You searched for vulnerability management tools but got vulnerability scanners instead, thinking they were the same. While procurement or finance teams might mistakenly equate the two, they serve different functions and offer different levels of security assurance. As cyber threats become more sophisticated, effective vulnerability management is crucial for business security.
True vulnerability management tools go beyond simply identifying potential threats; they provide actionable insights for vulnerability prioritizing and mitigating risks before they translate into security breaches.
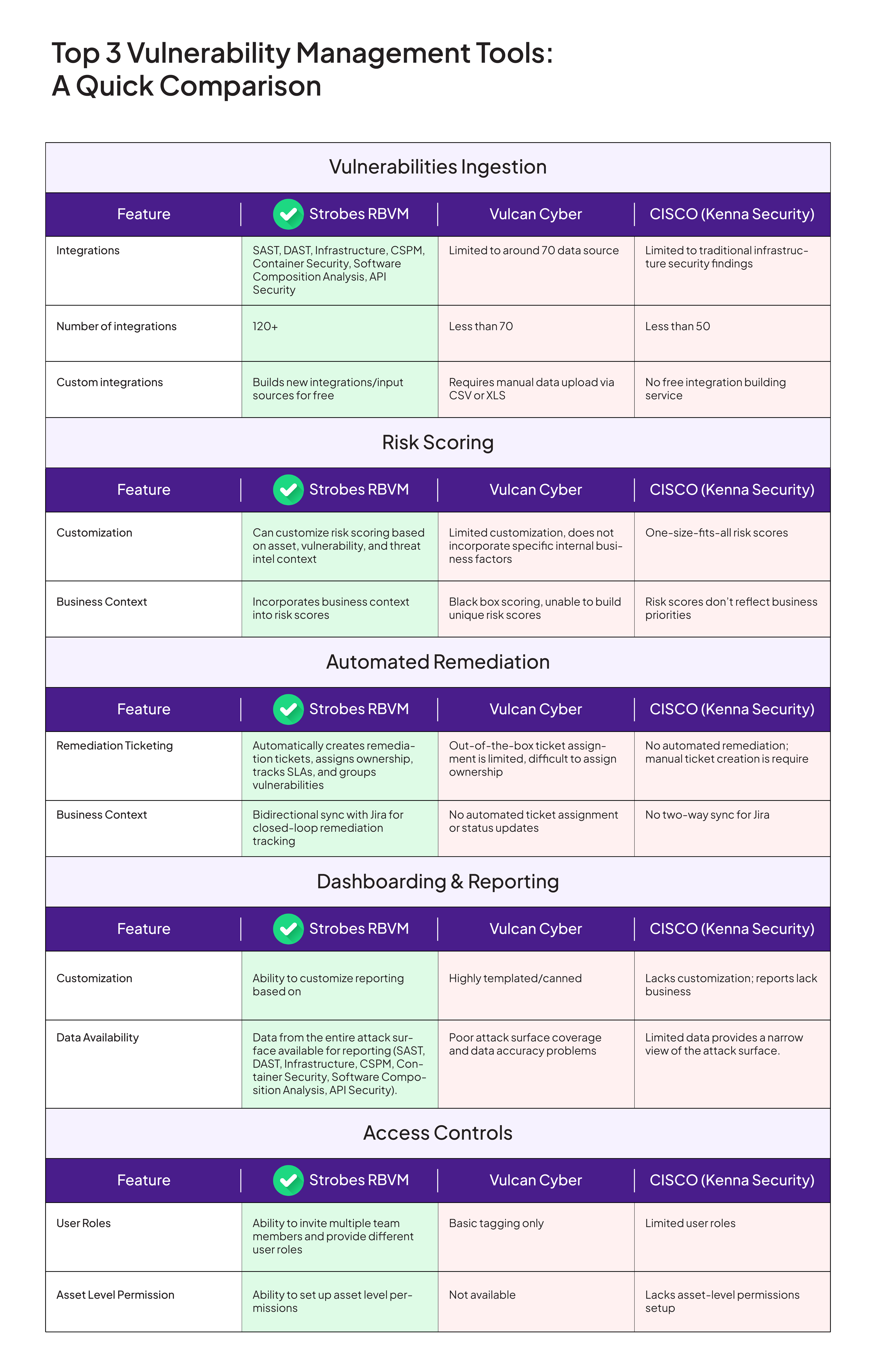
To assist you in selecting the optimal solution, Strobes has compiled a list of the top 10 vulnerability management tools.
What is a Vulnerability Management Tool?
Vulnerability management tools are specialized software applications designed to identify, assess, prioritize, and remediate weaknesses within your IT infrastructure. These weaknesses, often referred to as vulnerabilities, can be security flaws in operating systems, applications, or network configurations that malicious actors could exploit to gain unauthorized access to your systems and data.
Vulnerability Management Tools vs Vulnerability Scanners
| Feature | Vulnerability Management Tools | Vulnerability Scanners |
| Function | Manages the entire vulnerability lifecycle | Identifies vulnerabilities in systems and applications |
| Analogy | Security doctor | Security diagnostic tool |
| Output | Lists with prioritization, remediation advice, workflow, reporting | Lists of vulnerabilities with severity levels |
| Workflow | Automated or semi-automated workflow for assigning, tracking, and reporting on remediation efforts | Limited, may require manual prioritization and tracking |
| SLA Management | Can be used to define and track Service Level Agreements (SLAs) for vulnerability remediation times based on severity | Not applicable |
| Use Cases | Ongoing vulnerability management, Prioritize and remediate critical issues, Track patching progress , Generate security reports, Compliance audits (detailed) | Initial security assessment, Identify new vulnerabilities after patching, Compliance audits (basic) |
Factors to Consider While Selecting Vulnerability Management Tools
With so many vulnerability management tools on the market, choosing the right one can be overwhelming. Here at Strobes, we’re all about empowering businesses with the best security solutions. That’s why we’ve compiled a breakdown of the top 10 vulnerability management platforms, assessed using these key criteria:
- Vulnerability Scanning: How comprehensive and in-depth is the scanning capability?
- Prioritization: Does it prioritize threats based on real-world impact or just generic severity?
- Remediation Planning: Does it offer clear guidance and recommendations for fixing vulnerabilities?
- Reporting & Automation: How well does it present security data and automate tasks?
- Integrations: Does it work seamlessly with your existing security tools?
- Scalability: Can it handle the size and complexity of your network?
- Ease of Use: Is the interface user-friendly and easy to navigate for your security team?
- Cost: Does the pricing model fit your budget and security needs?
Top 15 Vulnerability Management Tools or Solutions
- Strobes RBVM
- Vulcan Cyber
- Cisco VM (Powered by Kenna Security)
- Crowdstrike Falcon Spotlight
- Rapid7 InsightVM
- Intruder
- Qualys VMDR
- Tenable.io Vulnerability Management
- Fortra Alert Logic MDR
- IBM Security Vulnerability Scanner
- Skybox Security Management Platform
- Balbix
- Nucleus Security
- New Relic Security Platform
- ManageEngine Vulnerability Manager Plus
1. Strobes RBVM
Best for – Organizations seeking a unified security posture, risk-based prioritization, seamless integrations, and streamlined workflow
Go beyond basic scanning with Strobes RBVM. This intelligent platform prioritizes threats based on real-world exploitability and potential business impact, not just generic severity and CVSS scores. Imagine, you’ll focus on the vulnerabilities that truly matter to your organization, saving you valuable time and resources. On top of that, Strobes RBVM automates tedious workflows and integrates seamlessly with your existing security setup, streamlining your entire vulnerability management process.
- Vulnerability Scanning: Integrates with various scanners for comprehensive coverage.
- Prioritization: Focuses on real-world exploitability and potential business impact of vulnerabilities.
- Remediation Planning: Offers clear guidance and prioritizes patches based on risk.
- Reporting & Automation: Provides customizable reports and automates vulnerability lifecycle management tasks.
- Integrations: 120+ integrations with two way Jira sync. Integrates with major security tools for a unified security posture.
- Scalability: Cloud-based architecture scales efficiently with your growing network.
- Ease of Use: User-friendly interface with clear visualizations and actionable insights.
- Cost: Competitive pricing with flexible models based on your organization’s size and needs.
Aggregate, Prioritize and Remediate Vulnerabilities Efficiently with all-in-one Strobes RBVM Platform
2. Vulcan Cyber
Best for – Organizations seeking a combined vulnerability management and XDR solution
Looking for an all-in-one powerhouse? Vulcan Cyber combines the power of vulnerability management with extended detection and response (XDR) capabilities. This means it can not only identify weaknesses in your systems but also actively hunt for threats and take action to stop them in their tracks. Think of it as a security defender that never sleeps, constantly on the lookout for potential dangers.
- Vulnerability Scanning: Provides comprehensive scanning for vulnerabilities across your network.
- Prioritization: Integrates threat intelligence to prioritize vulnerabilities based on exploitability.
- Remediation Planning: Offers remediation guidance and can automate patching workflows (depending on integrations).
- Reporting & Automation: Delivers rich reports on vulnerabilities and threat context with extensive automation capabilities.
- Integrations: Integrates with SIEM, SOAR, and other security tools for a holistic XDR approach.
- Scalability: Highly scalable architecture designed for large and complex networks.
- Ease of Use: Can be complex for smaller teams due to the XDR functionalities.
- Cost: Higher price point due to the comprehensive XDR capabilities.
3. Cisco VM (Powered by Kenna Security)
Best for – Organizations using Cisco security solutions and seeking threat intelligence-driven prioritization
This tool combines vulnerability scanning with threat intelligence from Kenna Security. This extra layer of context helps you prioritize vulnerabilities based on real-world threats, not just generic severity scores. Cisco VM integrates well with existing Cisco security solutions for a cohesive security posture.
- Vulnerability Scanning: Provides comprehensive vulnerability scanning with threat intelligence from Kenna Security.
- Prioritization: Prioritizes vulnerabilities based on severity, exploitability, and context from Kenna Security.
- Remediation Planning: Offers remediation recommendations with integration to vulnerability databases for patch information.
- Reporting & Automation: Provides detailed reports enriched with threat intelligence and some automation capabilities.
- Integrations: Integrates with Cisco security tools and other security platforms.
- Scalability: Scales well for large and complex networks.
- Ease of Use: Interface may require familiarity with Cisco security products and Kenna Security platform.
- Cost: Pricing typically bundled with other Cisco security solutions.
4. Crowdstrike Falcon Spotlight
Best for – Organizations prioritizing endpoint security and in-depth vulnerability assessments
Endpoint security your main focus? Crowdstrike Falcon Spotlight shines a light on vulnerabilities lurking on your devices. This endpoint security specialist provides in-depth vulnerability assessments and clear remediation guidance, helping you identify and fix weaknesses before they can be exploited. With Falcon Spotlight, your devices are constantly monitored and protected, keeping your organization safe from endpoint threats.
- Vulnerability Scanning: Focuses on endpoint security, providing detailed vulnerability assessments for devices.
- Prioritization: Prioritizes vulnerabilities based on endpoint criticality and potential impact on device functionality.
- Remediation Planning: Offers remediation recommendations and can automate patching on endpoints (depending on configuration).
- Reporting & Automation: Provides reports on endpoint vulnerabilities with some automation for remediation tasks.
- Integrations: Integrates with Crowdstrike Falcon platform for comprehensive endpoint protection.
- Scalability: Scales well for large deployments of endpoints.
- Ease of Use: User-friendly interface designed for endpoint security specialists.
- Cost: Pricing typically bundled with the broader Crowdstrike Falcon platform.
5. Rapid7 InsightVM
Best for – Organizations needing a robust vulnerability scanning and prioritization solution
A veteran in the vulnerability management field, Rapid7 InsightVM is a popular choice for its robust scanning and prioritization capabilities. Boasting a vast vulnerability database, InsightVM ensures you’re not missing any critical threats. This comprehensive tool identifies vulnerabilities across your network, prioritizes them based on severity and exploitability, and provides clear guidance on how to fix them. If you’re looking for a reliable and proven solution, Rapid7 InsightVM is a solid choice.
- Vulnerability Scanning: Offers extensive vulnerability scanning capabilities with a large vulnerability database.
- Prioritization: Prioritizes vulnerabilities based on severity, exploitability, and asset criticality.
- Remediation Planning: Provides remediation recommendations with integration to vulnerability databases for patch information.
- Reporting & Automation: Offers customizable reports and some automation capabilities for vulnerability management tasks.
- Integrations: Integrates with various security tools for broader security visibility.
- Scalability: Scales well for large and complex networks.
- Ease of Use: Interface can be complex for beginners, but extensive training resources are available.
- Cost: Pricing models based on features and network size.
6. Intruder
Best for – Organizations looking to combine vulnerability management with user behavior analysis
This solution goes beyond traditional vulnerability management by incorporating user behavior analysis. By analyzing user activity, Intruder can identify potential insider threats and suspicious behavior in addition to vulnerabilities in your systems. This holistic approach provides a more comprehensive view of your security landscape.
- Vulnerability Scanning: Integrates with various scanners to identify vulnerabilities across systems.
- Prioritization: Prioritizes vulnerabilities based on severity, exploitability, and user behavior analysis.
- Remediation Planning: Offers remediation recommendations and integrates with patching tools.
- Reporting & Automation: Provides detailed reports on vulnerabilities and user activity with automation for some remediation tasks.
- Integrations: Integrates with SIEM, SOAR, and user behavior analytics tools for a comprehensive security view.
- Scalability: Scales well for organizations with a focus on user behavior monitoring.
- Ease of Use: Interface can be complex for teams unfamiliar with user behavior analytics.
- Cost: Pricing varies based on features and number of users monitored.
7. Qualys VMDR
Best for – Organizations seeking cloud-based vulnerability management with automated patching capabilities
Cloud-based convenience is key with Qualys VMDR. This tool offers comprehensive vulnerability scanning specifically designed for cloud environments. Qualys VMDR also boasts automated patching capabilities, streamlining the process of fixing identified weaknesses in your cloud workloads.
- Vulnerability Scanning: Provides cloud-based vulnerability scanning for assets in your cloud environment.
- Prioritization: Prioritizes vulnerabilities based on severity, exploitability, and criticality of cloud workloads.
- Remediation Planning: Offers remediation recommendations with automated patching capabilities for cloud-based vulnerabilities.
- Reporting & Automation: Delivers detailed reports on cloud security posture with extensive automation for vulnerability management tasks, including patching.
- Integrations: Integrates with cloud platforms and security tools for centralized management.
- Scalability: Designed to handle the dynamic nature of cloud environments and scales efficiently.
- Ease of Use: User-friendly interface focused on cloud security management.
- Cost: Subscription-based pricing varies based on features and cloud environment size.
8. Tenable.io Vulnerability Management
Best for – Organizations looking for a cloud-based solution with extensive vulnerability database integration
A popular cloud-based solution, Tenable.io offers a wide range of features including vulnerability scanning, prioritization, and remediation guidance. It integrates with various security tools, giving you a consolidated view of your security posture. Tenable is known for its extensive vulnerability database and user-friendly interface.
- Vulnerability Scanning: Provides comprehensive vulnerability scanning across a wide range of assets (systems, applications, cloud workloads).
- Prioritization: Prioritizes vulnerabilities based on severity, exploitability, and potential business impact.
- Remediation Planning: Offers remediation recommendations and integrates with vulnerability databases for patch information.
- Reporting & Automation: Delivers detailed reports on vulnerabilities and automates some vulnerability management tasks.
- Integrations: Integrates with various security tools (SIEM, SOAR) for a consolidated security view.
- Scalability: Cloud-based architecture scales efficiently for large and complex networks.
- Ease of Use: User-friendly interface with clear visualizations and actionable insights.
- Cost: Subscription-based pricing varies depending on features and number of assets scanned.
9. Fortra Alert Logic MDR
Best for – Organizations requiring a security solution with managed detection, response, and analyst support
This offering goes beyond basic vulnerability management by providing continuous threat monitoring, detection, and response capabilities. Fortra Alert Logic MDR is a good option for organizations seeking a comprehensive security solution with the support of a team of security analysts. However, this advanced functionality comes at a higher price point.
- Vulnerability Scanning: Integrates with vulnerability scanners to provide comprehensive coverage.
- Prioritization: Prioritizes vulnerabilities based on severity, exploitability, and threat intelligence.
- Remediation Planning: Offers remediation recommendations and may automate patching workflows (depending on integrations).
- Reporting & Automation: Provides detailed reports on vulnerabilities, threats, and security incidents with extensive automation for detection and response tasks.
- Integrations: Integrates with SIEM, SOAR, and other security tools for a holistic security posture.
- Scalability: Highly scalable architecture designed for large and complex networks.
- Ease of Use: Interface may require some security expertise due to the MDR functionalities.
- Cost: Higher price point due to the comprehensive MDR services and team of security analysts.
10. IBM Security Vulnerability Scanner
Best for – Established organizations seeking comprehensive assessments with threat intelligence integration
This established solution offers comprehensive network and web application vulnerability assessments. IBM integrates with threat intelligence to provide risk scoring, helping you prioritize vulnerabilities based on the likelihood of exploit. While powerful, its interface can be complex for beginners.
- Vulnerability Scanning: Offers comprehensive network and web application vulnerability assessments.
- Prioritization: Integrates with threat intelligence for risk scoring, prioritizing vulnerabilities based on exploit likelihood.
- Remediation Planning: Provides remediation recommendations but may require additional tools for patching.
- Reporting & Automation: Offers customizable reporting tools and integrates with security information and event management (SIEM) systems.
- Integrations: Integrates with various security tools for a holistic view but may require some configuration effort.
- Scalability: Scales for large and complex IT environments.
- Ease of Use: Interface can be complex for beginners, but training resources are available.
- Cost: Pricing varies depending on features and deployment size.
11. Balbix
Best for – Organizations prioritizing threat-centric vulnerability management with a cloud-native approach
This cloud-native platform focuses on integrating with various vulnerability scanners, offering a consolidated view of your security posture. Balbix prioritizes vulnerabilities based on threat intelligence feeds, making it a decent option for organizations seeking threat-centric prioritization.
- Vulnerability Scanning: Integrates with various vulnerability scanners, providing a consolidated view across your security landscape.
- Prioritization: Prioritizes vulnerabilities based on threat intelligence feeds, focusing on the most relevant threats.
- Remediation Planning: Offers remediation recommendations and integrates with ticketing systems for streamlined workflow.
- Reporting & Automation: Provides customizable reports and integrates with reporting tools for visualization. Automation capabilities vary depending on integrations.
- Integrations: Designed for integration with various vulnerability scanners and security tools for a comprehensive view.
- Scalability: Scales efficiently for large and complex IT environments.
- Ease of Use: User-friendly interface simplifies vulnerability management tasks.
- Cost: Pricing varies based on features and number of assets scanned.
12. Nucleus Security
Best for – Organizations with a focus on securing cloud environments
Cloud security a top concern? Nucleus Security has you covered. This specialized tool offers comprehensive vulnerability scanning and prioritization designed specifically to keep your cloud environment safe. No more generic tools that miss cloud-specific vulnerabilities. Nucleus Security understands the unique challenges of the cloud and provides targeted protection to keep your cloud workloads secure.
- Vulnerability Scanning: Specializes in cloud environments, offering in-depth scanning for cloud vulnerabilities.
- Prioritization: Prioritizes vulnerabilities based on severity and potential impact on cloud workloads.
- Remediation Planning: Provides remediation recommendations with cloud-specific patching options.
- Reporting & Automation: Offers detailed reports on cloud security posture with some automation capabilities.
- Integrations: Integrates with cloud platforms and security tools for centralized management.
- Scalability: Designed to handle the dynamic nature of cloud environments.
- Ease of Use: Streamlined interface focused on cloud security, may have a learning curve for non-cloud environments.
- Cost: Pricing varies based on cloud environment size and features needed.
13. Skybox Security Management Platform
Best for – Organizations needing threat intelligence and automated network security alongside vulnerability management
Network security takes center stage with Skybox. This platform goes beyond basic vulnerability scanning, offering threat intelligence and automated breach simulations. While a powerful tool, Skybox may require some security expertise to fully utilize its features.
- Vulnerability Scanning: Offers network vulnerability assessments and threat intelligence for a broader security picture.
- Prioritization: Prioritizes vulnerabilities based on business context and exploit likelihood.
- Remediation Planning: Provides remediation recommendations and workflow automation for network security tasks.
- Reporting & Automation: Offers detailed security reports and dashboards with extensive automation capabilities.
- Integrations: Integrates with security orchestration, automation, and response (SOAR) platforms for streamlined workflows.
- Scalability: Scales efficiently for large and complex IT environments.
- Ease of Use: May require some security expertise to fully utilize all the advanced features.
- Cost: Pricing varies based on features and deployment size.
14. New Relic Security Platform
Best for – Organizations focused on application security within DevOps workflows
This solution focuses on application security vulnerabilities. New Relic integrates with DevOps tools and cloud platforms, making it a good fit for organizations with a focus on development security. Its focus is specific, so it may not be ideal for broader vulnerability management needs.
- Vulnerability Scanning: Focuses on application security vulnerabilities, integrating with DevOps tools and cloud platforms.
- Prioritization: Integrates with threat intelligence for vulnerability prioritization based on exploit likelihood.
- Remediation Planning: Offers remediation recommendations and integrates with ticketing systems for streamlined workflow.
- Reporting & Automation: Provides customizable security reports and integrates with reporting tools. Automation capabilities are geared towards application security tasks.
- Integrations: Integrates with DevOps tools and cloud platforms for seamless application security management.
- Scalability: Scales for on-premises and cloud environments, adapting to your deployment needs.
- Ease of Use: User-friendly interface designed for developers and security professionals working together.
- Cost: Pricing varies based on features and deployment size.
15. ManageEngine Vulnerability Manager Plus
Best for – Organizations prioritizing automated endpoint protection and remediation workflows
This user-friendly option provides automatic scanning for endpoint vulnerabilities, ensuring your devices are protected. ManageEngine integrates with ticketing systems and patch management tools, streamlining the remediation process. It offers a good balance of features and ease of use but might not be suitable for highly complex environments.
- Vulnerability Scanning: Provides automatic scanning for endpoint vulnerabilities, ensuring your devices are protected.
- Prioritization: Prioritizes vulnerabilities based on severity and exploitability for efficient remediation.
- Remediation Planning: Integrates with ticketing systems and patch management tools, streamlining the remediation process.
- Reporting & Automation: Offers customizable reports with vulnerability details and remediation recommendations. Automatic scanning ensures endpoint protection.
- Integrations: Integrates with major security tools (SIEM, SOAR) for a consolidated security view.
- Scalability: Scales well for large deployments of endpoints.
- Ease of Use: User-friendly interface simplifies vulnerability management for endpoint security teams.
- Cost: Competitive pricing with flexible models based on size and needs.
Why Vulnerability Management Tools Matter?
In the modern world of cybersecurity, safeguarding an organization’s information and systems is paramount. Here’s why vulnerability management tools are essential:
- Proactive Risk Identification: These tools continuously scan systems to identify weaknesses before they can be exploited, allowing organizations to address potential threats proactively.
- Comprehensive Asset Visibility: Vulnerability management tools provide a complete inventory of all devices, software, and services across the network, ensuring no asset is overlooked.
- Prioritization of Threats: Not all vulnerabilities pose the same level of risk. These tools assess and rank vulnerabilities based on their severity and potential impact, enabling teams to focus on the most critical issues first.
- Regulatory Compliance: Maintaining security compliance with industry standards and regulations is crucial. Vulnerability management platforms help ensure that security measures align with legal and regulatory requirements, thereby avoiding penalties and legal complications.
- Cost Efficiency: Addressing vulnerabilities early can prevent costly breaches. Investing in these tools can save significant amounts of money by mitigating risks before they escalate into major incidents.
- Automated Processes: By automating the scanning, identification, and reporting of vulnerabilities, these tools reduce the need for manual intervention, freeing up valuable time and resources for other essential tasks.
- Enhanced Reporting and Metrics: Detailed reports and metrics provided by these tools offer valuable insights into the organization’s security posture, helping to inform strategic decisions and resource allocation.
- Improved Incident Response: When a vulnerability is detected, these tools offer detailed guidance on remediation steps, allowing for swift and effective responses to potential threats.
- Integration with Other Security Solutions: Vulnerability management platforms often integrate seamlessly with other security measures, creating a more cohesive and robust defense strategy.
- Continuous Improvement: Regular use of these tools fosters a culture of continuous improvement in security practices, ensuring that the organization remains vigilant and prepared against new and emerging threats.
Investing in vulnerability management tools is not just a strategic choice but a necessary action to safeguard the integrity, confidentiality, and availability of an organization’s critical assets.
Benefits of Vulnerability Management Tools for CISOs
| Benefits | Description | Impact |
| Strategic Decision-Making | Vulnerability management tools provide comprehensive insights into the organization’s security posture. | Prioritize vulnerabilities based on risk, optimize resource allocation for remediation efforts. |
| Improved Risk Management | Proactively identify and address vulnerabilities before they can be exploited. | Mitigate high-impact threats first, demonstrate a strong security posture. |
| Reduced Costs | Identify and patch vulnerabilities before they can be exploited by attackers. | Prevent costly security breaches, improve overall security efficiency through automation. |
| Enhanced Regulatory Compliance | Provide a systematic approach to vulnerability identification, prioritization, and remediation. | Meet compliance requirements with ease, demonstrate a documented vulnerability management process. |
| Improved Visibility | Offer a comprehensive view of vulnerabilities across the entire IT infrastructure. | Gain a complete view of IT security posture, make informed security investment decisions. |
| Streamlined Workflows | Automate repetitive tasks like scheduling scans, analyzing results, and generating reports. | Free up valuable time for strategic security initiatives, improve team productivity. |
| Actionable Insights | Provide clear guidance on how to address vulnerabilities. | Save time and effort for security teams, ensure effective remediation efforts. |
| Deeper Security Understanding | Analyze vulnerability trends and identify potential security gaps. | Proactively improve overall security posture. |
Benefits of Vulnerability Management Tools for Different Security Roles
| Benefits | Security Analysts | SOC Team | Security Auditors |
| Streamlined Workflows | Share vulnerability data and remediation plans across the SOC team for a coordinated response. | Share vulnerability data and remediation plans across the SOC team for a coordinated response. | Automated vulnerability scanning and reporting save time and resources during security audits. |
| Prioritized Threat Focus | Focus on the most critical vulnerabilities first based on severity, exploitability, and potential impact. | Identify and prioritize vulnerabilities before they can be exploited by attackers. | Gain a deeper understanding of an organization’s security posture through comprehensive vulnerability data. |
| Actionable Insights | Receive clear guidance on how to address vulnerabilities, saving time and effort. | Automated patching or other remediation tasks reduce response times. | Improved audit efficiency through reduced risk of human error and faster reporting. |
| Improved Efficiency | Focus on more strategic security tasks by delegating repetitive tasks to the tool. | Improved security posture and reduced attack surface through continuous monitoring and remediation. | Generate detailed and accurate reports on vulnerabilities for stakeholders. |
Next Step
Now that you’re familiar with the top vulnerability management tools, it’s time to take action. But where do you go from here? Start by assessing your organization’s specific needs. What are your current pain points? What integrations do you need? Which features are essential for you?
Each of these tools offers unique strengths, so consider what aligns best with your requirements. Whether you’re looking for seamless integration, advanced analytics, or comprehensive reporting, there’s a solution tailored for you.
For instance, Strobes RBVM stands out for its exceptional risk-based prioritization and integration capabilities. It’s designed to help you stay ahead of threats efficiently and effectively.
Begin evaluating these top vulnerability management platforms today, and take a proactive step toward a more secure future for your organization. Your security, reputation, and peace of mind are worth it.
Ready to strengthen your security strategy? Book a free trial of Strobes RBVM today and see how risk-based vulnerability management can transform your defense!
FAQs
How do vulnerability management tools integrate with existing security infrastructure (SIEM, SOAR, etc.)?
Vulnerability management tools offer various integration options, including APIs, connectors, and pre-built integrations with popular SIEM and SOAR platforms. This allows for seamless data exchange, automated workflows, and enriched security insights.
What vulnerability data feeds do the tools support (e.g., CVE, threat intelligence feeds)?
Most tools support major vulnerability databases like CVE and integrate with threat intelligence feeds to provide context and prioritize vulnerabilities based on exploitability and real-world threat actors.
How do the tools handle false positives and ensure data accuracy?
Leading tools leverage advanced vulnerability scoring algorithms, threat intelligence, and machine learning to reduce false positives. Additionally, they allow for manual review and customization of scoring models to optimize accuracy for your specific environment.
Do the tools offer options for vulnerability scanning across different environments (cloud, on-prem, containers)?
Yes, many vulnerability management tools like Strobes RBVM offer comprehensive scanning capabilities across cloud, on-premise, and containerized environments. Look for tools that support multi-cloud deployments and container security features.
How do the tools handle vulnerability scanning for custom applications and code?
Tools like Strobes RBVM integrate with Software Composition Analysis (SCA) solutions to identify vulnerabilities within your custom codebase. Additionally, they might offer integrations with SAST (Static Application Security Testing) tools for deeper code analysis.
How do vulnerability management tools help demonstrate compliance with security regulations?
These tools generate detailed reports on vulnerabilities, remediation efforts, and risk assessments. These reports can serve as evidence of your organization’s commitment to vulnerability management and compliance with regulations like PCI-DSS, HIPAA, or GDPR.
What is the return on investment (ROI) for implementing a vulnerability management tool?
The ROI is multifaceted. It includes potential cost savings from preventing breaches, improved security posture, reduced remediation time, and better resource allocation for security efforts.
Related Reads
- RBVM Customized Dashboards: CFO Template
- Why Ignoring Vulnerability Prioritization is a CISO’s Worst Nightmare?
- Customized Vulnerability Management Dashboard for CISOs
- The Role of Asset Correlation in Vulnerability Management
- What is Vulnerability Management? Compliance, Challenges, & Solutions
- Is Vulnerability Scanning Enough for Organizations in 2025?
- Solution: Risk Based Vulnerability Management







