The cloud has revolutionized how businesses operate, offering unprecedented agility and scalability. However, this rapid adoption has also introduced a new wave of security challenges. CASM Security plays a crucial role in addressing these risks. A recent Checkpoint cloud security report underscores the gravity of the situation: 61% of organizations have suffered cloud security incidents this year alone, with a staggering 21% resulting in data breaches.
In this blog, we’ll go into detail about the specific challenges organizations face in securing their cloud infrastructure and demonstrate how Strobes addresses these issues head-on. We’ll explore how Strobes goes beyond traditional security solutions to provide a holistic approach that empowers you to confidently navigate the complexities of the cloud.
Strobes tackles these challenges head-on. It provides a powerful solution unifying Cloud Attack Surface Management (CASM), Cloud Security Posture Management (CSPM), and a deep cloud asset inventory to give unparalleled cloud security visibility.
Here’s why Strobes excels for CASM Security:
- Unmatched Visibility: Strobes relentlessly scours multi-cloud environments, unearthing shadow IT and unauthorized resources alongside managed assets. It tracks everything from compute to APIs to user identities.
- Prioritize Action, Not Alerts: Strobes doesn’t focus solely on discovery. It automatically prioritizes detected misconfigurations, risk based vulnerability management and cloud resource drifts based on your most critical assets and relevant regulatory controls.
- Compliance Confidence: With extensive out-of-the-box support for GDPR, HIPAA, PCI DSS, and more, Strobes continuously demonstrates compliance with detailed, customised reports at your fingertips.
In what follows, we’ll explore how Strobes specifically solves complex CASM Security problems that plague modern organizations.
What Problems Are We Solving Exactly?
Moving to the cloud is a popular choice for its benefits, but it can expose security vulnerabilities. This is because many companies struggle to bridge the gap between their existing on-premise security practices and the different processes, tools, and teams responsible for the cloud. As a result, they face several challenges:
- Exploding Attack Surface and Lack of Visibility: Strobes reveals shadow IT, dependencies between assets, and maps complex external attack surfaces that manual auditing or infrequent scans miss.
- Misconfigurations: Our inbuilt policies highlight misconfigurations against industry best practices, reducing the chance of errors introducing catastrophic risk.
- Vulnerabilities and Unpatched Systems: Strobes integrates with industry-leading scanners and asset data to match known vulnerabilities to your active inventory. Patching is prioritized on risk, not noise.
- Unmanaged Identities and Excessive Permissions: Strobes analyzes cloud identities against roles to uncover over-provisioned accounts, orphaned users, and other IAM weaknesses increasing compromise risk.
- Compliance Challenges: Strobes automatically maps findings to compliance controls. Pre-built compliance reports for common standards speed up auditing and evidence gathering.
How Do Strobes Help You Navigate Through the Cloud Clutter?
Strobes cuts through the chaos. Our powerful solution combines Cloud Attack Surface Management (CASM), Cloud Security Posture Management (CSPM), and a comprehensive cloud asset inventory, giving you unparalleled visibility and control over your entire cloud landscape.
Strobes understands cloud security demands a shift in approach. Perimeter-focused models and time-delayed scanning aren’t enough. Our platform enables teams to:
- Know Cloud Environment: Deep, automated asset discovery across infrastructure, data, and workloads illuminates potential attack paths and gaps in governance.
- Proactive Risk Reduction: Continuous assessment against policy and vulnerability data pinpoints problems before attackers can exploit them.
- Adapt Alongside the Cloud: Strobes is built for multi-cloud, supporting evolving services, so your security keeps pace with innovation.
In the face of escalating cloud security challenges, a proactive and continuous approach is essential. Organizations can significantly reduce their risk profile by combining the capabilities of Cloud Attack Surface Management (CASM), Cloud Security Posture Management (CSPM), and a centralized cloud asset inventory.
1. Cloud Attack Surface Management (CASM) with Strobes
While central to continuous cloud security, CASM goes far beyond simple asset listings. Strobes delivers an unmatched level of CASM power:
- Discover the Truly Unknown: Our discovery methods don’t stop at common infrastructure. Strobes finds orphaned SaaS subscriptions, unmanaged API endpoints, and forgotten PaaS resources that create gaping security holes.
- Visualize Risk, Not Just Assets: Attack surface graphs in Strobes automatically illuminate critical connections, prioritizing areas with the highest exposure and most likely paths for an attacker to exploit.
- Risk-Based Monitoring: Many CASM tools alert on “new.” Strobes factors in asset sensitivity, potential exploitability, and your evolving threat profile to reduce alert fatigue and focus your team on critical threats.
2. Cloud Security Posture Management (CSPM) with Strobes
Strobes ensures your cloud environment stays locked down while allowing the flexibility needed for innovation:
- Automate Posture Checks: Stop relying on manual audits. Strobes continuously evaluates configurations, comparing them to industry benchmarks and your organization’s own internal policies for truly effective governance.
- Contextual Vulnerability Analysis: A common CVE on a non-critical asset is still noise. Strobes factors in data sensitivity, business context, and threat intelligence for real-world risk assessment that cuts through the hype.
- Policy as Code Integration (Optional): If Strobes can integrate with existing infrastructure as code (IaC) tools, mention it here. Show how policy violations are caught early in the development lifecycle.
- Remediation Guidance: Strobes go beyond merely flagging a problem. It suggests prioritized corrective actions tailored to your environment, providing either in-tool remediation or seamless integration with your ticketing workflows.
Solution: Strobes CSPM Integration
3. Cloud Asset Inventory with Strobes
Strobes asset inventory isn’t just a database; it’s the always-accurate intelligence that powers sound security decisions:
- Beyond Infrastructure: Strobes inventories cloud configurations, application dependencies, data flows, IAM roles— everything needed to comprehend your overall risk exposure.
- Change Tracking for Security Context: Every modification to an asset or its relations is logged in Strobes. Not only does this aid in troubleshooting, it empowers forensic analysis for security incidents.
- Extensible Platform: Custom attributes are key to tracking what matters to your organization. Use Strobes tagging and enrichment capabilities to go beyond standard IT asset fields and align with the way you view risk.
Strobes: Unifying Cloud Security Beyond the Limitations of Others
Tired of juggling multiple tools and battling blind spots in your cloud security? Strobes offers a unified platform that surpasses the limitations of both cloud provider tools and dedicated vendors. Here’s how-
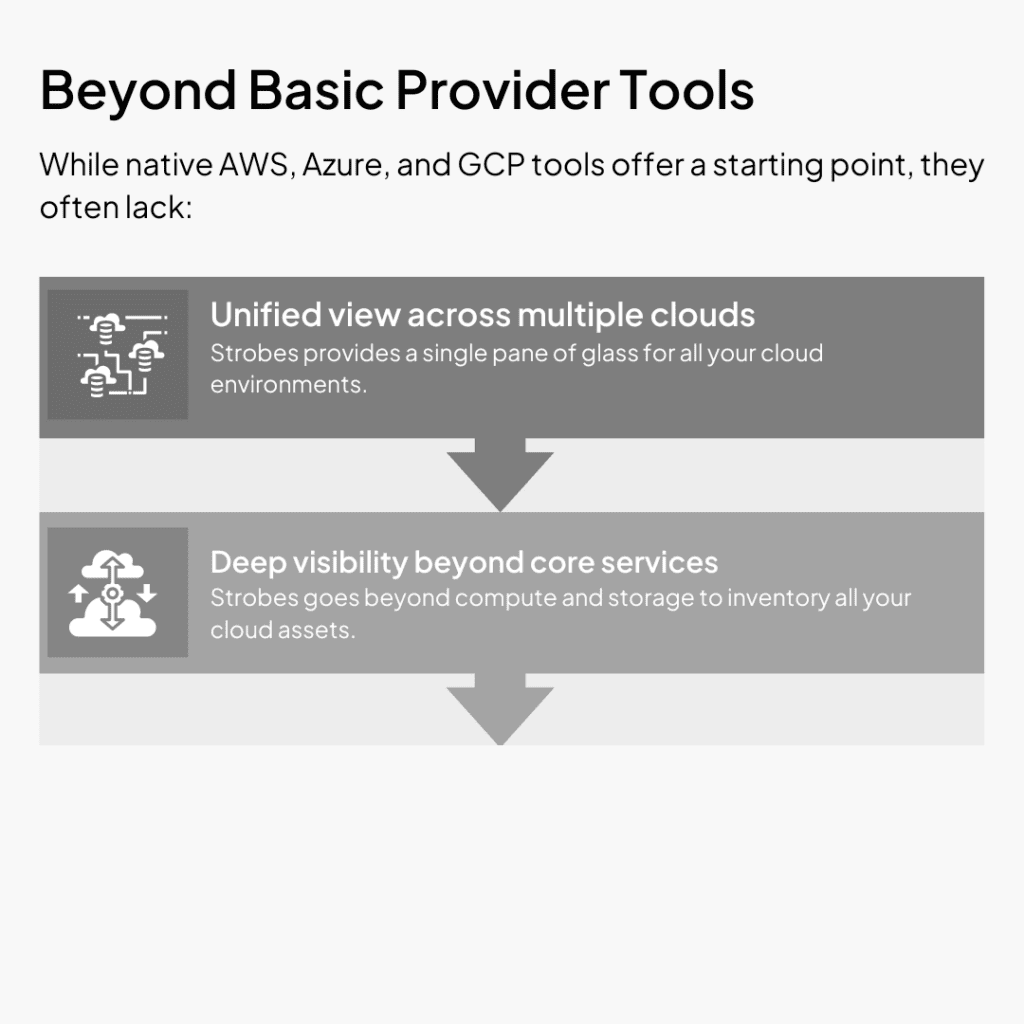
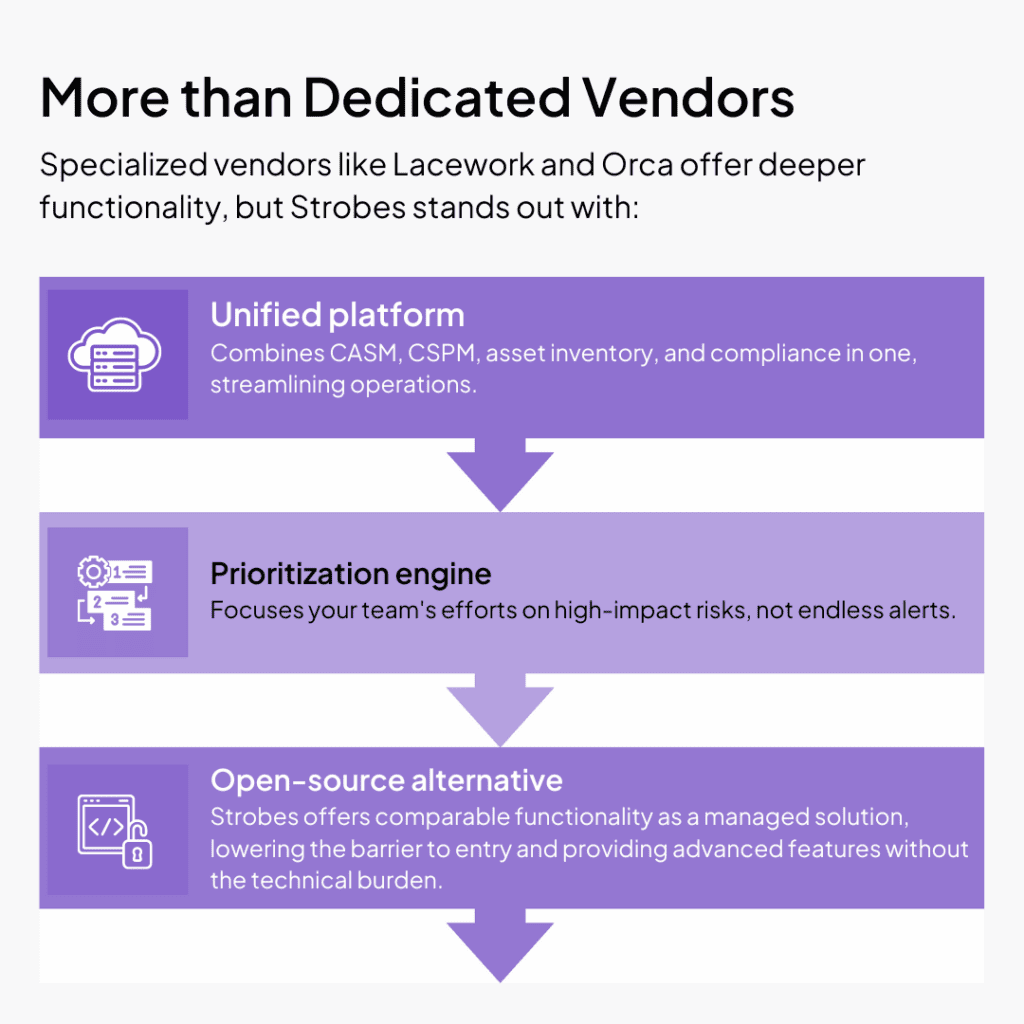
- Uncovering Hidden Risks: CASM continuously discovers and catalogs all cloud assets, both authorized and unknown, identifying potential vulnerabilities and revealing any “shadow IT” that puts the organization at risk.
- Enforcing Best Practices and Compliance: CSPM constantly monitors cloud configurations against security benchmarks and relevant compliance frameworks. It highlights misconfigurations, policy violations, and vulnerabilities, allowing teams to prioritize remediation efforts.
- Maintaining Centralized Visibility: A cloud asset inventory serves as a foundational “source of truth.” It tracks assets, their configurations, and relationships over time, ensuring a consistent and up-to-date view of security posture.
What Makes Strobes Solutions Better?
Check out this handy table mapping Strobes awesomeness to common cloud security concerns!
| Feature | Cloud Native Tools | Typical Vendor | Strobes |
| Cloud Providers Supported | Platform-specific | Multi-cloud support varies | AWS, Azure, GCP + focus on SaaS discovery |
| Depth of Asset Discovery | VMs, core storage | Deeper into containers, apps | Strobes excels: Unmanaged SaaS, APIs, IAM |
| Posture Rules (out-of-box) | Limited coverage | Framework coverage, some custom | Extensive mapping to frameworks |
| Vulnerability Coverage | Often requires separate tool | Integration varies | Built-in, vulnerability context engine |
| Compliance Focus | May require manual work | Varies by vendor | Audit-ready reports, policy drift detection |
| Pricing | Consumption or flat VM rate | Per-asset, user-based models | Bundled pricing, potential long-term discounts, support included |
Get Compliance-Ready With Strobes
- Always Audit-Ready: Strobes in-depth mapping of configurations and discovered assets provides an instant, customizable view into multiple compliance frameworks like GDPR, HIPAA, or PCI DSS.
- Translating Security Posture to Compliance: Stop manually correlating technical checks with legal jargon. Strobes automatically presents actionable reports tailored to the compliance requirements of your industry.
- Proactive Compliance: Catch policy drifts and deviations before they turn into non-compliance incidents. Strobes allows you to demonstrate that continuous controls were in place to reduce potential liabilities.
Implementing Strobes for CASM Security
Implementing a robust cloud security solution like Strobes requires a strategic approach. Here’s a breakdown of the key phases involved:
Phase 1: Planning and Prioritization
The foundation of a successful Strobes implementation lies in thorough planning and prioritization. This phase involves:
- Understanding Your Environment: A comprehensive assessment of your cloud infrastructure, including cloud providers, workloads, and sensitive data.
- Identifying Critical Assets: Determining which assets are most valuable to your organization and require heightened protection.
- Defining Security Goals: Clearly outlining your desired security outcomes, such as compliance adherence or risk reduction.
- Tailoring Strobes Configuration: Configuring Strobes to align with your specific security requirements and priorities.
- Resource Allocation: Determining the necessary human and technological resources for a successful implementation.
Phase 2: Monitoring and Remediation
Once Strobes is deployed, the focus shifts to continuous monitoring and effective remediation:
- Real-Time Visibility: Leveraging Strobes’ comprehensive visibility to identify potential vulnerabilities and threats.
- Prioritized Alerts: Acting on high-priority alerts to mitigate risks promptly.
- Remediation Workflow: Establishing efficient processes for addressing identified issues, including integration with ticketing systems.
- Incident Response: Preparing for and responding to security incidents effectively.
Phase 3: Ongoing Tuning and Training
To maximize the value of Strobes, continuous optimization and user education are essential:
- Regular Reviews: Conducting periodic assessments of Strobes’ performance and identifying areas for improvement.
- Policy Updates: Adjusting security policies as needed to reflect evolving threats and organizational changes.
- User Training: Providing ongoing training to empower users to effectively utilize Strobes and understand its value.
How Strobes Aligns with Other Cloud Solutions?
| Competitor | Strengths | Alignment with Strobes |
| Wiz | Deep container monitoring, vulnerability discovery, agentless cloud scanning | Similar to Strobes in vulnerability detection, but Strobes offers broader asset visibility. |
| Lacework | Data correlation for cloud, containers, and applications. Strong on workload protection alongside CASM/CSPM features. | Similar to Strobes in offering a unified platform, but Strobes focuses on actionable insights and risk prioritization. |
| Palo Alto Networks Prisma Cloud | Wide range of modules covering CASM, CSPM, workload security, and more. | Appeals to existing Palo Alto customers. Strobes offers a more streamlined platform focused on core CASM/CSPM/RBVM. |
| Orca Security | Side-scanning agentless technology provides deep asset visibility and vulnerability detection. Emphasizes risk prioritization. | Similar to Strobes in risk prioritization, but Strobes offers a unified platform and actionable remediation recommendations. |
| Trend Micro Cloud One | Extensive suite offering workload security, network protection, and posture management. | For organizations seeking a broader security platform. Strobes focuses on deep cloud security with a unified CASM/CSPM approach. |
Related Reads:
Use Case: Rapid Identification and Escalation of a Critical Threat by Strobes ASM
Open Source Security: How Strobes Integrates Security into Your Dev Workflow
Cloud Security Essentials: Protecting your Data in Cloud Environments
Solution: Cloud Security
Stop third-party threats and protect your cloud environment!