malware threats are not just a possibility they’re a reality. Organizations face an ever-expanding array of sophisticated malware types, each with unique capabilities and devastating potential. A single breach can disrupt operations, erode customer trust, and inflict significant financial losses.
To safeguard critical assets, data, and operations, organizations should implement a robust malware defense strategy. This strategy extends beyond basic antivirus tools to encompass a multi-layered, proactive approach that integrates technology, processes, and human awareness.
The Rising Threat of Malware
Malware attacks are more than just digital nuisances they’re deliberate, evolving threats that target critical business operations. From ransomware crippling entire networks to stealthy spyware extracting sensitive data, attackers continuously refine their techniques. Recent high-profile breaches highlight how even well-established organizations can fall victim to advanced malware, resulting in severe reputational and financial damage.
Key Components of a Robust Defense Strategy
To mitigate these risks, a multi-layered malware defense strategy should include:
- Comprehensive Endpoint Protection: Modern antivirus solutions combined with Endpoint Detection and Response (EDR) tools help identify and neutralize threats before they infiltrate deeper into your systems.
- Network Segmentation: Limiting access across different segments of your network prevents malware from spreading laterally, reducing potential damage.
- Regular Software Updates and Patching: Outdated systems are prime targets for attackers. Ensuring all software is up-to-date closes known vulnerabilities that malware can exploit.
- Employee Training and Awareness: Human error remains a leading cause of security breaches. Regular training sessions on recognizing phishing attempts and other social engineering tactics can strengthen your first line of defense.
- Behavior-Based Detection Systems: Traditional signature-based detection is no longer sufficient. Behavior analysis tools detect anomalies that may indicate malware activity, even if the specific threat is unknown.
- Incident Response Plan: Having a clear, well-practiced incident response plan ensures your organization can react quickly to contain and eliminate malware threats, minimizing downtime and data loss.
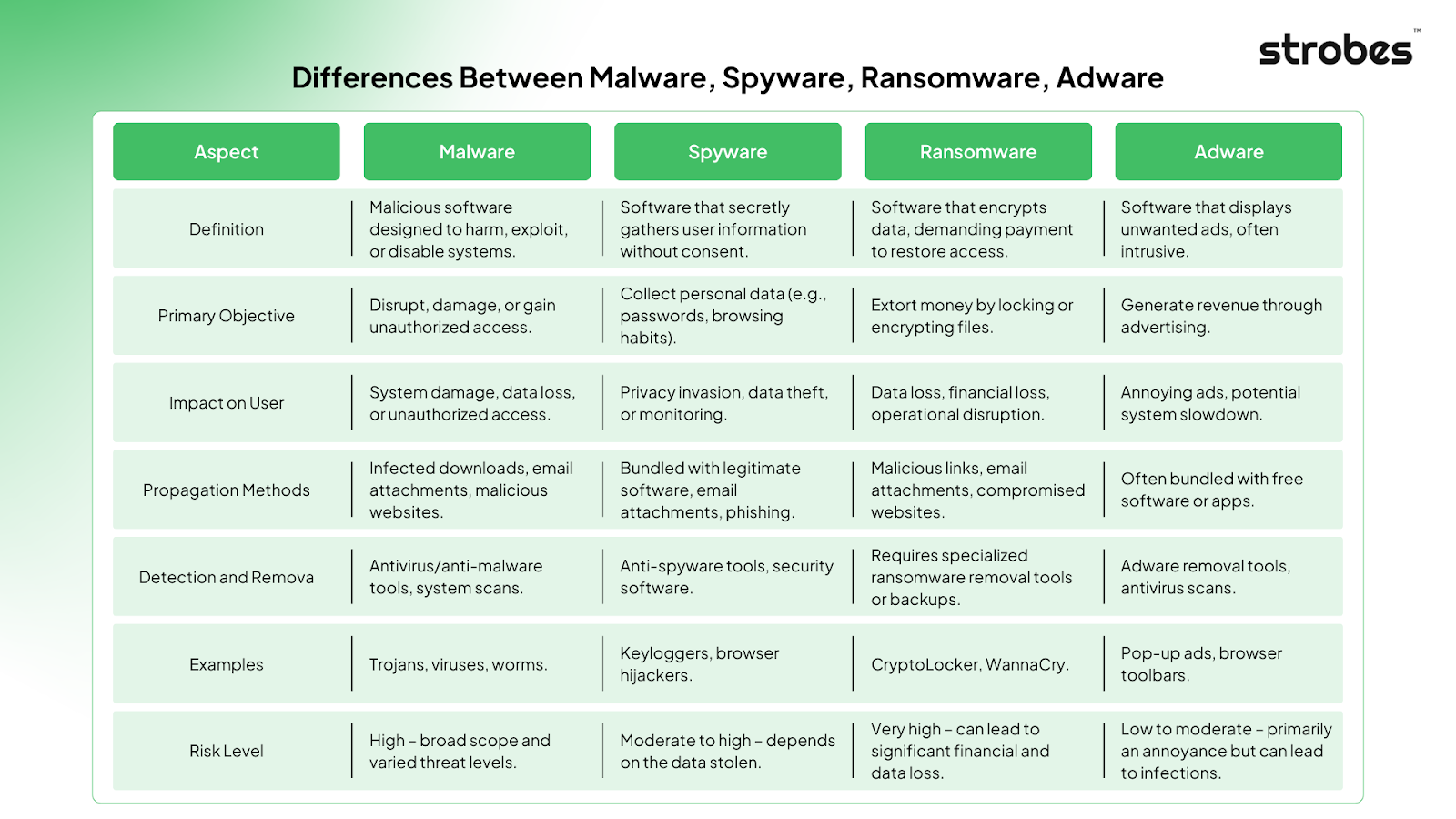
Differences Between Malware, Spyware, Ransomware, Adware
Malware Types and Their Threats
strategy begins with understanding the types of malware targeting your organization. Each form of malware poses distinct challenges and requires tailored defenses. Here’s a deeper look into some of the most prevalent malware types:
1. Ransomware
- Impact: Ransomware encrypts critical files or entire systems, rendering them inaccessible until a ransom is paid. In many cases, paying the ransom does not guarantee data recovery.
- Examples: WannaCry, REvil, Conti
- Why It Matters: Ransomware attacks have surged, targeting organizations of all sizes, and can bring entire operations to a halt. Healthcare, financial, and critical infrastructure sectors are particularly vulnerable due to their reliance on uninterrupted access to data.
- Preventive Measures:
- Maintain offline and encrypted backups to ensure recovery without paying the ransom.
- Implement advanced endpoint detection and response (EDR) solutions.
- Conduct regular penetration testing to identify vulnerabilities before attackers do.
- Train employees to recognize suspicious links, attachments, and social engineering tactics.
2. Spyware
- Impact: Spyware silently monitors user activity, capturing sensitive information such as login credentials, financial data, and personal communications.
- Examples: Pegasus, FinFisher
- Why It Matters: Spyware is often used in targeted attacks to steal proprietary information or gain unauthorized access to systems. It can go undetected for long periods, causing extensive data loss.
- Preventive Measures:
- Deploy advanced anti-spyware tools with behavior-based detection.
- Conduct regular system audits to identify and remove unauthorized software.
- Implement strong access controls and multi-factor authentication (MFA).
3. Trojans
- Impact: Disguised as legitimate software, Trojans create backdoors into systems, allowing attackers to control compromised machines remotely.
- Examples: Zeus, Emotet
- Why It Matters: Trojans can deliver additional payloads, such as ransomware or keyloggers, and are often used in spear-phishing campaigns.
- Preventive Measures:
- Validate all downloads and software sources to prevent the installation of malicious software.
- Utilize behavior-based detection tools that can identify suspicious activity patterns.
- Implement strict access controls and regularly monitor user activity.
4. Worms
- Impact: Worms are self-replicating malware that spread across networks without human intervention, often causing widespread disruption.
- Examples: Stuxnet, Mydoom
- Why It Matters: Worms can exploit vulnerabilities in network infrastructure to propagate rapidly, consuming system resources and potentially delivering destructive payloads.
- Preventive Measures:
- Implement network segmentation to limit the spread of infections.
- Keep all software and operating systems updated to close known vulnerabilities.
- Monitor network traffic for unusual patterns or anomalies.
5. Adware
- Impact: Displays unwanted advertisements, which can degrade system performance and expose users to further malware infections.
- Examples: Fireball, Gator
- Why It Matters: Although often seen as a minor threat, adware can serve as a gateway for more severe infections or be used for data tracking.
- Preventive Measures:
- Deploy reputable ad-blocking tools and regularly scan for potentially unwanted programs (PUPs).
- Educate employees on the risks associated with downloading free software from untrusted sources.
Malware Defense Strategy
1. Multi-Layered Defense
Adopting a defense-in-depth approach ensures that if one layer is breached, others remain intact to mitigate the threat. Key components include:
- Perimeter Security:
- Firewalls and intrusion detection systems (IDS) act as the first line of defense.
- Web and email filtering tools block malicious content before it reaches endpoints.
- Endpoint Protection:
- Modern antivirus solutions combined with EDR tools detect and respond to threats in real time.
- Device control policies restrict the use of removable media, reducing the risk of infection.
- Network Security:
- Network segmentation prevents malware from spreading laterally, limiting its impact.
- Implement zero-trust architecture to verify users and devices before granting access.
- Application Security:
- Regularly test applications for vulnerabilities using penetration testing and code reviews.
- Deploy application firewalls (WAF) to protect against web-based attacks.
2. Real-Time Threat Intelligence
Leveraging threat intelligence provides insights into emerging threats, enabling proactive defense measures. Benefits include:
- Identifying vulnerabilities before attackers exploit them.
- Adjusting security policies based on real-time threat data.
- Sharing intelligence with industry peers to strengthen collective defenses.
3. Proactive Monitoring and Incident Response
Continuous monitoring detects anomalies that could indicate malware activity. An effective incident response plan ensures a coordinated approach to containing and mitigating threats. Key steps include:
- Detecting and isolating infected systems.
- Conducting root cause analysis to understand how the malware entered.
- Communicating transparently with stakeholders and regulators.
4. User Education and Training
Employees are often the weakest link in cybersecurity. Regular training on recognizing phishing emails, suspicious links, and social engineering tactics is crucial. Simulated attack drills can help assess and improve employee awareness.
5. Secure Access Management
Implementing strong access controls ensures that only authorized users can access sensitive data and systems. Measures include:
- Multi-factor authentication (MFA) to add an extra layer of security.
- Applying the principle of least privilege (PoLP) to minimize potential entry points for attackers.
Examples:
Several high-profile malware incidents in 2024 have highlighted the severe impact on organizations, emphasizing the necessity for malware defense strategies:
- MOVEit Data Breach: A vulnerability in the MOVEit file transfer software led to extensive data theft. This zero-day exploit allowed attackers to exfiltrate sensitive data from numerous organizations worldwide, resulting in millions of records being compromised. The breach significantly affected both public and private sector entities, highlighting the risks of supply chain vulnerabilities and unpatched software.
- Black Basta Ransomware Surge: Black Basta, a ransomware group, targeted multiple large enterprises, encrypting data and demanding hefty ransoms. They also adopted double extortion tactics, threatening to leak stolen data if payments weren’t made. Industries such as healthcare and manufacturing were particularly affected, demonstrating the far-reaching impact of ransomware on critical infrastructure.
- LockBit 3.0 Campaigns: LockBit, one of the most prevalent ransomware groups, continued its aggressive campaigns, targeting organizations globally. Their operations disrupted services, with several victims facing significant operational downtime and data losses. LockBit’s advanced encryption methods and sophisticated attack vectors underscore the evolving complexity of modern malware.
- Critical Vulnerabilities in IoT Devices: In a major attack, threat actors exploited vulnerabilities in Internet of Things (IoT) devices, deploying botnets for large-scale distributed denial-of-service (DDoS) attacks. These incidents highlighted the risks posed by poorly secured devices connected to corporate networks.
- Supply Chain Attacks via RAMP: The RAMP marketplace facilitated numerous attacks by offering ransomware-as-a-service (RaaS) and initial access credentials. Companies with lower security postures, especially mid-sized firms, were prime targets, facing extortion and operational disruptions from malware deployments.
These incidents show the importance of a proactive multi-layered defense strategy to mitigate malware risks and safeguard organizational assets effectively. Continuous monitoring, rapid incident response, and regular updates are crucial for resilience in the evolving threat landscape.
Final Words:
Strobes can help combat typosquatting, prevent data breaches and data leaks, avoid regulatory fines, and protect customers’ trust through cyber security ratings and continuous exposure detection. Contact strobes and secure your data today.