There are no cybersecurity incidents that occur without a cause. Attackers look at the simplest way into your systems, often using weaknesses in what is referred to as the attack surface. The attack surface is all the possible ways in which attackers might have unauthorized access or do damage to the digital assets of your organization.
As organizations continue to adopt more cloud-based environments, integrate third-party tools, and support remote work, their attack surfaces are expanding. This increase in exposure is reflected in recent reports, with the average cost of a data breach reaching $4.2 million in 2023, highlighting the significant financial impact of security failures.
In this blog, we will explore the various types of attack surfaces internal, external, digital, physical, cloud, and human, and the threats posed by each. We will also explain how proper management of such surfaces can greatly minimize your exposure to cyber threats as an organization.
What is an Attack Surface?
An attack surface is the total of all potential locations (systems, applications, devices, users, and processes) that an attacker may attempt to exploit in order to compromise your environment. Here are the holes that the bad actors can use to take advantage of weaknesses.
You must know the distinction between Attack Surface and Attack Vector:
Attack Surface
An attack surface encompasses every potential entry point into your system or network that an attacker could exploit. These entry points could be physical or digital, existing across various layers of your organization’s technology stack. For example, it includes:
- Servers and workstations: Any device that connects to your network or stores sensitive information, including desktops, laptops, and cloud servers.
- Applications: Both internal and external apps that are part of your system, such as web applications, mobile apps, and third-party services you integrate.
- Endpoints: Devices that access your network, such as smartphones, tablets, printers, and IoT (Internet of Things) devices.
- Network infrastructure: Routers, switches, firewalls, and communication channels that allow data to flow across the system.
- Processes: The workflows or services that connect different parts of your IT environment, such as APIs, cloud services, and internal software.
- Users: Employees, contractors, partners, and customers who have access to your environment, and their methods of accessing systems, whether through VPNs, credentials, or other access points.
Attack Vector
An attack vector is the specific method or path that an attacker uses to exploit a weakness within the attack surface. It is the means through which the attacker gains access to your systems or sensitive data. Attack vectors are the tools, techniques, or strategies used by cybercriminals to carry out an attack after identifying a vulnerable point in your environment. Some common attack vectors include:
- Phishing emails: One of the most common attack vectors, where attackers impersonate legitimate entities to trick users into disclosing sensitive information, such as login credentials or financial data. These emails often contain malicious links or attachments that, when clicked, allow malware to be installed.
- Unpatched software: Attackers often exploiting vulnerabilities in outdated or unpatched software. If a security flaw in a piece of software (like an operating system or application) is discovered but not patched, it becomes a target for exploitation.
- Social engineering: Attackers manipulate individuals into revealing confidential information or performing actions that benefit the attacker, like transferring money or granting system access.
- Malware: Malicious software like viruses, worms, and ransomware, which are deployed to infiltrate systems, steal data, or disrupt normal operations.
- Brute force attacks: Attackers use automated tools to guess passwords by systematically attempting different combinations until they break into an account.
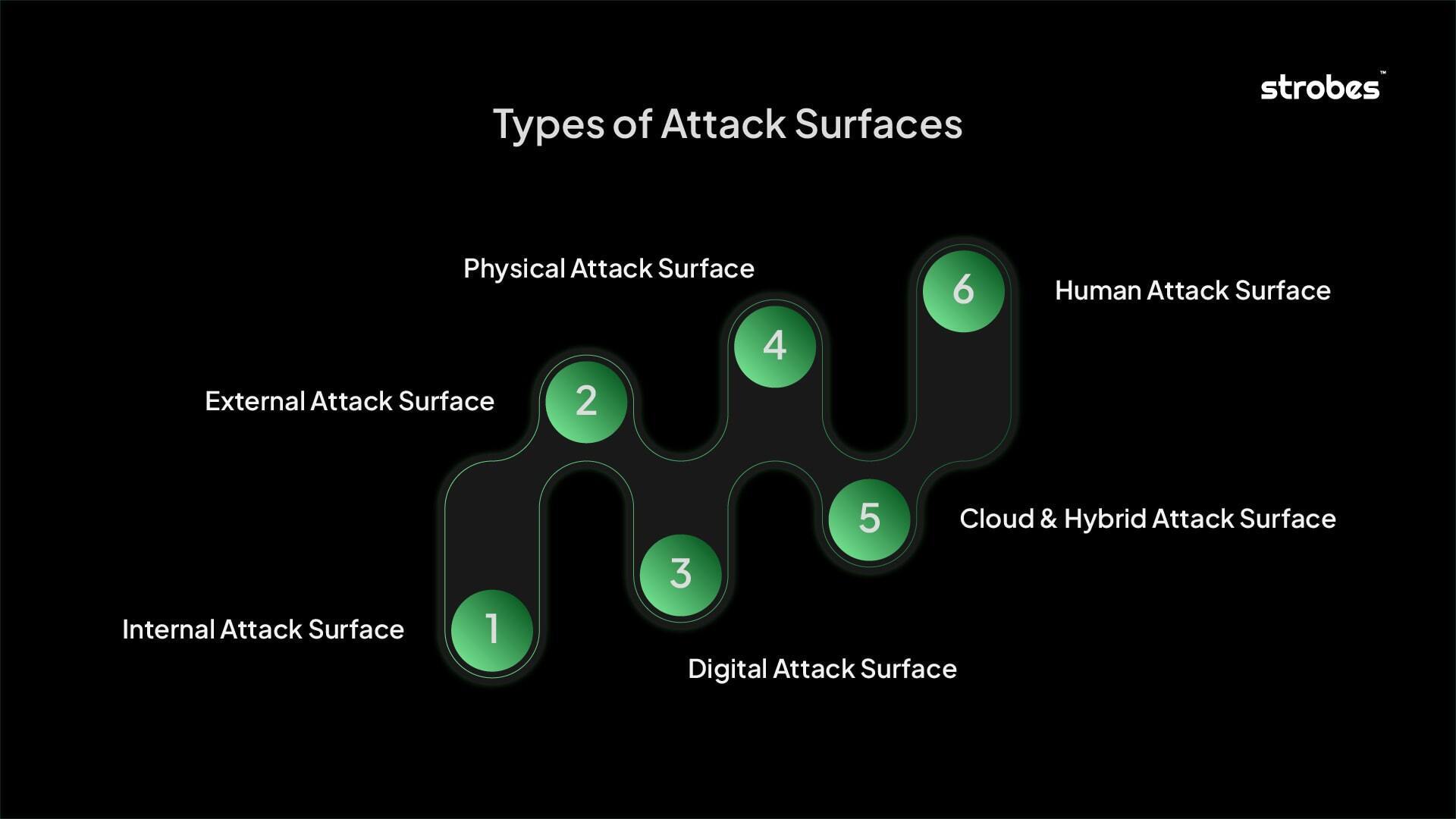
Exploring the Key Types of Attack Surfaces
1. Internal Attack Surface
Internal attack surface: the internal attack surface includes all systems, applications, and devices in the private network of your organization. These include:
- Servers, workstations, and internal applications.
- Final devices such as mobile devices, desktops and laptops.
- Resources and internal databases which are sensitive.
- Privileged user accounts that have high access to systems.
Common Risks
- Poorly configured access controls enable unauthorized system access.
- Systems are deliberately or inadvertently abused by their insiders (employees or contractors).
- Lateral movement of attackers who have already accessed.
2. External Attack Surface
The external attack surface makes reference to all systems and services that are open to the outside world, usually via the internet. Attackers like to attack it first.
Key Components
- External web applications, such as e-commerce applications and portal applications.
- APIs exposed to the internet.
- DNs configurations, networks, and external servers.
- Ports open to the internet.
Common Risks
- Flaws in cloud storage service configuration expose sensitive information.
- Unpatched Web applications, which are easily exploited by the attackers.
- And abandoned assets or shadow IT systems that remain open externally.
3. Digital Attack Surface
The digital attack surface is beyond the internal IT infrastructure and comprises all digital properties and third-party platforms related to your organization. These include:
- Social networks, blogs, and websites, as well as brand areas.
- SaaS systems and third party programs.
- Customer interaction platforms and marketing tools.
The threat actors usually use brand trust to deceive users, who end up falling into the trap of malicious links or revealing sensitive details.
4. Physical Attack Surface
The physical attack surface is defined as hardware and physical equipment that might be attacked by an attacker. These include:
- Data centres, servers, and networking equipment.
- IoT gadgets, printers, and routers in the grounds of the organization.
- Tablets, laptops, and mobile phones are used by employees.
Common Risks
- Devices with confidential information are stolen.
- Hacking into the system by destroying its physical equipment.
- Lack of physical space controls, such as server rooms or offices.
5. Cloud & Hybrid Attack Surface
With organizations moving more and more to the cloud, the cloud attack surface has maintained an increasing size and complexity. This includes:
- Cloud based applications, services, and workloads.
- Serverless functions, microservices, and containerized environments.
- IAM settings and API integrations.
Challenges
- Lack of proper configuration of cloud storage and published APIs.
- Unnecessarily permissive IAM roles.
- Absence of standard security policies in the hybrid cloud environment.
6. Human Attack Surface
The human attack surface involves all members of the organization and other people associated with the organization who may unwillingly or willingly pose a security risk. These include:
- Employees, contractors, and partners with system access.
- It is customers who use business applications and online portals.
Common Risks
- Credential or sensitive information is stolen by using phishing and social engineering tricks.
- Poor or faulty passwords, which can be easily cracked by the attacker.
- Poor security education results in dangerous behaviour.
Key Challenges in Managing Attack Surfaces
Managing and securing the various types of attack surface can be a complex task. Some key challenges include:
- Shadow IT: Employees adopting unauthorized tools or cloud services that increase the attack surface without being detected by IT.
- Constant Change: The introduction of new systems and applications, coupled with decommissioned systems, makes tracking and managing the attack surface challenging.
- Third-Party Risks: External vendors or partners with access to your systems or data introduce additional vulnerabilities.
- Limited Visibility: Without centralized visibility, it’s difficult to identify and manage all assets and vulnerabilities across internal, external, and cloud environments.
Benefits of Attack Surface Management (ASM)
- Comprehensive Visibility: A complete view of all assets, whether they’re in the cloud, on-premises, or with third parties.
- Risk Prioritization: By identifying the most critical assets, organizations can focus on the highest-risk exposures.
- Faster Response: Continuous monitoring and real-time detection allow for quicker action against vulnerabilities before they are exploited.
- Reduced Breach Impact: Proactively identifying and mitigating risks limits potential damage from cyberattacks.
Studies show that organizations with comprehensive ASM solutions experience a reduction in breach costs by up to 40%, thanks to faster identification and response times.
Strobes’ Approach to Attack Surface Risk
At Strobes, we take a proactive and comprehensive approach to attack surface management. Our platform helps organizations:
- Discover Assets Continuously: Identify every internal, external, and cloud asset in real-time, including shadow IT.
- Prioritize by Risk: Use AI-powered contextual insights for vulnerabilities prioritization based on real risk, not just severity.
- Integrate Seamlessly: Strobes integrates with over 120 tools to automate workflows and improve collaboration.
- Enable Continuous Monitoring: Our platform provides continuous monitoring to ensure you’re always aware of your attack surface and emerging risks.
Conclusion
As cybersecurity threats become increasingly complex, organizations need to understand and manage the different types of attack surfaces to mitigate risks effectively. Whether it’s internal networks, cloud infrastructure, digital assets, or human factors, each attack surface presents unique vulnerabilities that malicious actors can exploit.
Organizations need to implement strong protection by constantly scrutinizing, evaluating, and assigning priorities to vulnerabilities across all types of attack surfaces. Preemptively detecting and managing threats helps businesses become far less exposed to possible breaches and contain the effects of cyber threats.
At Strobes Security, we offer advanced solutions developed to simplify the management of the attack surface across both large and small organizations. Our attack surface management (ASM) platform provides real time asset discovery, automated risk based prioritization, and interoperability with other security tools to provide holistic protection against changing threat environments.
Enhance your defensive cyber position and protect your most valuable assets. Strobes ASM can help you start managing your attack surfaces today.
Book a free ASM trial with us today and see how our solution can transform the way your organization identifies and mitigates risks.
Related Reads:
- Attack Surface Management: What is it? Why do you need it?
- How to Tame Your Multi-Cloud Attack Surface with Pentesting
- Understanding External Attack Surface Management: Strobes EASM
- Integrating Attack Surface Management and Penetration Testing as a Service
- Solution: Strobes Attack Surface Management Solution