Security testing today isn’t just about finding vulnerabilities, it’s about how fast you find them, how quickly you fix them, and how confidently you prove risk reduction.
And that’s where most teams hit a wall.
Pentesting vs PTaaS vs Automated Pentesting – three models that promise security assurance, but only one may actually fit how your organization moves.
- Traditional pentesting gives you depth, but it’s slow, isolated, and outdated by the time the report lands on your desk.
- Automated pentesting scales fast, but it rarely understands real business impact or where logic truly breaks.
- PTaaS offers a hybrid: human expertise delivered continuously, with the transparency and integration modern teams need to move fast without missing critical issues.
But this isn’t about definitions. It’s about alignment.
Your testing model has to fit your release velocity, your infrastructure, your risk thresholds, and most importantly, your ability to act.
If you’re shipping features weekly but still testing once a quarter, or if you’re buried under scanner alerts with no clear prioritization, you’re not testing, you’re accumulating risk.
In this guide, we’ll break down:
- The core differences in Pentesting vs PTaaS vs Automated Pentesting
- Where each model thrives and where it falls short
- How to choose the right approach based on your technical maturity, team structure, and business goals
Security testing isn’t about checking a box anymore. It’s about building a feedback loop that closes risk faster than attackers can find it.
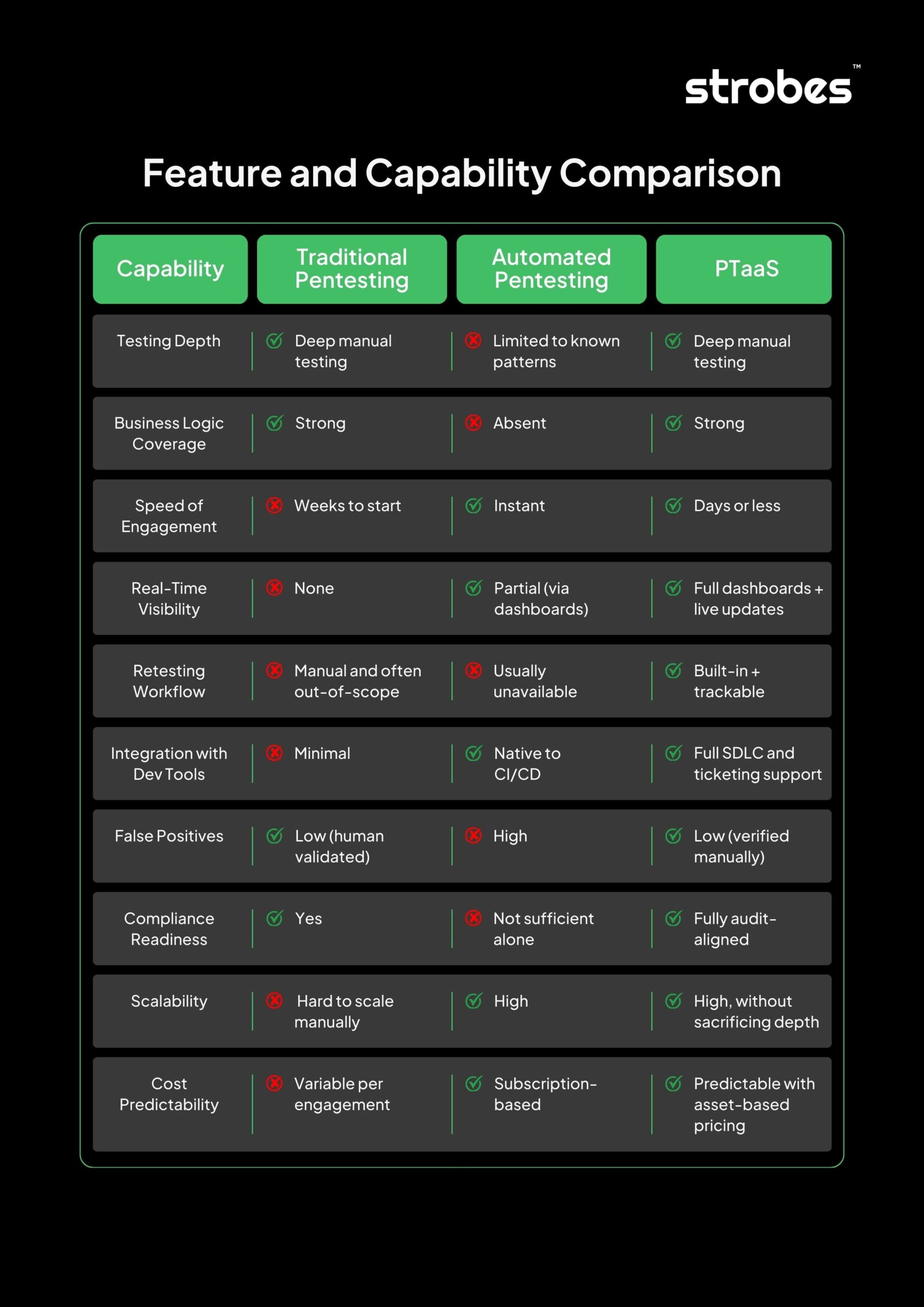
Feature and Capability Comparison
Choosing a security testing model isn’t just about what sounds modern or what checks a compliance box, it’s about what works operationally inside your environment.
Below is a side-by-side comparison that covers the most critical factors: speed, depth, integration, retesting, and more. Use this as a practical benchmark to evaluate your current model, or to make the case for change.
Takeaway
- Traditional Pentesting gives you depth but lacks speed, visibility, and repeatability.
- Automated Pentesting offers coverage and frequency, but misses context and critical logic flaws.
- PTaaS is the only model that combines expert-driven testing, platform-level transparency, and operational alignment across engineering, security, and compliance.
Let’s understand Pentesting vs PTaaS vs Automated Pentesting in detail.
Traditional Pentesting
Traditional pentesting is where most security programs began and in some cases, where they’re still stuck.
This model is human-led. A security team or external consultant manually simulates real-world attack techniques against scoped assets: web apps, APIs, infrastructure, or internal systems. The engagement typically lasts a few weeks, followed by a static report containing a list of findings, ranked by severity.
For years, this was the gold standard. And in some contexts, it still holds weight.
Where Traditional Pentesting Still Delivers
- Business Logic Testing: It’s excellent at identifying complex logic flaws, chained exploit paths, and abuse scenarios that scanners miss entirely.
- Red Team Exercises: When the goal is to test detection and response, not just vulnerabilities, traditional pentesting enables more creative, human-driven techniques.
- Regulatory Compliance: For frameworks like PCI-DSS, ISO 27001, SOC 2, and HIPAA, traditional pentesting remains a checkbox item for annual audits.
- Targeted Deep-Dive Engagements: Legacy ERP systems, high-risk financial applications, or healthcare platforms often require this level of scrutiny.
The Operational Gaps That Make It Hard to Scale
Despite its depth, traditional pentesting doesn’t fit modern SDLCs very well.
- Point-in-Time Only: It gives you a snapshot of your security posture, but the moment code changes, that snapshot becomes obsolete.
- Slow Turnaround: Reports often arrive weeks after testing begins. By then, your dev teams have already moved on to the next sprint.
- Limited Collaboration: Communication with pentesters is usually minimal, static, or delayed. There’s no live visibility into what’s being tested or found in real time.
- No Retesting Workflow: Fixing a vulnerability doesn’t mean it’s validated. Retesting is either manual, out of scope, or never happens, which breaks your SLA tracking.
When Traditional Pentesting Becomes a Bottleneck
It’s not that traditional pentesting is broken, it’s just misaligned with how most engineering and product teams now operate.
In high-velocity environments, where apps release multiple times per month (or per week), a model that relies on manual scope setting, static timelines, and postmortem reporting becomes more of a blocker than a value driver.
That’s when leadership starts asking hard questions:
- “Why are we still finding the same issues every quarter?”
- “Why does this report have findings from a build that’s already outdated?”
- “Why aren’t we fixing faster?”
And those questions aren’t unfair. They’re just symptoms of a testing model that was built for a slower, waterfall-era pace, not today’s cloud-native, API-first, product-driven world.
Automated Pentesting
If traditional pentesting is slow but deep, automated pentesting is fast but shallow.
This model relies on tooling; scanners, scripts, rule-based engines, to simulate attacks across infrastructure, web apps, APIs, and cloud environments. It’s designed for speed, scale, and repeatability, which makes it especially appealing to fast-moving dev teams and security programs looking for coverage across a large surface area.
But here’s the catch: automation sees what it’s told to look for. Nothing more.
Where Automated Pentesting Makes Sense
- CI/CD Integration: It fits naturally into pipelines. Trigger scans on every commit, pull request, or deployment, and gets results within minutes.
- Baseline Hygiene Checks: Quickly catch misconfigurations, open ports, outdated software, or missing patches across large fleets of assets.
- Asset Inventory + Discovery: Helps maintain visibility across cloud environments, container clusters, and ephemeral workloads.
- Compliance Support: While not sufficient alone, automation does assist in maintaining evidence of continuous scanning for standards like ISO 27001 and SOC 2.
For organizations with massive infrastructure or limited AppSec teams, automated pentesting can serve as the first line of defense, a high-speed filter for obvious issues.
The Limitations That Can’t Be Ignored
What automation gains in speed, it often loses in depth.
- No Business Context: Tools don’t understand how your application works, what logic governs access, or which flaws could actually result in financial or data loss.
- High False Positives: Without human validation, noisy results are common, wasting dev time and eroding trust in findings.
- No Exploit Chaining: It can’t string together multiple low-risk issues to identify a critical path, something human pentesters often excel at.
- No Real Collaboration: Automated reports are often dumped into ticketing systems or spreadsheets, with no contextual explanation or remediation guidance.
- Retesting Is Rare or Nonexistent: Once a fix is pushed, there’s typically no built-in mechanism to revalidate the patch.
Where Automation Falls Short Strategically
Here’s the trap many organizations fall into: assuming that automated pentesting is enough because it “runs all the time.”
But frequency isn’t the same as relevance.
If your scanner is flagging the same low-risk issue every week — or missing business-critical logic flaws entirely, then you’re not reducing risk. You’re just generating noise at scale.
Leaders who rely solely on automated tools often discover too late that:
- Their reports are clean, but the application is still exploitable
- Developers are fixing what’s easy, not what’s impactful
- Compliance boxes are ticked, but attackers still have open doors
In other words, automation isn’t a strategy. It’s a component. Without context, correlation, and confirmation, it won’t close the risk. It will just scan it.
Pentesting-as-a-Service (PTaaS)
PTaaS exists because security leaders wanted the depth of traditional pentesting, but the speed, flexibility, and visibility of modern engineering workflows.
It blends expert-led, manual testing with a SaaS-based delivery model. That means the core work; finding real, impactful vulnerabilities is still done by humans. But everything else, from scheduling to reporting to retesting, happens through a platform designed for integration, collaboration, and speed.
It’s not just a service. It’s a system.
What Makes PTaaS Different
- Continuous Engagement: No need to wait weeks to start. Many PTaaS platforms enable testing to begin within days or even hours as soon as scopes and assets are defined.
- Real-Time Dashboards: See testing progress, findings, and status updates in real time. No more blind waiting for a final report.
- Built-In Retesting Workflows: Once a vulnerability is fixed, the same platform allows you to request a retest and confirm closure, often within hours.
- DevSecOps Integration: Findings are pushed directly into Jira, GitHub, or your ticketing system. Engineers can see context, talk to testers, and work efficiently.
- Human + Tool Hybrid: Tools automate the repetitive tasks (recon, scanner-driven checks), while pentesters focus on business logic, chaining, and impact.
PTaaS doesn’t just make pentesting faster. It makes it continuous, collaborative, and measurable.
The Strategic Advantages for Modern Teams
- Faster Remediation Cycles: Real-time access and integrations mean developers aren’t waiting weeks to act. They can fix and revalidate within the same sprint.
- Higher Signal-to-Noise Ratio: Because findings are human-validated, teams aren’t drowning in false positives. Every issue reported is actionable.
- Stronger SLA Tracking: Time-to-remediate, time-to-retest, and overall closure metrics become trackable, helping you prove value to both internal and external stakeholders.
- Scalability with Depth: Whether you’re testing 5 apps or 500, PTaaS platforms can scale without compromising on logic coverage or attacker realism.
Why PTaaS Aligns with Business and Engineering Goals?
What makes PTaaS especially powerful is that it doesn’t fight the way your teams already work, it adapts to them.
Whether you’re releasing twice a month or ten times a day, PTaaS can plug into your SDLC and support continuous risk validation without slowing down velocity.
Security leaders can show measurable outcomes like:
- Reduced MTTR (Mean Time to Remediate)
- Verified fix rates
- Improved remediation SLAs across business-critical applications
- Compliance support with audit-ready reporting
And unlike traditional models, PTaaS doesn’t treat testing as an event. It becomes an ongoing, integrated process, one that supports collaboration, accountability, and outcomes that extend beyond a PDF.
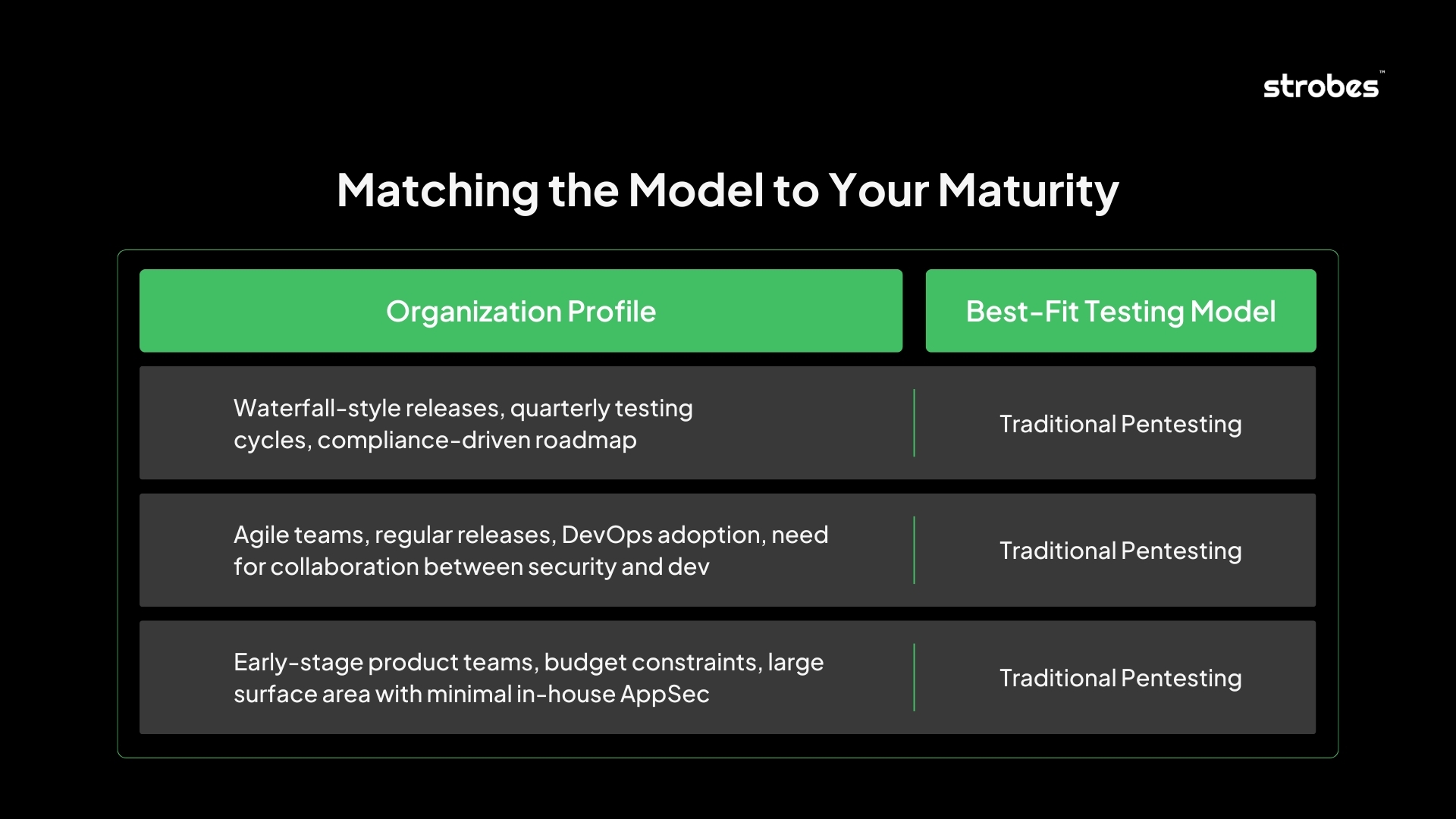
Testing Model Selection Framework
Choosing between Pentesting vs PTaaS vs Automated Pentesting isn’t about picking the “best” model, it’s about selecting the right model for where your organization is today, and where it’s headed.
This framework gives you a decision lens based on release cycles, security maturity, team structure, and risk tolerance.
Matching the Model to Your Maturity
 Questions to Help You Decide
Questions to Help You Decide
Ask these internally before committing to a model:
- How frequently do you deploy changes to production?
- Are your most critical vulnerabilities tied to logic errors or misconfigurations?
- Do developers actively collaborate with security, or is security still a separate gate?
- Are you struggling to track vulnerability SLAs and closure metrics?
- Do you need audit-ready reports that align with regulatory timelines?
Why One Size Doesn’t Fit All
Many organizations mix models, and that’s okay. In fact, that’s often the mature path.
- Use traditional pentesting for deep audits of legacy systems, red team simulations, or compliance snapshots.
- Use automation for surface-level hygiene, asset discovery, and CI/CD feedback.
- Use PTaaS for business-critical applications where depth, speed, and integration all matter, especially across fast-moving product teams.
Don’t select the model based on hype or budget alone. See how well a model supports your risk reduction, developer experience, and operational velocity.
The Role of Retesting in Modern Security
Finding a vulnerability isn’t the win. Fixing it and proving it’s fixed is where the impact lies.
Yet in many testing programs, retesting is either skipped, delayed, or not scoped at all. The result? Teams mark issues as resolved in dashboards, but the actual exploit path remains open.
Why Retesting Matters?
- Security SLAs rely on confirmation, not assumptions:
A fix that hasn’t been verified is just an educated guess, not a closed risk. - Audit and compliance expectations are evolving:
Standards like ISO 27001, PCI-DSS, and SOC 2 increasingly require not just discovery, but proof of remediation. - Developers need fast feedback loops:
No one wants to “fix” the same issue twice because the first patch was incomplete, or never retested. - Risk-based programs demand closure metrics:
Without retesting, metrics like MTTR (mean time to remediate) and fix-rate accuracy become inflated or unreliable.
Traditional and Automated Models Often Fall Short
- Traditional pentesting includes retesting as a separate, often billable engagement, with delays that can stretch into weeks.
- Automated tools rarely include any meaningful retesting. At best, they re-scan, without understanding the context of the fix or whether it addressed the root cause.
And that’s where PTaaS becomes a game-changer.
How PTaaS Brings Retesting Into the Workflow?
- Built-in retesting requests — triggered automatically when a ticket is marked as resolved
- Fast turnaround times — often validated within hours, not weeks
- Trackable SLAs — retesting linked to severity, timelines, and closure goals
- Shared visibility — developers, security teams, and auditors can all view retest outcomes on the same platform
Metrics That Actually Matter
Retesting makes it possible to measure security operations in a way that reflects actual risk reduction:
- Time to Retest (TTR): How quickly are we confirming fixes?
- Verified Fix Rate: What percentage of issues were closed correctly the first time?
- SLA Adherence: Are we meeting remediation timelines across business-critical assets?
Without retesting, you’re not reducing risk, you’re just completing a task list.
Security Testing ROI Breakdown
Security testing is often seen as a cost center until it prevents an incident, accelerates remediation, or satisfies an audit without fire drills. The right testing model doesn’t just uncover vulnerabilities. It reduces waste, speeds up decisions, and protects business-critical assets with measurable outcomes. Let’s break down how each approach impacts the bottom line.
Direct and Hidden Costs of Testing Models
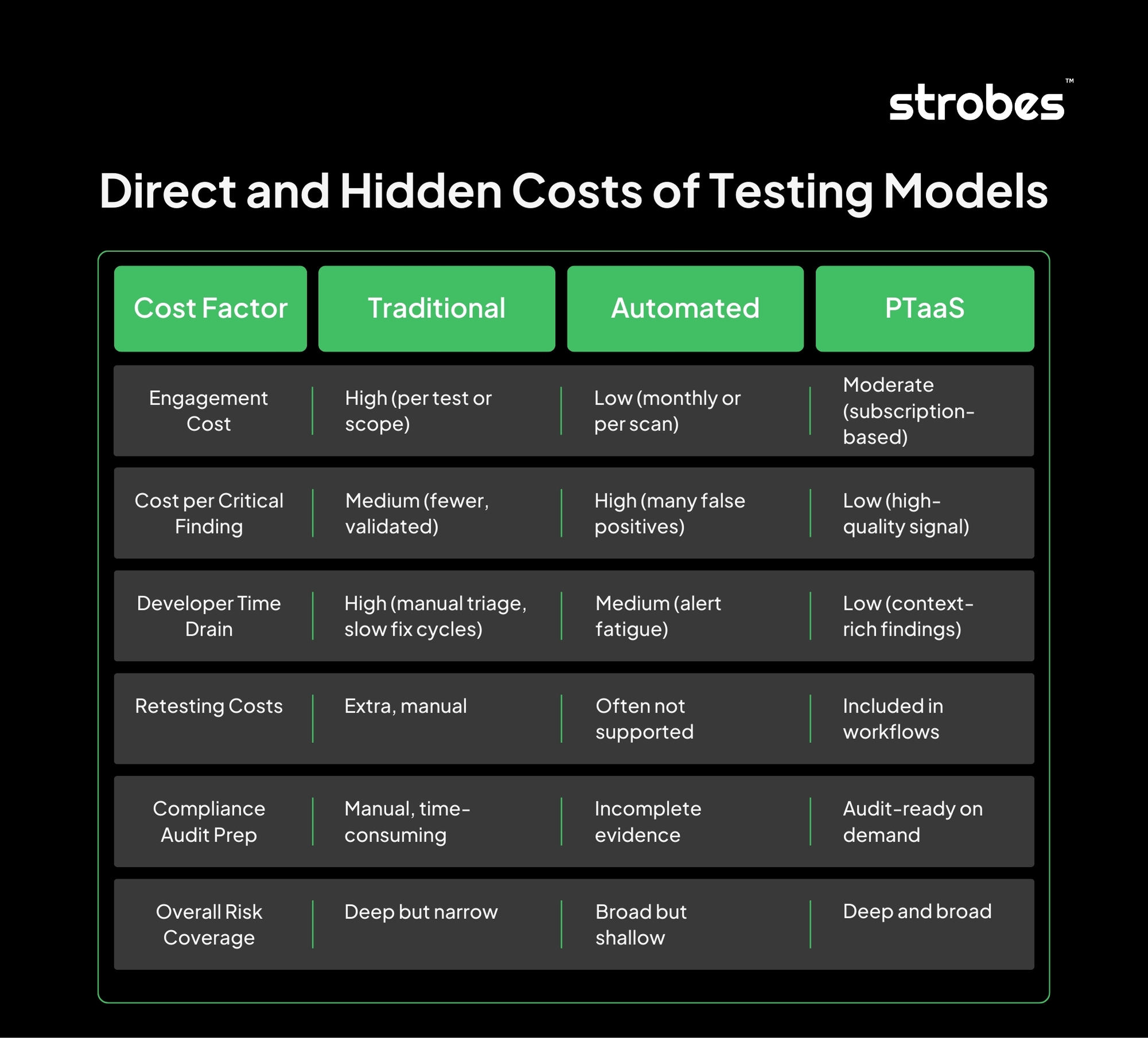
Operational ROI Metrics That Matter
- Mean Time to Remediate (MTTR): PTaaS reduces fix delays through faster visibility, direct collaboration, and fewer distractions.
- Reduction in Duplicate Effort: Validated findings cut back rework and repeated triage cycles.
- Security Debt Visibility: Knowing what’s fixed and what’s still open helps plan and prioritize resources more effectively.
- Compliance Efficiency: Export-ready reports, fix verification, and retesting timelines support faster audits with less back-and-forth.
Strategic Value Over Time
- Traditional pentesting gives assurance once a year, often after the fact.
- Automated tools provide frequency, but not confidence.
- PTaaS delivers both. Depth from human expertise, velocity from automation, and clarity from collaboration.
What looks cheaper on paper (like automated scanning) often turns out costlier in engineer time, missed risks, or patching the same issue multiple times.
The Future of Pentesting
Security testing isn’t static and neither are the systems it protects. As cloud-native architectures, microservices, and AI-driven applications become the norm, traditional testing models are already being pushed to their limits. What’s coming next isn’t just evolution, it’s convergence.
Continuous Validation Will Replace One-Time Testing
Security testing is shifting from scheduled events to ongoing validation pipelines. Instead of testing quarterly and hoping for the best, modern programs are embedding testing into every release cycle.
- PTaaS platforms are already enabling this, with always-on engagements tied to release schedules, asset changes, or SLA thresholds.
- Security becomes part of the CI/CD fabric, not a post-deploy checkpoint.
This isn’t about “shift left” anymore, it’s about staying embedded.
Business Risk Context Will Drive Testing Priorities
Not every vulnerability deserves equal attention. The future belongs to risk-aware testing, where severity is shaped by exploitability, business impact, and threat intelligence.
- Tests won’t just ask, “Is this exploitable?”
They’ll ask, “Is this being exploited in the wild, and does it affect crown-jewel assets?”
This is where platforms like PTaaS integrate with attack surface management (ASM), threat intel feeds, and risk scoring engines to help prioritize what truly matters.
AI Will Enhance Human Testing, Not Replace It
There’s no shortage of buzz around AI in security, and it’s already making an impact. But AI isn’t here to replace skilled pentesters. It’s here to amplify them.
- Large Language Models (LLMs) can assist with payload generation, recon automation, and exploit simulation.
- Machine learning models can predict exploit chains, correlate findings across tools, and suggest fixes faster.
The result? Faster, smarter testing, but still guided by human insight, especially when it comes to logic flaws, abuse scenarios, and interpreting risk in context.
Metrics Will Become the Language of Security Programs
Boards and executives are asking better questions, and security teams are responding with better answers. Metrics like:
- Time to retest
- Fix rate accuracy
- SLA adherence per asset class
- Risk reduction per pentest cycle
…are becoming the standard. The testing model you choose will directly impact whether you can track, measure, and report these metrics with confidence.
If your testing model doesn’t adapt to speed, integrate with engineering, or support real-time risk visibility, it won’t survive the next audit, let alone the next incident.
Final Thoughts
Security testing isn’t about running scans. It’s about making decisions with confidence.
And when you look at Pentesting vs PTaaS vs Automated Pentesting, the question isn’t which is “best”, it’s which one actually works for your environment, with your teams, and against your real risks.
- Traditional pentesting still has value, especially for compliance-heavy or highly sensitive systems. But it wasn’t designed for fast release cycles or agile teams.
- Automated pentesting is great for coverage and speed. But coverage without context leads to false assurance, noise, and wasted effort.
- PTaaS delivers a more sustainable model: continuous, collaborative, and outcome-focused. It merges expert-led testing with integrated workflows, real-time dashboards, and validation that doesn’t just check the box, it closes the risk.
Whatever model you choose, the end goal stays the same: Find what matters, fix it faster, and prove it’s fixed, with confidence. That’s not just good security. That’s good business.
Want to see how it works in action? Book a free demo today and take the next step toward smarter, faster security testing.

Related Reads:
- Traditional Vs Modern Penetration Testing (PTaaS): Choosing the Right Approach for Your Security Needs
- Penetration Testing as a Service (PTaaS): The Future of Agile Security
- Bug Bounty vs Penetration Testing as a Service (PTaaS): Complementary or Competing Approaches
- Integrating Attack Surface Management and Penetration Testing as a Service
- 3 Reasons Why Penetration Testing Is Needed and Why Traditional Pentesting Isn’t Working for You
- Why Penetration Testing Is Important: Enhancing Security & Reducing Cyber Risks
- Solution: Pentesting as a Service

 Questions to Help You Decide
Questions to Help You Decide