Modern enterprises are facing an unprecedented challenge, attack surfaces are growing faster than they can be secured. Without attack surface monitoring, cloud services, SaaS tools, third-party integrations, and remote work only accelerate this sprawl.
A recent report found that 62% of organizations reported an increased attack surface over the past two years due to third-party connections, IoT, and public cloud usage. Even more concerning, nearly 70% of organizations faced at least one cyberattack from unknown or poorly managed internet-facing assets.
Yet many security teams remain stuck in a cycle of chasing alerts. They respond reactively to incoming notifications, often with no clear sense of which issues truly matter to their business. This approach burns out resources and leaves critical exposures unaddressed.
Attack Surface Monitoring (ASM) flips this paradigm. It helps organizations focus on risk management instead of firefighting, providing a live, comprehensive view of external assets and their vulnerabilities.
What Is Attack Surface Monitoring?
Attack Surface Monitoring is the process of constantly discovering, monitoring, and assessing all external-facing assets to identify risks before attackers do.
Unlike periodic vulnerability scans or one-off assessments, ASM operates in real time. It provides a living inventory of every asset connected to the internet, including servers, APIs, cloud instances, exposed databases, and more.
The key difference? ASM doesn’t just report issues. It ties each exposure to business context, helping teams prioritize based on actual risk instead of raw counts.
Why Chasing Alerts Doesn’t Work Anymore

Alert-driven security models have been the norm for decades. But in today’s complex environments, they’re falling short. Here’s why:
1. Too Many Alerts, Too Little Value
Most security tools flood teams with alerts, many of them low priority or false positives. Analysts waste hours triaging noise, which slows down response times for real threats.
2. Blind Spots From Shadow Assets
Shadow IT, misconfigured cloud services, and forgotten assets create gaps in visibility. These assets often go unmonitored, giving attackers easy access points. Gartner predicts that by 2026, 75% of organizations will suffer from security failures due to unmanaged attack surfaces
3. No Business Context
Alerts often lack context about how critical an asset is to the organization. A vulnerability on a test server isn’t as urgent as one on a production database but most systems treat them equally.
4. Burnout and Fatigue
Constant alerts overwhelm analysts, increasing turnover rates and leaving teams in a reactive mode. This reactive posture doesn’t scale in environments where assets and threats change daily.
To succeed, organizations need a model that provides visibility, context, and prioritization, not just notifications.
From Reactive Alerts to Proactive Risk Management
Moving from alert-centric operations to risk-based security requires a mindset shift. Here’s what it looks like:
Focusing on What Matters Most
Rather than treating every alert as equally important, ASM enables teams to zero in on assets that are both exposed and critical to business operations.
Contextualizing Exposures
ASM correlates asset data with threat intelligence, helping teams understand:
- Which assets are internet-facing?
- Which vulnerabilities are actively being exploited in the wild?
- What’s the potential business impact of a compromise?
Staying Ahead of Attackers
Continuous monitoring detects changes in your external environment, newly exposed assets, DNS changes, and misconfigured storage buckets before attackers do.
Reducing Noise and Fatigue
By filtering out low-risk issues and focusing on high-value targets, ASM helps teams work smarter, not harder.
Real-World Impact
A large healthcare provider that adopted ASM reported a 67% reduction in critical vulnerabilities left unresolved past SLA, proving that context-based prioritization directly improves remediation timelines.
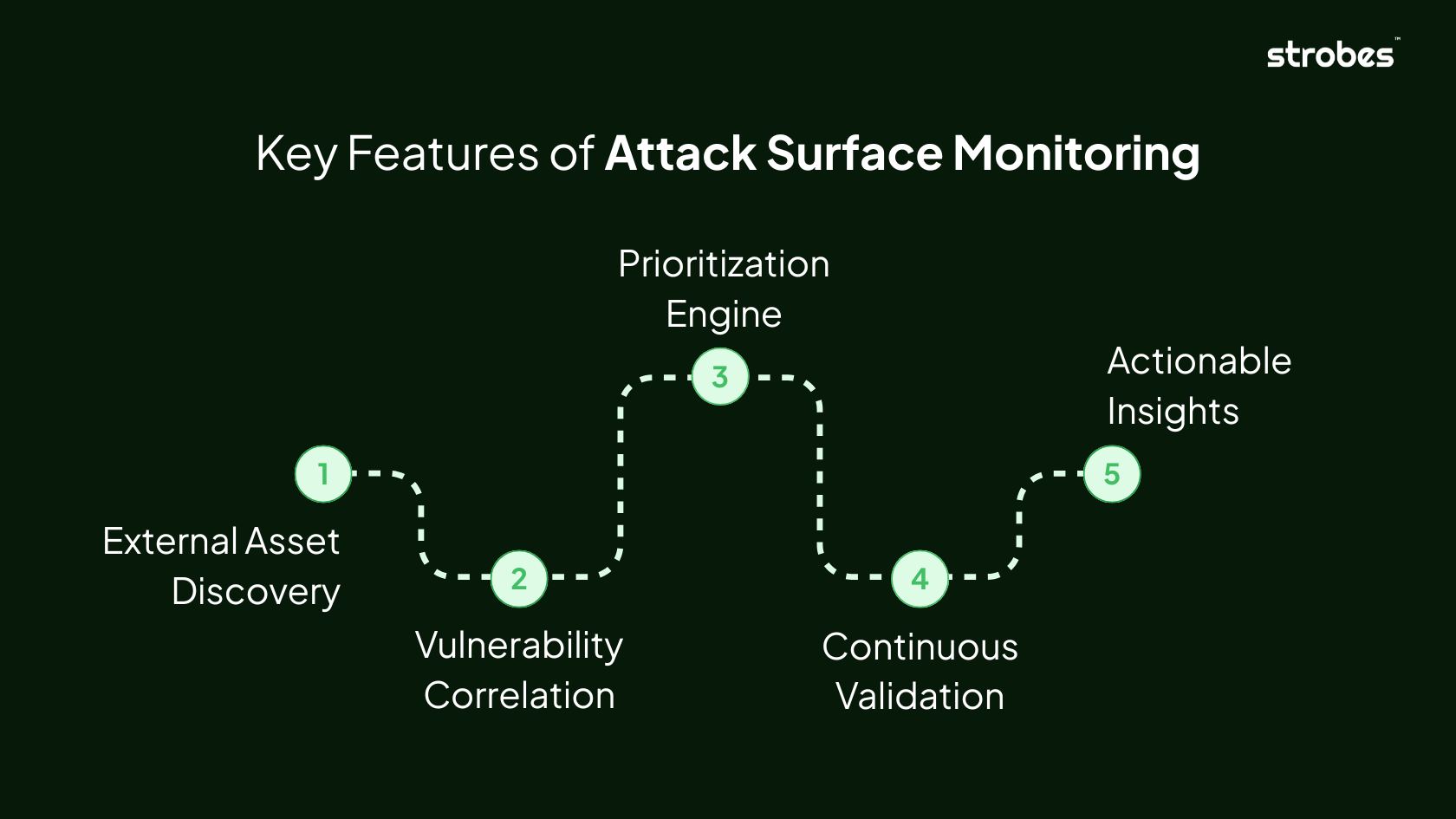
Key Features of Attack Surface Monitoring
- External Asset Discovery: ASM scans the internet to map your entire external footprint including shadow IT, rogue cloud instances, and forgotten domains.
- Vulnerability Correlation: It connects asset data with vulnerability intelligence to assess risk in context.
- Prioritization Engine: Not every exposure needs immediate action. ASM uses exploitability scores and business impact analysis to rank issues intelligently.
- Continuous Validation: After remediation, ASM verifies that fixes hold up against real-world attack techniques.
- Actionable Insights: It transforms raw findings into workflows for teams, integrating with ticketing systems and SIEM tools for seamless handoff.
Benefits of Continuous Monitoring for Enterprises
Deploying ASM brings measurable improvements:
- Reduced Alert Fatigue: By filtering low-priority findings, teams focus only on critical issues.
- Complete Visibility: A single source of truth for all internet-facing assets.
- Faster Detection: Spot new exposures within minutes, not weeks.
- Improved Collaboration: Shared visibility between SecOps, DevOps, and IT.
- Stronger Reporting: Clear metrics for leadership and regulatory compliance.
How to Get Started With Attack Surface Monitoring
Adopting ASM doesn’t require a full overhaul. Here’s how to begin:
1. Build a Comprehensive Asset Inventory
Start by identifying all internet-facing assets across cloud, SaaS, and on-prem environments. Automated discovery tools are essential here.
2. Define Business Context
Assign criticality levels to assets based on their role in operations.
3. Integrate With Existing Tools
Connect ASM to your SIEM, SOAR, and vulnerability management systems for seamless workflows.
4. Establish KPIs
Track metrics like:
- % of unknown assets discovered
- Reduction in high-risk exposures
- MTTD and MTTR improvements
5. Automate Monitoring
Enable continuous scanning and validation to ensure new assets are secured as they appear.
Why Leading Teams Are Making the Switch
A global retail chain adopted ASM after multiple incidents tied to forgotten cloud assets. Within six months, they discovered 1,200 unmanaged assets, including exposed storage buckets and APIs.
By prioritizing based on business risk, they cut their remediation time by 50% and reduced high-risk exposures by 67%. This is the power of shifting from alerts to risk management.
Strobes ASM
Strobes Attack Surface Management (ASM) is built to give organizations complete visibility into their external-facing assets. where businesses rely heavily on cloud services, SaaS platforms, and third-party integrations, it’s easy for assets to go unnoticed until they’re exploited. Strobes ASM continuously scans and maps your entire external environment to ensure nothing is left exposed.
But it doesn’t stop at discovery. Strobes ASM is great at identifying low-hanging fruit, the common misconfigurations and exposures that attackers often target first. These include open ports, exposed databases, outdated services, weak SSL configurations, and forgotten subdomains. Such issues are prime targets for script kiddies running automated scans and large campaign groups launching wide-scale attacks.
With Strobes ASM, you don’t just get a list of assets; you get actionable insights. Each exposure is tied to contextual risk scoring so your team can prioritize and remediate critical issues faster. This approach helps organizations stay ahead of opportunistic attackers by closing gaps that are easy to exploit but often overlooked in traditional vulnerability management.
Conclusion
Traditional approaches leave security teams stuck in endless alert triage while attackers quietly exploit unmanaged assets. Attack Surface Monitoring changes this by giving you real-time visibility across your external environment and helping you prioritize exposures that pose real business risk.
At Strobes Security, we built our platform to do exactly that map your attack surface, monitor it 24/7, and empower your team to respond faster with actionable insights.
Stop firefighting. Start managing your risk proactively.
Book a personalized demo today and watch how your security operations transform with continuous monitoring.