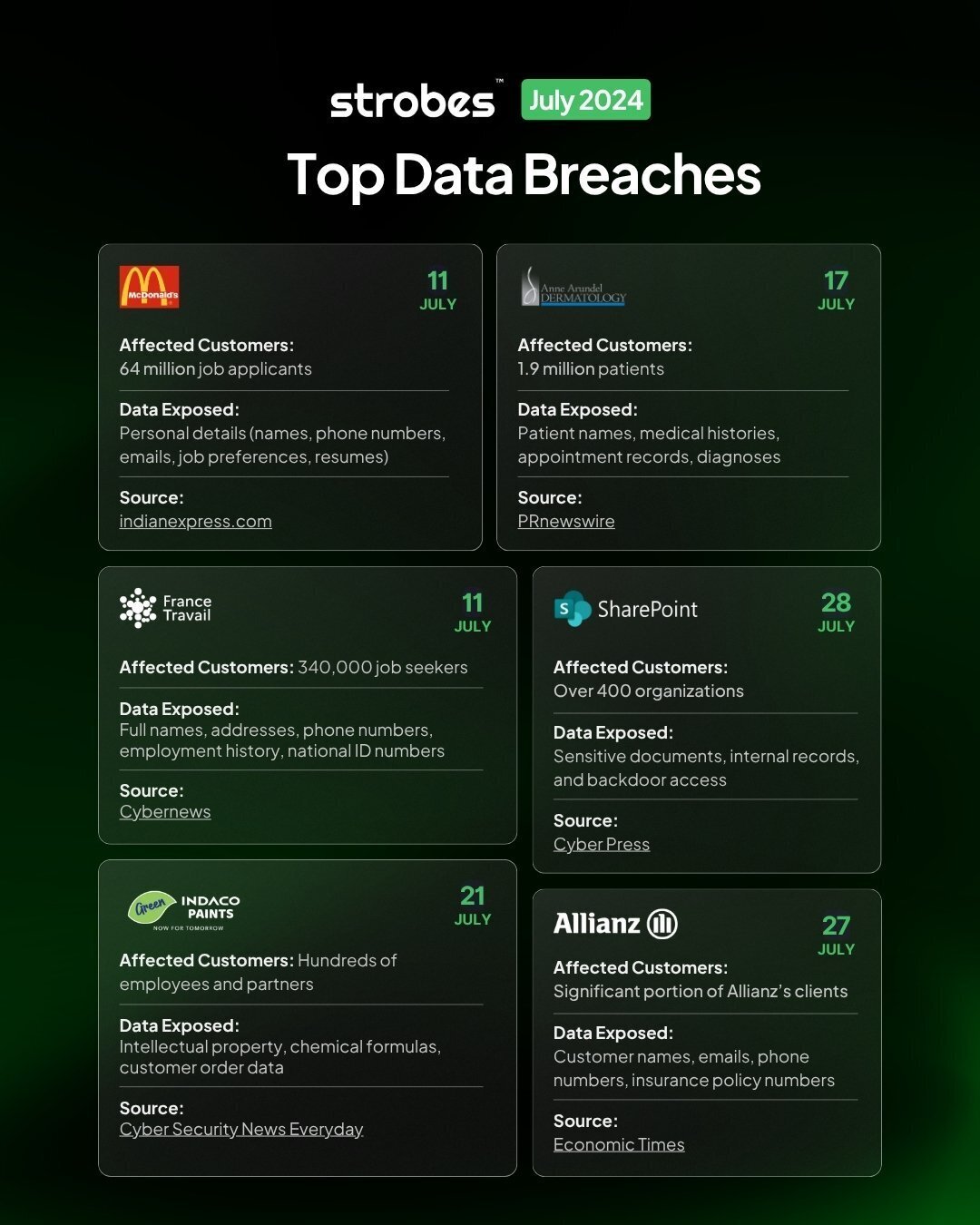
July 2025 was a turbulent month for cybersecurity, with several high-profile breaches exposing critical vulnerabilities across industries. From weak access controls to vendor mismanagement, these incidents underscored the need for a more robust, proactive security approach. Here’s an in-depth look at the data breaches in July 2025, the data exposed, and the key lessons to strengthen your organization’s defenses.
1. McDonald’s Job Applicant Data Exposure
McDonald’s recruitment chatbot was compromised due to a default password (“123456”). Attackers exploited this vulnerability to gain access to sensitive applicant data stored in poorly secured databases.
The breach exposed 64 million applicants’ PII, including:
- Full names
- Email addresses
- Phone numbers
- Resumes containing birthdates, educational history, and work experience
The breach highlights the critical importance of enforcing strong password policies and multi-factor authentication. Privileged account management and proper database segmentation could have prevented the breach.
2. Anne Arundel Dermatology Breach
Ransomware operators infiltrated the provider’s network, likely via compromised RDP credentials or an unpatched vulnerability. Once inside, they moved laterally to escalate privileges, exfiltrating and encrypting sensitive data.
The breach impacted 1.9 million patients, exposing:
- Full names
- Birthdates
- Diagnoses
- Insurance details
The lack of network segmentation and endpoint monitoring allowed the attackers to operate undetected. Implementing EDR tools, network segmentation, and regular vulnerability scanning would have reduced the attack surface and limited lateral movement.
3. France Travail National Employment Agency Breach
Attackers used infostealer malware to compromise a third-party training partner’s system, which allowed them to bypass two-factor authentication (2FA) by intercepting OTP tokens or hijacking sessions.
The exposed data affected 340,000 job seekers, including:
- Full names
- Addresses
- Phone numbers
- National ID numbers
The breach underscores the risks posed by third-party vendors and the need for stronger session management and device security. Combining 2FA with device monitoring and behavioral analysis would help prevent similar breaches.
4. Microsoft SharePoint “ToolShell” Exploits
Hackers exploited a zero-day vulnerability in Microsoft SharePoint using ToolShell scripts to gain admin privileges. They uploaded web shells to maintain access and move laterally across systems, extracting sensitive data.
The breach exposed:
- Sensitive internal documents
- Access credentials
- Procurement and architectural blueprints
This incident highlights the importance of zero-day vulnerability management and rapid patching. Web application firewalls (WAFs) and advanced packet inspection could have helped detect the malicious web shell activity sooner.
5. Indaco Data Leak
Indaco, a leading paint manufacturer, was breached via spear-phishing or by exploiting outdated VPN gateways. Attackers exfiltrated intellectual property (IP), including paint formulas and customer order data, and posted it online.
The exposed data included:
- Proprietary formulas
- R&D communications
- Customer orders
The breach underscores the need for regularly updated VPN software and the importance of protecting intellectual property. Strong encryption and access control should be standard for handling IP.
Trusted by leading enterprises like, GHX, Zoho, Darwinbox, Tricenties, and SHL
Strobes helped organizations continuously manage threats, reduce vulnerabilities, and stay compliant, powered by AI-driven security expertise.
6. Allianz Life Insurance Company Breach
A social engineering attack targeted Allianz’s third-party CRM vendor, using impersonation to gain access to sensitive customer data stored in the CRM.
The exposed data included:
- Full names
- Email addresses
- Phone numbers
- Insurance policy numbers
This breach highlights the risks of third-party vendors having privileged access to critical systems. Strengthening employee verification and implementing zero-trust principles for third-party access could have prevented this attack.
Bottomline: Top 6 Data Breaches in July 2025
The July data breaches highlight various attack vectors, from weak access controls to vendor mismanagement. To reduce risk, organizations must adopt proactive cybersecurity strategies and leverage AI-driven solutions.
- Patch management and zero-day vulnerability monitoring are critical to mitigating risk.
- Strong password policies and multi-factor authentication (MFA) are essential to securing sensitive systems.
- Third-party vendor management and continuous monitoring can protect against supply chain vulnerabilities.
- Data encryption, session management, and endpoint monitoring are key to protecting sensitive information.
Strobes’ unified CTEM platform – RBVM, ASM, PTaaS, and DAST – gives organizations real-time insights to identify, prioritize, and fix risks.
Schedule a demo with Strobes to see how this AI-driven unified platform can help secure your organization.
Sources:
- McDonald’s Job Applicant Data Exposure – indianexpress.com
- Anne Arundel Dermatology Breach – PRnewswire
- France Travail National Employment Agency Breach – Cybernews
- Microsoft SharePoint “ToolShell” Exploits – Cyber Press
- Indaco Data Leak – Cyber Security News Everyday
- Allianz Life Insurance Company Breach – Economic Times