Mobile applications are now central to business operations. From internal workforce tools to customer-facing platforms, organizations rely heavily on mobile ecosystems. But with this growth comes increased exposure. Addressing Data Protection and Compliance with Mobile Application Pentesting is essential, especially as the 2024 Mobile Security Index by Verizon reports that 45% of organizations experienced a mobile-related compromise that led to data loss or system downtime.
What’s more concerning is the compliance risk. Regulatory bodies expect mobile applications to enforce the same level of control as traditional systems. Whether it’s GDPR, HIPAA, or PCI-DSS, the standards are clear to protect user data at all times with no exceptions for mobile.
Mobile Application Pentesting has become essential. It provides the technical proof of whether an application holds up against modern threats and compliance expectations.
This blog explores where mobile risks originate, how they impact compliance, and why pentesting is a necessary step for safeguarding data and avoiding legal exposure.
The Real Risks Hidden Inside Mobile Apps ( Create image)
Mobile apps operate in untrusted environments. The application resides on devices the organization doesn’t control, often with limited insight into runtime behavior. This leads to a range of risks:
1. Insecure Data Storage
Apps frequently store tokens, credentials, or personal data in plaintext within the local file system, shared preferences, or SQLite databases. Even temporary caches can expose sensitive information, especially on rooted devices.
2. Broken Authentication & Authorization
Mobile applications often struggle with session handling. OTP reuse, missing session expiration, and poor token validation can let attackers reuse tokens or escalate privileges.
3. Reverse Engineering & Code Tampering
Without obfuscation, attackers can decompile apps, analyze API endpoints, and even modify code to bypass authentication checks.
4. Weak Encryption Practices
Hardcoded cryptographic keys, outdated cipher suites, and missing TLS pinning leave encrypted data vulnerable. Encryption is only as strong as its implementation.
5. Third-party SDKs & APIs
Applications integrate analytics, ad networks, and push notification services. Many of these SDKs introduce tracking issues, insecure API calls, or data storage concerns outside the control of the development team.
Mobile security is not just about reducing risk it’s about meeting legal and regulatory requirements. Here’s how different frameworks address mobile data handling:
GDPR – Mandates data minimization, explicit consent for tracking, and strong encryption. Breaches require notification within 72 hours. Mobile apps must prove how data is collected, processed, and stored securely.
HIPAA – Requires covered entities to ensure the confidentiality, integrity, and availability of electronic Protected Health Information (ePHI). Apps used by healthcare providers must encrypt PHI in transit and at rest, implement strong access controls, and log access events.
PCI-DSS – Requires secure transmission and storage of payment data. Mobile apps handling credit card info must avoid storing sensitive authentication data and must secure mobile payment SDKs.
CCPA – Grants consumers the right to access, delete, and restrict the sale of their data. Mobile applications must provide transparent privacy notices and ensure secure handling of user information.
Case Examples:
- In 2023, a U.S.-based telehealth provider was fined $1.3 million due to mobile app vulnerabilities exposing PHI to unauthorized users.
- A European retailer was fined €850,000 under GDPR when their Android app leaked user location and contact data due to insecure permissions.
What Is Mobile Application Pentesting?
Mobile application pentesting involves simulating attacks on mobile applications to identify and exploit security flaws. The goal is to mimic the techniques a real-world attacker would use and provide developers with the evidence and context to fix them.
Unlike automated scanners, mobile penetration testing involves manual validation of business logic, authentication flows, encryption strength, and storage mechanisms. It spans:
- Static Analysis – Reviewing decompiled source code for logic flaws, hardcoded credentials, and insecure SDKs
- Dynamic Analysis – Observing runtime behavior, intercepting API calls, and modifying data in transit
- Reverse Engineering – Using tools like jadx and MobSF to analyze app structure and vulnerabilities
Commonly used tools:
- MobSF for automated SAST/DAST
- Frida and Objection for runtime hooking
- Burp Suite for intercepting API traffic
- Drozer for Android component testing
Mobile Application Pentesting for Data Protection
Data is the prime target in most mobile attacks. Pentesting helps identify:
- Unsecured storage paths where tokens, credentials, and PII are left exposed
- Improper API security, such as missing rate limiting, verbose error messages, or weak authorization checks
- Leaky logs and caches storing sensitive details that persist across sessions
- Insecure clipboard use, which allows malicious apps to capture copied content like passwords or card details
- Improper SSL configurations, including disabled certificate validation or fallback to HTTP
Mobile application pentesting validates how an app handles and protects data not just in theory, but in live runtime. This ensures sensitive data isn’t left exposed through overlooked channels.
Mobile Application Penetration testing for Compliance
A detailed pentest report offers more than just a list of issues it serves as documentation for regulatory review. Here’s how it supports compliance:
- Maps vulnerabilities to standards like OWASP MASVS, NIST, and ISO 27001
- Provides evidence of proactive risk assessment and remediation, which can reduce penalties in the event of a breach
- Supports audit-readiness with reproducible test cases, screenshots, and remediation guidance
- Enables vendor assurance for B2B apps by showing a secure-by-design posture to partners
When and How Often Should You Test?
Compliance isn’t a one-time effort. Threats evolve, and so do applications. Testing frequency depends on several factors:
- Pre-release testing: Before major version upgrades, especially when introducing payment, health, or geo-location features
- Quarterly or biannual audits: For applications in regulated environments
- After third-party SDK updates: Many apps rely on components outside the team’s direct control
- Post-remediation verification: Ensuring previously reported issues were fixed correctly
Security testing should also be embedded into the CI/CD pipeline using integration hooks to trigger scans or manual review checkpoints.
Common Pitfalls Companies Make With Mobile Security
1. Over-reliance on store reviews
Passing the App Store or Play Store review doesn’t mean an app is secure. Review checks are often limited to functional and policy violations, not technical security.
2. Skipping jailbroken/rooted scenarios
Many attacks occur in environments where users have elevated privileges. If your app isn’t tested under these conditions, critical risks remain undetected.
3. No retesting after fixing vulnerabilities
Fixes often break other parts of the app or don’t address the root cause. Without retesting, the same issues may persist.
4. Mobile as an afterthought
Some organizations focus more on web app security. But mobile often connects to the same backend APIs and introduces new client-side risks.
Integrating Mobile Security into Your CI/CD Pipeline
Security gaps often go unnoticed when mobile applications are tested only after development is complete. A more effective approach is to bring security testing into the development workflow itself, specifically, into your CI/CD pipeline.
By introducing mobile security checks at earlier stages, development teams can identify misconfigurations, unsafe coding practices, and vulnerable dependencies before code reaches production. Static analysis, binary checks, and permission audits can be automatically run during build stages using tools like Bitrise, GitHub Actions, or Azure Pipelines. Post-build, dynamic testing and API validations can be scheduled without disrupting delivery timelines.
Benefits of integrating mobile security into CI/CD pipelines:
- Immediate visibility into security issues during development and QA stages
- Faster remediation cycles, as findings are reported directly to developers in platforms like Jira or Slack
- Improved audit readiness, with a consistent record of automated and manual testing activities
At Strobes, mobile application penetration testing engagements can be aligned with CI/CD practices. Our platform supports testing hooks, automated scanner triggers, and structured retesting, helping teams reduce rework, meet compliance goals, and ship more reliable applications.
Why Mobile Application Pentesting Shouldn’t Be a One-Time Activity
Security testing for mobile applications is often treated as a checkbox item—completed before an initial release and then forgotten. But mobile apps are updated frequently. Each version introduces new code, third-party SDKs, permission changes, or API dependencies. With every change, new risks can be introduced—even if the previous version was considered secure.
For example:
- A permissions update might unintentionally expose background location data.
- A newly added analytics SDK could transmit user identifiers without encryption.
- Changes in session management logic could bypass timeout rules or allow reuse of expired tokens.
These aren’t theoretical risks. Such flaws have repeatedly surfaced in production apps, often discovered only after users report unusual behavior or data exposure.
Routine pentesting ensures that new versions are held to the same security standards as the original release. It also allows organizations to validate that previously reported issues remain resolved after updates.
Strobes enables recurring assessments by offering retesting support and version-specific analysis. This allows security teams to track improvements, confirm issue resolution, and maintain consistency across releases without duplicating effort.
Choosing the Right Mobile Application Pentesting Partner
To get the most out of pentesting, the right partner makes all the difference. Look for:
- Expertise across iOS and Android
Ensure they test both platforms thoroughly, including platform-specific weaknesses. - Manual + automated testing capabilities
Automation speeds up scanning, but manual inspection catches logic and context-based flaws. - Compliance-mapped reporting
Reports should be aligned with frameworks your organization is subject to, from HIPAA to ISO 27001. - Post-remediation retest included
Fixing issues is only part of the job. You need confirmation that they’re truly resolved. - Transparent methodology
Ask what standards or methodologies they follow: OWASP MASVS, NIST SP 800-163, or custom playbooks?
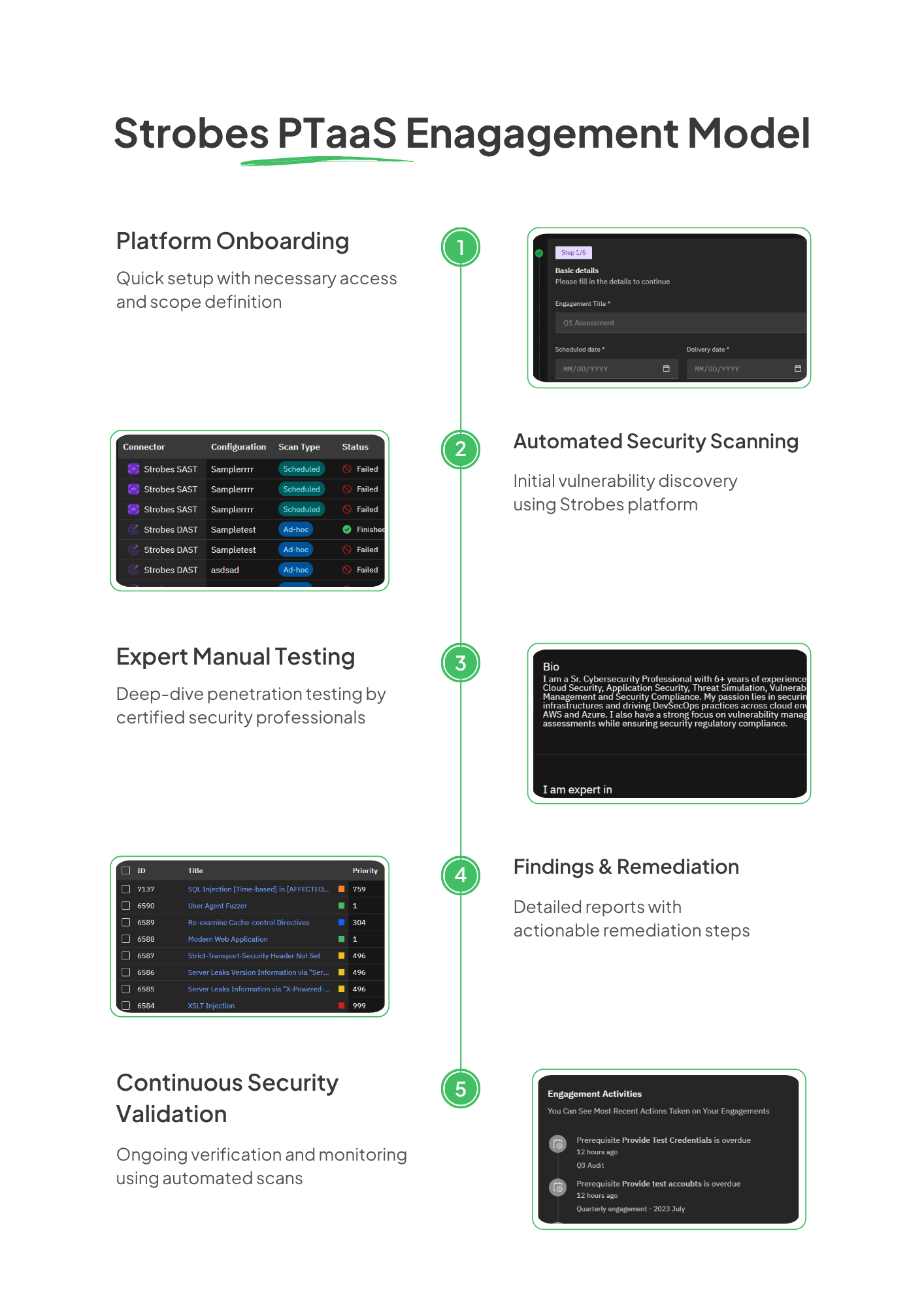
Strobes Mobile Application Pentesting for iOS and Android
Strobes Mobile Application Pentesting offers in-depth security testing for both iOS and Android applications using a hybrid approach that includes static analysis, dynamic testing, API assessments, and business logic validation. It uncovers risks like insecure data storage, broken authentication, hardcoded secrets, and misconfigured third-party SDKs. The service integrates seamlessly into CI/CD pipelines, enabling continuous testing with every app version.
It aligns with OWASP Mobile Top 10, MASVS, and major compliance standards like PCI DSS and HIPAA. Strobes provides contextual risk-based prioritization, reducing noise and helping teams fix what truly matters. Its native mobile scanners minimize false positives, and findings are automatically pushed into tools like Jira or GitHub for faster collaboration.
Detailed reports include reproduction steps, business impact, and remediation guidance with free retesting. Especially suited for fintech, healthcare, and compliance-heavy apps, Strobes enables secure releases without slowing down development. This makes it an essential part of any enterprise mobile security strategy.
 Conclusion: Data Protection and Compliance with Mobile Application Pentesting
Conclusion: Data Protection and Compliance with Mobile Application Pentesting
Mobile Application Penetration testing acts as a pressure test for both your data controls and your legal preparedness. It brings out hidden risks that could lead to data leaks, reputational harm, or regulatory fines. It also provides the documentation and evidence required to demonstrate compliance with standards like GDPR, HIPAA, and PCI-DSS.
At Strobes Security, we help teams go beyond surface-level scans by delivering expert-driven mobile application pentests tailored for compliance-heavy environments. From identifying critical data exposure paths to generating audit-ready reports, our platform and services are built to simplify your mobile security journey.
Ready to assess your mobile app’s true resilience?
- Schedule a free demo with a Strobes security expert
Related Reads:
- Simplifying Continuous Pentests: How Strobes PTaaS Makes Security Testing Efficient
- Web Application Penetration Testing: Steps & Test Cases
- The Web application Penetration Testing Tools That Actually Works
- Solution: Mobile Application Pentesting
- Solution: Application Security
- Solution: Web Application Pentesting


 Conclusion: Data Protection and Compliance with Mobile Application Pentesting
Conclusion: Data Protection and Compliance with Mobile Application Pentesting