November has surfaced several high-impact vulnerabilities, earning their spot among the Top CVEs of November 2024. These issues, ranging from remote code execution flaws to authentication gaps, are raising red flags across the cybersecurity landscape. Left unaddressed, they could lead to unauthorized access, data breaches, or disruptions that might impact critical operations.
Understanding what these vulnerabilities mean, why they matter, and how to address them is essential. Here’s everything you need to know about the most critical CVEs this month.
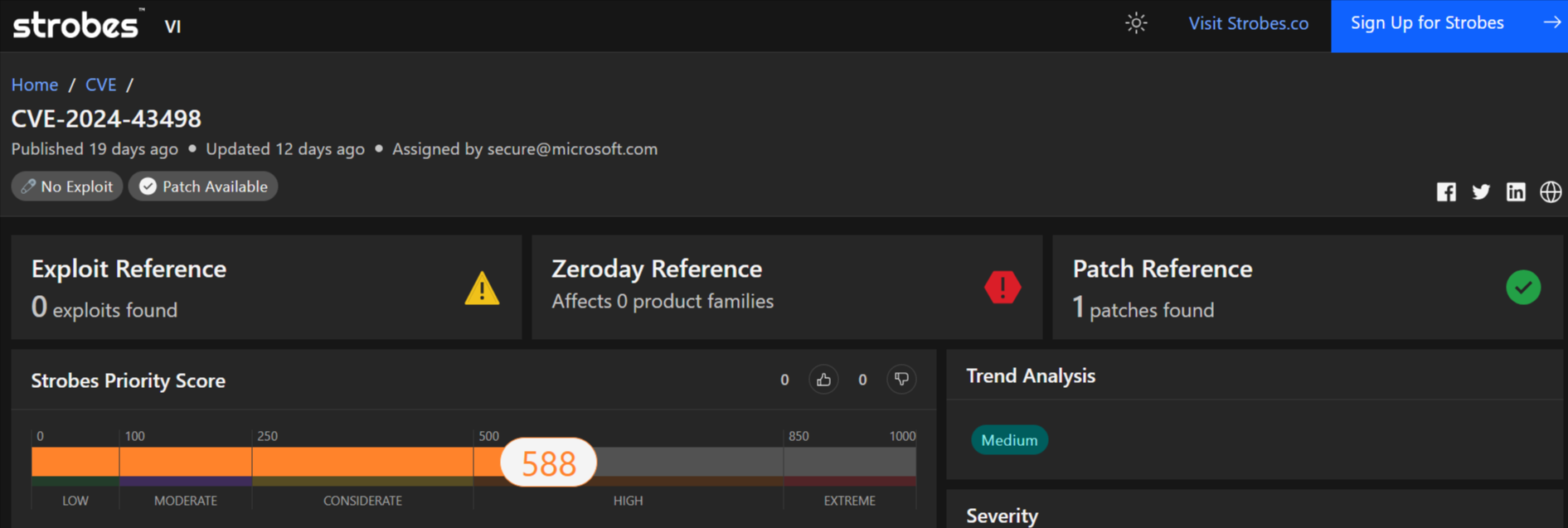
1. CVE-2024-43498: A Critical Vulnerability in .NET Core
CVE-2024-43498 is a critical security vulnerability discovered in the .NET Core framework. This vulnerability could potentially allow remote attackers to execute arbitrary code on affected systems.
Impact
Successful exploitation of this vulnerability could lead to severe consequences, including:
- Remote Code Execution (RCE): Attackers could gain control over vulnerable systems.
- Data Theft: Sensitive information could be stolen.
- System Compromise: Systems could be compromised and used for malicious activities.
Details of the Vulnerability
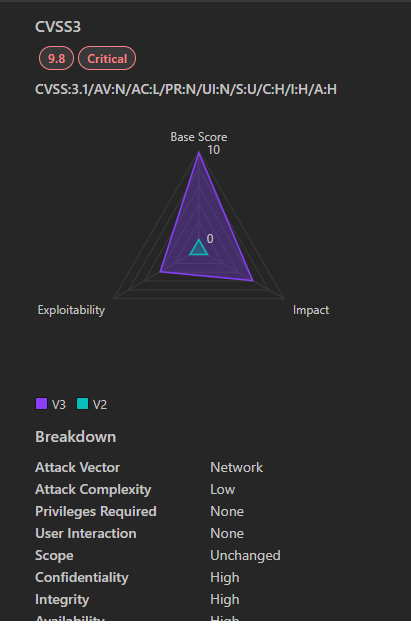
- Severity: Critical
- CVSS Score: 9.8 (CVSS 3.1)
- Affected Products: .NET Core
- Vulnerability Type: Type Confusion Vulnerability
- Exploitability: Remote
The vulnerability stems from a type confusion issue within the .NET Core NrbfDecoder component. This flaw can be exploited by crafting malicious input that could trick the component into misinterpreting data, leading to unexpected behavior and potential code execution.
Mitigation
Microsoft has released security updates to address this vulnerability. It is strongly recommended that all affected systems are patched as soon as possible. To mitigate the risk:
- Apply Security Updates: Install the latest security updates provided by Microsoft.
- Network Segmentation: Isolate vulnerable systems from the internet and other untrusted networks.
- Input Validation: Implement robust input validation and sanitization techniques to prevent malicious input.
- Regular Security Audits: Conduct regular security audits to identify and address potential vulnerabilities.
- Stay Informed: Keep up-to-date with the latest security advisories and patches.
Source:
- National Vulnerability Database (NVD): https://nvd.nist.gov/vuln/detail/CVE-2024-43498
- Microsoft Security Response Center (MSRC): https://msrc.microsoft.com/update-guide/vulnerability/CVE-2024-43498
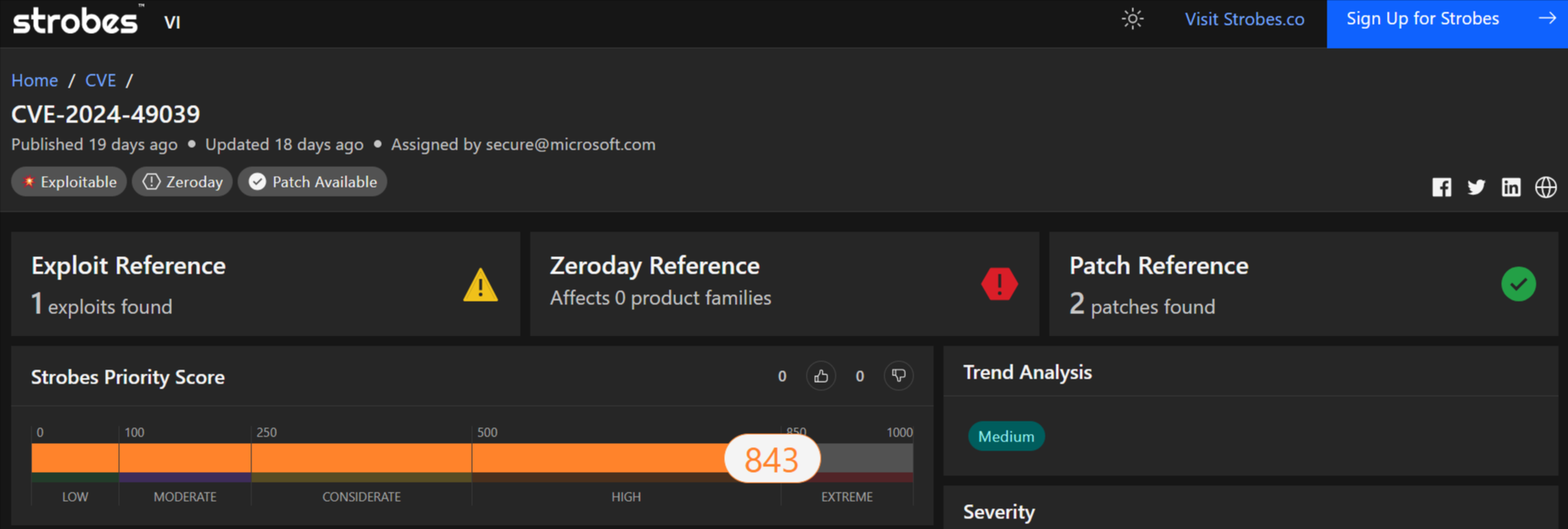
2. CVE-2024-49039: Windows Task Scheduler Elevation of Privilege Vulnerability
CVE-2024-49039 is a critical vulnerability discovered in Microsoft Windows Task Scheduler that could allow an attacker to gain elevated privileges on an affected system. This vulnerability could be exploited by a malicious actor to compromise the security of a system and potentially execute arbitrary code.
Impact
Successful exploitation of this vulnerability could lead to severe consequences, including:
- System Compromise: An attacker could gain control over the affected system.
- Data Theft: Sensitive data could be stolen or exfiltrated.
- Malicious Activity: The compromised system could be used as a launchpad for further attacks, such as spreading malware or launching ransomware attacks.
Details of the Vulnerability
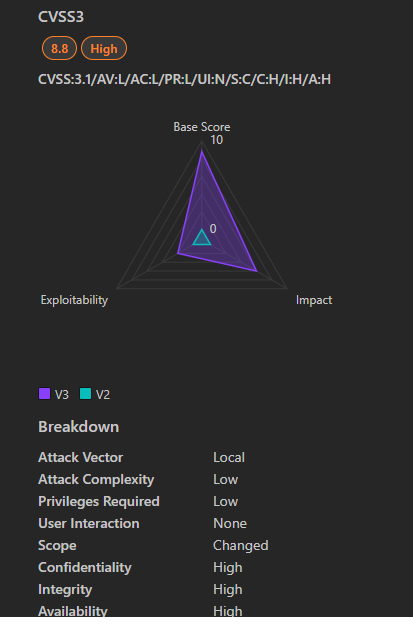
- Severity: Critical
- CVSS Score: 8.8
- Affected Products: Various Microsoft Windows versions
- Vulnerability Type: Elevation of Privilege
- Exploitability: Remote Code Execution
Mitigation
Microsoft has released security updates to address this vulnerability. To mitigate the risk, it is strongly recommended to:
- Install Security Updates: Apply the latest security updates from Microsoft as soon as they are available. These updates will patch the vulnerability and prevent successful exploitation.
- Principle of Least Privilege: Implement the principle of least privilege, granting users only the necessary permissions to perform their tasks. This can help limit the potential impact of a successful attack.
- Network Segmentation: Segment your network to isolate critical systems and reduce the attack surface.
- Regular Security Audits and Monitoring: Conduct regular security audits and monitor network traffic for signs of malicious activity.
- User Awareness and Training: Educate users about the importance of security best practices, such as avoiding suspicious links and attachments, and promptly reporting any unusual behavior.
Source:
- National Vulnerability Database (NVD): https://nvd.nist.gov/vuln/detail/CVE-2024-49039
- Microsoft Security Response Center (MSRC): https://msrc.microsoft.com/update-guide/vulnerability/CVE-2024-49039
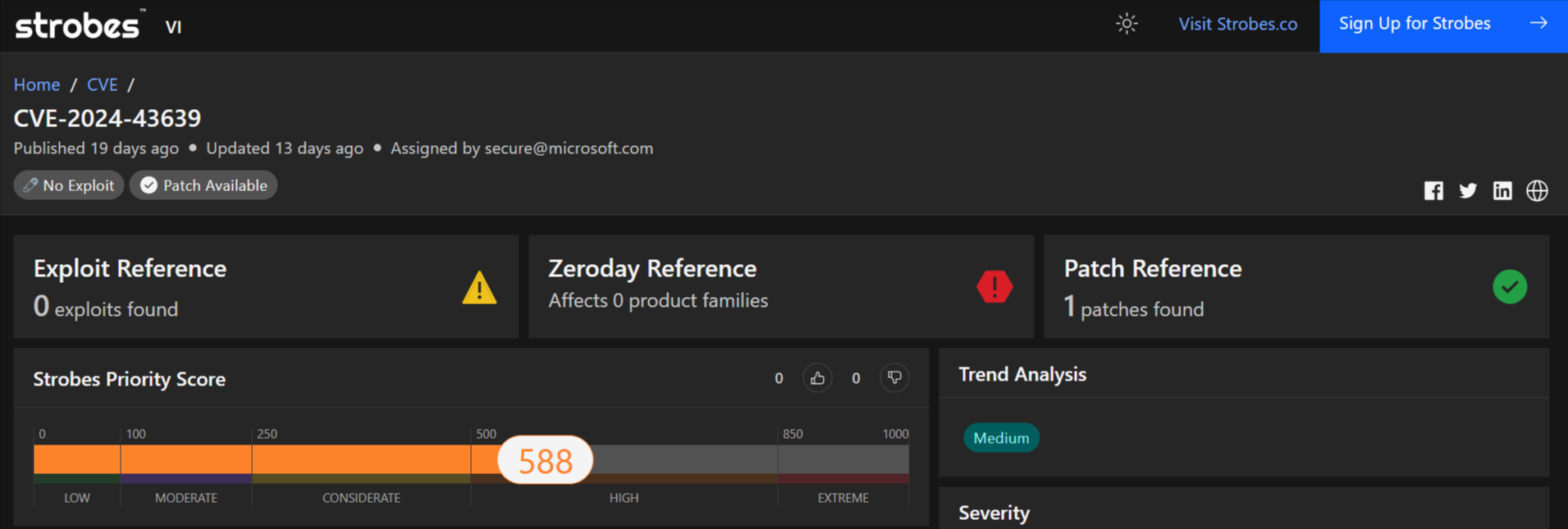
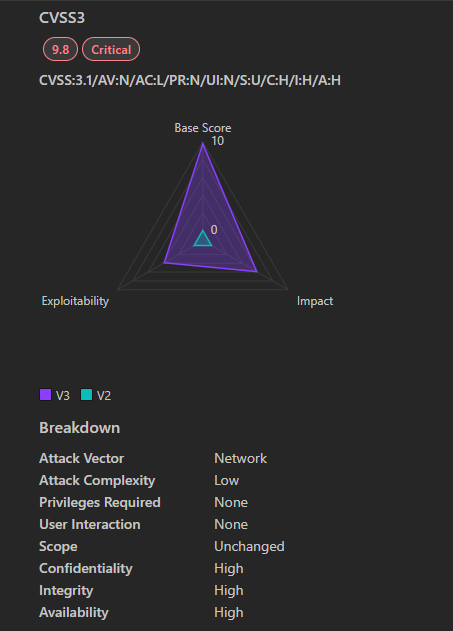
3. CVE-2024-43639: A Critical Windows Kerberos Vulnerability
CVE-2024-43639 is a critical vulnerability discovered in the Windows Kerberos authentication protocol. This flaw allows unauthenticated attackers to remotely execute code on vulnerable Windows systems configured as Kerberos Key Distribution Center (KDC) Proxy Protocol servers.
Impact
Successful exploitation of this vulnerability could have severe consequences, including:
- Remote Code Execution: Attackers can execute arbitrary code on the affected system, potentially gaining full control over it.
- Data Theft: Sensitive data stored on the compromised system could be accessed and exfiltrated.
- System Disruption: Critical system services could be disrupted or disabled.
Details of the Vulnerability
- Severity: Critical
- CVSS Score: 9.8 (CVSS v3.1)
- Affected Products: Windows Servers configured as KDC Proxy Protocol servers
- Vulnerability Type: Remote Code Execution
- Exploitability: Remote, unauthenticated
The vulnerability arises from a weakness in the Kerberos protocol’s handling of certain cryptographic operations. By sending specially crafted requests to a vulnerable KDC Proxy server, attackers can bypass security measures and execute malicious code.
Mitigation
Microsoft has released security updates to address this vulnerability. To protect your systems, it is crucial to:
- Install Security Updates: Apply the latest security updates from Microsoft as soon as they are available. These updates contain the necessary patches to mitigate the vulnerability.
- Network Segmentation: Implement network segmentation to isolate vulnerable systems from the broader network. This can limit the potential impact of a successful attack.
- Monitor Network Traffic: Regularly monitor network traffic for signs of malicious activity, such as unusual network connections or suspicious traffic patterns.
- Keep Software Up to Date: Ensure that all software on your systems is up-to-date with the latest security patches. This includes operating systems, applications, and firmware.
- Implement Strong Password Policies: Enforce strong password policies to prevent unauthorized access to accounts. Use complex passwords that are difficult to guess and change them regularly.
- Enable Multi-Factor Authentication (MFA): MFA adds an extra layer of security by requiring users to provide two or more forms of identification. This can significantly reduce the risk of unauthorized access.
Source:
- National Vulnerability Database (NVD): https://nvd.nist.gov/vuln/detail/CVE-2024-43639
- Microsoft Security Response Center (MSRC): https://msrc.microsoft.com/update-guide/vulnerability/CVE-2024-43639
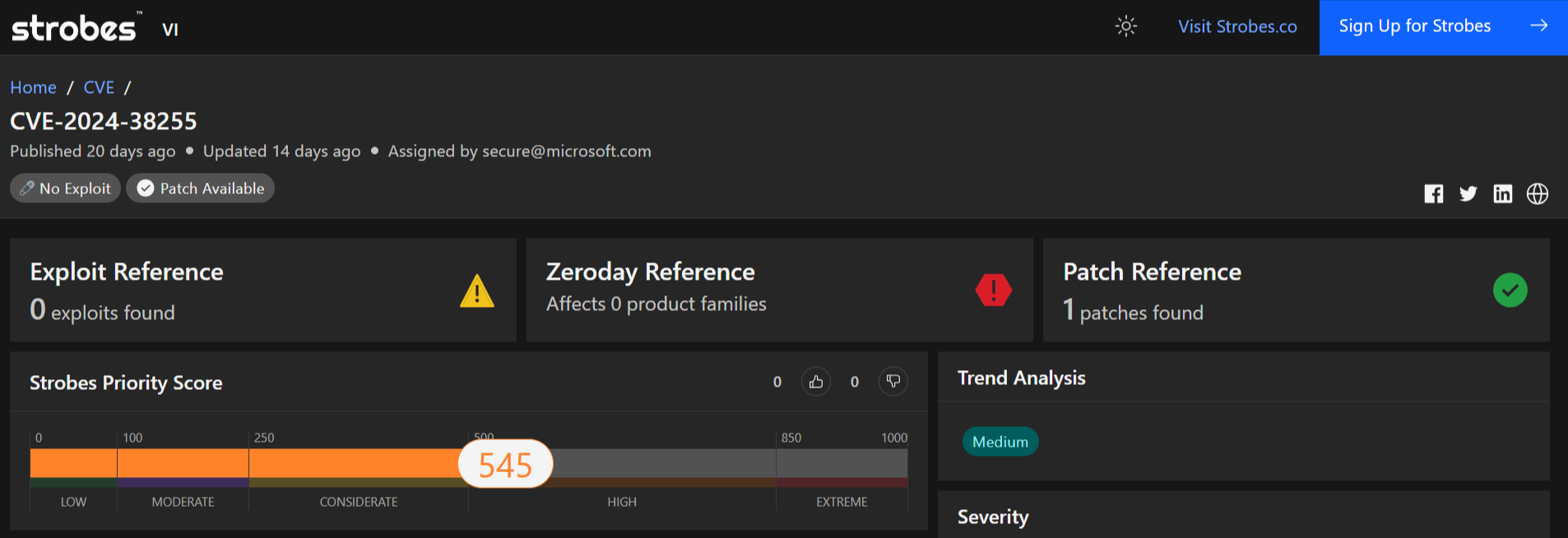
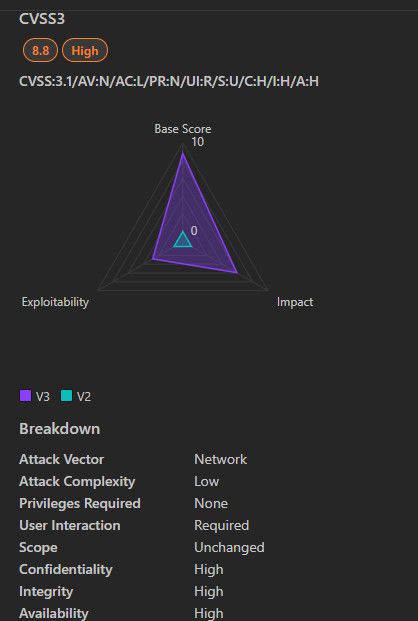
4. CVE-2024-38255: SQL Server Native Client Remote Code Execution Vulnerability
CVE-2024-38255 is a critical vulnerability affecting Microsoft SQL Server Native Client. This vulnerability could allow a remote attacker to execute arbitrary code on a vulnerable system.
Impact
Successful exploitation of this vulnerability could lead to severe consequences, including:
- Remote Code Execution: An attacker could gain control of the affected system.
- Data Theft: Sensitive data could be stolen or compromised.
- System Disruption: Critical system services could be disrupted or disabled.
Details of the Vulnerability
- Severity: Critical
- CVSS Score: 10.0 (Critical)
- Affected Products: Microsoft SQL Server Native Client
- Vulnerability Type: Remote Code Execution
- Exploitability: Remote (No user interaction required)
Mitigation
To mitigate the risk posed by CVE-2024-38255, Microsoft has released security updates. It is strongly recommended to:
- Install the Latest Security Updates: Apply the latest security updates from Microsoft as soon as they are available.
- Network Segmentation: Segment your network to limit the potential impact of a successful attack.
- Input Validation: Implement strict input validation to prevent malicious input from being processed.
- Least Privilege Principle: Grant users only the minimum necessary privileges to perform their tasks.
- Regular Security Audits: Conduct regular security audits to identify and address potential vulnerabilities.
- Keep Software Up-to-Date: Regularly update all software, including operating systems, applications, and firmware.
- Network Monitoring: Use network monitoring tools to detect and respond to suspicious activity.
- Security Awareness Training: Educate users about security best practices, including recognizing and avoiding phishing attacks.
Sources:
- National Vulnerability Database (NVD): https://nvd.nist.gov/vuln/detail/CVE-2024-38255
- Microsoft Security Response Center (MSRC): https://msrc.microsoft.com/update-guide/vulnerability/CVE-2024-38255
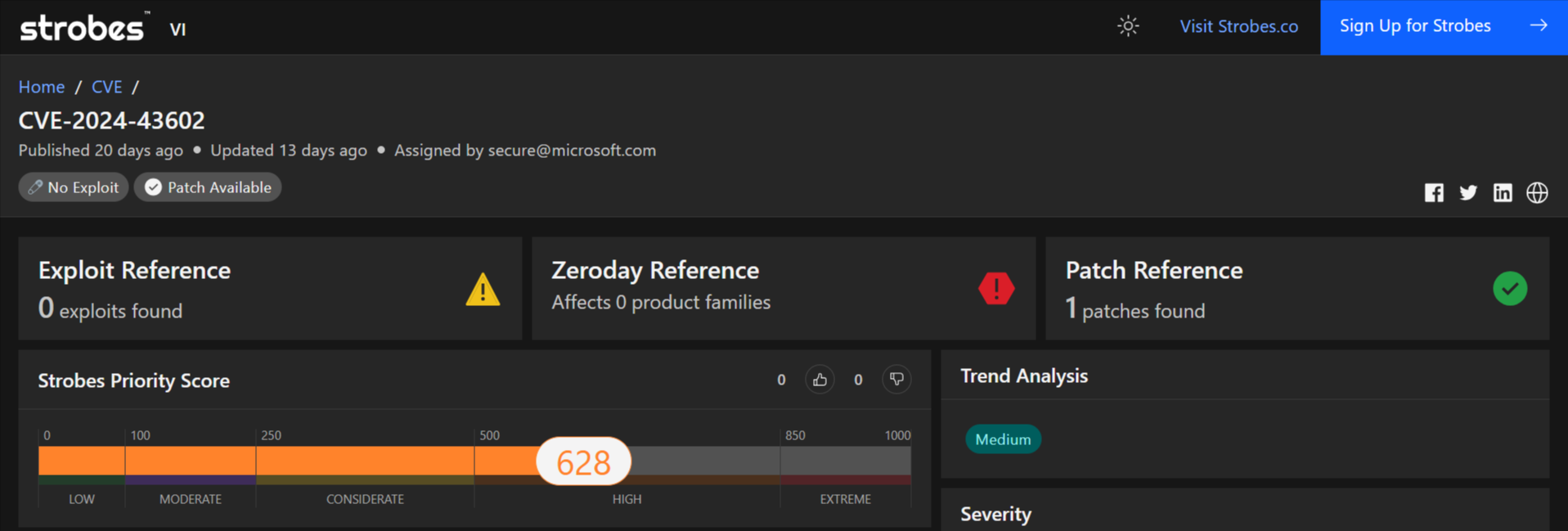
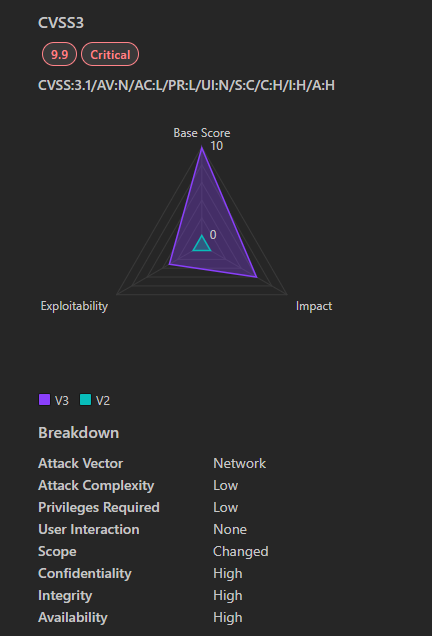
5. CVE-2024-43602: Azure CycleCloud Remote Code Execution Vulnerability
CVE-2024-43602 is a critical vulnerability discovered in Microsoft’s Azure CycleCloud, a tool designed to manage and orchestrate High-Performance Computing (HPC) environments within the Azure cloud platform. This vulnerability, if exploited successfully, could allow an attacker to execute arbitrary code on a vulnerable Azure CycleCloud cluster.
Impact
A successful exploitation of this vulnerability could lead to severe consequences, including:
- System Compromise: Attackers could gain unauthorized access to the underlying system and potentially take control of it.
- Data Theft: Sensitive data stored on the system could be stolen or exfiltrated.
- Service Disruption: Critical services and applications could be disrupted or rendered unavailable.
- Network Compromise: The attacker might be able to compromise other systems connected to the vulnerable Azure CycleCloud cluster.
Details of the Vulnerability
- Severity: Critical
- CVSS Score: 9.9 (Critical)
- Affected Products: Microsoft Azure CycleCloud
- Vulnerability Type: Remote Code Execution (RCE)
- Exploitability: Remote (No user interaction required)
Mitigation
To mitigate the risk posed by CVE-2024-43602, Microsoft has released security updates for Azure CycleCloud. It is strongly recommended to:
- Apply Security Updates Promptly: Install the latest security updates for Azure CycleCloud as soon as they are available from Microsoft.
- Restrict Access: Limit access to Azure CycleCloud to authorized personnel only.
- Monitor Network Traffic: Use network monitoring tools to detect and respond to suspicious activity.
- Implement Strong Password Policies: Enforce strong, unique passwords for all user accounts.
- Enable Multi-Factor Authentication (MFA): MFA adds an extra layer of security by requiring additional verification steps.
- Keep Software Up-to-Date: Regularly update all software, including operating systems, applications, and firmware.
- Security Awareness Training: Educate users about security best practices, including recognizing and avoiding phishing attacks.
Sources:
- National Vulnerability Database (NVD): https://nvd.nist.gov/vuln/detail/CVE-2024-43602
- Microsoft Security Response Center (MSRC): https://msrc.microsoft.com/update-guide/vulnerability/CVE-2024-43602
Final Words
Cyber threats are becoming increasingly sophisticated, and the vulnerabilities highlighted among the Top CVEs of November 2024 show just how quickly risks can emerge. With Strobes Vulnerability Intelligence, a key part of our Continuous Threat Exposure Management (CTEM) platform, you gain access to context-rich data, prioritization strategies, and actionable insights from over 250,000 CVEs and 200,000 exploits. Stay ahead with smarter, faster vulnerability management.
Subscribe to our newsletter for the latest updates and strategies to secure your organization effectively.