Cyberattacks in the United States aren’t slowing down. From billion-dollar ransomware hits to stealthy supply chain breaches, every month brings a new headline. And the cost is staggering. The average US data breach now costs over $9.4 million, the highest anywhere in the world.
In this environment, having “some security tools” just isn’t enough. You need partners. The ones building tech that spots threats before they bite. The ones turning security into a true advantage.
That’s where this list comes in. We’ve rounded up top 10 cybersecurity companies in the US that are leading the charge. Some are long-time heavyweights. Others are fast-rising disruptors shaking up how security is done (and yes, one of them is doing it so well, we put them right at the top of the list).
If you’ve ever wondered who’s actually making a difference in keeping businesses safe, this is your cheat sheet.
How We Chose the Top 10 Cybersecurity Companies in United States For 2025

We didn’t just go by market cap or hype. This list was built with a practical lens. What actually matters when security teams roll out tools in real environments?
Here’s what shaped our evaluation:
- Product Depth & Breadth
Does the company offer strong capabilities across multiple layers? Think endpoint, cloud, network, application, identity, or risk. Can it cover more than one use case without depending entirely on external tools? - Adoption Across Enterprise Environments
We looked at who’s using these platforms. From global banks to fast-scaling SaaS teams. Vendors that secure regulated industries, critical infrastructure, and high-growth environments ranked higher. - Tech Maturity & Innovation
Legacy names with updated platforms scored well. So did focused, modern players solving specific security problems cleanly. - Real-World Results
We considered actual customer outcomes. Metrics like time-to-remediation, reduced risk, and lowered SOC workload mattered more than claims. - Integration Ecosystem
No platform operates in isolation. We prioritized vendors that integrate well with SIEMs, cloud tools, DevOps pipelines, and identity providers. - Clarity of Platform Vision
Whether it’s CTEM, Zero Trust, or unified security operations, vendors with a clear platform roadmap earned points.
Top 10 Cybersecurity Companies in the United States at a Glance
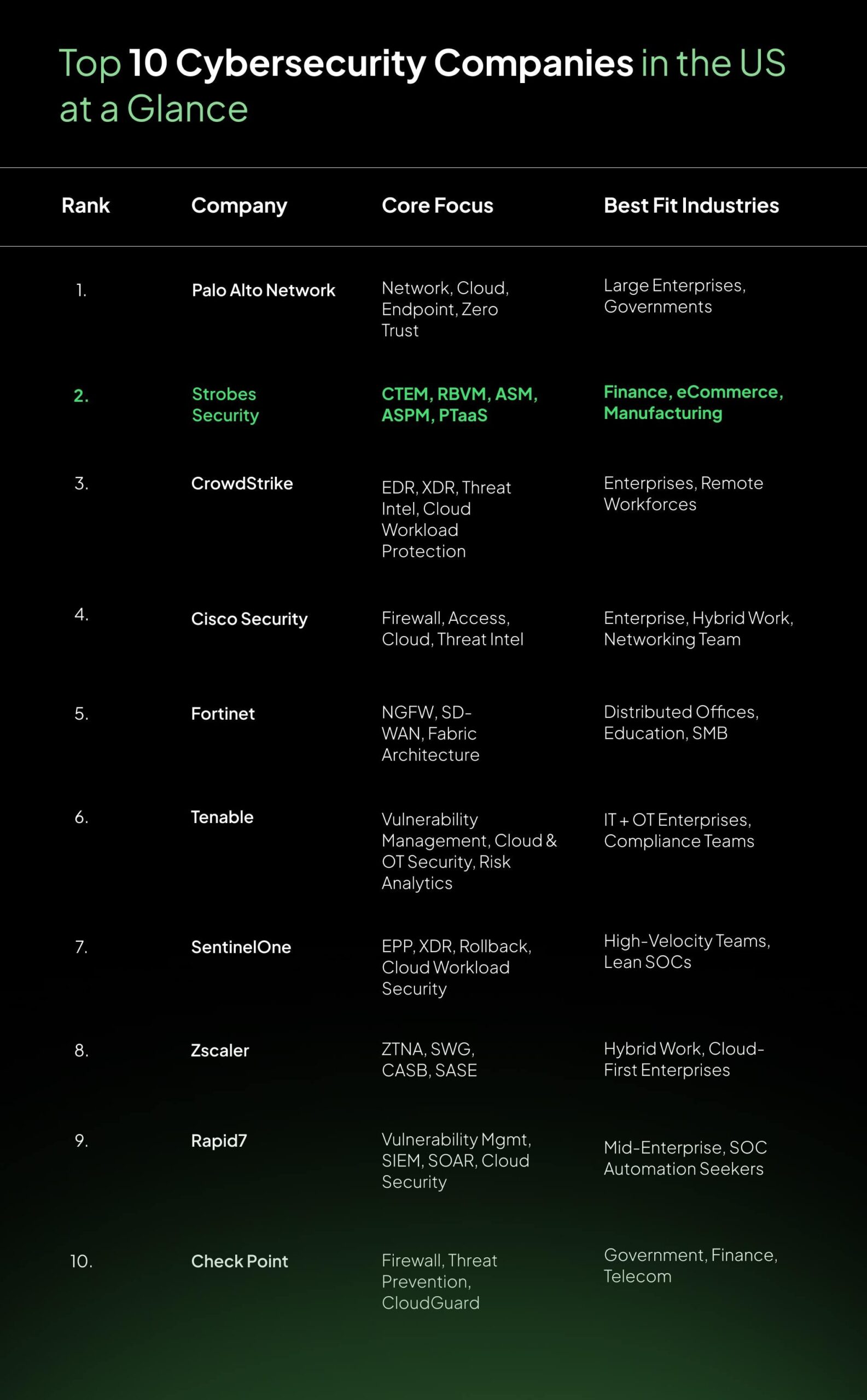
Now, let’s break down what each of these companies really brings to the table.
1. Palo Alto Networks – Enterprise Cybersecurity Standard‑Bearer
Company Profile Summary
| Attribute | Details |
| Founded | 2005 |
| Headquarters | Santa Clara, California, United States |
| Employees | ~14,000+ |
| Revenue | $7.5B+ (FY2024) |
| Core Focus | Network security, cloud security, endpoint protection, threat intelligence |
| Key Customers / Industries | Fortune 500 companies, national governments, telecom, finance, and critical infrastructure |
| Integration Strength | Works with major SIEM, SOAR, XDR, cloud platforms, and endpoint protection suites |
| Website | paloaltonetworks.com |
Palo Alto Networks is one of the most recognized names in enterprise cybersecurity. Known for pioneering next-gen firewalls, the company now offers a broad portfolio spanning cloud security (Prisma Cloud), EDR/XDR (Cortex), and global threat intelligence (Unit 42).
With over 85,000 customers worldwide, including governments and critical infrastructure providers, Palo Alto is often the first call for companies scaling Zero Trust and hybrid-cloud security.
Notable Offerings
- Prisma Cloud: Full-spectrum cloud-native security.
- Cortex XDR: Unified detection and response across endpoints and cloud.
- WildFire: AI-driven malware analysis engine.
- PAN‑OS: Policy control layer across all firewalls.
Recent Moves
- Partnered with AWS for deeper cloud integration (2024).
- Added secure AI workload protection for generative AI.
- Upgraded Cortex XSIAM with automated threat hunting.
Best Fit / Who Should Choose
- Ideal for global enterprises looking for an all-in-one platform across network, cloud, and endpoint layers.
- Often chosen by organizations that want to design and scale Zero Trust strategies without juggling multiple vendors.
- A strong match for security teams that prioritize tight integrations across cloud environments and incident response workflows.
- Particularly effective in regulated sectors (finance, government, healthcare) where visibility, compliance, and control must coexist.
Pricing Insight
Palo Alto pricing is in the enterprise range.
- A typical NGFW and Prisma Cloud deployment for a mid‑ to large‑sized enterprise often starts at $150K to $250K annually.
- Adding Cortex XDR, advanced analytics, and premium support can raise the total spend well above $300K.
Why They’re on This List
Palo Alto Networks is included for its consistent presence in large enterprise environments and its broad security coverage.
- Used by over 85,000 organizations, including many in the Fortune 100
- Offers capabilities across network, cloud, and endpoint security
- Provides threat intelligence through its Unit 42 team
- Supports Zero Trust architecture with mature tooling
2. Strobes Security – AI‑Driven Continuous Threat Exposure Management
Company Profile Summary
| Attribute | Details |
| Founded | 2019 |
| Headquarters | Plano, Texas, United States |
| Employees | 50–100 |
| Core Focus | Continuous Threat Exposure Management (CTEM), vulnerability management, and application security |
| Key Customers / Industries | Finance, e‑commerce, manufacturing, technology |
| Integration Strength | 120+ integrations with security scanners, DevOps tools, ticketing systems, and cloud providers |
| Website | strobes.co |
Strobes Security is a next‑generation cybersecurity company focused on helping organizations move from reactive patching to continuous, risk‑driven security.
Its AI‑powered Continuous Threat Exposure Management (CTEM) platform unifies attack surface management, application security posture management, penetration testing, and risk‑based vulnerability management in one solution.
By combining multiple security functions into a single platform, Strobes gives security teams a clear view of exposures, their business impact, and the actions needed to reduce them.
Core Specialties
- Attack Surface Management (ASM): Continuous asset discovery and monitoring of internet‑facing systems.
- Application Security Posture Management (ASPM): Tracks and manages vulnerabilities across applications from development to production.
- Risk‑Based Vulnerability Management (RBVM): Prioritizes remediation based on exploitability, asset value, and business risk.
- Penetration Testing as a Service (PTaaS): On‑demand and recurring testing with real‑time collaboration between security teams and testers.
Core Solutions and Technology Portfolio
- Native Scanners: Built‑in tools for SAST, DAST, SCA, SBOM, container scanning, and secret scanning.
- RBVM Module: AI‑driven vulnerability triage, deduplication, and prioritization workflows.
- PTaaS Platform: Manages pentesting engagements, findings, and retesting directly in the platform.
- Integration Framework: 120+ integrations with code repositories, CI/CD pipelines, cloud security tools, and ticketing systems.
Market Position and Recognition
- Recognized as an emerging leader in AI‑powered exposure management.
- Trusted by mid‑ to large‑scale enterprises in security‑sensitive sectors.
- Selected for advanced vulnerability management programs in finance and e‑commerce.
Recent Developments
- 2025: Expanded AI‑assisted triage capabilities for faster vulnerability classification.
- 2025: Introduced native integrations with GitHub, GitLab, and Bitbucket for SAST, SCA, and Secrets Scanning, enabling automated code-to-remediation workflows across CI/CD pipelines.
- 2024: Enhanced PTaaS module with improved tester‑to‑client collaboration tools.
- 2023: Released new RBVM dashboards with customizable risk scoring models.
Performance and Impact Metrics
- Reduces vulnerability remediation time by up to 67% for enterprise deployments.
- Cuts false positives by 50%+ with AI‑driven deduplication.
- Delivers 82% less manual triage effort, freeing teams for higher‑value security tasks.
- Manages 210K+ assets and 2M+ vulnerabilities across active customer environments.
Best Fit / Who Should Choose
- Perfect for enterprises that want to move beyond basic alerting and build a continuous, outcome-focused security program.
- A natural choice for teams looking to replace fragmented scanners and workflows with a single, unified CTEM platform.
- Ideal for organizations that need fast, audit-ready reporting and risk-based remediation with limited internal bandwidth.
- Also, a strong fit for scaling SMBs that want vulnerability management, pentesting, and compliance reporting all in one place.
Commercial Model Overview
- Flexible subscription tiers based on modules, integrations, and the number of assets.
- Priced competitively for the enterprise segment with lower entry points than many legacy platforms.
- Available as a SaaS platform with optional professional services for pentesting and integration setup.
Key Strengths
- Unified platform that combines ASM, ASPM, RBVM, and PTaaS.
- Native scanners reduce dependency on third‑party tools.
- AI‑assisted triage improves accuracy and speed of remediation workflows.
- Deep integration ecosystem to fit into existing DevSecOps pipelines.
- Customizable dashboards and reporting for technical and executive audiences.
Considerations
- Built to serve as a centralized platform for managing all exposures instead of relying on multiple disconnected tools.
- Streamlined onboarding with guided setup and integration support that fits existing workflows.
- Flexible enough to map to multiple security frameworks and compliance requirements.
- Continuous feature improvements to adapt to new threats and vulnerability challenges.
Why They’re on This List
Strobes Security stands out for its modern, AI‑driven approach to exposure management and vulnerability prioritization. It is included here for:
- Comprehensive CTEM Coverage: Combines attack surface, vulnerability, and testing management in one platform.
- AI‑Driven Risk Prioritization: Focuses resources on the exposures most likely to impact the business.
- Proven Efficiency Gains: Cuts remediation times and false positives significantly.
- Strong Integration Framework: Connects with over 120 tools to unify security operations.
- Flexible Deployment: Fits the needs of both mid‑market and enterprise customers.
3. CrowdStrike – Cloud‑Native Endpoint and Threat Intelligence Leader
Company Profile Summary
| Attribute | Details |
| Founded | 2011 |
| Headquarters | Austin, Texas, United States |
| Employees | ~8,000+ |
| Revenue | $3B+ (FY2024) |
| Core Focus | Endpoint protection, cloud workload security, threat intelligence, and incident response |
| Key Customers / Industries | Fortune 500 enterprises, financial services, healthcare, retail, and government |
| Integration Strength | 100+ integrations across SIEM, SOAR, EDR, threat intel, and cloud platforms |
| Website | crowdstrike.com |
CrowdStrike is best known for its cloud-native Falcon platform, built to deliver EDR and XDR across endpoints, cloud workloads, identities, and mobile devices.
With its lightweight agent, real-time analytics, and strong threat intel, it has become the go-to platform for many modern SOCs. Its usage spans both mid-sized businesses and large, security-mature enterprises.
Notable Offerings
- Falcon Insight: EDR and XDR with real-time detection and response.
- Falcon Complete: Fully managed endpoint threat hunting.
- Falcon Cloud Security: Agentless and agent-based workload protection.
- Falcon Identity Threat Protection: Prevents lateral movement and identity-based attacks.
Recent Moves
- Launched Falcon Foundry, a no-code platform to build custom detections.
- Expanded CNAPP capabilities across multi-cloud.
- Acquired Bionic.ai to enhance application security visibility.
Best Fit / Who Should Choose
- Perfect for organizations that prioritize endpoint visibility and fast incident response.
- A natural choice for teams without a large SOC, but still need automated and managed detection.
- Also works well for cloud-native businesses scaling their security operations.
Pricing Insight
CrowdStrike operates on a modular pricing model, with per-endpoint and per-module rates.
Costs scale based on features added (XDR, cloud, identity, managed services).
Why They’re on This List
CrowdStrike is included for its modern EDR/XDR capabilities, strong threat intel, and growing adoption across cloud and identity security.
- Offers full-stack detection across endpoints, cloud, and identities
- Known for fast deployment and a lightweight agent
- Provides managed detection services for lean teams
- Backed by threat intel from CrowdStrike’s OverWatch team
4. Cisco Security – Comprehensive Enterprise Network and Cloud Security
Company Profile Summary
| Attribute | Details |
| Founded | 1984 |
| Headquarters | San Jose, California, United States |
| Employees | ~84,000+ |
| Revenue | $57B+ (FY2024, Cisco overall) |
| Core Focus | Network security, secure access, cloud security, threat intelligence |
| Key Customers / Industries | Large enterprises, service providers, government agencies, education, and healthcare |
| Integration Strength | Broad integration with networking, collaboration, SIEM, SOAR, and cloud platforms |
| Website | cisco.com |
Cisco has long been a backbone of enterprise networking and now plays a major role in cybersecurity. Its security solutions focus on securing users, endpoints, and infrastructure through both appliance-based and cloud-delivered services.
Cisco’s strength lies in embedding security into the network layer itself, making it a natural fit for large enterprises already invested in Cisco hardware and SD-WAN.
Notable Offerings
- Cisco Secure Firewall: Advanced threat defense with traffic segmentation.
- Cisco SecureX: XDR and orchestration across Cisco and third-party tools.
- Cisco Umbrella: Cloud-delivered DNS-layer and secure web gateway protection.
- Duo Security: Multi-factor authentication and access control.
Recent Moves
- Integrated XDR with Talos threat intel across the Cisco Secure portfolio.
- Enhanced Zero Trust capabilities via Duo’s adaptive access policies.
- Added extended visibility across hybrid cloud networks with Secure Firewall updates.
Best Fit / Who Should Choose
- Perfect for large enterprises that already use Cisco networking gear and want security built into it.
- A natural choice for companies building a Zero Trust strategy starting at the access and identity layer.
- Also well-suited for organizations prioritizing centralized management across campus, branch, and cloud networks.
Pricing Insight
Cisco offers bundled licensing across platforms or individual solution subscriptions.
Pricing often varies based on enterprise agreements and infrastructure size.
Why They’re on This List
Cisco is included for its ability to embed security within existing network infrastructure and extend it through cloud-managed platforms.
- Combines network, endpoint, and identity security in one ecosystem
- Built-in XDR and orchestration via SecureX
- Leverages threat intel from Cisco Talos
- Trusted by large enterprises managing complex hybrid environments
5. Fortinet – Integrated Network and Cybersecurity Solutions Provider
Company Profile Summary
| Attribute | Details |
| Founded | 2000 |
| Headquarters | Sunnyvale, California, United States |
| Employees | ~13,000+ |
| Revenue | $5B+ (FY2024) |
| Core Focus | Network security, SD‑WAN, secure access, cloud security |
| Key Customers / Industries | Enterprises, service providers, SMBs, government, and education |
| Integration Strength | Deep integration across the Fortinet Security Fabric ecosystem and third‑party tools |
| Website | fortinet.com |
Fortinet is known for delivering high-performance security through its FortiGate firewalls, SD-WAN appliances, and broad platform ecosystem. The Fortinet Security Fabric connects these layers with endpoint, access, and analytics modules under a single console.
With strong adoption in sectors like retail, manufacturing, and education, Fortinet is often selected where cost, performance, and centralized control are equally important.
Notable Offerings
- FortiGate: NGFW with built-in SD-WAN, SSL inspection, and IPS.
- FortiAnalyzer & FortiManager: Centralized management, logging, and analytics.
- FortiEDR: Endpoint protection and ransomware rollback.
- FortiNAC: Network access control across IT and OT.
- FortiSIEM: Unified SIEM with security event correlation.
Recent Moves
- Enhanced OT and industrial security features for ICS/SCADA.
- Expanded cloud-native firewall capabilities for hybrid deployments.
- Updated AI-powered threat detection across NGFW and endpoint layers.
Best Fit / Who Should Choose
- Perfect for organizations seeking high-throughput security across distributed environments.
- A natural choice for companies with branch-heavy or retail footprints needing integrated SD-WAN and firewall.
- Also fits teams looking to unify operations and security under one platform.
Pricing Insight
- Fortinet offers flexible appliance bundles and licensing tiers that support scale and performance planning.
- Often selected by businesses balancing performance with long-term platform consistency.
Why They’re on This List
Fortinet is included for combining network performance and security in one tightly integrated stack, with strong adoption in distributed enterprises.
- Security Fabric ties together the network, endpoint, and cloud
- Strong firewall performance with low latency
- Growing presence in OT and industrial security
- Centralized visibility across multiple security domains
6. Tenable – Vulnerability Management at Scale
Company Profile Summary
| Attribute | Details |
| Founded | 2002 |
| Headquarters | Columbia, Maryland, United States |
| Employees | ~2,500+ |
| Revenue | $800M+ (FY2024) |
| Core Focus | Vulnerability management, attack surface monitoring, exposure analytics |
| Key Customers / Industries | Government, finance, healthcare, education, and manufacturing |
| Integration Strength | Strong integrations with cloud providers, asset inventories, ticketing tools, and SIEMs |
| Website | tenable.com |
Tenable is known for helping organizations identify and prioritize vulnerabilities across IT, cloud, and container environments. Its flagship platform, Tenable.io, offers risk-based insights using asset criticality, exploitability, and threat intelligence.
The company also maintains Tenable.sc for on-prem deployments and Tenable Cloud Security for securing workloads and configurations.
Notable Offerings
- Tenable.io: Cloud-based vulnerability management platform.
- Tenable.sc: On-prem solution for mature, compliance-focused orgs.
- Tenable Cloud Security: Configuration and permission monitoring across AWS, Azure, and GCP.
- Tenable Nessus: Widely used vulnerability scanner trusted by practitioners.
Recent Moves
- Introduced AI-powered exposure analytics in Tenable One.
- Added SBOM inspection and software composition insights.
- Expanded integrations with cloud-native asset inventory tools.
Best Fit / Who Should Choose
- Perfect for organizations focused on proactive vulnerability detection and risk-based remediation.
- A natural choice for teams managing hybrid or multi-cloud infrastructures.
- Also valuable for compliance-heavy environments that need reporting, audit, and visibility in one place.
Pricing Insight
Tenable follows a per-asset pricing model based on license tiers and capabilities.
Packages vary by deployment model (cloud vs. on-prem) and scale of asset coverage.
Why They’re on This List
Tenable is included for its focus on helping organizations reduce exposure through continuous, data-driven vulnerability insights.
- Longstanding leader in vulnerability scanning and prioritization
- Offers both SaaS and on-prem deployment options
- Widely adopted in compliance and audit-focused teams
- Strong visibility into cloud, container, and on-prem assets
7. SentinelOne – Autonomous Endpoint and Cloud Workload Defense
Company Profile Summary
| Attribute | Details |
| Founded | 2013 |
| Headquarters | Mountain View, California, United States |
| Employees | ~2,300+ |
| Revenue | $875M+ (FY2024) |
| Core Focus | Endpoint security, XDR, cloud workload protection, autonomous response |
| Key Customers / Industries | Finance, healthcare, technology, legal, and education |
| Integration Strength | 100+ integrations with SIEM, SOAR, cloud providers, and IT operations tools |
| Website | sentinelone.com |
SentinelOne offers automated detection, response, and rollback across endpoints, cloud workloads, and identities. Its standout feature is autonomous protection, driven by AI models that detect and mitigate threats without manual intervention.
Often compared with CrowdStrike, SentinelOne appeals to organizations looking for speed, automation, and operational simplicity in threat response.
Notable Offerings
- Singularity XDR: Unifies endpoint, cloud, and identity telemetry.
- Ranger: Autonomous asset discovery and attack surface visibility.
- Cloud Workload Security: Protects Kubernetes and cloud-native applications.
- Storyline Active Response (STAR): Enables custom detection logic with automated remediation.
Recent Moves
- Released Purple AI, a GenAI assistant for SOC analysts.
- Added Linux protection for embedded systems and containers.
- Enhanced identity threat detection and cloud security posture insights.
Best Fit / Who Should Choose
- Perfect for teams seeking real-time detection and autonomous response.
- A natural fit for organizations with lean security teams that need strong protection with minimal tuning.
- Also ideal for companies that want built-in rollback and isolation features during ransomware or malware events.
Pricing Insight
- SentinelOne uses a per-agent pricing model, with tiers based on features like rollback, telemetry, and cloud coverage.
- Often priced competitively with other leading EDR/XDR vendors.
Why They’re on This List
SentinelOne is included for its AI-driven approach to endpoint and cloud security, offering speed, autonomy, and a strong open XDR foundation.
- AI-powered, real-time threat detection and response
- Automated rollback and attack containment
- Strong visibility across endpoints, containers, and identity
- Easy to deploy and manage for fast-moving teams
8. Zscaler – Cloud-Native Zero Trust and SASE Platform
Company Profile Summary
| Attribute | Details |
| Founded | 2007 |
| Headquarters | San Jose, California, United States |
| Employees | ~6,000+ |
| Revenue | $2.2B+ (FY2024) |
| Core Focus | Zero Trust, secure web access, cloud security, SASE |
| Key Customers / Industries | Fortune 500, healthcare, telecom, manufacturing, government |
| Integration Strength | Deep integrations with identity providers, SIEM, SD-WAN, EDR, and M365 apps |
| Website | zscaler.com |
Zscaler offers a cloud-native platform that securely connects users to applications — without relying on traditional network-based VPNs or firewalls. Its Zero Trust Exchange acts as a secure broker between users, apps, and devices across locations.
Zscaler is widely adopted by enterprises embracing hybrid work and cloud migration, especially where network perimeter models are being phased out.
Notable Offerings
- Zscaler Internet Access (ZIA): Replaces legacy SWG with inline cloud security.
- Zscaler Private Access (ZPA): Zero-trust access to internal apps without VPNs.
- ZDX (Zscaler Digital Experience): Monitors app performance and user experience.
- Zscaler Cloud Firewall: Inspects and controls traffic without physical appliances.
Recent Moves
- Rolled out AI-based policy tuning and anomaly detection features.
- Expanded ZDX capabilities with real-time diagnostics and SLA enforcement.
- Deepened integrations with identity providers and EDR platforms.
Best Fit / Who Should Choose
- Perfect for enterprises adopting Zero Trust architecture across a remote or hybrid workforce.
- A natural fit for teams replacing VPNs, firewalls, and proxies with cloud-delivered alternatives.
- Also ideal for global businesses that need scalable, user-to-app security without MPLS or complex appliances.
Pricing Insight
- Zscaler pricing depends on user count, access needs (ZIA/ZPA), and advanced modules.
- Licensing is typically per-user, per-service, and scales with security policies.
Why They’re on This List
Zscaler is included for its focus on enabling secure, scalable, identity-driven access across enterprise networks, without relying on legacy infrastructure.
- Purpose-built for Zero Trust network access
- Cloud-delivered, inline inspection and threat prevention
- Removes VPN complexity for internal applications
- Trusted by large enterprises for remote and hybrid environments
9. Rapid7 – Unified Security Operations for Modern Teams
Company Profile Summary
| Attribute | Details |
| Founded | 2000 |
| Headquarters | Boston, Massachusetts, United States |
| Employees | ~2,700+ |
| Revenue | $850M+ (FY2024) |
| Core Focus | Vulnerability management, SIEM, cloud security, detection, and response |
| Key Customers / Industries | Financial services, retail, healthcare, tech, education |
| Integration Strength | 300+ integrations across IT, cloud, DevOps, and SOC tools |
| Website | rapid7.com |
Rapid7 provides security analytics, visibility, and automation across IT environments through its cloud-native Insight Platform. Known for making security data more accessible to lean or mid-sized teams, it supports both SIEM/XDR workflows and vulnerability management.
It’s often chosen by orgs looking to unify detection, investigation, and response under one pane of glass without managing complex infrastructure.
Notable Offerings
- InsightVM: Risk-based vulnerability management.
- InsightIDR: SIEM and XDR with user behavior analytics.
- InsightCloudSec: Multi-cloud security posture and compliance.
- InsightConnect: Security orchestration and automation (SOAR).
Recent Moves
- Introduced AI-driven log analysis in InsightIDR.
- Expanded IAM misconfiguration detection in cloud platforms.
- Released deeper integrations with Microsoft Sentinel and AWS Security Hub.
Best Fit / Who Should Choose
- Perfect for security teams needing centralized visibility without large in-house resources.
- A natural fit for orgs with lean SOC teams and diverse attack surfaces.
- Also useful for cloud-heavy environments needing unified risk and incident tracking.
Pricing Insight
- Rapid7 pricing is modular, based on asset count, log volume, and feature tier.
- It offers flexible packages for cloud-first and hybrid customers.
Why They’re on This List
Rapid7 is included for enabling centralized risk and incident management across hybrid environments, with strong usability for mid-sized and growing teams.
- Unified analytics for vulnerability, cloud, and detection
- Cloud-native SIEM and XDR with UBA
- Widely used for compliance, threat detection, and automation
- Focused on simplifying security workflows for smaller teams
10. Check Point Software Technologies – Firewall and Threat Prevention
Company Profile Summary
| Attribute | Details |
| Founded | 1993 |
| Headquarters | San Carlos, California, United States (Global HQ: Tel Aviv, Israel) |
| Employees | ~6,200+ |
| Revenue | $2.4B+ (FY2024) |
| Core Focus | Network security, firewalls, threat prevention, cloud security |
| Key Customers / Industries | Government, finance, healthcare, telecom, manufacturing |
| Integration Strength | Integrates with SIEMs, identity providers, cloud platforms, and endpoint tools |
| Website | checkpoint.com |
Check Point has been a longstanding player in the cybersecurity space, known for its deep firewall expertise and broad platform coverage across cloud, endpoints, and networks. Its Infinity architecture ties together threat prevention, visibility, and access control across environments.
Check Point is used heavily in sectors that require multi-layered defense with centralized policy control, including finance and government.
Notable Offerings
- Quantum Security Gateways: High-performance NGFWs with threat prevention.
- Harmony: Endpoint, mobile, and collaboration app security.
- CloudGuard: Cloud security posture and workload protection.
- Infinity SOC: Unified threat detection, incident response, and XDR.
Recent Moves
- Expanded AI-based behavioral analysis across endpoints and gateways.
- Released automated incident response for Infinity SOC.
- Deepened coverage of SaaS security misconfigurations via CloudGuard.
Best Fit / Who Should Choose
- Perfect for enterprises needing layered protection with centralized policy enforcement.
- A natural fit for regulated sectors looking for consolidated visibility and threat prevention.
- Also strong for teams that prioritize custom policy tuning and fine-grained controls.
Pricing Insight
- Check Point offers appliance and cloud-delivered licensing, often customized by deployment model and features.
- Pricing varies based on product suite (Harmony, Quantum, CloudGuard).
Why They’re on This List
Check Point is included for its ability to deliver consistent protection across hybrid environments, anchored in deep NGFW and endpoint security experience.
- Long-established leader in firewall and gateway security
- Centralized platform for network, cloud, and user protection
- Emphasis on prevention-first architecture and policy enforcement
- Used across industries with high regulatory and uptime demands
How to Choose the Right Cybersecurity Company for Your Business

Choosing a cybersecurity vendor isn’t just a technical decision. It’s a business decision. The right platform can help you reduce risk, meet compliance requirements, and free up your team’s time. The wrong one? It adds more dashboards, more noise, and more delays.
Here’s how to approach the decision in a practical way.
1. Start with your environment, not just the tools
Before comparing vendors, map out what you’re actually trying to protect. Are most of your assets cloud-native? Do you manage a large on-prem infrastructure? Are your dev teams shipping code daily through CI/CD?
The answers to these questions will shape the kind of platform you need. If your environment is hybrid and fast-changing, you’ll need something that can adapt in real-time and integrate with multiple systems. If you’re working in a highly regulated sector, compliance automation may be a bigger priority than attack simulation.
2. Prioritize outcomes over features
It’s easy to get distracted by feature checklists. But what matters is what the platform helps you achieve.
For example:
- Can it actually reduce the number of hours your team spends on manual triage?
- Does it help you cut through thousands of vulnerabilities and focus on what’s exploitable in your setup?
- Does it make it easier to prepare audit-ready reports without pulling data from five different sources?
You don’t need all the features. You need the right ones that solve your operational challenges.
3. Look closely at integration and workflow fit
Your security stack isn’t built from scratch. You already have tools in place — Jira, Slack, ServiceNow, GitHub, vulnerability scanners, and cloud accounts.
Ask if the vendor can plug into those without forcing major changes to your workflows. Do they support bidirectional sync with your ticketing systems? Can they trigger actions based on CI/CD events? Do they offer APIs or webhooks for automation?
If the answer is no, you’re likely looking at a high operational overhead just to keep things in sync.
4. Evaluate scalability across teams, not just infrastructure
Scalability isn’t only about handling more assets. It’s also about how well the platform supports different teams — from AppSec and DevOps to compliance and executive leadership.
Check if the platform can handle role-based dashboards, asset ownership mapping, and remediation workflows that reflect how your organization actually functions. The more aligned it is with your internal processes, the easier it is to drive adoption across teams.
5. Ask about support and roadmap visibility
Even great tools need support. Ask real questions. How fast is their average response time? Is support limited to email, or do they offer Slack or phone access for critical issues? Can you influence the product roadmap if you’re an enterprise client?
Good support isn’t a luxury. It’s part of your risk reduction strategy.