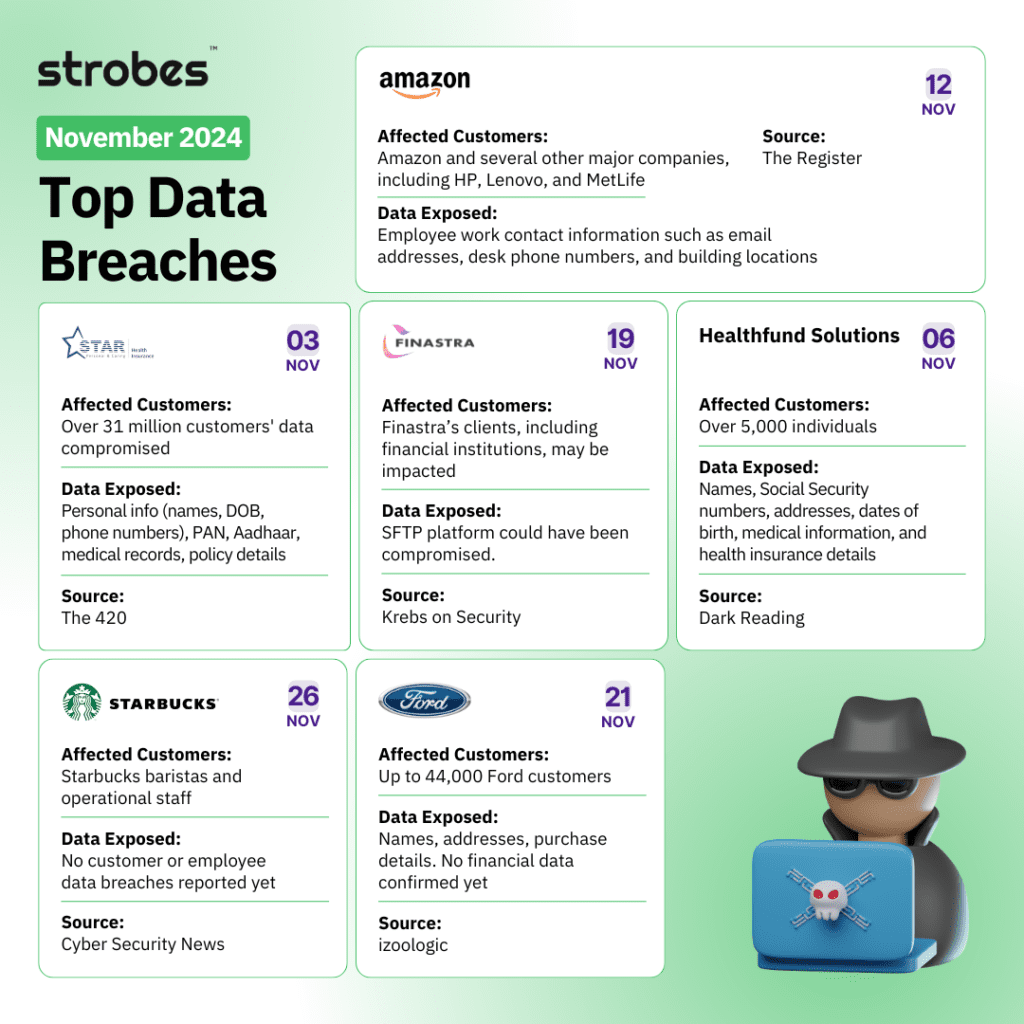
As data breaches become increasingly common, the statistics reveal alarming trends: over 35 billion records have been breached throughout the year, with the average cost of a data breach rising to $4.88 million globally, a 10% increase from the previous year. This month alone saw several significant incidents that affected thousands of individuals and organizations.
1. Ford Investigates Alleged Security Breach After Data Leak
Ford is actively investigating an alleged security breach involving the leak of sensitive data reportedly affecting up to 44,000 customer records. Cybercriminals associated with the forum BreachForums—specifically a group called IntelBroker and EnergyWeaponUser—claimed responsibility for releasing the data, which includes customer names, addresses, and purchase details. The data was made available for free, potentially as an effort to damage Ford’s reputation, rather than for financial gain.
While Ford has yet to confirm the breach’s scope, they emphasize that no direct compromise of their systems or customer data has been verified. The company is examining whether a third-party supplier might be involved in the incident. This leak raises significant concerns, as the exposed information could be used for identity theft or social engineering attacks, prompting security experts to advise vigilance among potentially affected customers.
2. Starbucks Hit by Ransomware Attack via Third-Party Supplier
Starbucks experienced significant operational disruptions due to a ransomware attack targeting its third-party software supplier, Blue Yonder. This Arizona-based provider, crucial for Starbucks’ employee scheduling and payment systems, faced a cyber intrusion, causing widespread service outages. As a result, Starbucks had to shift to manual processes for managing barista schedules and ensuring payroll continuity. The attack also impacted other retailers relying on Blue Yonder’s supply chain software. Starbucks is collaborating with cybersecurity firm CrowdStrike to mitigate the situation and enhance future defenses.
3. Healthfund Solutions Faces Data Breach Disclosure
HealthFund Solutions, a healthcare solutions provider based in Florida, recently reported a data breach impacting sensitive personal and medical information. On August 14, 2024, the company identified unauthorized access to an employee email account. This prompted an investigation, which confirmed that personally identifiable information (PII) and protected health information (PHI) of over 5,000 individuals were potentially compromised. The affected data varied by individual and included names, Social Security numbers, addresses, dates of birth, medical information, and health insurance details.
The company concluded its investigation on October 4, 2024, and began notifying affected individuals on November 1, 2024. These notifications included specifics about the breached data for each individual. HealthFund Solutions provides credit monitoring services to mitigate risks such as identity theft and fraud, which often result from breaches involving such sensitive information
This incident underscores the importance of robust cybersecurity measures, especially in sectors dealing with sensitive health data. Those affected should consider monitoring their accounts, updating security credentials, and enrolling in credit monitoring to safeguard against potential data misuse.
4. Finastra Investigates Data Breach Impacting Internal SFTP Platform
Finastra, a global leader in fintech solutions, is currently investigating a significant data breach that has affected its internal systems. The breach is believed to have impacted their secure file transfer platform (SFTP), which is used for handling sensitive data transfers across their network. The incident, reported on November 19, 2024, prompted the company to launch an internal investigation, though further details about the scope of the breach remain unclear.
The hacker responsible for the attack has claimed responsibility, adding a layer of complexity to the situation. This breach could have serious implications for Finastra’s clients, as the platform in question handles a variety of financial and transactional data. However, the company has assured that they are working closely with cybersecurity experts and law enforcement to understand the breach’s full impact and implement measures to prevent further unauthorized access.
While the investigation continues, Finastra has yet to disclose specific details regarding the number of affected individuals or organizations, or whether any financial data has been exposed. As of now, they are focusing on securing their infrastructure and ensuring that such an incident does not recur in the future.
5. Amazon Confirms Employee Data Breach Linked to MOVEit Vulnerability
Amazon has confirmed that employee data was exposed as part of a larger data breach linked to the MOVEit vulnerability from May 2023. The breach involved a third-party vendor providing property management services to Amazon, not Amazon’s internal systems or AWS infrastructure. While Amazon’s systems remained secure, data compromised in this breach included employee work contact information, such as email addresses, desk phone numbers, and building locations.
The incident is connected to a broader breach of the MOVEit Transfer software, which was targeted by the Cl0p hacking group exploiting a zero-day SQL injection vulnerability. This breach impacted multiple organizations, with the hacker, operating under the alias ‘Nam3L3ss,’ claiming to have leaked millions of records, including data from Amazon and other major tech companies like HP and Lenovo.
Although the exact number of Amazon employees affected has not been disclosed, the breach highlights the risks posed by third-party vendors and their associated supply chains. Amazon has emphasized that the exposed data was limited and did not affect its core systems.
6. Star Health Data Breach
The data breach involving Star Health Insurance has raised significant concerns, with claims pointing to a breach that compromised the personal and sensitive data of over 31 million customers. The breach was allegedly executed by a hacker named xenZen, who has put the stolen data up for sale online, claiming to have purchased it from Star Health’s Chief Information Security Officer (CISO), Amarjeet Khanuja.
According to the hacker, the transaction involved the sale of the data for $43,000, which was allegedly arranged via encrypted communication. The hacker even released details about the transaction, including alleged screenshots of interactions between them and Khanuja. The stolen data includes sensitive information such as PAN and Aadhaar numbers, medical records, and insurance claim details, which are now being sold in bulk or in smaller packages.
Star Health, on its part, has denied these allegations, asserting that the breach was a malicious cyberattack and not an insider leak. The company has filed a lawsuit against the hacker and platforms like Telegram, which were used to facilitate the leak. The firm is also conducting an internal investigation with the help of cybersecurity experts and collaborating with authorities.
The breach not only impacted individual policyholders but also raised concerns over the integrity of data protection measures at major institutions. While Star Health maintains that its services are unaffected, the incident highlights the growing risks associated with cybersecurity vulnerabilities within the health insurance sector.
Final Words:
November’s data breaches underscore the critical need for cybersecurity across all organizations. To effectively protect your business, consider partnering with Strobes, which offers a comprehensive suite of security solutions tailored to your needs. Strobes’ solutions are designed to maintain customer trust by ensuring the confidentiality, integrity, and availability of mission-critical resources. With the rise in cyber threats, including ransomware and data breaches, a multi-layered approach to security is essential. Contact us today and get a free trial.