63% of organizations suffered cyberattacks due to unpatched vulnerabilities, highlighting a critical issue. However, top-tier companies consistently maintain superior security. How do they do it? Their advantage lies in a robust vulnerability management strategy, anchored by a well-defined vulnerability management lifecycle (VML).
Each component within your IT infrastructure, from essential databases to network devices, represents a potential entry point for cyber threats. To counteract these threats, organizations rely on the vulnerability management lifecycle.
This structured approach helps identify, assess, and mitigate vulnerabilities across their IT infrastructure. It’s like performing regular safety checks around your home to ensure every lock and window is secure.
This lifecycle isn’t just a technical necessity. It’s a proactive approach to safeguarding your assets. So, what happens if a single vulnerability goes undetected? How can you make sure you are always one step ahead of cyber threats?
Stick with us. By the end, you’ll understand the importance of a well-structured Vulnerability management lifecycle and be ready to implement practices that protect your assets effectively.
What is the Vulnerability Management Lifecycle?
The Vulnerability Management Lifecycle is a structured, ongoing process designed to identify, assess, prioritize, and address vulnerabilities within an organization’s IT infrastructure. It’s a crucial element of any cybersecurity strategy, offering a systematic approach to proactively manage security risks and minimize the potential for cyberattacks.
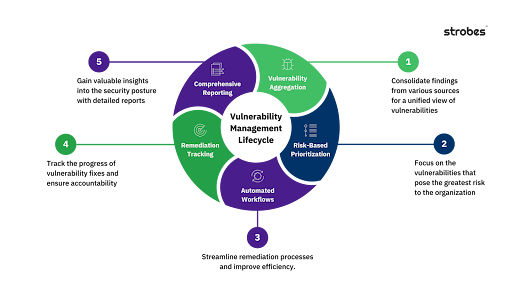
Vulnerability Management Lifecycle
- Vulnerability Aggregation – Consolidate findings from various sources for a unified view of vulnerabilities
- Risk-Based Prioritization – Focus on the vulnerabilities that pose the greatest risk to the organization
- Automated Workflows – Streamline remediation processes and improve efficiency.
- Remediation Tracking – Track the progress of vulnerability fixes and ensure accountability
- Comprehensive Reporting – Gain valuable insights into the security posture with detailed reports
Benefits of Vulnerability Management Lifecycle
1. Enhanced Threat Prioritization with Data-Driven Insights
- Leverage vulnerability scanners and threat intelligence feeds to prioritize vulnerabilities based on:
- Exploitability: Are there readily available exploits for the vulnerability?
- CVSS Scoring: Prioritize vulnerabilities with high CVSS scores (severity and exploitability).
- Business-Critical Asset Impact: Focus on vulnerabilities affecting critical systems and data.
- This enables resource allocation towards the most dangerous threats, maximizing security ROI.
2. Unparalleled Threat Visibility Across the IT Environment
- Achieve comprehensive visibility of the entire IT environment through VML, including:
- Network Devices and Endpoints: Identify unpatched or vulnerable devices.
- Software Applications and Versions: Track outdated software with known vulnerabilities.
- System Configurations: Detects misconfigurations that create security weaknesses.
- This holistic view empowers proactive identification and remediation of vulnerabilities before attackers exploit them.
3. Automated Patch Management for Reduced Vulnerability Window
- Integrate vulnerability management lifecycle with patch management systems to automate vulnerability patching processes. This facilitates:
- Reduced manual intervention for patching tasks, freeing up security personnel for complex issues.
- Minimized window of vulnerability between identification and patching, reducing attacker opportunity.
- Timely patching of critical systems to address high-risk vulnerabilities.
4. Unified Security Tools for a Holistic Threat Detection Approach
- Integrate vulnerability management lifecycle with SIEM systems to create a central hub for security data. This enables:
- Correlation of vulnerability data with security events, allowing for identification of potential attack patterns.
- Early detection and mitigation of threats before they escalate into major incidents.
5. Security Analytics for Proactive Threat Defense
- Utilize vulnerability management lifecycle to collect and analyze vulnerability data to gain insights for proactive defense:
- Identify trends to understand attacker targeting methods and emerging threats.
- Predict future threats based on vulnerability data and threat intelligence.
- Leverage these insights to proactively adjust security strategies and optimize resource allocation for maximum impact.
6. Demonstrate Security Improvement with Measurable KPIs
- Utilize vulnerability management lifecycle to track key performance indicators (KPIs) that quantify security improvements:
- Mean Time to Remediation (MTTR): Track the time taken to patch vulnerabilities, aiming for faster remediation cycles.
- Percentage of Vulnerabilities Patched: Monitor the overall progress in addressing vulnerabilities.
- Track these metrics to demonstrate the effectiveness of your security program to stakeholders and justify security budget requests.
7. Reduced False Positives for Enhanced Security Team Efficiency
- Modern vulnerability management solutions incorporate advanced threat intelligence and exploitability data to minimize false positives from vulnerability scanners.
- This allows security teams to focus on the most relevant threats, improving operational efficiency by reducing wasted time investigating false alarms.
Phase 1 – Vulnerability Aggregation
Effective vulnerability management begins with a comprehensive understanding of all potential threats within an IT environment. This involves consolidating findings from various sources to obtain a unified view of vulnerabilities.
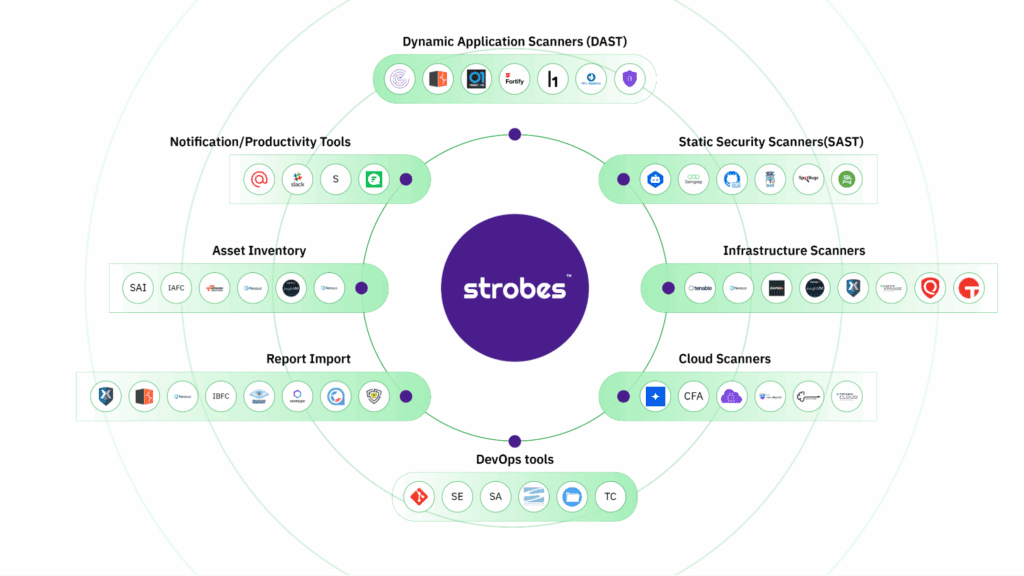
Here’s a detailed look at the key components of vulnerability aggregation:
1. Source Identification
Data Gathering from Multiple Sources:
- Network Scans: Regularly scanning the network to identify vulnerabilities in devices, servers, and other network components. Tools like Strobes RBVM can aggregate those results.
- Threat Intelligence Feeds: Integrating threat intelligence feeds that provide real-time information on new vulnerabilities and emerging threats. Sources can include commercial providers, open-source communities, and government agencies.
- Third-Party Assessments: Engaging external security experts or firms to perform penetration testing and vulnerability assessments. These third-party evaluations provide an objective view of the security posture.
- Comprehensive Approach: By gathering data from a wide array of sources, organizations ensure they have a complete and accurate view of all potential vulnerabilities. This multi-faceted approach helps in identifying not only known vulnerabilities but also zero-day exploits and emerging threats.
2. Data Integration
Merging Collected Data:
- Unified Platform or Dashboard: All collected data is integrated into a centralized platform or dashboard. This could be a Security Information and Event Management (SIEM) system or a dedicated vulnerability management tool.
- Simplified Analysis: Having all data in one place allows for easier analysis and management. Security teams can quickly identify trends, correlate data from different sources, and prioritize vulnerabilities more effectively.
- Preventing Overlooked Issues: A unified view ensures that critical vulnerabilities are not missed. It eliminates the risk of fragmented data across multiple tools and reports, which can lead to overlooked issues.
3. Normalization
Standardizing Data:
- Common Format: Data collected from different sources may vary in format, naming conventions, and categorization. Normalization involves converting this diverse data into a standard format.
- Consistent Comparison: Standardized data allows for consistent comparison of vulnerabilities. For instance, vulnerabilities identified by different tools can be assessed using a common scoring system, such as the Common Vulnerability Scoring System (CVSS).
- Effective Prioritization: With data in a common format, it becomes easier to prioritize vulnerabilities based on their severity, impact, and exploitability. This ensures that the most critical vulnerabilities are addressed first.
4. Deduplication
Removing Duplicate Entries:
- Streamlined Efforts: Vulnerability data often contains duplicates, especially when multiple tools and sources identify the same vulnerability. De-duplication removes these redundant entries, streamlining the management process.
- Maintaining Accuracy: By focusing on unique vulnerabilities, security teams can allocate their efforts more efficiently. This ensures that resources are not wasted on addressing the same issue multiple times.
- Efficient Resource Allocation: De-duplication helps in maintaining a clear and accurate inventory of vulnerabilities, which aids in better planning and resource allocation.
5. Continuous Monitoring
Regular Updates and Current State:
- Dynamic IT Environments: IT environments are constantly evolving with new assets being added and existing ones being updated or decommissioned. Continuous monitoring ensures that the vulnerability data remains up-to-date with these changes.
- Reflecting Latest Vulnerabilities: Regular updates to the aggregated data capture the latest vulnerabilities and threat intelligence. This dynamic approach ensures that security measures are always aligned with the current threat landscape.
- Proactive Management: Continuous monitoring enables proactive vulnerability management. Instead of reacting to discovered vulnerabilities, organizations can anticipate and mitigate risks before they are exploited.
Phase 2 – Risk-Based Prioritization
Vulnerability management is not just about identifying vulnerabilities; it’s about prioritizing vulnerabilities in a way that optimizes resource allocation and mitigates the most critical risks first.
Here are the elements that make up risk-based prioritization:
1. Risk Assessment
Evaluation of Potential Impact and Likelihood:
- Each identified vulnerability is carefully assessed to determine its potential impact on the organization. This involves understanding the technical severity of the vulnerability, which includes factors like how easily it can be exploited, the potential damage it can cause, and the systems it affects.
- The likelihood of exploitation is another crucial factor. This involves examining historical data on similar vulnerabilities, current trends in cyber attacks, and the ease with which the vulnerability can be exploited by attackers.
Contextual Analysis
- Understanding the context in which a vulnerability exists is essential. For example, a vulnerability in a system that is exposed to the internet poses a higher risk than one in a system that is isolated from external networks.
- context also includes the specific environment and configuration of the affected system. A vulnerability might be severe in one context but less critical in another depending on existing mitigations and protections in place.
2. Business Context
Criticality of Affected Assets:
- Not all systems and assets are created equal. The importance of a system to business operations plays a significant role in prioritization. Critical systems that support essential business functions, store sensitive data, or are part of customer-facing services are prioritized higher.
- Understanding which business processes depend on the affected systems helps in assessing the real-world impact of a vulnerability being exploited.
Operational Importance:
- Assets are evaluated based on their role in the overall business operations. For example, vulnerabilities in financial systems, customer databases, or core operational infrastructure will often take precedence over less critical systems.
- This ensures that the vulnerabilities that could cause the most significant disruption to the business are addressed first.
3. Threat Intelligence
Active Exploitation Data:
- Threat intelligence involves gathering up-to-date information about which vulnerabilities are currently being targeted by attackers. This includes intelligence from various sources such as cybersecurity vendors, threat feeds, and security communities.
- Understanding current exploitation trends helps prioritize vulnerabilities that are most likely to be targeted in the near term, thus addressing immediate threats.
Emerging Threats:
- Continuous monitoring of the threat landscape helps in identifying new threats as they emerge. This proactive approach ensures that vulnerabilities with a high likelihood of being exploited soon are addressed promptly.
- Threat intelligence also helps in understanding the tactics, techniques, and procedures (TTPs) used by attackers, aiding in better defense planning.
4. Severity Scoring
Quantifiable Risk Assessment:
- Vulnerabilities are assigned scores based on their severity using standardized frameworks such as the Common Vulnerability Scoring System (CVSS). CVSS provides a numerical score that reflects the severity of a vulnerability based on factors like exploitability, impact on confidentiality, integrity, and availability.
- This standardized scoring helps in creating a uniform approach to assessing the severity of vulnerabilities across the organization.
Contextual Adjustments:
- While CVSS scores provide a baseline, they are often adjusted based on the specific context of the organization. For example, a high CVSS score might be downgraded if existing mitigations reduce the real-world impact, or a lower score might be upgraded if the asset is critical to operations.
- This ensures that the prioritization is tailored to the unique risk profile of the organization.
5. Prioritization
Ranking Based on Risk Scores:
- Once vulnerabilities are assessed and scored, they are ranked based on their risk scores. This ranking ensures that the most critical issues are addressed first.
- The process involves creating a prioritized list that takes into account all the factors mentioned above: technical severity, business context, threat intelligence, and adjusted severity scores.
Resource Allocation:
- Prioritizing vulnerabilities helps in effective allocation of resources. By focusing on the most critical vulnerabilities first, organizations can ensure that their security efforts are directed where they will have the greatest impact.
- This prioritization is dynamic and continuously updated as new vulnerabilities are discovered and the threat landscape evolves.

Phase 3 – Automated Workflows
Automation enhances efficiency by streamlining the remediation process and ensuring consistent, timely responses to vulnerabilities. The main elements of this phase includes:
1. Task Automation
Automating repetitive tasks such as vulnerability scanning, data collection, and reporting saves time and reduces human error. Automation ensures consistent and timely updates.
- Vulnerability Scanning: Automating the process of scanning for vulnerabilities means that scans can be scheduled to run at regular intervals without manual intervention. This ensures that no systems are missed and that scans are performed consistently across the entire IT environment. Automated scanners use predefined configurations to look for known vulnerabilities, applying the latest updates and signatures to identify potential threats accurately.
- Data Collection: Gathering data from various sources, such as network devices, servers, and endpoints, can be a labor-intensive process. Automating data collection helps in compiling comprehensive and up-to-date information about the IT environment. Automated tools aggregate data from logs, configuration files, and other relevant sources, ensuring that the vulnerability management system has a complete and accurate picture of the infrastructure.
- Reporting: Generating reports manually can be time-consuming and prone to errors. Automation tools can generate detailed reports on vulnerability status, trends, and remediation progress. These reports can be customized to meet the needs of different stakeholders, providing actionable insights in a consistent format. Automation ensures that reports are produced on schedule and include the most current data.
2. Integration with IT Systems
Connecting vulnerability management tools with existing IT systems, such as ticketing systems and configuration management databases, streamlines workflows and ensures seamless communication.
- Ticketing Systems: Integrating vulnerability management tools with ticketing systems, such as Jira or ServiceNow, ensures that identified vulnerabilities are automatically converted into actionable tasks. This integration enables the security team to assign remediation tasks directly to the responsible parties, track progress, and ensure timely resolution. It also helps in maintaining a clear audit trail of actions taken to address vulnerabilities.
- Configuration Management Databases (CMDBs): Linking vulnerability management tools with CMDBs ensures that the vulnerability data is associated with the correct assets and configurations. This integration provides context to the identified vulnerabilities, such as which systems are affected, their criticality, and their dependencies. It helps in prioritizing remediation efforts based on the importance of the affected assets and understanding the potential impact of vulnerabilities on the overall IT environment.
3. Remediation Playbooks
Developing predefined workflows for common remediation tasks provides a consistent and efficient approach to addressing vulnerabilities. These playbooks outline the steps to be taken for each task.
- Standardized Processes: Remediation playbooks standardize the steps for addressing specific types of vulnerabilities. For example, a playbook for patching operating system vulnerabilities would include steps such as identifying affected systems, testing patches in a staging environment, deploying patches to production, and verifying successful applications. This standardization ensures that remediation efforts are consistent and follow best practices.
- Efficiency and Speed: Having predefined workflows means that security teams can respond quickly to identified vulnerabilities without having to devise a plan from scratch. Playbooks provide clear instructions and can be executed rapidly, reducing the time it takes to remediate vulnerabilities. This efficiency is crucial in minimizing the window of exposure and preventing potential exploits.
- Knowledge Sharing: Playbooks serve as a knowledge repository, capturing the collective expertise of the security team. New team members can refer to these playbooks to understand the procedures and ensure they are following the established protocols. This knowledge sharing helps in maintaining a high level of security even as team members change.
4. Notification Systems
Automated alerts inform relevant teams about new vulnerabilities and required actions. Prompt notifications ensure quick responses and minimize the window of opportunity for attackers.
- Real-Time Alerts: Automated notification systems can be configured to send real-time alerts whenever a new vulnerability is detected. These alerts can be delivered via email, SMS, or integrated communication platforms such as Slack or Microsoft Teams. Real-time notifications ensure that the relevant teams are immediately aware of the issue and can begin remediation efforts without delay.
- Customized Notifications: Alerts can be tailored to the needs of different stakeholders. For example, critical vulnerabilities might trigger immediate alerts to senior security personnel, while less severe issues might be directed to specific teams responsible for those systems. Customizing notifications ensures that the right people are informed about the vulnerabilities that affect them directly, streamlining the response process.
- Actionable Information: Notifications should include detailed information about the vulnerability, such as its severity, affected systems, and recommended remediation steps. Providing actionable information in the alerts helps teams quickly understand the issue and take appropriate actions. This reduces the time spent on diagnosing the problem and accelerates the remediation process.
5. Orchestration
Coordinating actions across different teams and tools ensures a unified response to vulnerabilities. Orchestration manages complex remediation efforts involving multiple stakeholders.
- Unified Response: Orchestration tools coordinate the activities of various teams, such as security, IT operations, and development, to ensure a cohesive response to vulnerabilities. This unified approach prevents silos and ensures that all stakeholders are working towards the same goal. Orchestration platforms can manage the entire remediation process, from initial detection to final resolution, providing visibility and control over each step.
- Workflow Automation: Orchestration automates the execution of remediation workflows across different tools and systems. For example, it can automatically update firewalls, apply patches, and adjust configurations based on predefined policies. This automation reduces manual intervention and ensures that remediation actions are applied consistently and accurately across the environment.
- Stakeholder Collaboration: Effective orchestration facilitates communication and collaboration among stakeholders. It provides a central platform where all parties can access the latest information, track progress, and share updates. This collaboration is essential for managing complex remediation efforts that require input and coordination from multiple teams.
Phase 4 – Remediation Tracking
Remediation tracking is a critical component of the vulnerability management lifecycle. It ensures that vulnerabilities are effectively addressed and resolved, thereby maintaining the security and integrity of an organization’s IT infrastructure. Here’s an in-depth exploration of each key aspect of remediation tracking:
1. Task Assignment
Remediation tasks are clearly assigned to specific individuals or teams, defining responsibilities and ensuring everyone knows their role.
- Clear Responsibilities: Each vulnerability remediation task is assigned to a specific individual or team with the necessary skills and authority to address the issue. This clarity in assignment prevents confusion and ensures that there is no overlap or neglect of tasks.
- Defined Roles: Responsibilities are well-defined, so each team member knows exactly what is expected of them. This includes understanding the vulnerability, the steps required for remediation, and the timeline for completion.
- Communication: Effective task assignment involves clear communication channels to ensure that assignees are aware of their tasks and any updates or changes to the remediation plan.
Proper task assignment ensures that remediation efforts are organized and efficient, with each vulnerability being addressed by the most suitable resources.
2. Progress Monitoring
The status of remediation efforts is continuously monitored. Real-time tracking ensures tasks are completed on time and no vulnerabilities are overlooked.
- Real-Time Tracking: Tools and dashboards provide real-time updates on the status of each remediation task. This helps in identifying bottlenecks and ensuring that tasks are progressing as planned.
- Timeliness: Monitoring systems set deadlines for each task and send reminders as deadlines approach. This ensures that remediation efforts stay on schedule and that vulnerabilities are not left unaddressed.
- Visibility: Progress monitoring provides visibility into the remediation process for all stakeholders, enabling them to see which tasks are completed, which are in progress, and which are pending.
Continuous progress monitoring helps maintain momentum in remediation efforts and ensures that no vulnerabilities slip through the cracks.
3. Verification
Follow-up scans and assessments validate that vulnerabilities have been successfully remediated, confirming that fixes are effective and vulnerabilities are resolved.
- Follow-Up Scans: After remediation efforts are completed, follow-up scans are conducted to ensure that the vulnerabilities have been effectively addressed. These scans verify that the fixes applied are functioning as intended.
- Validation Assessments: In addition to automated scans, manual assessments or penetration tests may be conducted to validate the effectiveness of remediation efforts. This comprehensive approach ensures that vulnerabilities are thoroughly resolved.
- Confirmation: Verification processes confirm that the system is secure and that the same vulnerabilities will not reappear. This step is crucial for maintaining the integrity and security of IT systems.
Verification ensures that remediation efforts are successful and that vulnerabilities are truly resolved, rather than just temporarily mitigated.
4. Accountability
Detailed records of who performed each remediation task and when they were completed ensure accountability and provide an audit trail for compliance purposes.
- Detailed Records: Every remediation task is documented, including details of who performed the task, when it was completed, and the specific actions taken. This documentation provides a clear audit trail.
- Audit Trail: An audit trail is essential for demonstrating compliance with regulatory requirements and internal policies. It shows that the organization is actively managing vulnerabilities and taking appropriate actions to mitigate risks.
- Responsibility: By tracking who is responsible for each task, organizations can ensure accountability. This accountability helps maintain high standards of performance and encourages thorough and timely remediation efforts.
Accountability is crucial for ensuring that remediation tasks are performed correctly and for providing evidence of compliance with security standards and regulations.
5. Feedback Loop
Insights gained from remediation efforts are used to improve future processes. A feedback loop helps refine the vulnerability management lifecycle over time, making it more effective.
- Learning from Experience: Each remediation effort provides valuable insights into what worked well and what didn’t. These lessons are documented and analyzed to improve future vulnerability management processes.
- Continuous Improvement: A feedback loop ensures that the vulnerability management lifecycle evolves and becomes more effective over time. This involves updating remediation playbooks, refining task assignment processes, and enhancing monitoring and verification techniques.
- Process Refinement: By incorporating feedback, organizations can streamline their remediation efforts, reduce the time required to address vulnerabilities, and improve the overall security posture.
A feedback loop fosters continuous improvement, ensuring that vulnerability management processes remain effective and responsive to new challenges.
6. Service Level Agreements (SLAs)
Establishing SLAs for vulnerability management processes ensures that tasks are completed within defined timeframes, maintaining accountability and performance standards. For example, an SLA might specify that critical vulnerabilities must be remediated within 24 hours, while lower-priority issues must be addressed within a week. Automated workflows can track SLA compliance, generating alerts and reports to ensure that remediation efforts stay on track. SLAs provide clear expectations for response times and help organizations measure the effectiveness of their vulnerability management programs.
Phase 5 – Comprehensive Reporting
1. Dashboard Views
Real-time dashboards offer an overview of current vulnerabilities, their statuses, and remediation efforts. Dashboards help stakeholders quickly grasp the security posture, providing a visual summary of key metrics.
- Current Vulnerabilities: Dashboards display the number and severity of vulnerabilities currently affecting the organization’s IT infrastructure. This visibility allows security teams to prioritize remediation efforts based on the most critical issues.
- Status Updates: Dashboards provide real-time updates on the progress of vulnerability remediation tasks. Stakeholders can see which vulnerabilities have been mitigated, which are in progress, and which require immediate attention.
- Remediation Efforts: Visual representations, such as charts and graphs, illustrate the effectiveness of remediation efforts over time. This helps in assessing the organization’s ability to reduce its attack surface and improve overall security posture.
Dashboard views are instrumental in providing a holistic view of vulnerabilities and their remediation status, enabling informed decision-making and proactive management of security risks.
2. Trend Analysis
Historical data analysis identifies trends and patterns in vulnerabilities and remediation efforts. Understanding these trends helps in predicting and preventing future issues.
- Identifying Patterns: By analyzing historical data, organizations can identify recurring vulnerabilities or trends in attack vectors. This insight enables proactive measures to mitigate similar vulnerabilities in the future.
- Predictive Analytics: Trend analysis facilitates predictive analytics, allowing organizations to anticipate potential security threats and vulnerabilities. This proactive approach reduces the likelihood of security incidents and improves response times.
- Continuous Improvement: Insights from trend analysis guide continuous improvement efforts in vulnerability management strategies and practices. Organizations can adjust their security policies and procedures based on data-driven insights to enhance resilience against evolving threats.
Trend analysis is crucial for leveraging historical data to strengthen proactive security measures and preemptively address vulnerabilities before they can be exploited.
3. Risk Metrics
Reports on key risk metrics, such as the number of critical vulnerabilities, average time to remediation, and overall risk score, provide a quantifiable measure of the security posture. These metrics help track progress and identify areas needing improvement.
- Critical Vulnerabilities: Metrics quantify the severity and impact of vulnerabilities classified as critical, allowing organizations to prioritize remediation efforts based on risk levels.
- Time to Remediation: Average time metrics indicate how quickly vulnerabilities are remediated once identified. Monitoring this metric helps in assessing the efficiency of remediation processes and identifying bottlenecks.
- Overall Risk Score: A composite risk score consolidates various risk metrics into a single measure of the organization’s security posture. This score facilitates comparison over time and benchmarking against industry standards.
Risk metrics provide stakeholders, from IT teams to executive management, with actionable insights to improve security resilience and operational efficiency.
4. Compliance Reporting
Reports demonstrate compliance with industry standards and regulations. Compliance reports are essential for meeting regulatory requirements and passing audits. Detailed reports show adherence to standards like PCI DSS or HIPAA.
- Regulatory Standards: Compliance reports detail how well the organization adheres to specific regulatory requirements, such as data protection laws (GDPR), financial regulations (PCI DSS), or healthcare standards (HIPAA).
- Audit Preparation: Comprehensive compliance reporting simplifies the audit process by providing documented evidence of adherence to regulatory guidelines. This ensures that organizations are well-prepared for regulatory audits and inspections.
- Continuous Compliance: Regular compliance reporting ensures ongoing adherence to regulatory standards, helping organizations avoid penalties, legal liabilities, and reputational damage associated with non-compliance.
Effective compliance reporting is critical for demonstrating due diligence in maintaining a secure and compliant environment, fostering trust with customers, partners, and regulatory authorities.
5. Executive Summaries
High-level reports for executive stakeholders summarize the current security posture and highlight areas of concern and improvement. These summaries ensure executives are informed and engaged in security efforts, providing clear, concise insights for decision-making.
- Key Metrics: Executive summaries highlight critical security metrics, such as overall risk score, status of major vulnerabilities, and compliance status. This enables executives to quickly grasp the organization’s security posture at a glance.
- Strategic Insights: Summaries include strategic insights and recommendations for improving security resilience and addressing emerging threats. This empowers executives to make informed decisions regarding resource allocation and strategic initiatives.
- Alignment with Business Goals: Executive summaries contextualize security issues within the broader business context, emphasizing the impact on operational continuity, reputation, and regulatory compliance.
Executive summaries bridge the gap between technical details and strategic decision-making, ensuring alignment between security priorities and organizational objectives.
Vulnerability Management Challenges & Its Solution
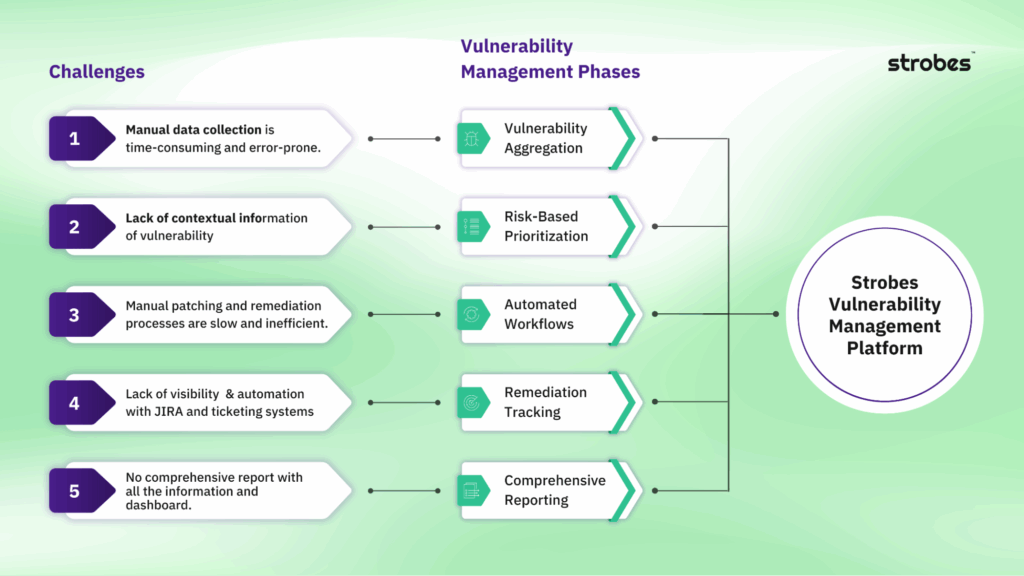

Why Vulnerability Management Matters?
1. Protection Against Exploits
Vulnerabilities in software, hardware, or configurations are prime targets for cybercriminals. Exploiting these weaknesses allows attackers to gain unauthorized access to systems, data, and networks. Effective vulnerability management identifies these flaws before they can be exploited, thereby preventing potential breaches. Regular scanning and assessment ensure that new vulnerabilities are detected promptly, reducing the attack surface and enhancing overall security.
2. Minimizing Risk Exposure
Every vulnerability in an organization’s IT environment represents a potential risk. Without a structured approach to vulnerability management, these risks can accumulate, leading to significant security gaps. By systematically identifying, assessing, and remediating vulnerabilities, organizations can prioritize and address the most critical risks. This risk-based approach ensures that resources are allocated efficiently, focusing on vulnerabilities that pose the greatest threat.
3. Compliance and Regulatory Requirements
Many industries are subject to stringent regulatory standards that mandate specific security practices. For instance, regulations like GDPR, HIPAA, and PCI DSS require organizations to implement comprehensive vulnerability management programs. Non-compliance can result in severe penalties, legal liabilities, and reputational damage. By adhering to these regulatory requirements, organizations not only avoid penalties but also demonstrate their commitment to protecting sensitive data and maintaining robust security practices.
4. Safeguarding Sensitive Data
Data breaches can have devastating consequences, including financial losses, reputational harm, and legal repercussions. Vulnerability management plays a critical role in safeguarding sensitive data by identifying and addressing security weaknesses that could lead to data breaches. This proactive approach ensures that personal, financial, and proprietary information remains protected against unauthorized access and theft.
5. Maintaining System Integrity and Availability
Vulnerabilities can disrupt the normal functioning of IT systems, leading to downtime, reduced performance, and operational inefficiencies. Effective vulnerability management ensures that systems remain secure, stable, and reliable. By addressing vulnerabilities promptly, organizations can maintain the integrity and availability of their critical systems and applications, thereby supporting business continuity and productivity.
6. Cost Efficiency
The cost of addressing a security breach can be astronomical, encompassing incident response, remediation, legal fees, and reputational damage. Proactive vulnerability management is a cost-effective strategy that helps prevent breaches before they occur. By investing in regular vulnerability assessments and timely remediation, organizations can avoid the far greater costs associated with security incidents.
7. Enhancing Threat Intelligence
Vulnerability management provides valuable insights into the evolving threat landscape. By continuously monitoring and analyzing vulnerabilities, organizations can gain a deeper understanding of emerging threats and attack vectors. This intelligence is crucial for adapting security strategies, improving defenses, and staying ahead of cybercriminals. It also helps in refining security policies and procedures to better address future challenges.
8. Supporting a Security Culture
A robust vulnerability management program fosters a culture of security awareness and responsibility within the organization. It encourages continuous improvement and vigilance, ensuring that security is integrated into every aspect of operations. This cultural shift is essential for creating an environment where security is prioritized and actively maintained by all stakeholders.
Vulnerability Management Lifecycle for Different Sized Organizations with Strobes RBVM
1. Small Organizations
Characteristics:
- Limited IT resources and staff.
- Smaller IT infrastructure.
- Less complex systems and fewer devices.
- Often rely on basic tools and manual processes.
Approach:
- Vulnerability Aggregation:
- Use free or low-cost vulnerability scanning tools.
- Focus on scanning critical assets like web servers and databases.
- Risk-Based Prioritization:
- Apply a simple risk scoring system to categorize vulnerabilities as High, Medium, or Low.
- Prioritize remediation based on the potential impact on business operations.
- Automated Workflows:
- Implement basic automation for regular scans and simple tasks.
- Set up automated alerts to notify the team of critical vulnerabilities.
- Remediation Tracking:
- Maintain a manual log to track identified vulnerabilities and remediation efforts.
- Conduct follow-up scans to ensure issues are resolved.
- Comprehensive Reporting:
- Generate simple reports highlighting the most critical vulnerabilities and remediation status.
- Keep stakeholders informed with regular updates on security posture.
Using Strobes RBVM: Small organizations can leverage Strobes RBVM to automate scanning and reporting, helping to manage vulnerabilities effectively with limited resources.
2. Medium-Sized Organizations
Characteristics:
- Moderate IT resources and staff.
- More complex IT infrastructure with increased devices and applications.
- Utilize automated tools and structured processes.
- Greater need for detailed reporting and compliance.
Approach:
- Vulnerability Aggregation:
- Invest in automated vulnerability scanning tools for comprehensive coverage.
- Maintain a detailed asset inventory to ensure thorough scanning.
- Risk-Based Prioritization:
- Use frameworks like CVSS for detailed risk assessments.
- Develop internal policies to guide regular risk evaluations.
- Automated Workflows:
- Implement automated workflows for scanning, data collection, and basic remediation tasks.
- Set up automated alerts and notifications to relevant teams.
- Remediation Tracking:
- Use dedicated tools to track remediation efforts and timelines.
- Develop remediation playbooks for consistent responses to common vulnerabilities.
- Comprehensive Reporting:
- Generate detailed reports including risk metrics and compliance status.
- Provide stakeholders with insights through dashboards and trend analysis.
How Strobes RBVM can help: Medium-sized organizations can benefit from Strobes RBVM’s advanced risk assessment and automated workflows, ensuring efficient vulnerability management and compliance.
3. Large Organizations
Characteristics:
- Extensive IT resources and specialized staff.
- Highly complex IT infrastructure with numerous devices and network segments.
- Employ enterprise-level tools and continuous monitoring.
- Require advanced reporting and compliance mechanisms.
Approach:
- Vulnerability Aggregation:
- Utilize enterprise-level vulnerability management tools with comprehensive scanning and asset discovery.
- Continuously update the asset inventory to ensure no device is overlooked.
- Risk-Based Prioritization:
- Apply sophisticated risk management frameworks to assess and prioritize vulnerabilities.
- Involve cross-functional teams for thorough risk evaluation.
- Automated Workflows:
- Implement advanced automation for scanning, remediation, and reporting.
- Orchestrate workflows across different teams and tools for a unified response.
- Remediation Tracking:
- Use robust tracking systems to monitor and validate remediation efforts.
- Conduct regular audits to ensure ongoing effectiveness.
- Comprehensive Reporting:
- Produce high-level executive summaries and detailed compliance reports.
- Leverage dashboards and advanced analytics for real-time visibility and trend analysis.
Why Strobes RBVM: Large organizations can leverage Strobes RBVM’s enterprise-level features and continuous monitoring capabilities to maintain a robust security posture and comprehensive reporting.
Conclusion
So, you’ve taken a vital step towards proactive security by educating yourself on the vulnerability management lifecycle. Now is the time to transform this knowledge into action. Don’t let vulnerabilities linger. Empower your security team with the right vulnerability management tools to identify, assess, prioritize, remediate, and report on threats before they wreak havoc.
FAQs
1. How often should vulnerability scans be conducted?
Vulnerability scan frequency depends on factors like asset criticality, industry, and risk tolerance. However, a best practice is monthly scans, with more frequent scans (weekly/daily) for high-risk environments.
2. How can vulnerability management tasks be automated?
Vulnerability management tools automate tasks like scanning, prioritizing vulnerabilities, and generating reports. Advanced solutions like Strobes RBVM offer extensive automation, streamlining the process and freeing your security team for strategic initiatives.
3. How can the cost of a vulnerability management program be justified to leadership?
Focus on the potential financial impact of security breaches. Data breaches can incur significant costs like fines, legal fees, and reputational damage. A strong vulnerability management program demonstrates proactive risk management, reducing these potential costs and protecting the organization’s bottom line.
4. How can vulnerability management be integrated into the overall security strategy?
Vulnerability management is a core component of any comprehensive security strategy. By identifying and addressing vulnerabilities, you can significantly reduce your attack surface and improve your overall security posture. Vulnerability management should be integrated with other security initiatives like penetration testing and security awareness training.
5. What are the benefits of using a risk-based approach to vulnerability management?
A risk-based approach prioritizes vulnerabilities based on their potential impact on your organization. This ensures your security team focuses on the most critical issues first. Strobes RBVM utilizes a robust risk-scoring engine to prioritize vulnerabilities based on exploitability, severity, and business context, allowing for optimized remediation efforts.







