Your organization’s attack surface isn’t what it used to be. Cloud workloads, third-party vendors, and remote employees have expanded it far beyond traditional boundaries. Every day, new risks emerge, some visible and many hidden, making it harder to know where you truly stand.
Yet most vulnerability management programs still follow the same pattern: scan, patch, repeat. They generate long lists of issues but offer little clarity on what matters most. This leaves security leaders facing the same hard question from the board:
“Are we truly secure or just hoping we are?”
This is where Threat Exposure Management (TEM) makes a difference. It shifts focus from endless vulnerability lists to a clear, prioritized view of the exposures that could disrupt your business tomorrow.
In this guide, we’ll explore:
- What TEM means for security leaders
- A practical roadmap to put it in place
- The metrics and insights that matter at the executive level
- Common mistakes and how to avoid them
What Is Threat Exposure Management?

Threat Exposure Management (TEM) is a continuous process that helps organizations identify, monitor, prioritize, and remediate security exposures across their entire attack surface.
Unlike traditional vulnerability management, which often delivers long lists of issues without context, TEM helps security leaders focus on the exposures that matter most. It connects technical findings to real business risk and ensures teams act where it counts.
TEM brings together:
- Asset discovery, covering cloud, shadow IT, and third-party systems
- Continuous monitoring of external and internal attack surfaces
- Threat intelligence for actionable insights
- Risk-based prioritization to allocate resources effectively
- Validation of defenses through simulated attacks and penetration testing
This approach aligns with Gartner’s Continuous Threat Exposure Management (CTEM) model. CTEM promotes a proactive lifecycle where organizations move from periodic assessments to continuous risk management:
- Plan – Define scope and align with business priorities
- Monitor – Track exposures as they emerge
- Validate – Test defenses with real-world simulations
- Remediate – Address high-risk vulnerabilities first
- Respond – Report progress and adjust strategies as needed
For security leaders, threat exposure management provides the clarity and control needed to answer a critical boardroom question: “Where are we exposed, and how are we reducing that risk?”
“Download the Security Leader’s Checklist: Your 5-Stage Plan for Threat Exposure Management Success”
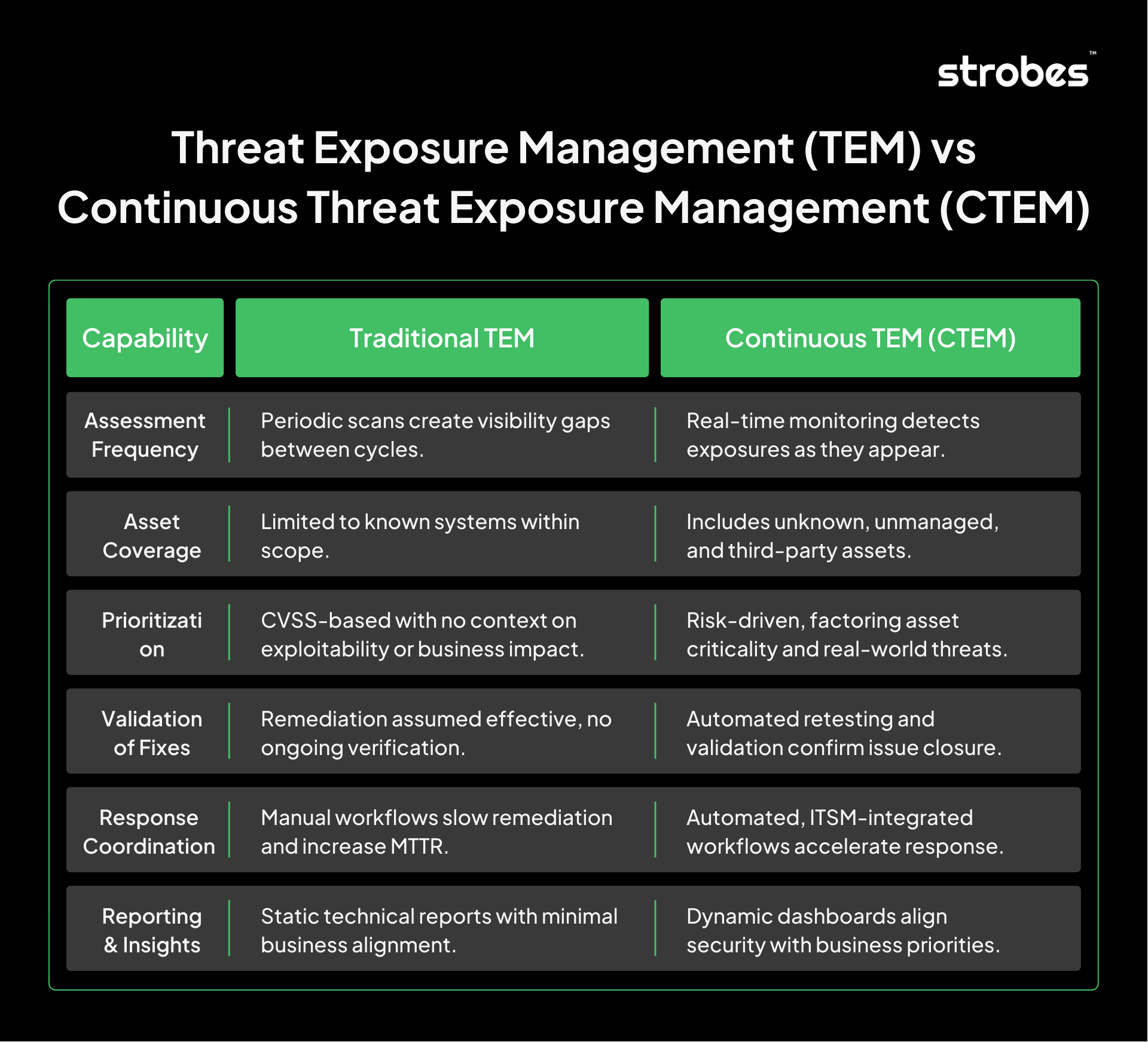
Threat Exposure Management (TEM) vs Continuous Threat Exposure Management (CTEM)
Traditional Threat Exposure Management has served as a starting point for many organizations, offering visibility and structure in addressing vulnerabilities. But with rapidly expanding attack surfaces, hybrid infrastructures, and real-time threats, TEM’s periodic approach leaves critical gaps.
This is why Gartner recommends shifting to Continuous Threat Exposure Management (CTEM). CTEM builds on TEM but adds the capabilities enterprises need to keep pace with today’s dynamic environments. With Strobes, organizations can accelerate this transition by adopting a unified platform designed for continuous discovery, validation, and risk-driven remediation.
The Stages of Threat Exposure Management Success
A successful Threat Exposure Management program isn’t built overnight. Security leaders need a structured, step-by-step approach that aligns technical activities with business objectives.
This roadmap provides a clear framework for implementing threat exposure management at scale:
Stage 1: Plan with Context
- Start by mapping all digital assets across cloud, on-premises, and third-party environments. This includes shadow IT and vendor-managed systems that often remain outside traditional visibility.
- Classify assets based on business criticality to identify those that require the highest level of protection.
- Establish governance models that align security priorities with operational requirements and regulatory obligations.
Strobes enables this stage with continuous asset discovery and context-aware classification, helping teams create an accurate and prioritized asset inventory.
Stage 2: Monitor Continuously
- Implement ongoing attack surface monitoring to detect changes in infrastructure, newly exposed services, and misconfigurations in real time.
- Leverage external scanning to identify public-facing vulnerabilities before they are exploited.
- Correlate findings from multiple sources for a unified, real-time view of exposures.
Strobes ASM provides continuous visibility into external and internal attack surfaces, uncovering unmanaged and unknown assets that expand organizational risk.
Stage 3: Validate with Real-World Scenarios
- Go beyond theoretical risk by simulating real-world attacks through penetration testing, red teaming, and breach & attack simulations (BAS).
- Validate controls and defensive measures to ensure they perform as expected under active exploitation scenarios.
Strobes PTaaS combines human expertise with an intelligent platform, enabling security teams to conduct continuous validation with greater efficiency and collaboration.
Stage 4: Remediate and Orchestrate
- Prioritize remediation efforts based on risk, focusing on vulnerabilities most likely to be exploited in business-critical systems.
- Automate ticket creation, assignment, and SLA tracking to streamline workflows and reduce manual effort.
- Use playbooks for repetitive tasks to accelerate response times.
Strobes RBVM applies AI-driven prioritization and risk-based workflows, allowing teams to focus on the exposures that matter most while maintaining operational efficiency.
Stage 5: Report and Respond at the Executive Level
- Create role-based dashboards that deliver relevant insights to SOC teams, IT operations, and senior leadership.
- Track progress against KPIs such as exposure reduction rates, MTTR, and compliance alignment.
- Ensure executive reporting focuses on business risk and resilience, not technical detail.
Strobes provides customizable reporting tools and dashboards that support board-level communication and demonstrate the value of security initiatives in measurable terms.
5 Key Metrics to Track with Threat Exposure Management

An effective Threat Exposure Management program must show measurable results. With Strobes, security leaders can monitor these key metrics to demonstrate progress, align with business goals, and report confidently to stakeholders.
1. Exposure Reduction Rate
This measures the percentage decrease in identified exposures across the organization over time. It reflects how effectively your team is reducing the attack surface and addressing vulnerabilities.
- Example: A global telecom company reduced its exposure count by 48% in three months after consolidating scanner findings in Strobes and prioritizing remediation for critical assets.
2. Mean Time to Remediate (MTTR)
MTTR tracks the average time taken to resolve critical exposures from discovery to closure. Strobes enables security teams to automate workflows, assign tasks, and monitor SLA compliance to reduce MTTR significantly.
- Example: A financial institution used Strobes RBVM to bring down MTTR for high-severity vulnerabilities from 21 days to 8 days by streamlining handoffs between security and IT teams.
3. Risk Score Trends for Business-Critical Assets
Strobes calculates a risk score based on asset criticality, vulnerability severity, and exploitability. Tracking changes in these scores over time helps security leaders demonstrate improvement in protecting high-value systems.
- Example: A manufacturing company reduced the risk score for its production systems by 35% after integrating Strobes RBVM with its existing CI/CD pipelines for faster issue resolution.
4. Validation Success Rate
This metric shows the percentage of remediated vulnerabilities that successfully pass revalidation testing. Strobes supports this through PTaaS workflows and integrated scanners, ensuring that fixes are effective before issues are closed.
- Example: A healthcare provider achieved a 97% validation success rate after adopting Strobes for automated retesting of previously identified exposures.
5. Compliance Coverage Percentage
Strobes provides role-based dashboards and automated reporting to measure how well the organization aligns with regulatory requirements and internal security policies.
- Example: A retail enterprise achieved 93% compliance coverage for PCI DSS and GDPR requirements, reducing audit preparation time by 50% with Strobes’ pre-built compliance reporting templates.
Common Pitfalls Security Leaders Should Avoid
Threat Exposure Management often struggles to deliver business value when it’s approached as a purely operational activity. These are the critical mistakes security leaders must avoid to build a program that scales with the complexity of modern enterprises.
1. Treating TEM as a Periodic Assessment
- Relying on quarterly or annual scans creates significant blind spots. New exposures introduced through continuous deployments, third-party integrations, or cloud misconfigurations often remain undetected for months.
- In hybrid environments, where assets shift between on-premises and multiple cloud providers, the attack surface changes too quickly for periodic assessments to keep pace.
- Legacy systems and unmanaged endpoints often fall outside the scope of scheduled scans, leaving them vulnerable to exploitation.
Strobes enables continuous monitoring and real-time asset discovery across dynamic infrastructures, ensuring risks are surfaced as they emerge and not weeks later.
2. Prioritizing Vulnerabilities Without Business Context
- Traditional vulnerability management focuses on severity scores like CVSS without considering whether a vulnerability is exploitable or if it affects business-critical systems.
- Teams often waste resources patching low-impact issues while high-risk exposures tied to crown-jewel assets remain unresolved.
- Inadequate prioritization also creates friction between security and operations teams when patching schedules disrupt critical workflows unnecessarily.
Strobes uses a multi-dimensional risk model that incorporates asset criticality, exploitability, threat intelligence, and business impact. This approach enables teams to focus on vulnerabilities that could disrupt operations or trigger compliance failures.
3. Relying on Manual Processes for Correlation and Reporting
- Large enterprises often use multiple scanners and tools, resulting in fragmented datasets that must be manually aggregated. This process is slow, error-prone, and unable to scale as the volume of findings increases.
- Deduplication errors lead to redundant remediation efforts and inflate the perception of risk.
- Reporting bottlenecks make it difficult for security leaders to present accurate, timely insights to executives and boards.
Strobes automates ingestion from 120+ security tools, applies intelligent deduplication algorithms, and integrates with ITSM platforms like Jira and ServiceNow. This allows teams to streamline workflows and maintain an accurate, real-time view of organizational risk.
4. Closing Tickets Without Validating Fixes
- Marking a vulnerability as resolved in a ticketing system does not guarantee it has been mitigated in production environments. Misconfigurations, failed patches, or rollbacks can leave the exposure active.
- Attackers increasingly target “fixed” vulnerabilities that were incompletely patched or accidentally reintroduced during software updates.
- Without revalidation, organizations risk inflated remediation metrics and a false sense of security.
Strobes enables automated retesting and validation through its PTaaS workflows and scanner integrations, ensuring that remediation efforts have been successful before issues are considered closed.
5. Overlooking Shadow IT and Third-Party Exposures
- Assets created outside formal IT processes, such as rogue cloud instances or developer-owned systems, expand the attack surface without centralized visibility.
- Third-party vendors and partners often manage systems that are externally accessible yet beyond the direct control of the organization’s security team.
- These unmanaged and external-facing assets are prime targets for attackers exploiting overlooked misconfigurations or outdated software.
Strobes’ Attack Surface Management continuously scans for external-facing assets, subdomains, APIs, and services. It provides security teams with an up-to-date map of their attack surface, including shadow IT and third-party exposures, enabling proactive remediation.
Why Threat Exposure Management Must Go Continuous?
Periodic assessments worked when infrastructures were static and updates happened quarterly. But today’s environments—cloud-native, API-driven, and heavily reliant on third-party ecosystems shift too rapidly for point-in-time visibility to keep pace.
Every new deployment, configuration change, or vendor integration can introduce exposures. Attackers are leveraging automation to exploit these faster than traditional processes can detect them.
To stay ahead, security leaders are moving beyond static Threat Exposure Management to continuous, lifecycle-driven programs that:
- Maintain real-time visibility across hybrid and multi-cloud environments.
- Prioritize exposures dynamically based on exploit activity, asset criticality, and business impact.
- Validate remediation efforts through automated retesting and real-world attack simulations.
- Orchestrate workflows across security, IT, and development teams to reduce mean time to remediate.
This evolution gives enterprises not only a clearer picture of their current risk posture but also the agility to act decisively when new threats emerge.
Strobes Is Already There
Strobes enables this shift with a unified platform built for continuous exposure management. It combines:
- Continuous asset discovery, including shadow IT and third-party ecosystems.
- Risk-based prioritization that moves beyond CVSS scores.
- Integrated validation workflows with retesting and PTaaS capabilities.
- Automated remediation orchestration integrated with ITSM systems.
Enterprises using Strobes are already bridging the gap between detection and action, reducing exposure windows, and aligning security operations with business objectives.
The shift from periodic scans to real-time risk reduction is already underway. Don’t get left behind. Schedule a Call.
Frequently Answered Questions (FAQ’s)
Q.1 What is the main difference between Threat Exposure Management (TEM) and traditional vulnerability management?
TEM focuses on continuously identifying and prioritizing exposures based on real business risk, whereas traditional vulnerability management often relies on periodic scanning and long lists of issues without context. TEM integrates asset discovery, threat intelligence, and validation to drive focused remediation aligned with business priorities, enabling security leaders to address exposures that matter most.
Q.2 How does continuous monitoring improve security posture?
Continuous monitoring provides real-time visibility into changes across cloud, shadow IT, and third-party environments, enabling faster identification of new threats and misconfigurations. This approach reduces the time exposures remain undetected and helps maintain an accurate attack surface inventory, improving overall security effectiveness and compliance readiness.
Q.3 What measurable benefits can organizations expect from implementing Threat Exposure Management?
Organizations typically see faster exposure reduction rates, decreased mean time to remediate critical vulnerabilities (MTTR), improved validation success rates, and enhanced compliance coverage. These metrics translate to reduced operational risk, better audit outcomes for standards such as NIST, ISO 27001, PCI DSS, and HIPAA, and stronger alignment between security investments and business outcomes.
Q.4 Is Threat Exposure Management scalable for large enterprises with complex infrastructures?
Yes, TEM platforms designed for scalability can handle thousands of assets across hybrid, cloud, and third-party environments without performance degradation. Automation, AI-driven prioritization, and integration with existing ITSM systems enable security teams to manage complex risk landscapes efficiently, regardless of organization size.
Q.5 What integration capabilities are essential for effective Threat Exposure Management?
Effective TEM requires seamless integration with vulnerability scanners, cloud providers, SIEM, ITSM tools (like Jira, ServiceNow), and threat intelligence platforms. These integrations enable automated data aggregation, correlation, risk scoring, and workflow orchestration for end-to-end exposure lifecycle management.
Q.6 What common challenges impede the successful implementation of Threat Exposure Management?
Challenges include overwhelming threat intelligence volume, limited visibility into dynamic environments, skill shortages within security teams, fragmented toolsets causing data silos, and operational friction between security and IT teams. Addressing these with continuous discovery, context-aware risk models, automation, and cross-team collaboration is crucial for success.