Attack Surface Management
Get complete visibility of your attack surface in one platform. Continuously discover assets, monitor domains, detect zero-days, and uncover misconfigurations, with actionable insights that accelerate remediation and reduce business risk.






Secure Your Attack Surface with Strobes ASM in 3 Steps
Add Assets
Provide your domains, IP ranges, and organization names to create a complete inventory of assets for continuous monitoring.
Monitor & Visualize
Track phishing, malware, DNS squatting, vulnerabilities, and other threats in real time to gain actionable insights instantly.
Remediate Risks
Prioritize vulnerabilities by severity and business impact, then start patching and closing critical threats efficiently across all assets.
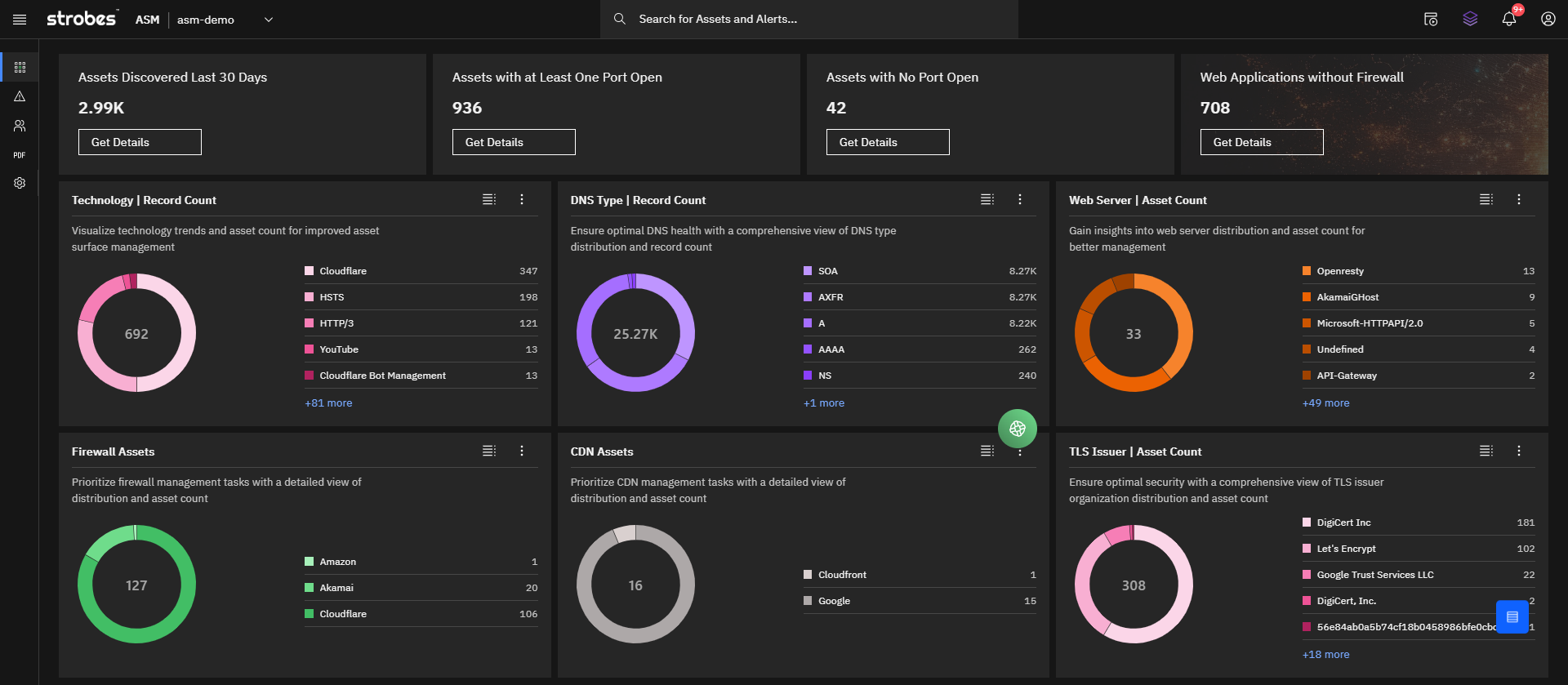
Checkout How Strobes ASM Works
How Attack Surface Management Works
Why Strobes ASM
Shadow IT Discovery
Reveal unmanaged applications, forgotten domains, and hidden assets across your environment, eliminating blind spots that attackers can exploit.
Risk Context First
Prioritize vulnerabilities by exploitability, asset value, and business impact, ensuring teams address the most critical exposures first.
Guided Remediation
Support faster response with contextual insights, automation, and integrations that guide teams on resolving exposures efficiently.
Continuous Monitoring
Track domains, cloud workloads, and configurations in real time, maintaining accurate visibility across your entire attack surface.
3
Assets Discovered
Continuous asset discovery across environments, ensuring unmatched visibility and eliminating hidden blind spots.
100
Vulnerabilities Identified
Actionable, prioritized findings that reduce noise and highlight the exposures that matter most to your business.
10
Domains Monitored
External attack surface coverage with active monitoring, keeping domains and digital assets protected around the clock.
1000
Hours Saved
Automated correlation and insights that streamline processes, freeing teams to focus on high-value security tasks.