2023 has seen the AI boom with LLM models taking all over the internet and thousands of organizations fine-tuning it into their existing processes. Well, the cybersecurity world hasn’t been left behind either. Organizations are incorporating AI models into their anti-malware systems and leveraging extensive vulnerability data to streamline operations and minimize manual efforts. As we anticipate continued innovation in 2024, it’s crucial to acknowledge that hackers are also keeping pace with this rapid evolution, emphasizing the ongoing need for vigilance and adaptive security measures. In this context, it becomes imperative to anticipate the top cybersecurity trends that will shape the narrative in 2024.
Here is an abridged version of the top 6 cybersecurity trends to expect in 2024:
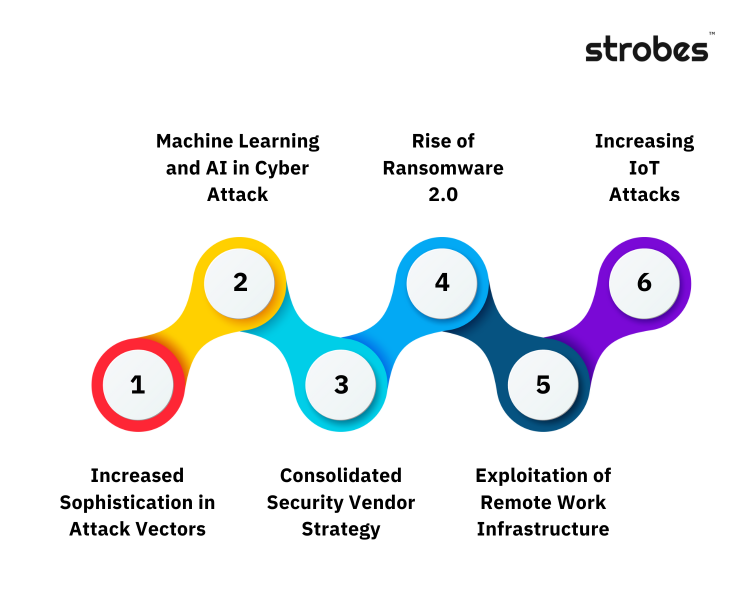
- Increased Sophistication in Attack Vectors – From advanced phishing schemes to polymorphic malware, the breadth and depth of attack vectors are expanding with organizations’ growing digital footprint.
- Machine Learning and AI in Cyber Attack – Understanding the dual role of ML and AI is crucial. CISOs and CIOs must strike a delicate balance by integrating these technologies into their defense & offense strategies while remaining vigilant to potential adversarial use.
- Consolidated Security Vendor Strategy– A Gartner survey shows that 75% of organizations are pursuing a security vendor consolidation strategy. Several organizations are actively exploring the adoption of vendor consolidation as a positive step toward improving their overall security posture.
- Rise of Ransomware 2.0– The era of Ransomware 2.0 demands a paradigm shift in defense mechanisms. Cybercriminals are not just encrypting data for extortion; they are exfiltrating sensitive information, adding a layer of complexity to the crisis.
- Exploitation of Remote Work Infrastructure– Remote workers are the primary target of criminals as cyberattacks have risen 238% since the beginning of the pandemic.
- Increasing IoT Attacks– With the proliferation of diverse IoT devices, ranging from smart home gadgets, and connected vehicles to critical industrial systems, the importance of IoT security is only going to increase.
Let’s take a closer look at the intricacies of each trend-
1. Increased Sophistication in Attack Vectors
We’ve observed a notable escalation in the complexity of attack vectors. Cybercriminals are no longer just exploiting straightforward vulnerabilities; they are now crafting multifaceted attack strategies that often combine social engineering with advanced technical exploits.
- Endpoint Attacks: The expansion of endpoint attack surfaces has been a critical concern, with threats including ransomware, phishing scams, zero-day exploits, fileless malware, and Denial-of-Service (DoS) attacks. These attacks exploit vulnerabilities within privileged computers, smartphones, and IoT devices.
- Ransomware Attacks: Ransomware continues to target critical infrastructure and major companies, with examples like the attacks on San Francisco’s Bay Area Rapid Transit, Reddit, Dole Food Company, the United States Marshals Service, the City of Oregon, and Enzo Biochem. These incidents highlight the multifaceted nature of modern ransomware attacks, combining technical exploits with social engineering tactics.
- Supply Chain Attack on 3CX: The North Korean regime-associated actors compromised the 3CX PABX platform in a sophisticated supply chain attack. They inserted malicious code into 3CX endpoint clients, downloaded as updates, using stealthy steganography to encode a payload in an image file. This kind of attack shows the innovative methods threat actors use to exploit network access and distribute malware.
- ESXi & Linux Ransomware: Ransomware groups have expanded their targets to include Linux systems and VMware ESXi servers. This shift reflects the adaptability of cybercriminals to target critical services and sensitive data across different platforms.
- Identity-Based Attacks: With the growth in digital identities, identity-based attacks exploiting weaknesses in user identities, credentials, and authentication processes have risen. These attacks aim to gain unauthorized access to sensitive data and systems and include threats like phishing, credential stuffing, identity theft, and attacks on SSO systems and MFA protocols.
- Exploitation of Microsoft Services: An espionage-motivated actor, STORM-0558, exploited components of Microsoft permissions, including broad application scopes and a stolen signing key, to mint session tokens to affected organizations’ Microsoft services. This attack demonstrates the intricacies involved in targeting digital trust and authentication mechanisms.
- Cloud-Based Attacks: Cloud environments have been targeted to exploit weak access controls and infiltrate cloud repositories. These attacks compromise sensitive data and disrupt operations. A notable rise in cloud infostealers has been observed, where financially motivated tools steal data from vulnerable or misconfigured cloud services.
- The Exploitation of Cloud Storage Services: The Cl0p ransomware group exploited a zero-day vulnerability in the MOVEit file transfer server application, targeting cloud storage services and compromising the data of millions of individuals. This marked a significant shift in ransomware tactics, from focusing on endpoints to directly targeting cloud storage services.
- Rise of Cloud Infostealers: Tools like AlienFox and Legion, distributed via Telegram channels, target credentials from exposed cloud services. These tools demonstrate the evolving nature of attacks, now focusing more on harvesting credentials and exploiting cloud vulnerabilities.
2. Machine Learning and AI in Cyber Attacks
The advent of Large Language Models (LLMs) has marked a pivotal shift in how threats are both constructed and combated. These sophisticated AI tools are not just being leveraged for defensive cybersecurity strategies but are increasingly being exploited by attackers, including those with minimal technical expertise.
Exploitation by Script Kiddies, A notable trend is the rise of ‘script kiddies’ utilizing LLMs to craft complex exploit scripts. These individuals, traditionally with limited hacking skills, are now empowered to execute advanced cyber attacks. By inputting basic prompts into LLMs, they can generate intricate code, which would have previously required deep technical knowledge.
Prompt Injection Tactics, More concerning is the emergence of prompt injection techniques. Attackers are manipulating LLMs to bypass their built-in safeguards designed to prevent the generation of malicious content. By cleverly crafting prompts, they can deceive these models into producing exploit codes or strategies that align with malicious intents.

3. Consolidated Security Vendor Strategy
Cybersecurity is becoming increasingly complex day by day. With the attack surface continuously growing, vendor sprawl poses challenges such as increased management complexity, integration issues, and potential gaps in security coverage for organizations.
The sheer volume and complexity of threats in an organization’s digital ecosystem have rendered it impractical to address each identified threat individually. As a strategic response, it is strongly advised that enterprises transition to a continuous approach to continuous threat management. This approach entails broadening the scope of threat assessments to encompass integrated supply chains, recognizing the interconnected nature of modern business operations.
While cost-cutting should not be the primary driver for a consolidated cybersecurity strategy, it however leads to an overall growth in the organizational cybersecurity posture-
- Unified Security Strategy
- Simplified Management
- Improved Visibility
- Reduced Complexity
- Streamlined Communication
- Consistent Policy Enforcement
- Enhanced Incident Response
- Economies of Scale
4. Rise of Ransomware 2.0
The prevalence of ransomware has taken a more menacing turn. Beyond data encryption, threat actors are now engaging in data exfiltration, creating a dual-threat scenario: data lockdown and potential data breach.
- A report from Panda Security discusses the rise of double extortion in ransomware attacks. Traditionally, ransomware focused on single extortion by encrypting an organization’s data and demanding a ransom for a decryption key. However, ransomware groups have now evolved to exfiltrating victims’ data to an offsite location before encryption. Then, they threaten to leak or publish the data if a ransom isn’t received, thereby creating a double extortion scenario. This approach is increasingly leveraged as it proves to be more profitable. – Panda Security
- Trend Micro’s analysis for 2023 highlights a focus on data extortion in ransomware trends. Groups like LAPSU$ have targeted major companies like Microsoft, Nvidia, Uber, and Rockstar Games, gaining prominence by extorting their victims and posting stolen data online when ransom demands are not met. This trend indicates that adversaries are finding more avenues to profit from their targets. Additionally, the stolen data is not only valuable to its rightful owners but also to other cybercriminals, making it an asset for monetization and sale on the dark web. This evolution suggests that ransomware groups are poised to become brokers in the underground industry, maximizing profit while minimizing exposure. – Trend Micro
- A report on Security Boulevard discusses how ransomware’s fundamental nature has shifted from encryption to data exfiltration, meaning traditional data backup and recovery practices are no longer sufficient protection. As ransomware organizations adopt “as-a-service” business models on the dark web, attackers of all levels can participate, and cybercriminals can purchase the entire ransomware infrastructure on the dark web. The analysis by the Flare research team reviewed thousands of double and triple extortion ransomware attacks, identifying trends such as changes to data extortion attacks over time, groups representing the most significant threats, and the industries most affected by these attacks. Ransomware groups are now part of a broader cybercrime ecosystem, including resources like initial access to corporate IT environments, credentials, cookies for SSO applications, and ready-made infrastructure for distribution. – Security Boulevard
5. Exploitation of Remote Work Infrastructure
As remote work becomes the norm, vulnerabilities in remote access technologies and collaboration tools have become prime targets. This trend underscores the need for robust security protocols in remote work setups.
- Citrix Vulnerability Exploitation The Cybersecurity and Infrastructure Security Agency (CISA) released advisories regarding the exploitation of a specific vulnerability, CVE-2023-3519, in Citrix’s NetScaler Application Delivery Controller (ADC) and NetScaler Gateway. This unauthenticated remote code execution vulnerability has been a target for implanting webshells by threat actors, demonstrating the vulnerabilities inherent in remote work technologies.
- LockBit 3.0 Ransomware Using Citrix Vulnerability Further emphasizing the risks, CISA also reported on the exploitation of another vulnerability, CVE-2023-4966, found in Citrix NetScaler ADC and Gateway appliances. This vulnerability was actively exploited as early as August 2023 by affiliates of LockBit 3.0 ransomware, which highlights the sophistication of current cyber threats. These threat actors were able to bypass multi-factor authentication and hijack legitimate user sessions, showcasing a deep understanding of and capability to exploit remote work infrastructure vulnerabilities.
- Atlassian Confluence Vulnerability: Another instance noted by CISA involved the exploitation of a vulnerability in Atlassian Confluence (CVE-2023-22515). CISA added this vulnerability to its Known Exploited Vulnerabilities Catalog due to active exploitation. The ease of exploitation and the widespread use of Confluence in remote work setups underline the heightened risk of cyber attacks in remote and hybrid work environments.
6. Increase in IoT Attacks
As per the mid-year update of the 2023 SonicWall Cyber Threat Report, there was a total of 77.9 million attacks, marking a notable rise from the 57 million attacks recorded in the corresponding period of 2022. Scary right?
With the extensive rise in IoT devices, the focus on IoT security protocols is also predicted to increase significantly. Anticipated trends include the widespread adoption of more robust authentication protocols, the integration of advanced encryption techniques, and the implementation of stringent access controls. Additionally, there is a growing emphasis on regular software updates and patch management to address vulnerabilities promptly. Collaborative efforts within the industry are expected to yield standardized security frameworks tailored for diverse IoT applications, fostering a more resilient and secure environment for the interconnected web of devices. This ensures that data transmitted between IoT devices remains confidential and protected from potential breaches.
- Edge Computing for Enhanced Security:
The integration of edge computing within IoT architectures will contribute to improved security. Edge devices can preprocess and filter data locally, reducing the volume of sensitive information transmitted over networks and minimizing the attack surface for potential cyber threats.
- Security-by-Design Principles:
There will be a growing emphasis on integrating security into the design and development phases of IoT devices. Following security-by-design principles ensures that security considerations are a fundamental aspect of the device’s architecture, reducing vulnerabilities from the outset.
Old habits die hard!
The age-old saying “Old Habits Die Hard” resonates as a poignant reminder that despite the rapid evolution of threats and the emergence of cutting-edge security measures, ingrained practices and vulnerabilities persist. Whether it be the enduring susceptibility to identity-based attacks, the lag in adopting comprehensive Zero Trust Security Models, or the challenges in securing remote work infrastructure, organizations often grapple with breaking away from traditional paradigms. As we head into 2024, overcoming these entrenched habits demands a concerted effort to embrace innovative strategies, integrate security into every facet of operations, and foster a culture of continuous adaptation to effectively mitigate the ever-changing cybersecurity world.