The sheer scale and diversity of digital assets, spanning cloud environments, on-premises systems, IoT devices, and more—make it nearly impossible to address every vulnerability with equal urgency.
This is where asset correlation in vulnerability management becomes a pivotal strategy. By linking vulnerabilities to the assets they impact, organisations can prioritize remediation efforts based on the criticality of affected assets and the real-world risks they pose. Asset correlation bridges the gap between overwhelming vulnerability data and actionable insights, enabling teams to allocate resources efficiently and bolster their security posture.
In this blog, we explore the technical intricacies of Asset Correlation in Vulnerability Management, its critical role in effective risk reduction, and how Strobes’ advanced platform redefines the process, empowering organisations to stay ahead in an increasingly threat-rich environment.
What is Asset Correlation?
Asset correlation is the process of mapping vulnerabilities to their associated assets in a way that prioritizes remediation efforts based on contextual factors. These factors include the asset’s business importance, its exposure level, and its dependency relationships. Effective asset correlation relies on:
- Dynamic Asset Discovery: Continuous scanning and inventory of physical, virtual, and cloud-based assets.
- Contextual Enrichment: Augmenting raw data with metadata such as ownership, compliance requirements, and operational criticality.
- Risk Scoring Algorithms: Using advanced machine learning models to assign risk scores to vulnerabilities based on their potential exploitability and impact.
- Integration Across Toolchains: Aggregating data from vulnerability scanners, configuration management databases (CMDB), and threat intelligence platforms.
Without robust asset correlation, organizations face challenges such as inefficient prioritization, wasted resources, and prolonged exposure to exploitable risks.
Advanced Asset Correlation in Vulnerability Management with Strobes
The Strobes platform is engineered to redefine vulnerability management by embedding asset correlation into its core functionalities. Here’s how it delivers technical superiority:
- Real-Time Asset Discovery: Strobes integrates with leading discovery tools, such as Qualys, Nessus, and AWS Asset Manager, to create a dynamic inventory of all assets, whether they are on-premises, cloud-based, or in hybrid environments.
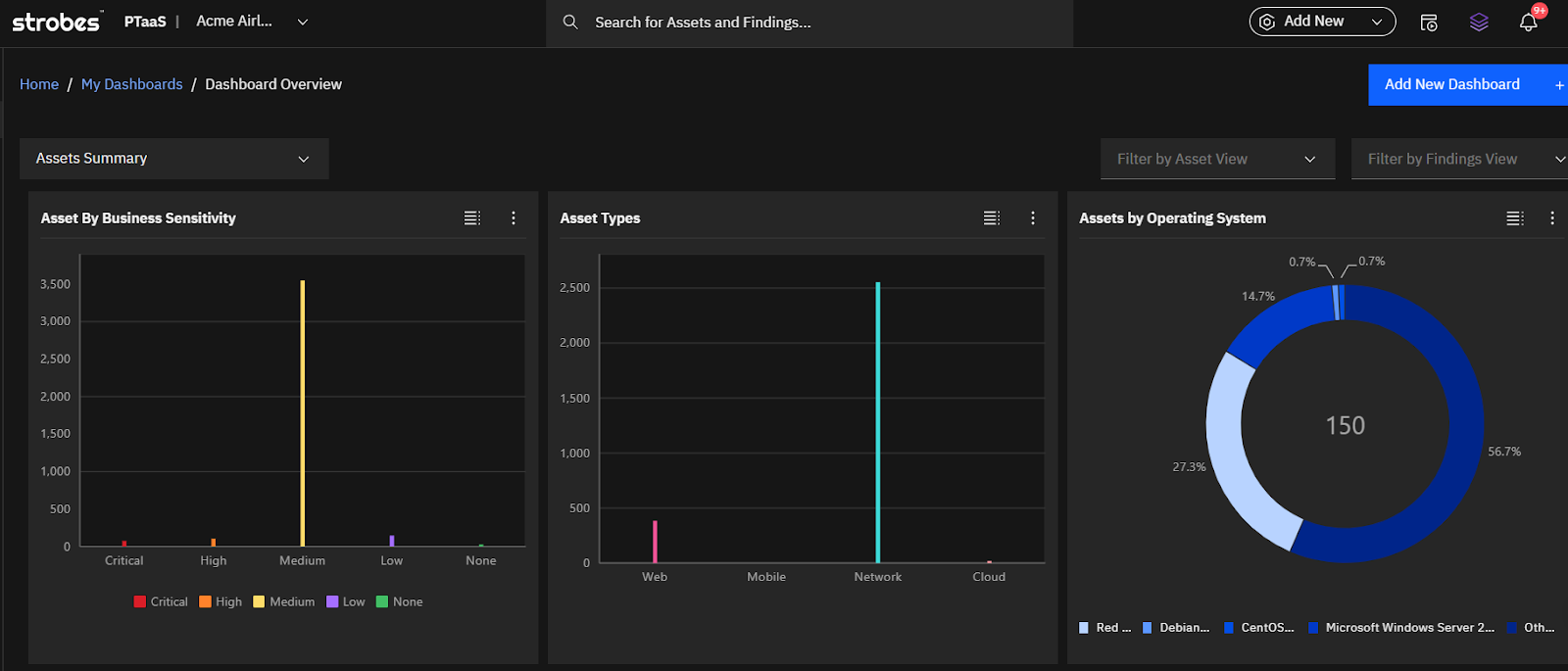
- Deep Contextual Analysis: By leveraging integrations with CMDBs and IT asset management (ITAM) tools, Strobes enriches asset data with attributes like:
- Criticality to business operations.
- Connectivity to other systems.
- Associated user roles and permissions.
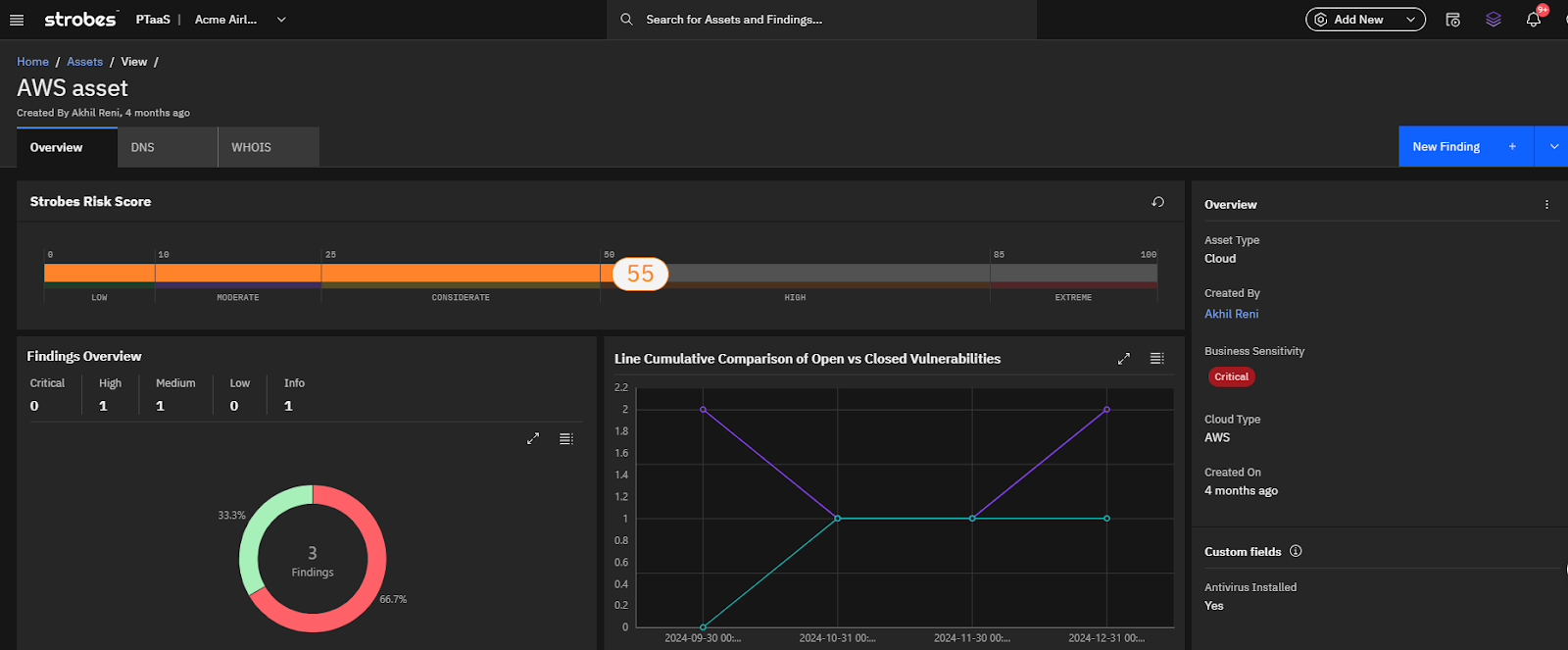
- AI-Driven Risk Prioritization: Strobes employs machine learning algorithms to calculate risk scores by considering:
- CVSS severity levels.
- Exploit maturity and availability in threat feeds.
- Asset sensitivity and exposure.
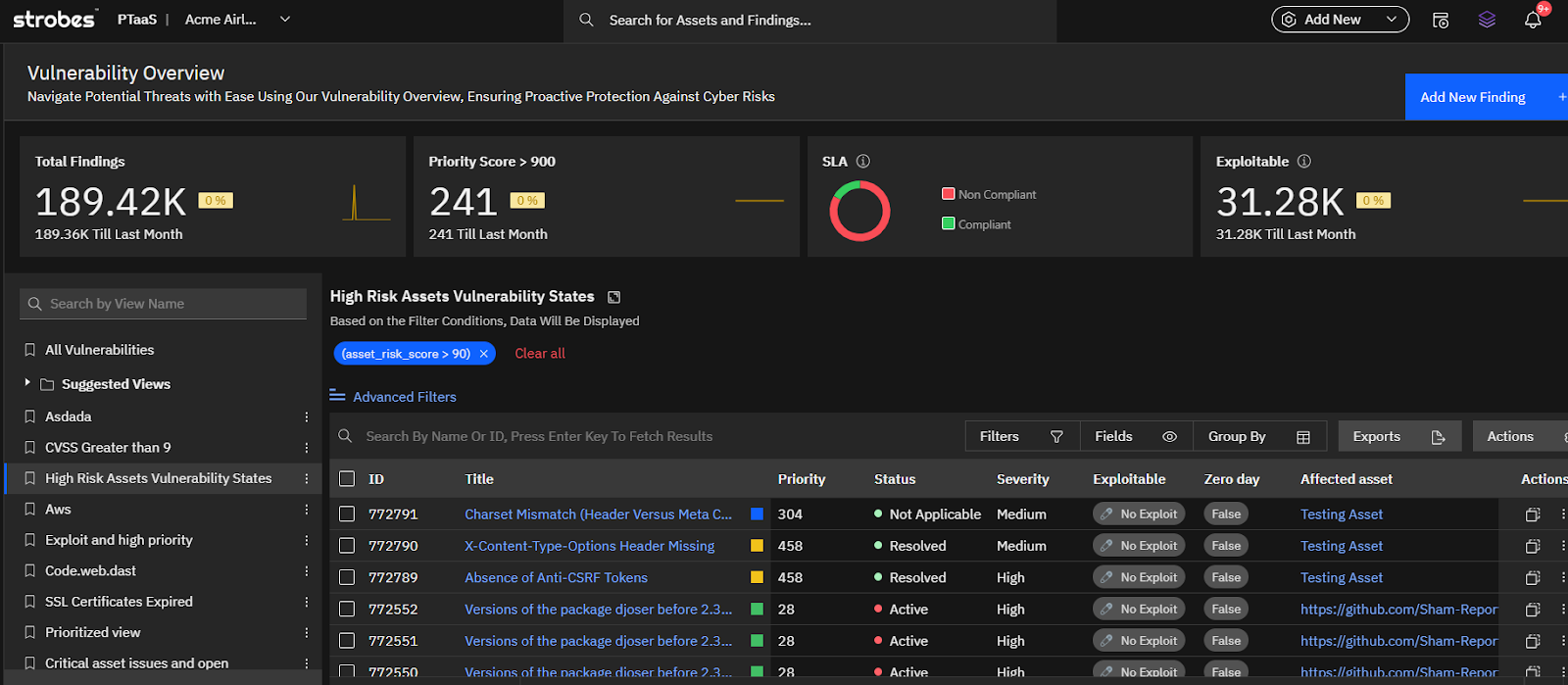
- Visual Dependency Mapping: The platform’s dependency visualization feature allows security teams to:
- Understand interdependencies between assets.
- Identify single points of failure.
- Simulate potential cascading impacts of vulnerabilities.
- Customizable Playbooks: Strobes allows the creation of automated remediation workflows that align with organizational policies and compliance requirements. By integrating with tools like Jira, ServiceNow, and Ansible, Strobes ensures vulnerabilities are addressed with minimal manual intervention.
Asset Correlation in Complex Environments
Modern IT environments, characterized by cloud-native applications, containerized workloads, and edge computing, add layers of complexity to vulnerability management. Asset correlation must account for the following:
- Dynamic Infrastructure: In cloud environments, ephemeral assets like containers and serverless functions require constant monitoring and reassessment.
- Distributed Architectures: Organizations operating in multi-cloud or hybrid setups need correlation that spans disparate environments seamlessly.
- Diverse Asset Types: From IoT devices to legacy systems, asset correlation must accommodate varied protocols and configurations.
How Strobes Addresses Complexity?
- Dynamic Updates: The platform’s real-time asset discovery ensures that transient assets are captured and evaluated.
- Cloud-Native Integrations: Strobes supports major platforms such as AWS, Azure, and Kubernetes, enabling holistic asset correlation.
- Unified Dashboards: Security teams can view vulnerabilities and associated risks across all environments in a consolidated interface.
Key Algorithms and Models Used in Strobes
Vulnerability Grouping Algorithms:
- Categorical Grouping: Vulnerabilities are grouped based on asset types such as application servers, databases, or network devices. This allows teams to focus remediation efforts on specific categories where issues are most prevalent.
- Cluster Analysis: Using clustering algorithms, Strobes identifies patterns of similar vulnerabilities across interconnected assets. For example, a misconfiguration pattern in multiple web servers can be identified and addressed collectively.
- Hierarchical Clustering: Strobes employs hierarchical clustering to organise vulnerabilities by severity and business impact, ensuring a structured prioritisation approach.
Weighted Risk Scoring Models:
- Dynamic CVSS Scoring: CVSS base scores are adjusted dynamically using factors like exploit maturity, exploit kit availability, and active attack vectors observed in the wild.
- Business-Driven Weighting: Risk scores are weighted according to asset importance, such as criticality to business operations or handling of sensitive data.
- Lateral Movement Analysis: Strobes incorporate algorithms that evaluate the potential for lateral movement, highlighting vulnerabilities that could escalate into widespread breaches.
Also Read: CVSS Score: A Comprehensive Guide to Vulnerability Scoring
Threat Intelligence Enrichment:
- Real-Time Integration: Strobes pulls data from industry-leading threat intelligence platforms like AlienVault and MISP, correlating vulnerabilities with active threat campaigns.
- Exploit Prediction Models: Machine learning models predict the likelihood of a vulnerability being exploited, providing an additional layer of prioritization.
- Historical Context Analysis: The platform tracks the history of exploits related to specific vulnerabilities, offering insights into recurrence and patch efficacy.
Graph-Based Correlation:
- Dependency Graph Modelling: Strobes uses graph databases to map asset inter-dependencies. For example, it can visualize how a vulnerability in a middleware server could impact downstream applications and databases.
- Attack Path Analysis: Graph-based models simulate potential attack paths, helping teams identify and secure high-risk chokepoints.
- Causal Relationship Mapping: By analysing causal relationships between vulnerabilities and assets, Strobes identifies systemic issues that require broader remediation efforts.
Practical Applications and Benefits
Scenario 1: Zero-Day Vulnerability Management
A zero-day exploit is discovered impacting an organization’s infrastructure. Traditional vulnerability management might:
- Identify hundreds of potential targets.
- Lack of clarity on which assets are mission-critical.
Also Read: The Ultimate Guide to Zero-Day Vulnerability Exploits & Attacks
Strobes’ Approach:
- Instantly identifies assets directly exposed to the exploit based on dependency mapping.
- Prioritizes remediation for assets handling sensitive data or critical operations.
- Provides detailed remediation steps aligned with organizational workflows.
Scenario 2: Compliance-Driven Remediation
An organization preparing for a PCI DSS audit must ensure vulnerabilities on payment systems are resolved promptly.
Strobes’ Approach:
- Automatically identifies assets within PCI DSS scope.
- Flags vulnerabilities that violate compliance requirements.
- Generates compliance-specific reports to demonstrate adherence.
Technical Challenges Addressed by Strobes
- Data Overload – Traditional vulnerability management tools often generate vast amounts of raw data, overwhelming security teams and making it difficult to focus on actionable insights. Strobes addresses this challenge by employing sophisticated filtering and prioritization mechanisms.
The platform categorizes vulnerabilities based on their business impact and technical severity, allowing teams to concentrate on high-priority risks. Additionally, Strobes provides customizable dashboards that summarize critical information, drastically reducing analysis time. - Integration Silos – Many organizations rely on disparate tools for asset management, vulnerability scanning, and threat intelligence. These silos lead to fragmented workflows and gaps in visibility. Strobes eliminates these issues through its open APIs and pre-built integrations with popular tools like Jira, ServiceNow, Qualys, and Splunk.
This seamless interoperability ensures that data flows smoothly across systems, enabling unified vulnerability management processes and better coordination between security and IT teams. - Scalability- Legacy vulnerability management systems struggle to handle the scale of modern IT infrastructures, especially in large enterprises with thousands of assets. Strobes is built on a scalable architecture that supports high volumes of data without performance degradation.
Whether managing vulnerabilities in a single cloud environment or across global data centers, the platform’s distributed processing capabilities ensure consistent and efficient performance, even under heavy workloads. - False Positives- One of the most significant challenges in vulnerability management is the high rate of false positives, which can divert resources away from real threats. Strobes mitigates this issue through advanced risk-scoring algorithms that combine CVSS scores with contextual factors like exploit availability, asset criticality, and real-world attack trends.
By correlating vulnerability data with actionable threat intelligence, the platform effectively filters out low-risk issues, ensuring that security teams focus on the most pressing threats.
Metrics to Evaluate Asset Correlation Success
Organizations can measure the effectiveness of their asset correlation strategies by tracking:
- Mean Time to Detect (MTTD): The speed at which vulnerabilities are correlated with relevant assets.
- Mean Time to Remediate (MTTR): The efficiency of resolving vulnerabilities post-correlation.
- Risk Reduction Percentage: Quantifiable decrease in overall risk exposure.
- Compliance Scores: Improved alignment with frameworks such as ISO 27001, NIST CSF, or GDPR.
Conclusion
Strobes eliminates this challenge by turning raw data into actionable intelligence—mapping vulnerabilities to business-critical assets, leveraging AI-driven risk scoring, and providing a unified, real-time view of an organization’s security posture. By embedding advanced techniques for Asset Correlation in Vulnerability Management, Strobes transforms vulnerability management into a proactive, intelligence-driven process.
Its AI-powered risk scoring, real-time asset discovery, and deep contextual analysis empower security teams to focus on what truly matters: remediating high-impact vulnerabilities efficiently.
With dynamic CVSS scoring and seamless tool chain integrations, Strobes enables organizations to:
- Prioritize remediation based on real-world risk.
- Eliminate noise and false positives.
- Automate vulnerability workflows with minimal manual intervention.
- Achieve compliance with industry standards effortlessly.
As cyber threats continue to evolve, asset correlation in vulnerability management will no longer be optional—it will be a necessity. Organizations that fail to implement robust asset correlation will struggle with security blind spots, while those leveraging platforms like Strobes will gain a competitive edge in resilience and risk mitigation.
Are you ready to revolutionise your vulnerability management strategy? Book a demo today and see how Strobes’ advanced asset correlation can help you stay ahead of threats.







