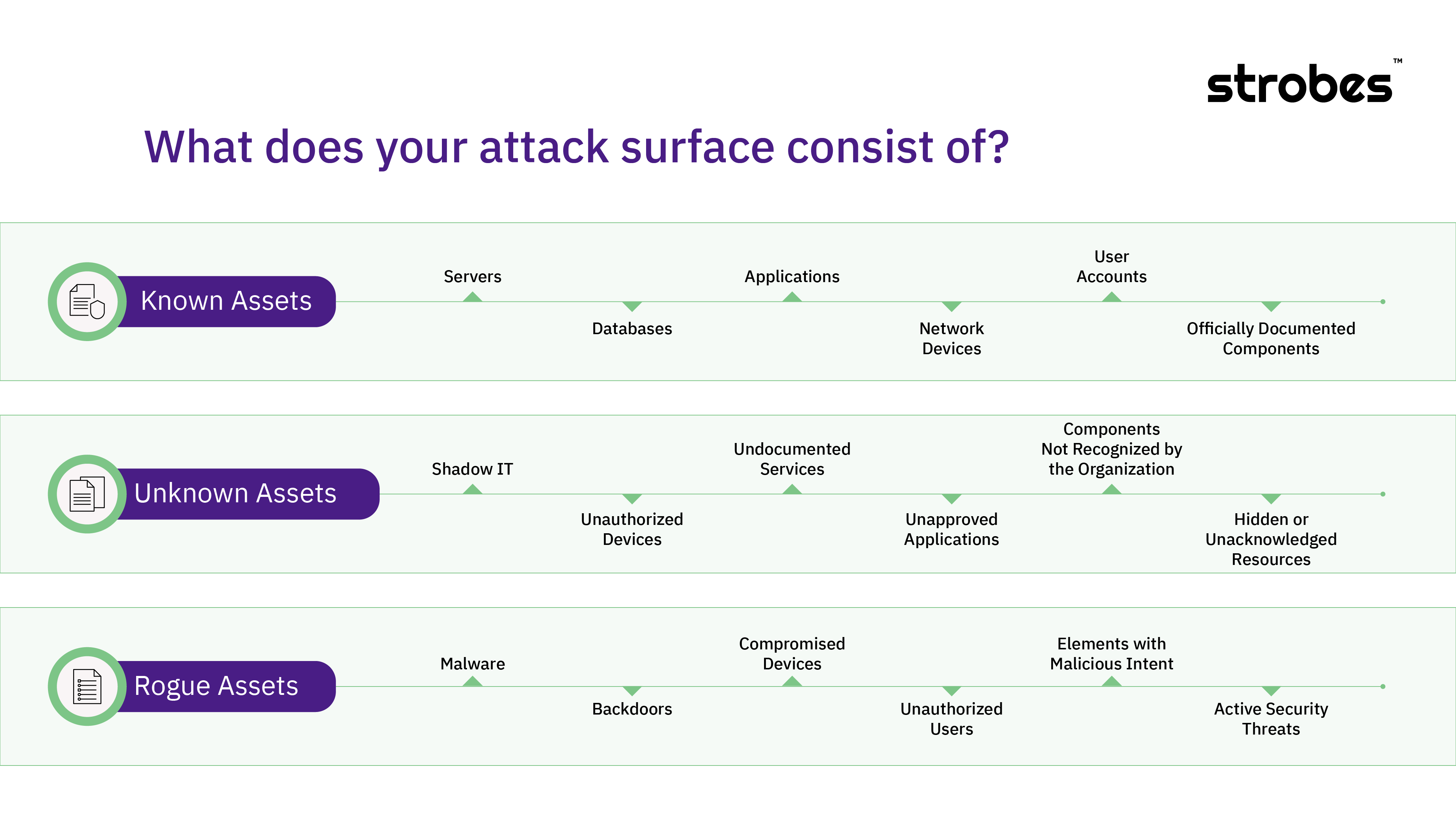
A. Known Assets
Known assets are the elements of the IT environment that are inventoried and actively managed by the organization. This includes:
- Corporate Websites: The main face of your organization online, which could be targeted for defacement, denial of service, or as an entry point for deeper attacks.
- Examples –
- www.yourcompany.com
- login.yourcompany.com (Employee login portal)
- Examples –
- Servers: Host a variety of services and applications and can be vulnerable to various attacks if not properly secured and updated.
- Examples –
- Main application server hosting customer portal.
- Database server storing customer information.
- Examples –
- Dependencies: Software libraries or services that your systems depend on, which can contain vulnerabilities that could be exploited if they are not kept up to date.
- Examples –
- MySQL database used by the customer relationship management (CRM) system
- External API service used for payment processing.
- Examples –
B. Unknown Assets
These are the assets that the organization has lost track of or never knew existed often referred to as Shadow IT. Examples include
- Unmanaged IT Infrastructure: Servers, databases, or applications that were set up without security oversight and may be running outdated software or contain sensitive data.
- Examples-
- Legacy server set up by a department without IT oversight.
- Forgotten test server running outdated software.
- Examples-
- Development and Marketing Websites: These may not follow the same stringent security protocols as the main corporate website and can be an easy target for attackers.
- Examples-
- www.promo.yourcompany.com created by the marketing team for a campaign.
- Internal project website set up by a development team without IT approval.
- Examples-
C. Rogue Assets
Rogue assets are unauthorized or malicious infrastructure that can be used to launch attacks against an organization, including
- Malware: Malicious software that can infiltrate systems to steal data, cause damage, or create a foothold for further attacks.
- Examples-
- A phishing email containing malware that, once opened, infiltrates the user’s computer.
- USB drive with malware introduced into the corporate network.
- Examples-
- Typosquatted Domains: Domains that are variations of your company’s domain name, set up by threat actors to deceive and capture information from your clients or employees.
- Examples-
- www.yourcompny.com – a variation of your official domain designed to deceive.
- www.yourcompany-login.com – a deceptive login page.
- Examples-
- Impersonated Websites or Apps: These can be used in phishing campaigns to trick users into providing sensitive information.
2. Inventory and Classification
Once assets are discovered, they are classified and categorized based on their criticality, function, and potential risk factors. This step involves creating a detailed inventory that helps organizations understand the scope of their attack surface. Assets may be classified as internal or external, and their importance to business operations is assessed. Here is a list of the classifications of the assets-
- Cloud storage and network devices
- Public code repositories such as GitHub, BitBucket, and GitLab
- Domain names, SSL certificates, and IP addresses
- Mobile applications and their backends
- IoT and connected devices
- Web applications, services, and APIs
- Email servers
3. Asset Analysis and Prioritization
ASM involves a detailed analysis of each asset’s vulnerabilities, weaknesses, and potential exposure points. This analysis is crucial for prioritizing vulnerability based on risk. Critical assets, such as those containing sensitive data or serving essential functions, are given higher priority for security measures. This step helps organizations allocate resources efficiently to address the most significant risks first.
4. Continuous Monitoring
ASM is not a one-time process but a continuous, ongoing effort. Continuous monitoring involves real-time tracking of changes in the organization’s digital landscape. Any new assets, vulnerabilities, or changes in the environment are promptly identified and assessed. This proactive approach ensures that the organization can adapt to emerging threats and evolving attacks.
These checks include evaluating vulnerabilities in software, network security, insecure SSL/TLS certificates, potential exposure to known data breaches and leaks, HTTP accessibility, email spoofing and phishing risks, SPF, DKIM, and DMARC settings, unnecessary exposure of open administration, database, app, email, and file-sharing ports, HTTP Strict Transport Security (HSTS) compliance, and the secure configuration of cookies vectors.
Types of threats that can happen on your Attack Surface
The attack surface of an organization can be broad and varied, encompassing all the points where an attacker could potentially gain unauthorized access to systems or data. Here are the primary areas where attacks can materialize:
1. Network Services
- Open Ports: Unnecessary open ports on servers can provide entry points for attackers.
- Protocol Vulnerabilities: Weaknesses in protocols like SMB, FTP, or HTTP can be exploited.
- Firewall Misconfigurations: Incorrectly configured firewalls may leave network services exposed.
2. Software Vulnerabilities
- Outdated Software: Systems running on outdated software may have unpatched vulnerabilities.
- Third-Party Components: Vulnerable third-party libraries or plugins can serve as a gateway for attacks.
3. Web Applications
- Injection Flaws: SQL injection, command injection, and other flaws can allow attackers to run malicious commands.
- Broken Authentication: Weak login mechanisms can allow attackers to assume the identity of legitimate users.
4. Endpoints
- Unsecured Devices: Employee devices without adequate security controls can be compromised.
- Mobile Devices: Mobile phones and tablets, if not properly managed, can provide easy access to corporate networks.
5. Cloud Services
- Misconfigured Storage: Improperly secured cloud storage buckets can lead to data leaks.
- Inadequate Access Controls: A lack of robust access controls can allow unauthorized access to cloud resources.
6. User Interaction
- Phishing Attacks: Social engineering attacks can trick users into revealing sensitive information.
- Physical Security: Unauthorized physical access to facilities can lead to direct system compromise.
7. Internet of Things (IoT)
- Insecure IoT Devices: Many IoT devices lack basic security features, making them susceptible to attacks.
- Device Interconnectivity: The interconnectivity of IoT devices can allow an attacker to pivot from one device to another within a network.
8. Operational Technology (OT) and Industrial Control Systems (ICS)
- Legacy Systems: Many OT systems were not designed with internet connectivity in mind and are vulnerable to modern threats.
- Network Segmentation: Lack of proper segmentation between IT and OT networks can allow threats to traverse from one to the other.
9. Third-Party and Supply Chain
- Vendor Risks: Compromise of a vendor’s systems can lead to a breach in your own environment.
- Supply Chain Attacks: Attackers can compromise software or hardware at any point in the supply chain
10. APIs and Service Endpoints
- API Vulnerabilities: APIs that are not properly authenticated and encrypted can be exploited to access backend systems and data.
- Service Exposures: Services exposed for integration purposes may inadvertently expose sensitive data or functionality.
Why is Attack Surface Management Important?
The adage “less is more” is particularly apt when it comes to managing an organization’s attack surface. The attack surface encompasses all the points where an attacker can try to enter or extract data from your environment. Therefore, the larger the attack surface, the more opportunities there are for attackers to exploit it. Reducing the attack surface by using platforms like Strobes ASM is about minimizing these opportunities and is a strategic necessity for several reasons
1. Simplifying Security Management
A smaller attack surface is inherently easier to monitor and protect. With fewer components to manage, security teams can concentrate their efforts and resources more effectively, reducing the chances of oversight or errors that could lead to breaches.
2. Minimizing Attack Vectors
Each open port, active service, or deployed application is a potential entry point for an attacker. By reducing the number of these entry points, you inherently decrease the number of vectors an attacker can use to compromise your systems.
3. Improving Response Time
When the attack surface is limited, it is quicker for security teams to detect and respond to threats. This rapid response can be the difference between a minor security incident and a catastrophic data breach.
4. Reducing Complexity
Complex systems with extensive attack surfaces can have interdependencies that are difficult to understand and secure. Reducing the attack surface simplifies these systems, making it easier to implement security measures effectively.
Example: The Mirai Botnet Exploit
The importance of attack surface reduction was starkly highlighted by the Mirai botnet incident. Mirai exploited simple vulnerabilities in widespread IoT devices – namely, default username/password combinations that were rarely changed by the user.
These IoT devices were designed for convenience and functionality, not security, thus significantly expanding the attack surface. The result was a massive botnet of compromised devices capable of launching devastating Distributed Denial of Service (DDoS) attacks.
Examples of Attacks
1. Subdomain Takeover
This occurs when an attacker takes control of a subdomain of a legitimate website, often due to a DNS configuration issue or when a service that the subdomain was pointing to is no longer active.
Reference: https://github.com/EdOverflow/can-i-take-over-xyz
2. Secrets Listed on Public GitHub Repository
Sensitive information such as API keys or passwords is accidentally uploaded to public repositories on GitHub, making it available to anyone who knows where to look.
Reference: https://blog.gitguardian.com/leaking-secrets-on-github-what-to-do/
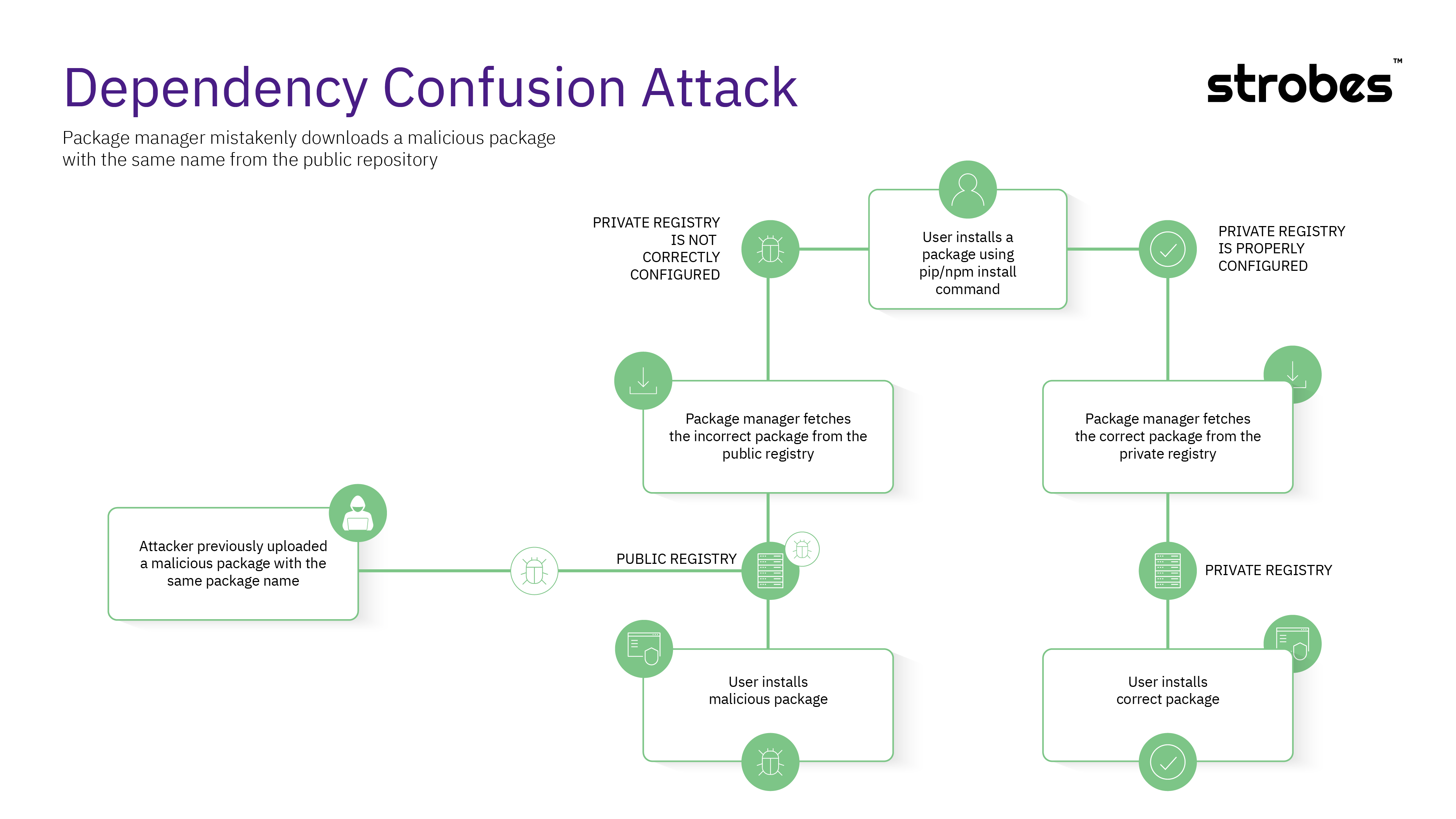
3. Dependency Confusion Attacks
An adversary publishes a malicious package with the same name as a private module used within a company’s software. If the company’s package management system is misconfigured, it could pull the malicious package instead of the internal one.
Reference: https://fossa.com/blog/dependency-confusion-understanding-preventing-attacks/
4. Credentials Leaked in a Breach
Credentials from a company breach are discovered in a public dump. The same credentials are used across multiple services, including Active Directory, leading to a widespread compromise within the organization.
Reference: https://haveibeenpwned.com/Passwords
5. Misconfigured AWS S3 Buckets, Azure Blobs, etc
S3 buckets are left open to the public, allowing anyone to view or download the stored data. This misconfiguration has led to numerous data leaks and exposures.
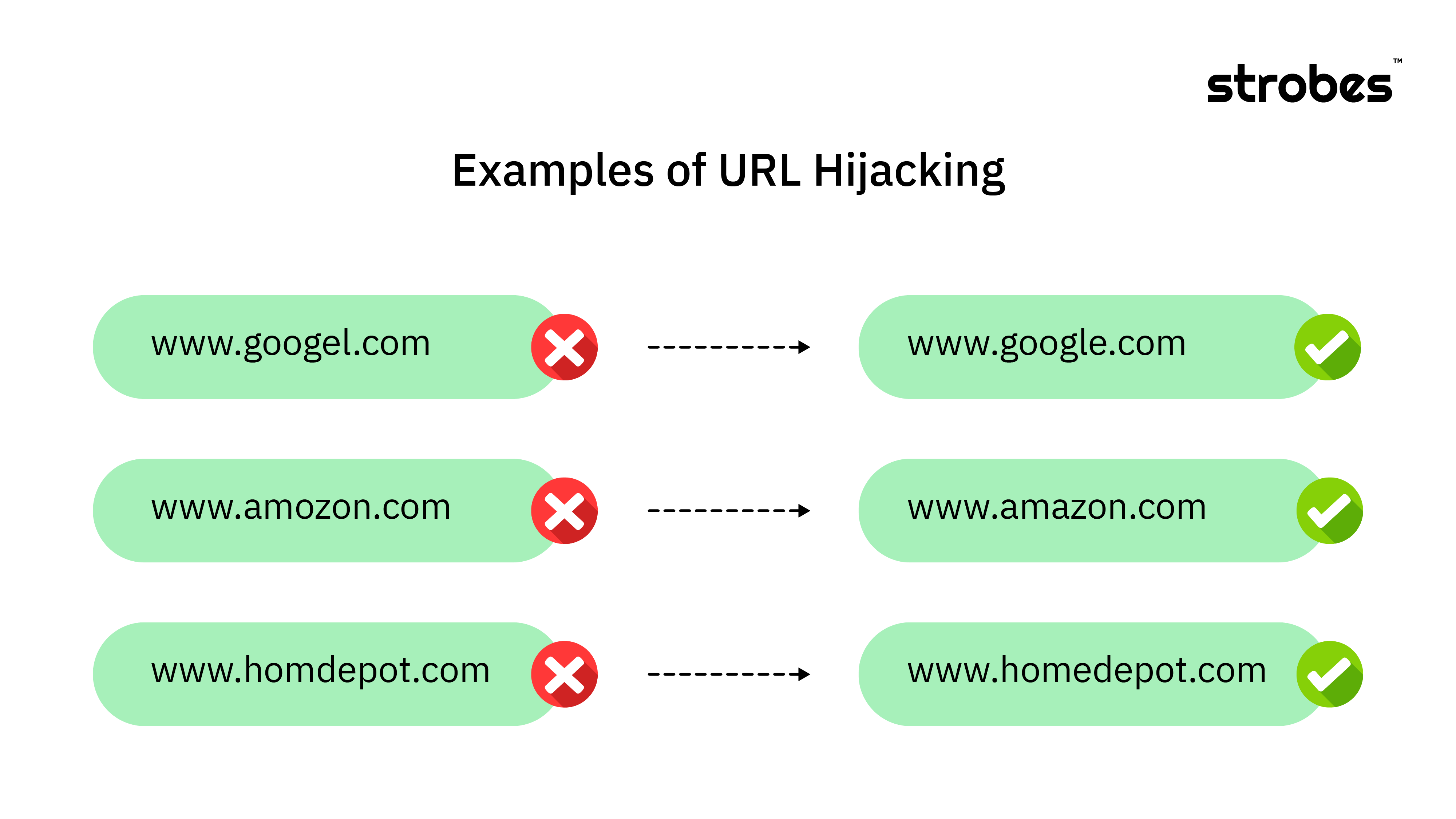
6. Phishing & DNS Squatting
Attackers continuously create fake landing pages similar to your internal or public websites using DNS squatting to phish employees and use the same credentials to login to sensitive applications.
Reference: https://github.com/mitchellkrogza/Phishing.Database
How can Strobes help you manage your Attack Surface?
The ability to quickly identify and respond to vulnerabilities is not just advantageous—it’s imperative for survival. Strobes Attack Surface Management (ASM) stands as a vanguard, offering organizations a robust platform capable of detecting over 10,000 known CVEs, alongside a wide spectrum of threats akin to the ones we’ve discussed.
From network misconfigurations and software vulnerabilities to cloud exposures and endpoint weaknesses, Strobes ASM empowers businesses to stay ahead of breaches with its comprehensive surveillance capabilities.
With Strobes ASM, you can
- Gain a complete 360° view of your attack surface.
- Reduce risk by proactively identifying and addressing vulnerabilities.
- Prioritize remediation efforts with actionable intelligence.
- Enhance your security posture with continuous monitoring.
Create an account and experience all the features of ASM for 30 days risk-free. Start your free trial now!
Related Reads:
- Integrating Attack Surface Management and Penetration Testing as a Service
- Understanding External Attack Surface Management (EASM)
- Use Case: Rapid Identification and Escalation of a Critical Threat by Strobes ASM
- How to Check for Subdomain Takeover: A Step-by-Step Guide
- Cloud Attack Surface Management(CASM): What is it? How does Strobes CASM help you with cloud security?
- Case-Study: How We Secured a Leading SaaS CRM: Unmasking Exposed Docker Images with ASM
- Solution: Attack Surface Management Solution









