Like every year, we are releasing some research and analysis around our pen-testing in 2023. This article covers key penetration testing statistics, including what category of vulnerabilities we commonly report across hundreds of customers, and how we reduce compliance times and turnaround time when reporting critical vulnerabilities.
In a different article, we will also share some research on how our red teaming and app sec teams found clever ways to exploit vulnerabilities and provide strong value to our customers.
Our exploration begins by charting the trajectory of assessment volumes, offering a panoramic view of how different sectors and geographic locations grapple with the ever-present specter of cyber threats. As we dive deeper, we confront the fading allure of low-hanging fruits — vulnerabilities that were once exploited with ease — and examine the reasons behind their gradual decline.
Complementing our qualitative analysis, we present compelling statistical evidence that substantiates the paradigm shift in cybersecurity.

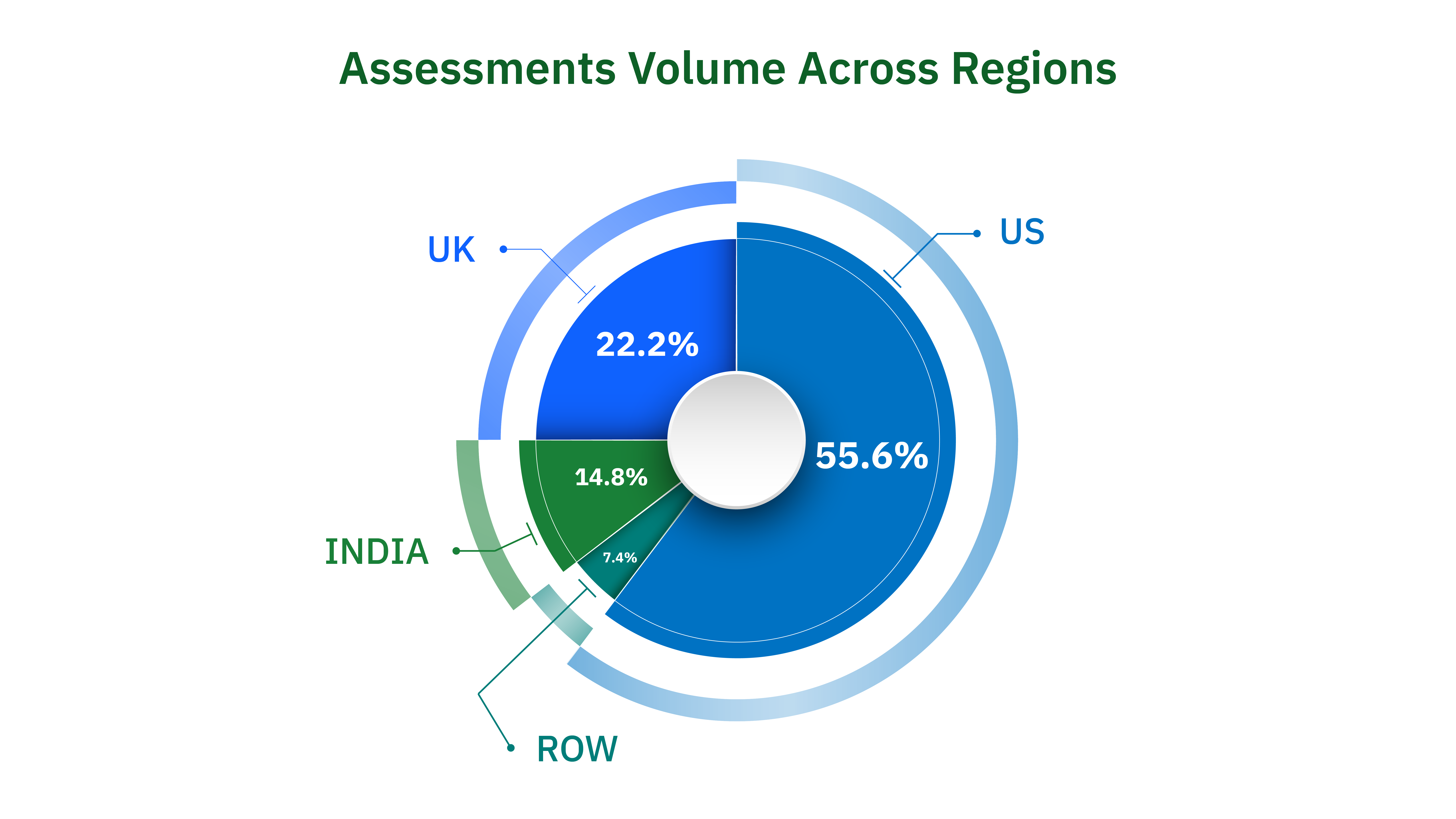
Assessments Volumes Across Industries and Regions
In 2023, we have worked with well over 150 customers, starting from startups to enterprises with over 10,000 employees. Again, these customers fall under different industries like Internet, Banking, Fintech, E-commerce, AI, Blockchain and more. We have seen some crazy trends in industries like banking, financial services, and AI.
Banking & Finance was leading from the front in terms of volume for pen-testing, especially in markets like the US, Europe, and India. India, driven by strict RBI regulations, showed strong penetration testing statistics, with companies required to conduct regular pentests. Even businesses registered outside India but looking to operate there had to meet these testing requirements consistently.
From a European standpoint, the GDPR data policies are still going strong, and we see a similar trend from them, more and more companies want to perform pen-testing.
Here is the volume of assessments across industries, assessments include IP or application testing:
The Slow Death of Low-Hanging Fruits
In the rapidly evolving world of cybersecurity, the trends and vulnerabilities witnessed in penetration testing (pentesting) reflect the changing dynamics of web applications and their security postures.
As we analyse our data from 2023, a notable trend emerges: the gradual decline of traditional vulnerabilities like Cross-Site Scripting (XSS) and SQL Injection, contrasted by the rise in complex issues such as Privilege Escalations, Insecure Direct Object References (IDORs), Server-Side Request Forgery (SSRF), business logic errors, and Server-Side Template Injection (SSTI). This article delves into this shift, shedding light on the reasons behind it and its implications on the cybersecurity landscape.
The Declining Trend of Conventional Vulnerabilities
Historically, XSS and SQL Injection have been the ‘low-hanging fruits’ of web application vulnerabilities. Easy to identify and exploit, these vulnerabilities have been the bane of web applications for years. XSS, for instance, has been a prevalent issue, allowing attackers to inject malicious scripts into web pages viewed by other users.
SQL Injection, on the other hand, has enabled attackers to manipulate back-end databases through poorly designed web applications. However, our data indicates a significant downturn in these vulnerabilities. A key reason is the advancement in development frameworks and technologies. Modern frameworks like Next.js, React, and Django have built-in security features that effectively neutralise such threats.
For instance, React’s DOM sanitization automatically mitigates the risk of XSS attacks. Similarly, ORMs (Object-Relational Mapping) used in frameworks like Django provide a layer of protection against SQL Injection by handling data queries securely.
Also Read: CVE-2025-29927 – Understanding the Next.js Middleware Vulnerability
The Rise of Sophisticated Vulnerabilities
While the traditional vulnerabilities are on the decline, we are witnessing an uptick in more sophisticated security challenges. Privilege escalation attacks, which involve gaining unauthorised access to higher-level permissions, are becoming more common. These attacks exploit flaws in application logic or system configurations and are often harder to detect and prevent.
IDORs and SSRF present similar challenges. IDORs exploit the way web applications manage data, allowing attackers unauthorised access to data belonging to other users. SSRF attacks trick a server into performing requests on behalf of the attacker, potentially leading to sensitive data exposure.
Business logic errors, often overlooked in automated testing, are becoming a significant threat. These errors arise from flawed application logic and can lead to unauthorised actions or data exposure. SSTI, meanwhile, targets the way web applications process templates, enabling attackers to inject malicious code into a server-side template, leading to data exposure or server compromise.
The Role of Modern DevSecOps Practices
The shift in the vulnerability landscape is also attributable to modern development practices. Applications developed within the last five years, particularly those using newer frameworks and technologies, are less prone to traditional vulnerabilities. These applications are designed with security as a core principle, incorporating secure coding practices from the outset.
Frameworks like Next.js and React enforce secure defaults and encourage patterns that reduce the risk of common vulnerabilities. Additionally, the adoption of DevSecOps practices, where security is integrated into the development life cycle, has played a crucial role in enhancing application security.
Also Read: Open Source Security: How Strobes Integrates Security into Your Dev Workflow
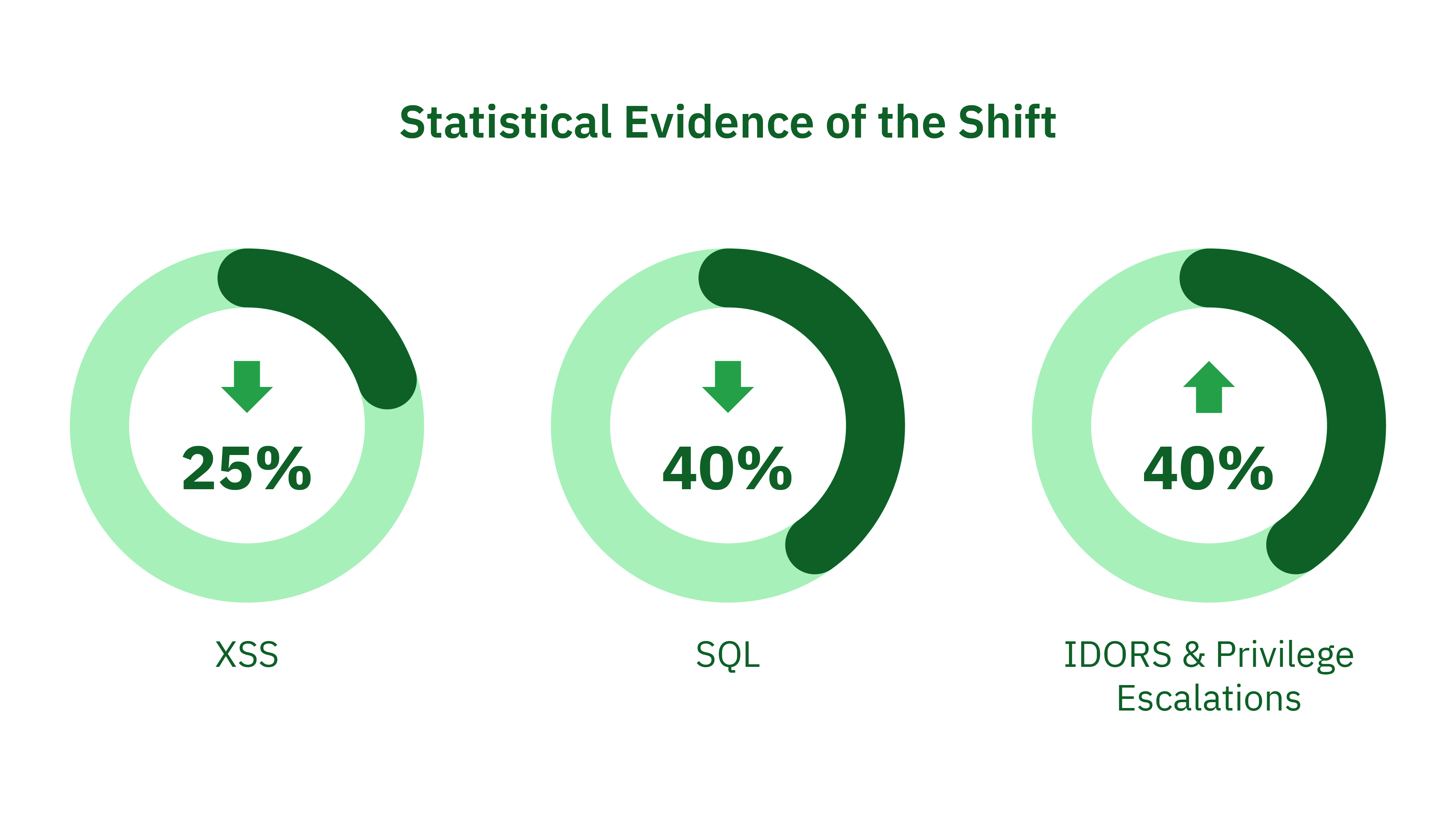
Penetration Testing Statistical Evidence of the Shift:
To substantiate these observations, let’s turn to some statistics. According to our data, XSS vulnerabilities have seen a reduction of approximately 25% in modern web applications compared to those developed five years ago. Similarly, SQL Injection vulnerabilities have decreased by around 40% in newer applications. On the other hand, issues like Privilege Escalations and IDORs have seen an increase of about 40% in the same period.
A Statistical Deep Dive into how Strobes Pentesting has Enhanced Security Compliance and Reporting
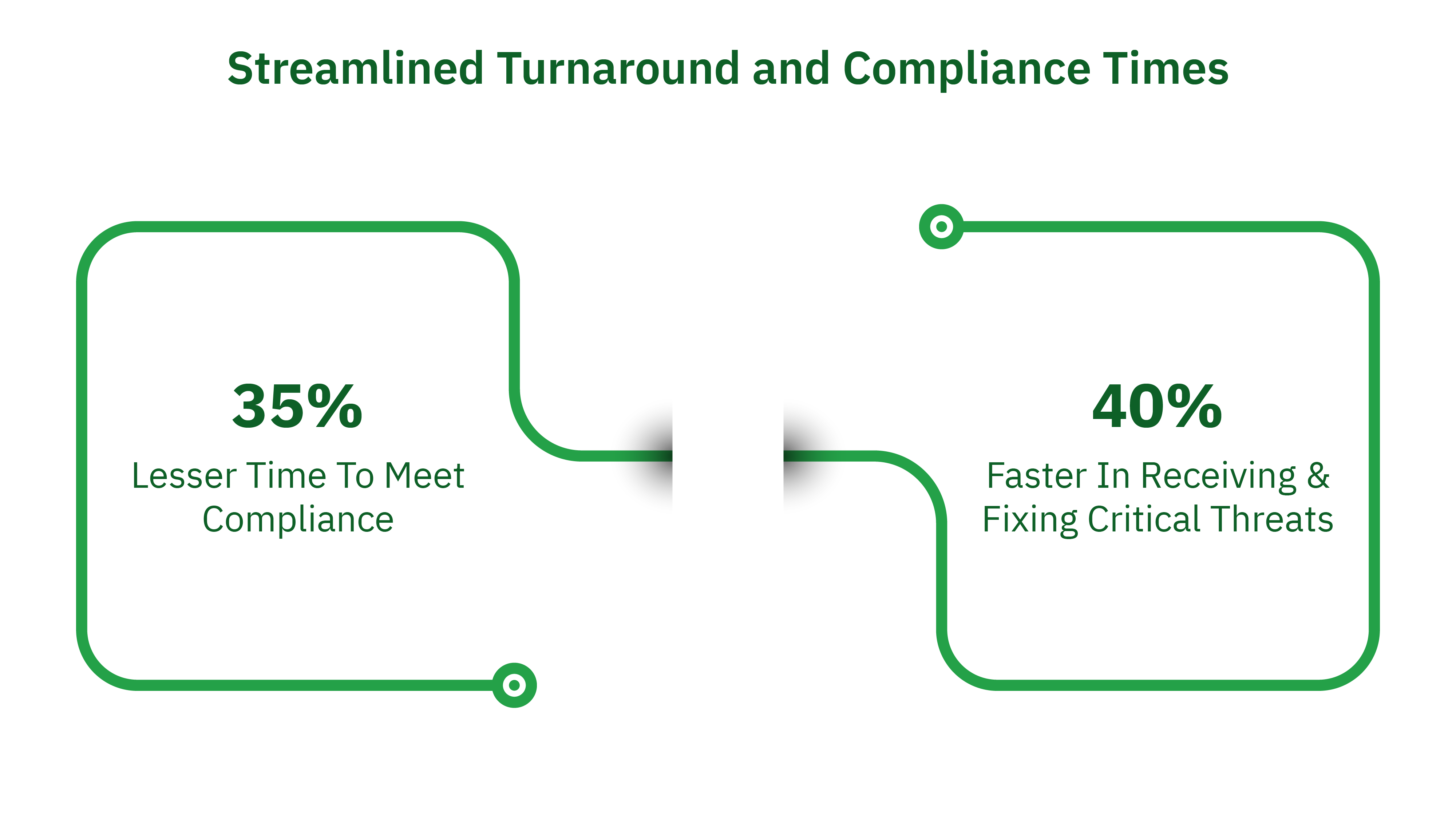
Streamlined Turnaround and Compliance Times
The agility of Strobes PTaaS is evident in its turnaround times. Over the past year, our platform and team have facilitated a 40% reduction in the time-to-remediation for critical vulnerabilities, a benchmark that significantly outpaces the industry average. By implementing integrated workflows and prioritised issue tracking, customers have reported a 35% improvement in their time-to-compliance, ensuring they meet regulatory standards swiftly without compromising on thoroughness.
For example, one of the customers using our Strobes PTaaS platform requested an urgent application pen-test ahead of a critical audit. The audit was time-sensitive and could have delayed their deal with a client. Strobes delivered the pentest report within 48 hours of starting the test, without compromising on quality or coverage. Our penetration testing statistics reflect how often we meet fast turnaround needs like this while maintaining depth and accuracy.
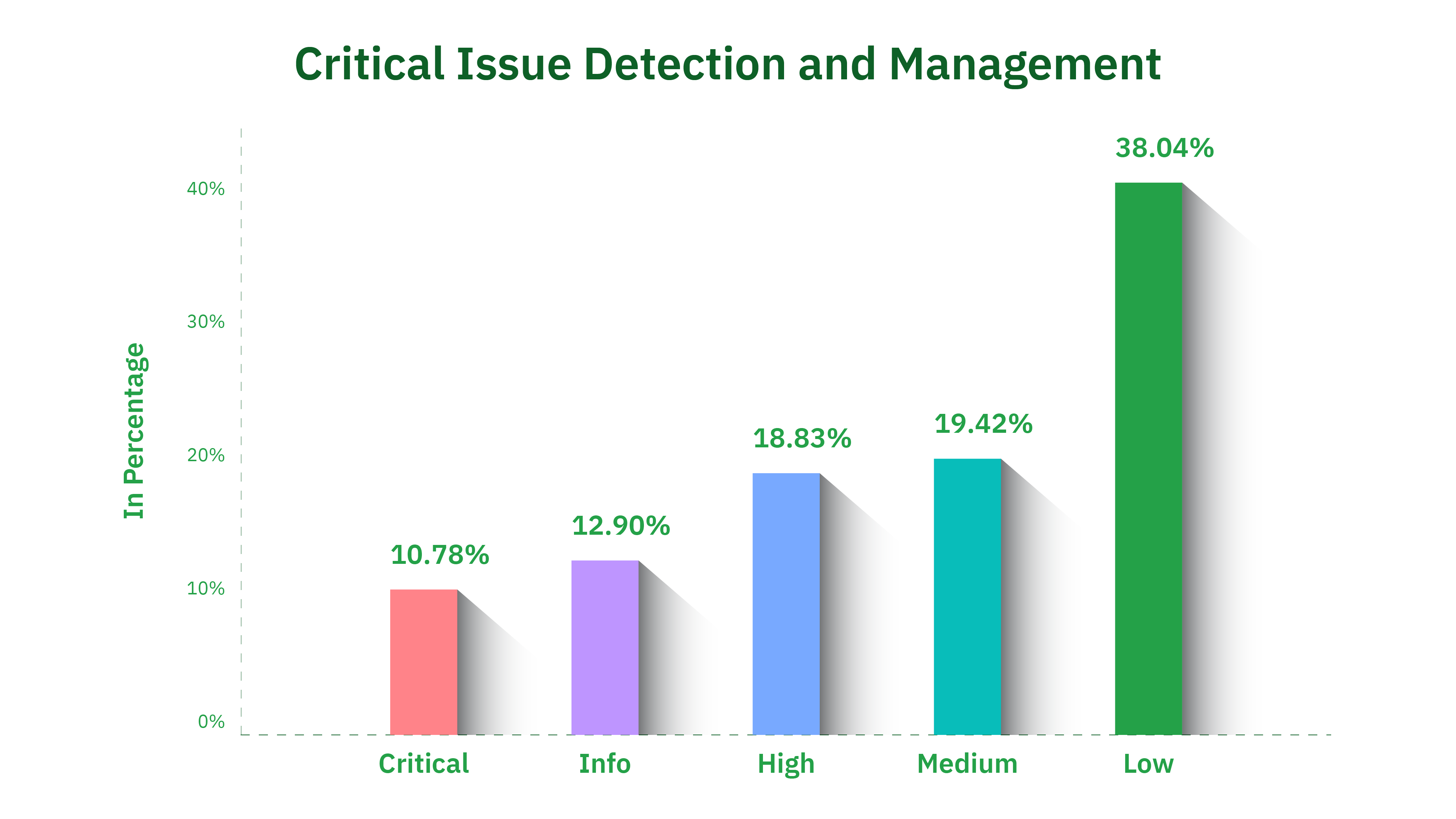
Critical Issue Detection and Management
Critical issue detection is at the heart of Strobes PTaaS’s efficacy. In 2023, our team identified and helped remediate of over 700 critical vulnerabilities across applications, networks and the cloud. The critical vulnerabilities are really critical and could have allowed a bad actor to compromise the customer’s infrastructure or even exfiltrate PII information.
Industry-Specific Vulnerability Discovery
Our approach is tailored and nuanced, cognizant of the unique challenges each industry faces:
- Banking and Finance: In the banking sector, we reported a 30% incidence rate of payment tampering and rounding off issues, significantly higher than the industry average. Our proactive pentesting methodologies have helped secure transactional interfaces, safeguarding millions in fiscal assets.
- Fintech: Fintech firms benefited from our targeted test cases, where we discovered critical API vulnerabilities at a rate of 15% wherein we discovered unauthorized API calls, business logical issues and more.
- Blockchain Companies: For blockchain entities, smart contract vulnerabilities were a focus, with Strobes PTaaS identifying critical flaws that could have led to significant financial losses, at a rate 15% higher than seen via traditional security measures.
The Comparative Edge in Diverse Industries
Further to the aforementioned industries, our pentesting services have made significant inroads in other sectors:
- Healthcare: In healthcare, we’ve reduced the average detection time for HIPAA non-compliance issues by 50%, ensuring customers fix vulnerabilities in time and always are in compliance
- E-Commerce: E-commerce platforms saw a 20% improvement in securing customer data, with Strobes PTaaS identifying critical checkout flaws that could have led to massive data breaches.
How Our Platform Is Beating Traditional Practices & Increasing Customer Satisfaction?
Strobes’ approach to Pentesting as a Service (PTaaS) is transforming traditional penetration testing practices, enhancing customer satisfaction through several innovative features. Here’s an exploration of how Strobes is achieving this:
- Vulnerability Tracking and Prioritization: Unlike traditional penetration testing, which can be sporadic and inconsistent, Strobes provides continuous vulnerability tracking. This means that vulnerabilities are not only identified but also prioritized based on their severity. This helps customers focus their attention and resources on the most critical issues first, ensuring that the most damaging vulnerabilities are remediated in a timely manner.
- Workflow Integration with Jira and Slack: Strobes integrates with popular project management and communication tools like Jira and Slack. This streamlines the workflow for developers and security teams by enabling them to receive and manage vulnerability reports within the tools they are already using. Such integration facilitates quicker response times, better team coordination, and smoother remediation processes, all of which contribute to increased customer satisfaction.
- Real-Time Collaboration with Pentesters: PTaaS offers a collaborative Software as a Service (SaaS) portal that allows for direct engagement with the expert pentesting team. This feature ensures that any issues can be discussed and addressed in real-time, fostering a more interactive and responsive pentesting process. It also allows for immediate action on vulnerabilities, reducing the window of risk and enhancing the overall security posture.
- Certified Ethical Hackers and Advanced Reporting: Strobes employs certified ethical hackers with prestigious certifications like CREST, OSCP, CISSP, and CEH, ensuring that the pentesting is conducted by experts. Furthermore, Strobes provides detailed reports tailored to various stakeholders, including technical reports for IT staff and executive summary reports for non-technical stakeholders, ensuring that everyone involved has the relevant information they need.
- Customisation and Scalability: The platform allows for a high degree of customisation to meet specific business requirements and can easily scale to handle larger scopes or multiple tests, thanks to its automated nature and platform-based delivery model. This flexibility is key to providing a service that can adapt to the unique needs of each customer, thus improving satisfaction.
- Cost Efficiency and Speed: Strobes’ PTaaS simplifies pricing with transparent, goal-oriented models, which is a departure from the unpredictable pricing of traditional penetration testing. The use of automated tools also means that vulnerabilities are scanned and identified swiftly, enabling faster remediation and contributing to overall cost savings.
The picture is clear. Strobes PTaaS is not just another cybersecurity platform; it’s a strategic partner in the cybersecurity ecosystem. By delivering tailored solutions, reducing remediation times, and enhancing compliance efficiency, we empower businesses to stay ahead of security threats.
Our penetration testing statistics from 2023 back this up, showing how our approach improves detection, reporting, and overall security outcomes across industries. Request a demo to see how Strobes can strengthen your security program.
Related Reads:
- Penetration Testing as a Service (PTaaS): The Future of Agile Security
- Strobes 2023 Pentesting Recap: Trends, Stats, and How PTaaS is Transforming Cybersecurity
- Traditional Vs Modern Penetration Testing (PTaaS): Choosing the Right Approach for Your Security Needs
- How Strobes Penetration Testing Supports Compliance Audits and Assessments
- Why Penetration Testing Is Important: Enhancing Security & Reducing Cyber Risks
- 3 Reasons Why Penetration Testing Is Needed and Why Traditional Pentesting Isn’t Working for You