Did you know that the total number of data breaches more than tripled between 2013 and 2022?
These breaches exposed 2.6 billion personal records in the past two years alone and have worsened in 2023. From small startups to large companies, data and application security threats abound and are at an all-time high. These are expected to increase even more in the future, necessitating a solid and constantly improving system for application security posture management (ASPM) to deal with and prevent cybersecurity threats.
What is Application Security Posture Management?
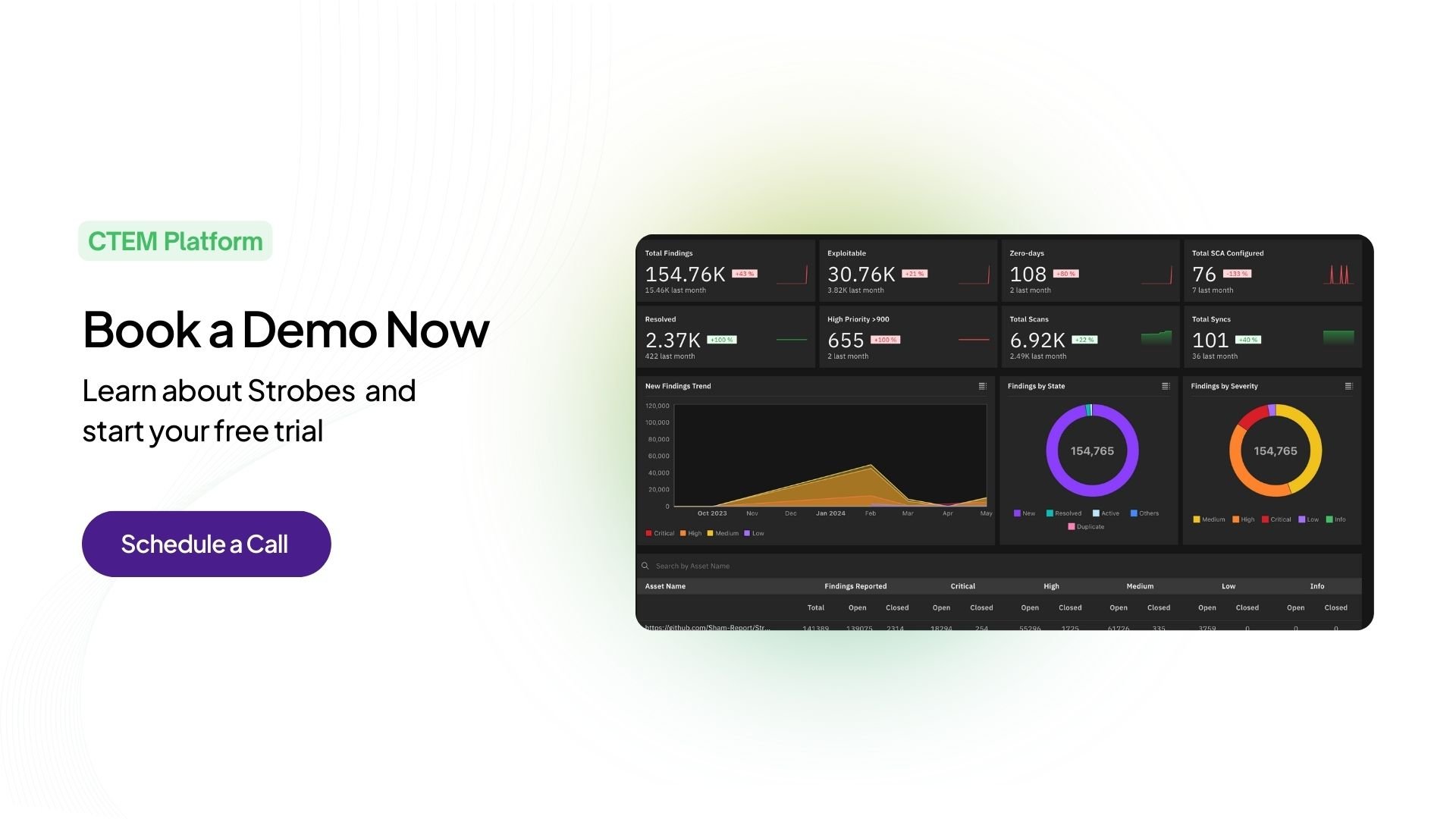
ASPM software is a security approach for applications that involves tools and methods that work together to continuously assess, manage, and improve the security of an organization’s applications. The ultimate goal is to make applications more resistant to cyberattacks and data breaches.
ASPM acts like a security radar, constantly scanning your application ecosystem to build a robust AppSec program. It espouses an ell-encompassing view of app security and utilizes task automation and risk prioritization for tackling critical issues first. ASPM streamlines workflows unifies security data for analysis, and aids in vulnerability detection throughout the development lifecycle. Ultimately, ASPM keeps your applications secure, compliant, and resistant to cyber threats.
Why Application Security Posture Management Matters
Do you think the largest tech companies’ data security protocols are infallible? Think again—even big tech stumbles on data security. Facebook was fined a whopping $886.6 million in 2021 for allegedly breaking EU data protection laws and also faced mass legal action over a data leak that compromised the personal information, including phone numbers, of about 530 million people.
In the Cambridge Analytica scandal, it was also sued for failing to protect the personal data of 87 million people which was used for advertising during elections.
In September 2021, spyware called Pegasus infected iPhones and other devices via a ‘zero-click exploit’, granting the spyware broad power over a user’s device. Additionally, in April 2022, a major data exposure occurred when over 540 million records about Facebook users were publicly exposed on Amazon’s cloud computing service.
Application Security Posture Management is critical and truly matters, from small startups to large conglomerates, and all business sizes in between. One can just imagine the severe losses in monetary terms and brand reputation that cyberattacks can cause.
Steps in Implementing a Successful ASPM Program
Here are some common steps in planning and implementing your company’s unique ASPM program. Your exact requirements may deviate a little from these, but generally, these fit quite well with many ASMP programs.
1. Chart Your Course
- Identify all applications within your IT environment.
- Rank and prioritize them based on how critical they are to your business and their potential security risks.
- Set clear, measurable objectives for your ASPM program (e.g., significantly reduce high-risk vulnerabilities).
2. Take Inventory and Assess
- Utilize an automated discovery tool to create a comprehensive application inventory.
- Conduct vulnerability assessments using a combination of the following:
- Static Application Security Testing (SAST): Analyzes code and code structure (source code or compiled) to find security vulnerabilities and weaknesses.
- Dynamic Application Security Testing (DAST): Vulnerability assessment through simulating attacks on a running application. It crawls through the application and probes for weaknesses such as SQL injection.
- Software Composition Analysis (SCA): Identifies vulnerabilities in third-party libraries and frameworks used within your application by scanning their components for known security issues.
3. Prioritize and Remediate
- Consolidate the findings from all assessments.
- Rank vulnerabilities based on their severity, how easily they can be exploited, and their impact on your business.
- Develop a remediation plan that assigns clear ownership and sets timelines for addressing vulnerabilities.
4. Embed Security in Development (DevSecOps)
- Integrate security testing tools throughout the software development lifecycle (SDLC) to identify and fix issues early.
- Train developers on secure coding practices to prevent vulnerabilities in the first place.
- Automate security checks within your CI/CD pipelines for continuous integration and delivery.
5. Continuous Monitoring and Improvement
- Implement ongoing vulnerability scanning to identify new threats as they emerge.
- Monitor application behavior to detect suspicious activity.
- Regularly review and update your security policies and procedures.
- Track progress towards your goals and adapt the program based on your findings.
Regular reporting on the program’s effectiveness to stakeholders ensures alignment and continued support for security initiatives. In addition, consider integrating other systems such as computerized maintenance management systems—the best CMMS systems help decrease downtime and prevent asset and equipment issues even before they occur.
Integrating ASPM with Cloud Providers
As almost all businesses have most of their applications on the cloud, ASPM integration with cloud apps has become the hottest trend. Dealing with cloud infrastructure presents its unique challenges, and the following practical tips are worth considering:
- API Integration: Integrate ASPM with cloud provider APIs for automated data exchange and security control enforcement.
- Centralized Logging and Monitoring: Aggregate logs from cloud resources and ASPM for comprehensive security monitoring.
- Leveraging Native Security Tools: Utilize built-in security features offered by your cloud provider (e.g., IAM for access control).
- Standardized Security Policies: Ensure consistent security policies are applied across your entire cloud environment.
- Streamlined Incident Response: Facilitate faster and more efficient response to security incidents in the cloud.
The Future of Application Security: A Data-Driven and Automated Approach
Application security is a never-ending process of detection, treatment, prevention, and cure. With AI and automation permeating all aspects of the tech industry, we can look forward to the following developments in the future:
Automated Vulnerability Detection and Prioritization
AI/ML can analyze vast amounts of security data to identify complex vulnerabilities and prioritize them based on real-time threat intelligence.
- Predictive Threat Modeling: Machine learning algorithms can analyze historical data to predict potential security threats and proactively take mitigation measures.
- Phishing and Malware Detection: AI can analyze user behavior and network traffic to identify and block sophisticated phishing attempts and malware attacks.
- Security Incident Response Automation: AI can assist in automating incident response workflows, enabling faster detection, containment, and remediation of security breaches.
ASPM Integration with DevSecOps for a More Secure Pipeline
- Automated Security Checks: ASPM can automate security checks within CI/CD pipelines, ensuring code adheres to security best practices before deployment.
- Shifting Security Left: Security testing tools are integrated throughout the development lifecycle (SDLC) using CI/CD pipelines. This allows vulnerabilities to be identified and fixed early in the development process.
- Standardized Security Policies: ASPM helps enforce consistent security policies across all development stages, reducing the risk of human error.
- Improved Communication and Collaboration: Integration fosters better communication between security and development teams, leading to a more collaborative and secure development process.
Cloud-Native ASPM Solutions
- Compliance Protocols: Ensuring automated regulatory compliance across a variety of industries via cloud platforms is an exciting development.
- Enhanced Scalability and Flexibility: Cloud-native ASPM solutions can scale automatically to accommodate the dynamic nature of cloud environments.
- Integration with Cloud Providers: Seamless integration with cloud platforms like AWS, Azure, or GCP allows for streamlined security management and automated workflows within the cloud environment.
- Improved Visibility and Control: Cloud-native ASPM provides centralized visibility and control over security posture across all cloud-based applications.
- Reduced Infrastructure Costs: Cloud-based solutions eliminate the need to manage and maintain on-premises security infrastructure, reducing costs.
With improved vigilance, subdomain takeovers through abandoned subdomains or typosquatting should be a thing of the past.
ASPM Adaptation to Evolving Security Threats
- Advanced Threat Detection: ASPM can adapt to new and evolving threats by leveraging threat intelligence feeds and continuously updating its detection mechanisms.
- Automated Security Workflows: Most security tasks will be automated, freeing up security professionals to focus on complex issues and strategic security planning.
- Automated Threat Hunting: ASPM can automate threat-hunting capabilities, allowing security teams to focus on strategic security initiatives.
- Continuous Security Monitoring and Improvement: Security will become an ongoing process of monitoring, analyzing data, and adapting security posture to address evolving threats.
- Continuous Security Posture Improvement: Machine learning can analyze security data to identify trends and proactively address potential security weaknesses before they can be exploited.
- Data-Driven Decisions: Security decisions will be based on real-time security data analysis using AI and machine learning, leading to more efficient and effective security strategies.
- Integration with Security Information and Event Management (SIEM): ASPM will seamlessly integrate with SIEM systems to provide a holistic view of security posture across the entire IT infrastructure.
- Risk-based Vulnerability Management: Unlike standalone vulnerability scanners, risk-based vulnerability management aggregates data from multiple sources, correlating with threat intelligence data and prioritizing issues automatically.
- Zero-Day Exploit Detection: AI and machine learning are used to analyze security data in real time to identify and respond to zero-day exploits even faster.
We hope your company’s ASPM software can incorporate many of our suggestions and industry best practices. Remember, ASPM is never-ending and is constantly needed to protect your data and business. If you are interested in more than cybersecurity, you may want to enroll in criminal justice degree online programs to help catch the bad guys too. All the best!