In this extensive dive, we’re going to explore the intricacies of attack Surface Management (ASM) and penetration testing as a Service (PTaaS), two critical components in the cybersecurity arsenal.
By the end of this, you’ll have a deep understanding of how these elements work independently and, more importantly, how integrating attack surface management and penetration testing as a service creates a more resilient and proactive cybersecurity posture.
Part 1: Decoding Attack Surface Management
The concept of an attack surface is straightforward – it’s all the points where an attacker can try to enter your systems or extract data. Managing this surface is a complex, ongoing task that’s crucial for robust cybersecurity.
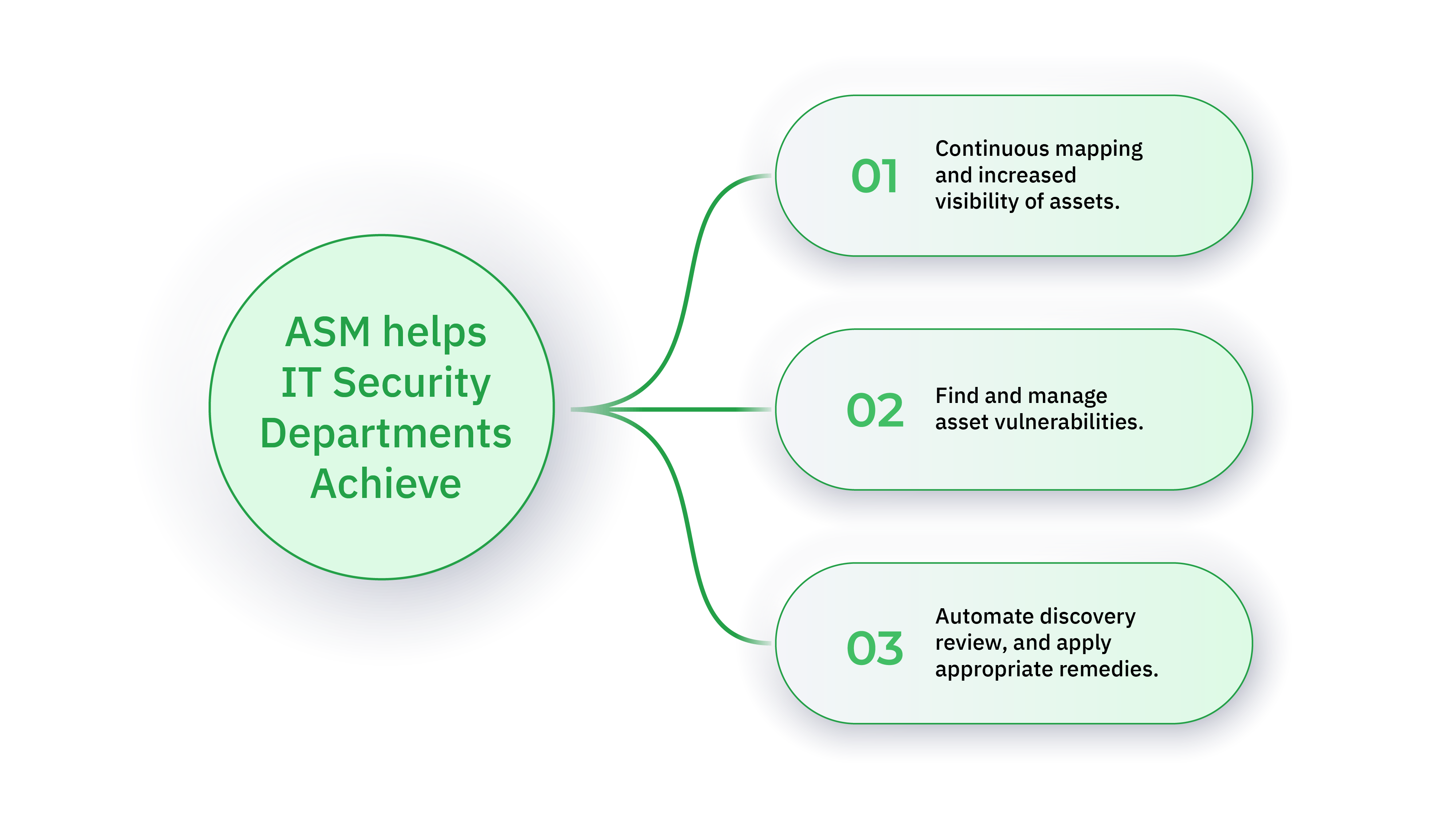
- Continuous Asset Discovery and Monitoring: The first step in ASM is knowing what you need to protect. This isn’t a one-time activity; it’s a continuous process. Imagine an environment where new servers are spun up, services are deployed, and existing ones are updated – all these change your attack surface.
Tools used here include automated scanners that can detect active web servers, DNS records, and even cloud storage instances. A practical example is when a new subdomain is created for a marketing campaign; attack surface management tools should automatically detect this and add it to the list of assets that need protection.
- Vulnerability Identification and Prioritization: Once you know what’s on your attack surface, the next step is to understand the vulnerabilities each asset has. This process involves using tools and techniques like vulnerability scanners, which can detect issues ranging from unpatched software to misconfigurations.
For example, suppose an ASM tool finds an open S3 bucket. It’s not just about identifying this bucket but also understanding the data it holds and the potential risks associated with it.
- Asset Classification and Risk Assessment: Not all assets are created equal. Some hold sensitive customer data, while others might be less critical public-facing informational websites. ASM involves classifying these assets based on their criticality and the risk they pose. For instance, an internal database with customer information would be classified as high risk and therefore would be a higher priority for remediation efforts.
Part 2: The World of Penetration Testing as a Service
PTaaS takes an offensive stance in cybersecurity. It’s about thinking like an attacker and finding ways to breach defences before a real attacker does.
- Customized Penetration Tests: The beauty of PTaaS is its tailored approach. Based on the reconnaissance, PTaaS teams create specific tests for specific assets. This could mean launching a series of targeted attacks against a newly deployed API to uncover any potential security flaws.
- Advanced Threat Simulation: In today’s cyber landscape, attackers are sophisticated and so should be the testing. PTaaS includes simulating advanced threats, like Zero-Day Vulnerability Exploits & Attacks, to see if the current defenses can withstand them. An example here could be simulating an advanced persistent threat (APT) attack on the company’s network to test the resilience of network defenses and employee awareness.
- Ongoing Testing and Adaptation: Cybersecurity is not static; it’s dynamic and constantly evolving. PTaaS embodies this principle by not only conducting one-off tests but also by adapting and evolving testing methodologies as new threats emerge and as the organization’s digital landscape changes.
Part 3: How ASM and PTaaS Can Work Together
The true power of cybersecurity is realized when ASM and PTaaS are integrated. Let’s delve into how these services complement each other.
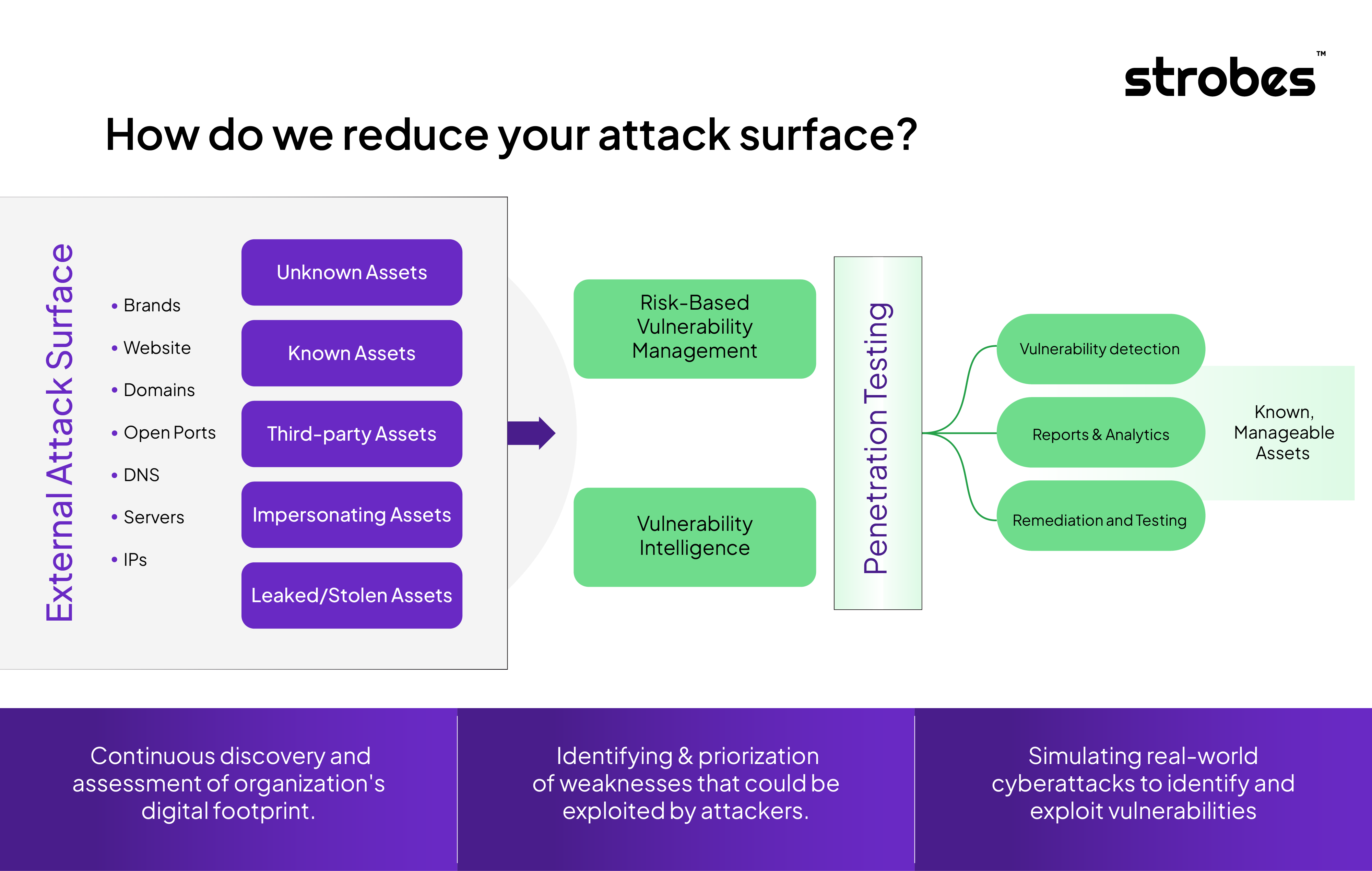
- Data-Driven Penetration Testing: With the continuous data flow from ASM, PTaaS can be more strategic and targeted in its approach. For example, if ASM identifies a new service or application, Pentesting as a Service (PTaaS) can immediately begin testing it for vulnerabilities. This ensures that new assets are not just discovered, but their security is also verified.
- Real-Time Threat Response: When ASM detects a change or a new potential threat, PTaaS can respond in real-time. This rapid response capability is essential in a landscape where threats can emerge and evolve quickly.
- Feedback Loop and Continuous Improvement: Findings from penetration tests can be fed back into the ASM process, continually refining the detection and monitoring capabilities. If a particular type of vulnerability is repeatedly found by PTaaS, ASM tools can be adjusted to look for this type of vulnerability more aggressively in the future.
Part 4: Deep Dive into Continuous Asset Discovery in ASM
One of the pillars of ASM is the continuous discovery and monitoring of assets. This goes beyond mere listing of assets; it involves understanding each asset’s nature, its role in the organization, and its potential vulnerabilities.
- Dynamic Asset Discovery: In a dynamic digital environment, new assets can pop up at any time. ASM tools use a variety of methods, like network scanning, DNS enumeration, and even crawling web applications, to identify new assets. For instance, when a development team deploys a new version of an application, the ASM system should automatically detect it and assess its security posture.
- Integration with Development and Deployment Pipelines: Modern ASM solutions are not standalone systems; they’re integrated into the CI/CD pipeline. This means that when new code is deployed, the ASM system is immediately aware and starts its assessment. This could involve scanning new Docker containers as they are deployed, ensuring that no vulnerabilities are introduced in the deployment process.
Also Read: Introducing Strobes Enhanced Role-Based Access Control: Dynamic Asset Permissions
Part 5: Advanced Vulnerability Analysis in PTaaS
Penetration testing as a service goes far beyond basic vulnerability scanning. It involves a deep analysis of potential security flaws and their exploitation.
- Targeted Attack Scenarios: Based on the information provided by the ASM, PTaaS teams can create specific attack scenarios. This might involve crafting specialized payloads to exploit a SQL injection vulnerability found in a new web application pentesting or testing custom exploit code against a newly discovered service.
- Emulating Real-World Attackers: A crucial aspect of PTaaS is to think and act like real-world attackers. This includes using techniques like social engineering, phishing campaigns, or even physical security breach attempts, depending on the scope of the test.
For example, a PTaaS team might launch a spear-phishing campaign targeting employees who have access to a recently identified critical internal application, to see how well they resist such attacks.
- Automated and Manual Testing Combination: While automated tools are an essential part of penetration testing process, they’re complemented by manual testing efforts. This blend ensures both breadth and depth in testing, as some vulnerabilities, especially those involving complex business logic, can only be identified and exploited by a human tester.
Part 6: The Interplay Between Attack Surface Management and Penetration Testing in Incident Response
When a potential security incident occurs, the combination of Attack Surface Management and Penetration Testing can significantly enhance the response.
- Rapid Incident Analysis: If ASM detects an anomaly, such as an unexpected change in a web application’s behavior, it can trigger an immediate PTaaS response. The PTaaS team can quickly analyze whether this is an actual breach attempt or a false positive.
- Post-Incident Testing: After an incident, PTaaS can be used to conduct targeted tests around the affected area to ensure that no other vulnerabilities were exploited during the incident and to fortify the defenses against similar future attacks.
Part 7: Continuous Improvement Through Feedback Loops
A critical aspect of integrating ASM with PTaaS is the establishment of feedback loops.
- Learning from Penetration Tests: Each penetration test provides valuable insights. For example, if a PTaaS engagement reveals a previously unknown vulnerability in a web application, this information can be used to update ASM processes to look for similar vulnerabilities in other applications.
- Adaptive Security Postures: As the threat landscape evolves, so should the organization’s security posture. Insights gained from ASM and PTaaS should be used to continuously adapt and refine security strategies.
Part 8: Use Cases To Integrate ASM With PTaaS
Let’s look at some real-world scenarios where the integration of Attack Surface Management and Penetration Testing provided significant benefits.
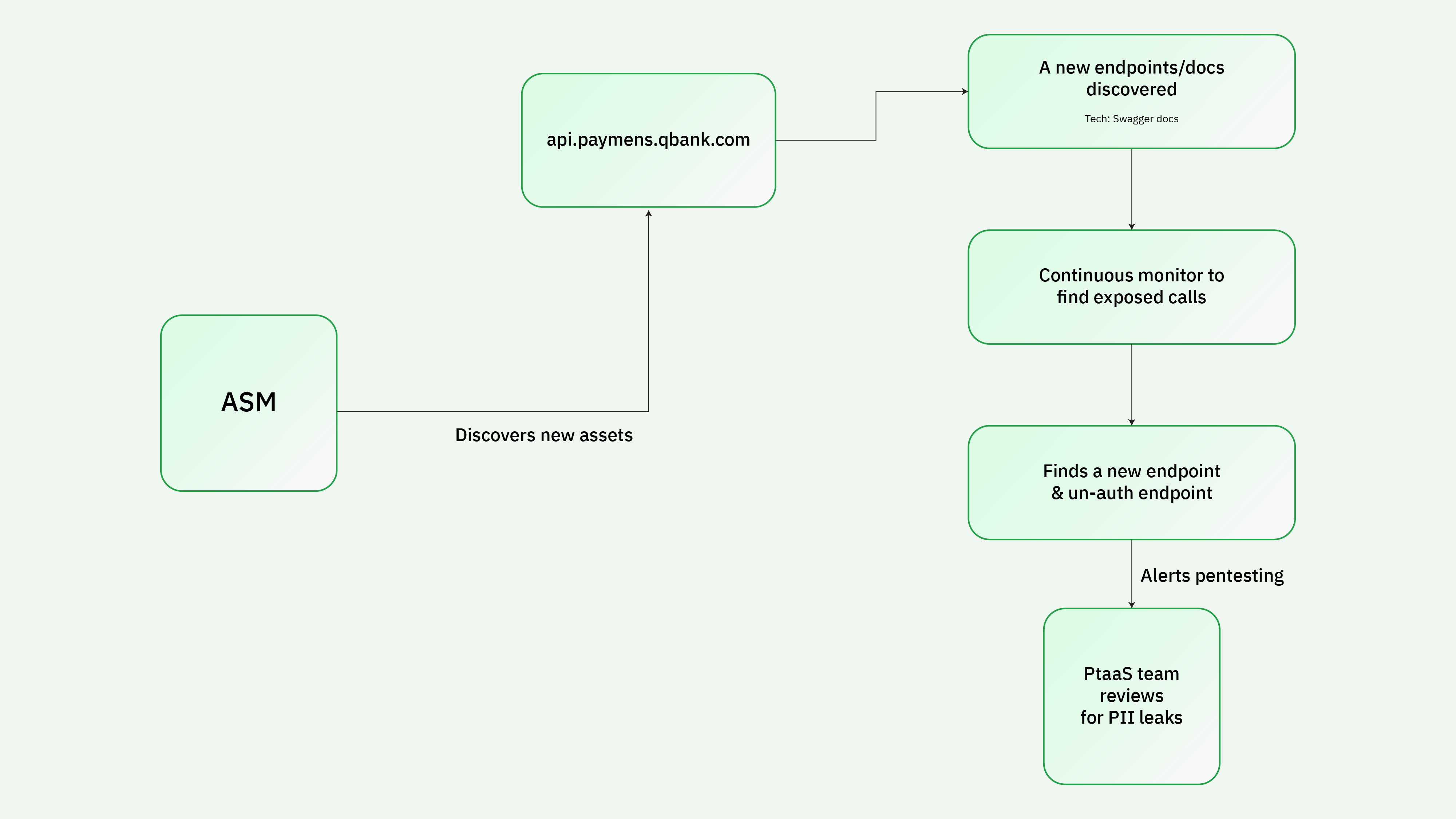
In banks or fintech companies, ASM tools detect an unauthorized API endpoint via exposed swagger docs and immediately notify the PTaaS team to review to find if any sensitive information is being leaked
Part 9: Industry Best Practices in Attack Surface Management and Penetration Testing
For organizations looking to implement or improve their Attack Surface Management and Penetration Testing strategies, here are some best practices:
- Comprehensive Asset Inventory: Ensure that your ASM tool provides a complete and up-to-date inventory of all digital assets, including those in the cloud, on-premises, and in hybrid environments.
- Regular and Rigorous Penetration Testing: Schedule regular penetration tests and ensure they cover all aspects of your digital environment. These tests should be as rigorous and realistic as possible.
- Prioritize Based on Risk: Use the data from ASM to prioritize penetration tests based on the criticality and vulnerability of assets.
- Human Expertise and Automated Tools: Rely on a blend of automated tools and human expertise in both ASM and PTaaS to ensure a comprehensive approach to security.
Part 10: Future Trends in ASM and PTaaS
As we look to the future, several trends are likely to shape the evolution of ASM and PTaaS:
- AI and Machine Learning: The use of AI and machine learning in ASM tools will become more prevalent, allowing for more sophisticated and proactive identification of potential vulnerabilities.
- Increased Automation in PTaaS: We’ll see more advanced automation in penetration testing, although this will not eliminate the need for skilled human testers.
- Greater Integration with DevSecOps: ASM and PTaaS will become more deeply integrated into the DevSecOps pipeline, enabling more agile and responsive security practices.
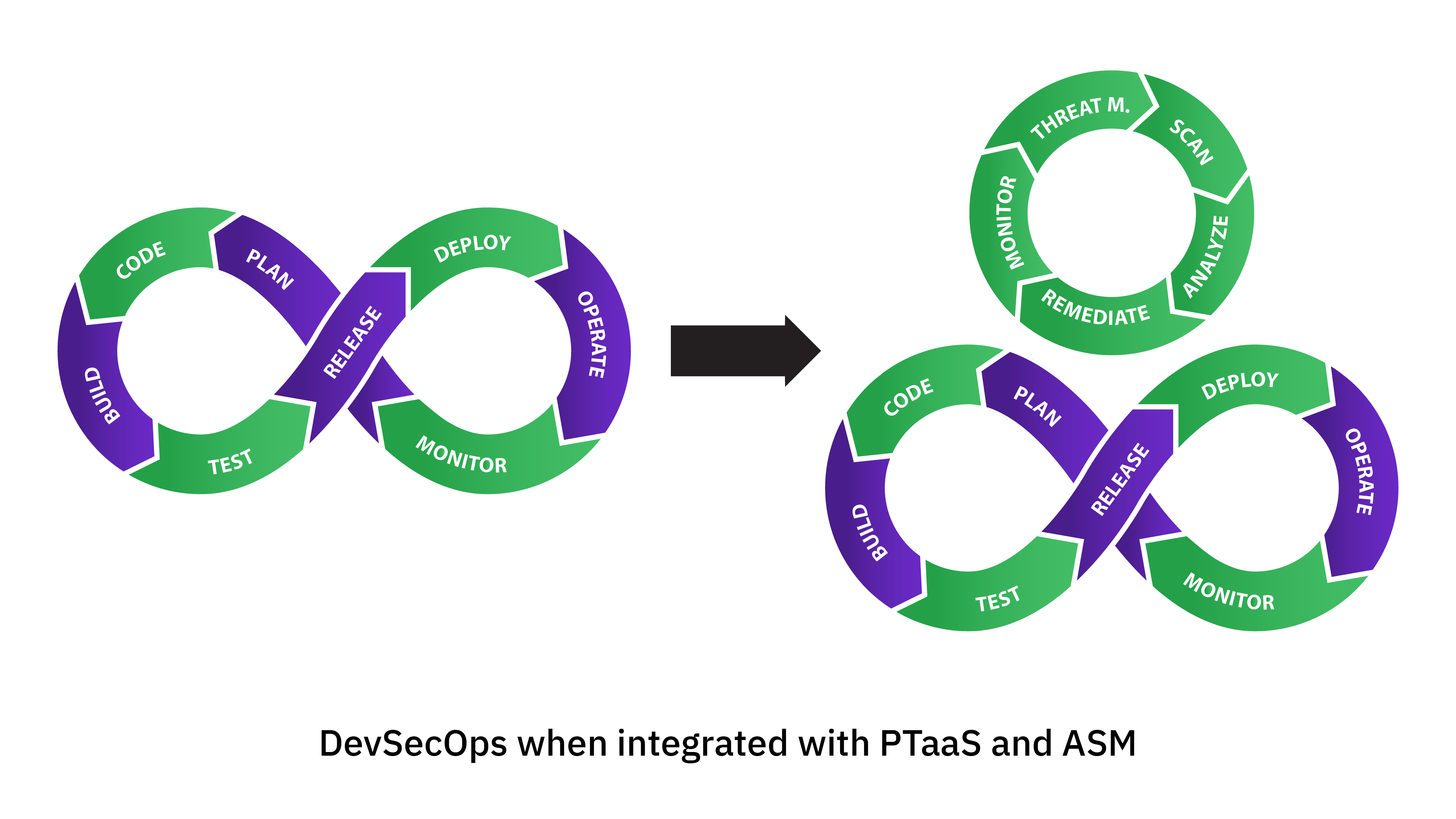
The fusion of attack surface management and penetration testing as a service is more than just a combination of two cybersecurity strategies. It represents a paradigm shift towards a more dynamic, proactive, and comprehensive approach to security.
As we navigate the complexities of the digital age, this fusion is not just beneficial; it’s essential for organizations seeking to protect themselves against an ever-evolving threat landscape.
Synchronizing Strobes ASM with PTaaS: A Unified Approach
The intersection of Strobes ASM and PTaaS cultivates a complementary ecosystem that scales up cybersecurity capabilities efficiently. Advantages of Integrating Strobes ASM with PTaaS:
- Comprehensive Coverage: Ensures no asset is le unmonitored or untested, covering the entire digital footprint.
- Compliance Assurance: Helps maintain compliance with regulatory requirements by ensuring mandatory assets are pen-tested periodically.
- Optimized Resource Allocation: Ulizes the data from ASM to prioritize pentesting efforts, focusing on assets with significant vulnerabilities or those overdue for testing.
- Data-Driven Decision Making: Leverages dashboards and custom fields to extract actionable insights and enhance cybersecurity metrics.
A solution analogous to Strobes PTaaS can significantly enhance an ASM framework. By providing tailored, continuous penetration testing, it ensures that the ASM’s continuous monitoring is complemented by proactive security measures. This integrated approach not only identifies vulnerabilities but also tests and validates the security of each asset, creating a robust and resilient cybersecurity ecosystem.
Ready to see how integrating Attack Surface Management and Penetration Testing can transform your security strategy? Book a demo with Strobes today!
Related Reads:
- Attack Surface Management: What is it? Why do you need it?
- Understanding External Attack Surface Management (EASM)
- Cloud Attack Surface Management(CASM): What is it? How does Strobes CASM help you with cloud security?
- Use Case: Rapid Identification and Escalation of a Critical Threat by Strobes ASM
- Solution: Attack Surface Management









