Radio-Frequency Identification (RFID) technology is everywhere—powering everything from contactless payments and inventory tracking to access control systems. But while RFID systems makes life more convenient, it also introduces serious security risks that many businesses overlook.
Hackers have found creative ways to exploit RFID vulnerabilities, potentially gaining unauthorized access to sensitive information, cloning access cards, or even disrupting entire systems. This raises a critical question: How secure is your RFID infrastructure?
To ensure these systems remain secure and reliable, rigorous RFID security testing is essential. From read range testing to encryption assessments, companies need to proactively identify weaknesses before bad actors do.
In this blog, we’ll dive into how RFID technology works, common hacking methods, and best practices for testing and securing your RFID ecosystem.
Understanding RFID Systems and the Importance of Testing
RFID technology plays a vital role in modern tracking and identification systems, making it essential to ensure its security and efficiency through rigorous testing. This article explores why RFID testing is crucial, the commonly used testing methods, and best practices for optimizing performance and security.
At its core, RFID technology consists of two primary components: RFID readers and RFID tags. These elements work in tandem with an RFID software system to automatically identify and track objects in various applications, from inventory management to access control.
When an RFID reader scans an object, it emits a radio frequency (RF) signal that interacts with nearby RFID tags, potentially up to 1.14 million tags in a single area. The antenna on each tag absorbs this energy, powering the embedded microchip. The chip then encodes its stored data into a binary format (0s and 1s) and transmits it back to the RFID reader using reverse signal modulation. The collected data is then stored and processed, either for human interpretation or automated system operations.
Given its widespread use, ensuring the reliability and security of RFID systems is critical. That’s why thorough performance, security, and compliance testing is necessary to protect against vulnerabilities and maintain operational efficiency.
Also Read: Why Penetration Testing Is Important: Enhancing Security & Reducing Cyber Risks
RFID standards and protocols
As with many wireless technologies, RFID technology adheres to certain standards and communication protocols. Because it operates over a number of frequency bands, RFID technology is regulated by many authorities worldwide. In the United States, the FCC (Federal Communications Commission) is the main body that assigns operational bands for various ISM (Industrial, Scientific, and Medical) radio devices, including RFID.
In Europe, the use of RFID is regulated by the ETSI (European Telecommunications Standards Institute). Japan, India, and other countries have their own regulatory bodies that determine appropriate frequency bands for the operation of RFID systems.
RFID frequencies are as follows:
- Low Frequency (LF, 125KHz)
- High Frequency (HF, 13.56MHz)
- Ultra High Frequency (UHF, 860 MHz-960 MHz)
RFID technology is also regulated by various standards such as EPC standards and ISO standards. These standards define the ‘air interface protocol’ that RFID readers and RFID tags use to communicate and how data is read and written.
What is an RFID Tag?
Radio frequency identification (RFID) tags, which could also be called RFID chips, are a type of tracking system that employs smart barcodes. What do we mean by “smart barcodes”? A standard barcode transmits data to a reader in a straight line. You might think of it as working pretty much the same way as a painted line on the ground, which a runner must follow to reach the finish line.
But for an item like a car not only to be read but also to be understood when it reaches the finish line in the RFID computer program, the data must be encoded so that the message it carries can be deciphered.
How do RFID Tags Work?
An RFID tag operates by sending and receiving signals through an antenna and a microchip, or integrated circuit (IC). The IC in RFID tags is encoded with the precise information that the tag is meant to store and relay. Tags can come in different forms, some are small and flat like stickers, and others are rigid and about the size of a credit card.
In addition, some hard-core RFID enthusiasts have managed to slip RFID chips into everyday objects like pens and sheet magnets. Adding to the possible forms that RFID tags can take, some interesting research is being done on the possibility of embedding the chips inside human beings.
Types of RFID Tags
RFID tags are broadly classified into two main types: active (battery-operated) and passive. Each type functions differently and is suited for specific applications based on factors such as power source, range, and durability.
1. Active RFID Tags (Battery-Operated)
Active RFID tags are equipped with an onboard battery, which serves as their power source. These tags continuously broadcast signals, making them ideal for tracking assets over long distances.
Key Features of Active RFID Tags:
- Operate at 433 MHz or 915 MHz frequency bands
- Longer transmission range compared to passive tags
- Typically last 3-5 years before the battery depletes
- Used for high-value asset tracking, logistics, and vehicle monitoring
- Contain three primary components:Tag: Stores and transmits data
Antenna: Facilitates communication with the reader
Interrogator: Manages the data exchange
Once the battery dies, the entire unit must be replaced, as the batteries in most active RFID tags are not replaceable.
2. Passive RFID Tags (Battery-Free)
Unlike active tags, passive RFID tags do not have a built-in battery. Instead, they rely on the electromagnetic energy transmitted by an RFID reader to power their microchip and antenna.
Frequency Ranges of Passive RFID Tags:
Passive RFID tags operate across three primary frequency bands:
- Low Frequency (LF) – 125 – 134 KHz (Short-range applications like animal tracking)
- High Frequency (HF) – 13.56 MHz (Used for Near-Field Communication (NFC), payments, and secure access control)
- Ultra High Frequency (UHF) – 865 – 960 MHz (Long-range applications like supply chain tracking)
The frequency used directly influences the range and performance of the tag.
When an RFID reader scans a passive tag, it transmits energy to the tag, activating it just long enough for the microchip to encode and send data back. This data is then processed by the RFID system for interpretation.
Types of Passive RFID Tags
Passive RFID tags come in two main forms based on their physical structure and application:
1. Inlays:
- Thin and flexible, designed for adhesive attachment
- Often found on product labels, retail packaging, and ID cards
2. Hard Tags:
- Made of durable materials such as plastic or metal
- Resistant to harsh environmental conditions
- Used for industrial applications, asset tracking, and equipment monitoring
Choosing the Right RFID Tag
- Active RFID tags are best suited for long-range tracking and real-time monitoring.
- Passive RFID tags are ideal for cost-effective, close-range identification in access control, inventory management, and retail applications.
Understanding the differences between active and passive RFID tags is crucial for optimizing RFID-based security and tracking systems in any industry.
Why RFID Testing is Crucial
RFID systems are complex and involve multiple components, including tags, readers, antennas, and software. Testing is crucial to verify that all components work together seamlessly and meet the desired performance standards. Here’s why RFID testing is essential:
- Performance Validation: Ensures that RFID systems can read and write data accurately under various conditions.
- Reliability Assurance: Verifies that the system operates consistently over time and across different environments.
- Security Testing: Identifies vulnerabilities to prevent unauthorized access and ensure data integrity.
- Compliance Verification: Ensures that the RFID system adheres to industry standards and regulations.
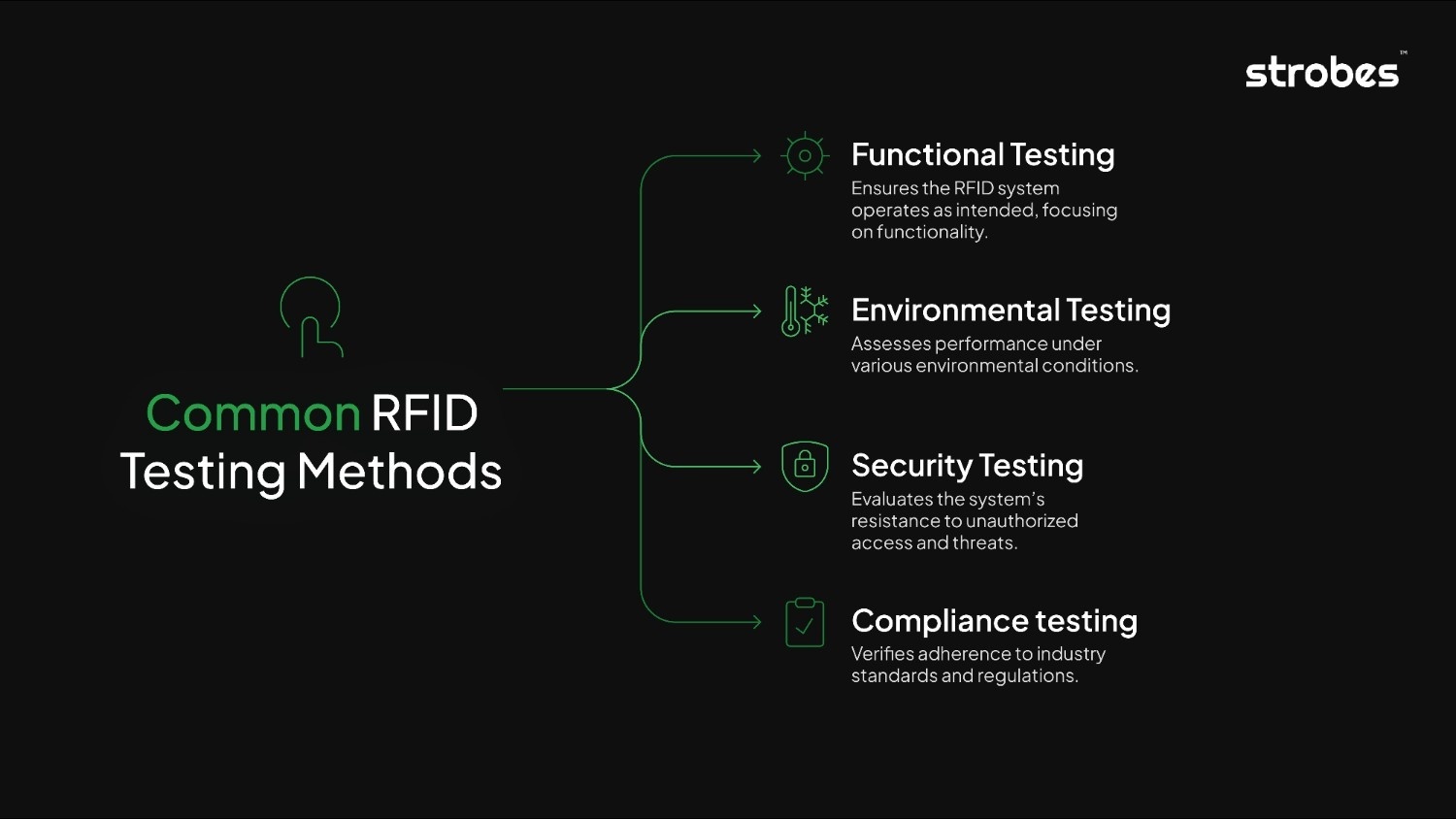
Common RFID Testing Methods
1. Functional Testing
Functional testing verifies that the RFID system performs its intended functions. This includes checking if the system can correctly read and write data to RFID tags and if the tags are properly identified and processed by the reader.
- Read Range Testing: Determines the maximum distance at which a reader can successfully read a tag.
- Write Range Testing: Measures the distance at which data can be written to a tag.
- Tag Response Time: Assesses the time taken by a tag to respond to a reader’s query.
2. Environmental Testing
RFID systems are often used in diverse environments, so testing under various conditions is crucial.
- Temperature Testing: Evaluates system performance in extreme temperatures.
- Humidity Testing: Assesses how moisture and humidity affect RFID functionality.
- Interference Testing: Checks how other electronic devices or materials impact RFID performance.
3. Security Testing
Security testing ensures that RFID systems are resistant to potential threats.
- Encryption Testing: Verifies that data transmitted between tags and readers is encrypted and secure.
- Access Control Testing: Ensures that only authorized personnel can access or modify the system.
- Vulnerability Assessment: Identifies potential security weaknesses and threats.
4. Compliance Testing
Compliance testing ensures that the RFID system adheres to industry standards and regulations.
- Regulatory Compliance: Verifies adherence to local and international regulations (e.g., ISO standards, FCC regulations).
- Interoperability Testing: Ensures that RFID components from different manufacturers work together seamlessly.
RFID testing results can be used to determine any problems and enhance RFID systems functionality and performance. To guarantee the dependability and functionality of RFID systems in real-world circumstances, RFID testing is a crucial component of product development and certification.
Trusted by leading enterprises like, GHX, Zoho, Darwinbox, Tricenties, and SHL
Strobes helped organizations continuously manage threats, reduce vulnerabilities, and stay compliant, powered by AI-driven security expertise.
Strobes Solutions: Security Testing for Compliance
Common IoT Test cases
To verify and validate IoT testing applications, the test engineers need to ensure the following types of testing are planned, designed, and executed to ensure full quality coverage:
| Functionality |
|
| Connectivity |
|
| Usability |
|
| Compatibility |
|
| Security |
|
| Performance |
|
Defending Against RFID Hacking in a Digital World
As RFID technology becomes increasingly embedded in everyday operations, from access control and inventory tracking to cashless payments, the risks associated with RFID hacking cannot be ignored. The same features that make RFID efficient and convenient, wireless communication and automatic identification, also make it vulnerable to cyber threats.
RFID hacking techniques, such as cloning, skimming, eavesdropping, and relay attacks, allow cybercriminals to intercept sensitive information, manipulate access controls, or even exploit entire systems. Without proper security measures, businesses and individuals risk unauthorized data breaches, financial fraud, and identity theft.
Also Read: Top Data Breaches of February 2025
To combat RFID hacking, organizations must adopt a proactive security approach that includes:
- Thorough penetration testing and security audits to uncover vulnerabilities before attackers do.
- Strong encryption and authentication protocols to prevent data interception and unauthorized access.
- RFID shielding solutions such as Faraday cages and blocking wallets to protect against unauthorized scanning.
- Multi-factor authentication (MFA) for RFID-based access control systems to add an extra layer of security.
- Employee and consumer awareness programs to educate on RFID hacking risks and protective measures.
The fight against RFID hacking is an ongoing challenge that requires constant vigilance, innovation, and security reinforcements. By integrating robust cybersecurity strategies, implementing best practices, and staying ahead of emerging hacking techniques, businesses can ensure their RFID infrastructure remains secure and resilient.
As hackers continue to exploit weaknesses in wireless technologies, companies that fail to prioritize RFID security may find themselves exposed to costly cyber threats. The key to staying ahead of RFID hacking lies in continuous security testing, risk-based vulnerability management, and a commitment to evolving cybersecurity standards.
Businesses and individuals must take RFID hacking seriously. The only way to truly leverage the power of RFID without compromising security is to stay informed, invest in security measures, and ensure regular system testing.
Book a demo with Strobes to discover how our security testing solutions can help you safeguard your RFID systems against evolving cyber threats.
Related Reads:
- Integrating PTaaS with CI/CD Pipelines: A Guide to CI/CD Security Testing
- Why Penetration Testing Is Important: Enhancing Security & Reducing Cyber Risks
- Strobes Security Scanners: Application Security for Modern Enterprises
- Web Application Penetration Testing: Steps & Test Cases
- Solution: Pentesting as a Service
- Solution: Breach & Attack Simulation Services