Subdomain takeovers pose a serious risk to businesses, as websites are the cornerstone of their online identity, driving brand awareness, customer engagement, and revenue. But what if, unknowingly, you’ve created a vulnerability that could expose your entire digital presence to attackers?
Understanding how to check for subdomain takeover is crucial, as these silent threats hide in the shadows, waiting to exploit forgotten or misconfigured subdomains. This blog post is your comprehensive guide to identifying and preventing subdomain takeover.
Understanding Subdomain Takeover
A subdomain is a subdivision of your main domain, allowing you to create separate sections for different functionalities. For example, “<invalid URL removed>” could be a subdomain for your email service.
How do Subdomain Takeover Occur?
Subdomain takeover occur when attackers discover and exploit vulnerabilities in your subdomain configuration, typically through:
- Misconfigured DNS Records: Outdated or unused CNAME or A records pointing to third-party services that are no longer in use.
- Expired or Abandoned Subdomains: Subdomains that are no longer actively managed and lack proper security measures.
- Typosquatting: Attackers register domains with subtle typos of your subdomains to redirect traffic.
Once attackers gain control, they can:
- Redirect users to malicious websites: Phishing sites, malware distribution platforms, or spam pages.
- Steal sensitive data: Login credentials, financial information, or customer data.
- Launch further attacks: Use your subdomain as a launching point for attacks on your internal systems.
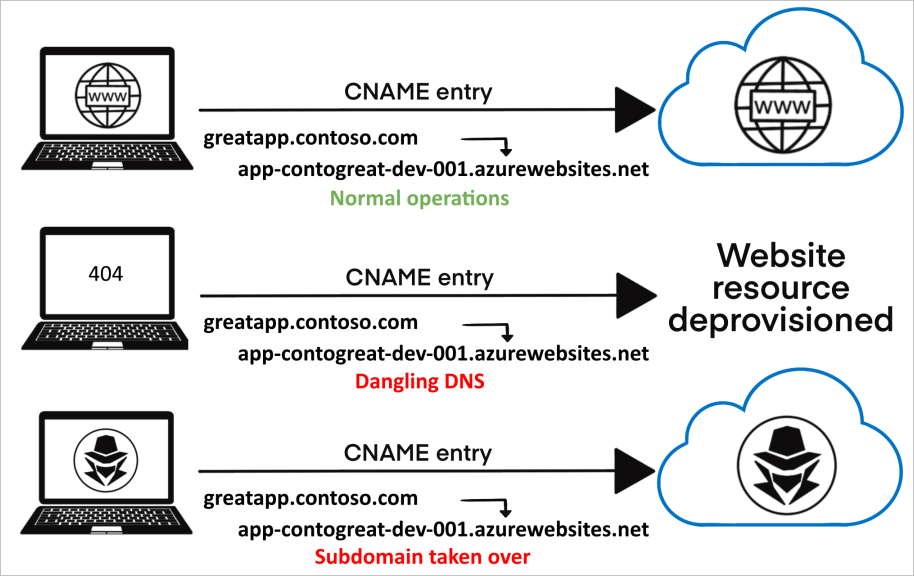
Impact of Subdomain Takeover
The consequences of a subdomain takeover can be far-reaching:
- Data Breaches: Attackers can steal sensitive user information like login credentials, financial details, or personal data.
- Reputational Damage: Malicious content displayed on a compromised subdomain can erode user trust and brand image.
- Further Attacks: The compromised subdomain can become a launchpad for attacks on your main domain or other systems.
Real-World Examples
Several high-profile subdomain takeover have highlighted the importance of vigilance and proper configuration:
- GitHub Pages: Developers often use custom domains with GitHub Pages. If a GitHub repository is deleted but the DNS record remains, an attacker can create a new repository with the same name and serve malicious content.
- Amazon S3 Buckets: If a DNS record points to an S3 bucket that’s deleted, an attacker can claim the bucket name and take over the subdomain.
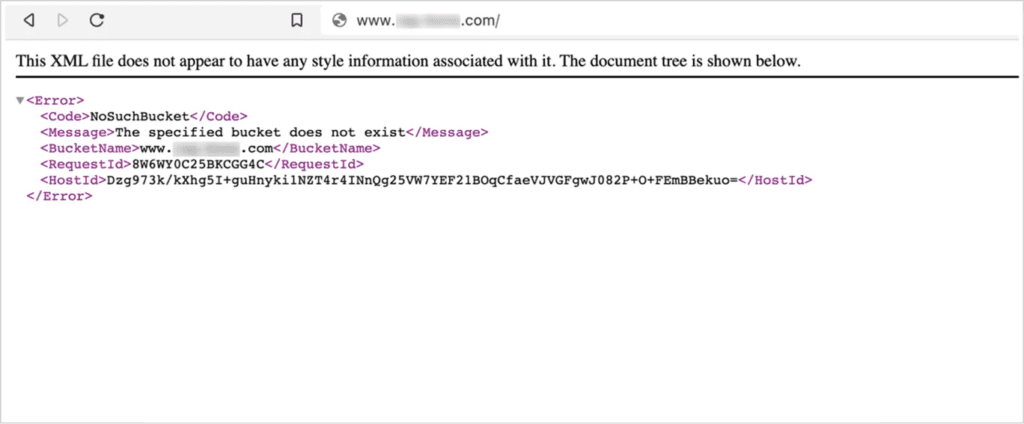
Top Strategies to Mitigate Subdomain Takeover
Proactive defence is key to preventing subdomain takeover. Here are some crucial strategies:
1. Regular DNS Record Audits:
- Frequency: Conduct DNS record audits at least quarterly, with more frequent checks for critical domains or those undergoing frequent changes.
- Scope: Review all DNS records, including CNAMEs, A records, TXT records, and MX records.
- Focus: Look for unused records, outdated entries, and records pointing to unauthorised destinations. Remove unused records and update outdated ones.
- Tools: Utilise DNS management tools or scripts to automate the process and identify inconsistencies.
2. Implement Domain Monitoring Tools:
- Choose the right tool: Select a tool that offers continuous threat exposure management, vulnerability scanning, and alerts for suspicious activity.
- Monitor key metrics: Track changes in DNS records, new subdomain registrations, and unauthorised access attempts.
- Set up alerts: Configure real-time alerts for any suspicious activity, allowing for immediate response.
- Consider penetration testing tools: Some tools offers penetration testing services to identify exploitable vulnerabilities in your subdomain configuration.
3. Enable Domain Registrar Locking:
- Activate locking features: Most registrars offer domain locking, which prevents unauthorised modifications to your DNS settings.
- Enable MFA: Add an extra layer of security by requiring Multi-Factor Authentication (MFA) for accessing your domain management account.
- Review access controls: Regularly review and restrict access to your domain management account to authorised personnel only.
4. Implement DNSSEC:
- Understand the benefits: DNSSEC adds cryptographic signatures to your DNS records, making them tamper-proof and preventing attackers from rerouting traffic.
- Evaluate your needs: Consider the complexity and potential benefits of DNSSEC implementation based on your domain’s criticality and technical expertise.
- Seek expert help: If necessary, consult with security professionals to ensure proper DNSSEC configuration and management.
5. Secure Third-Party Services:
- Inventory and assess: Identify all third-party services your subdomains rely on and assess their security posture.
- Enforce strong authentication: Implement strong password policies and MFA for all third-party service accounts.
- Monitor access and activity: Monitor user activity and access controls within these third-party services for suspicious behaviour.
6. Leverage Penetration Testing:
- Schedule regular testing: Conduct pentesting at least annually, with more frequent testing for critical domains or those undergoing significant changes.
- Focus on subdomains: Include subdomains in your penetration testing scope to identify vulnerabilities specific to their configuration.
- Remediate vulnerabilities: Address identified vulnerabilities promptly to prevent attackers from exploiting them.
7. Implement Content Security Policy (CSP):
- Define trusted sources: Configure your CSP to define authorized sources for scripts, images, and other content on your website.
- Block malicious content: This mitigates the risk of attackers injecting malicious scripts through compromised subdomains.
- Start gradually: Implement a basic CSP initially and gradually refine it as you gain more experience.
8. Stay Informed:
- Subscribe to security advisories: Follow reputable security organisations and subscribe to their advisories on emerging STO techniques and vulnerabilities.
- Attend security workshops: Participate in workshops and training sessions to stay updated on best practices and emerging threats.
- Engage with the security community: Connect with other security professionals to share knowledge and learn from their experiences.
The Power of Attack Surface Management in Subdomain Takeover Prevention
Attack Surface Management (ASM) platforms offer a comprehensive approach to securing your digital footprint by:
- Automated Discovery: ASM solutions automatically discover all your subdomains, including hidden and unused ones, providing a complete view of your attack surface.
- Continuous Monitoring: ASM continuously monitors your subdomains for changes, misconfigurations, and vulnerabilities, alerting you to potential SDO risks.
- Vulnerability Assessment: ASM tools can assess the security posture of your subdomains, identifying weak points that attackers could exploit.
- Prioritization and Remediation: ASM helps prioritize vulnerabilities based on their risk level, allowing you to focus on addressing the most critical issues first.
Also Read: Attack Surface Management: What is it? Why do you need it?
How Strobes Protects Your Website from Subdomain Takeover
Strobes, a leading provider of ASM solutions, empowers organisations to effectively protect their websites from subdomain takeover with its advanced features:
- Comprehensive Subdomain Discovery: Strobes uncovers all your subdomains, including those hidden or forgotten, ensuring complete visibility of your attack surface.
- Real-time Change Detection: Strobes continuously monitors your subdomains for unauthorised modifications, alerting you instantly to potential subdomain takeover attempts.
- Automated Vulnerability Scanning: Strobes identifies vulnerabilities in your subdomains, including misconfigured DNS records and weak authentication protocols.
- Prioritized Remediation: Strobes prioritizes vulnerabilities based on their potential impact, helping you focus on the most critical issues first.
- Expert Security Guidance: Strobes provides expert guidance and support throughout the remediation process, ensuring you effectively address vulnerabilities and prevent subdomain takeover.
Prevent Subdomain Takeover with Strobes’ Robust Protection
By proactively implementing these measures, you can significantly reduce the risk of subdomain takeover and protect your website, data, and brand reputation. At Strobes, we understand the complexities of cybersecurity and the importance of protecting your online assets.
Our team of experts can help you implement robust security measures to prevent subdomain takeover and other cyber threats.
Secure your digital assets with confidence—Get started with a Free Trial today!
Related Reads:
- Attack Surface Management: What is it? Why do you need it?
- Understanding External Attack Surface Management (EASM)
- Use Case: Rapid Identification and Escalation of a Critical Threat by Strobes ASM
- Integrating Attack Surface Management and Penetration Testing as a Service
- How CTEM Impacts Cyber Security Insurance Premiums?









