Security challenges for organizations have become increasingly complex. We often find ourselves contending with sophisticated threats that demand more than just reacting to incidents as they occur. There’s a clear and pressing need to move towards a more proactive stance, one that provides comprehensive insight and precise control over where vulnerabilities might exist.
Within this critical context, two methodologies have emerged as central to achieving this proactive security: Continuous Threat Exposure Management (CTEM) and Attack Surface Management (ASM).
This article aims to thoroughly explain CTEM and ASM, clarifying their distinct purposes, how they operate, and the strategic advantages each offers. Our goal is to provide technology and security leaders with the clarity needed to make informed decisions about implementing these approaches, whether individually or in combination, to genuinely strengthen their organization’s proactive security capabilities.
What Is CTEM
Continuous Threat Exposure Management (CTEM) represents a structured, cyclical methodology designed to systematically identify, prioritize, validate, and remediate security exposures across an enterprise. Its core principle lies in moving beyond theoretical vulnerability assessment to empirically proving the exploitability and business impact of identified weaknesses.
CTEM focuses on simulating real-world attack scenarios to gain a precise understanding of how vulnerabilities, misconfigurations, and control gaps could be leveraged by malicious actors. This approach provides a data-driven view of an organization’s actual threat exposure, enabling more effective risk mitigation.
Benefits of CTEM
CTEM offers several significant advantages for organizations striving for robust security:
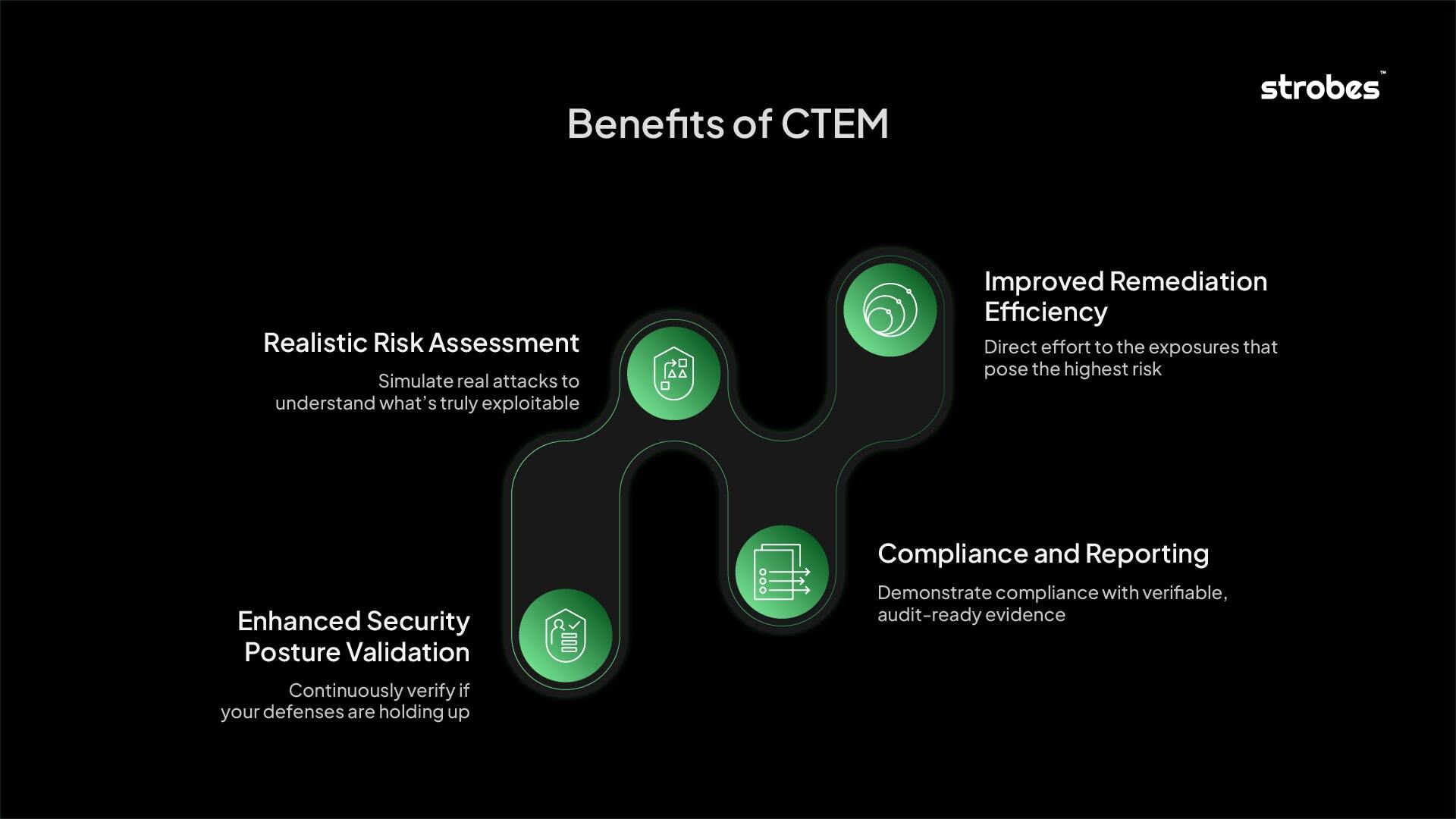
- Realistic Risk Assessment: By simulating actual attacks, CTEM provides a more accurate and realistic understanding of an organization’s true security exposure, moving beyond theoretical vulnerability counts. This enables leaders to make more informed risk management decisions.
- Improved Remediation Efficiency: The empirical validation of exposures allows security teams to prioritize remediation efforts on weaknesses that genuinely pose the highest risk, thereby optimizing resource allocation and accelerating the reduction of critical exposures.
- Enhanced Security Posture Validation: CTEM provides continuous validation of existing security controls and investments. It answers the critical question: “Are our existing security measures truly effective against current threats?”
- Compliance and Reporting: The continuous, evidence-based nature of CTEM provides robust data for demonstrating compliance with various regulatory requirements and industry standards, facilitating comprehensive reporting to stakeholders.
What Is ASM
Attack Surface Management (ASM) is the systematic and continuous process of discovering, inventorying, classifying, and monitoring all of an organization’s internet-facing and internal assets that could potentially serve as entry points for malicious actors.
The primary focus of ASM is to gain comprehensive visibility into every component of an organization’s operational footprint, including those that are unknown or unmanaged (often referred to as “shadow IT”). ASM aims to eliminate blind spots by providing a complete, up-to-date map of all potential avenues an attacker could exploit to gain unauthorized access or cause disruption.
Benefits of CTEM
Implementing a robust ASM program yields several critical benefits:
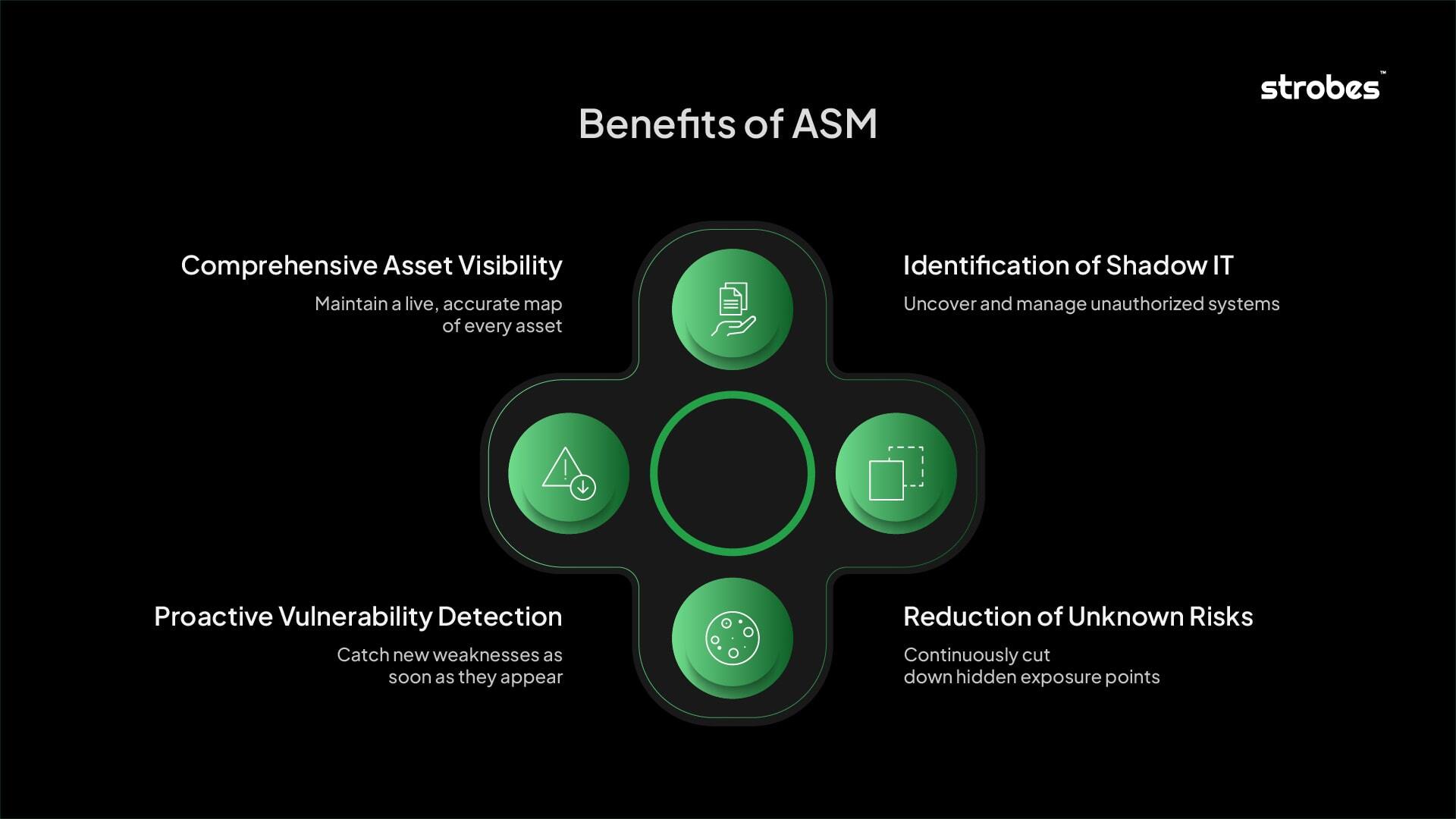
- Comprehensive Asset Visibility: ASM provides an exhaustive and up-to-date inventory of all organizational assets, eliminating blind spots and ensuring that no potential entry point remains unknown. This complete picture is fundamental for any security strategy.
- Identification of Shadow IT: By actively discovering unknown or unauthorized systems and applications, ASM helps organizations bring these unmanaged risks under control, significantly reducing the likelihood of compromise through overlooked assets.
- Proactive Vulnerability Detection: Continuous monitoring allows for the early detection of new vulnerabilities and misconfigurations as they emerge, enabling proactive mitigation before they can be exploited by malicious actors.
- Reduction of Unknown Risks: By systematically mapping and monitoring the entire attack surface, ASM drastically reduces the number of unknown or unmanaged risks, thereby strengthening the overall security posture.
CTEM vs ASM
The CTEM approach adds context that traditional tools miss. It helps teams avoid chasing hypothetical risks and instead focus on what’s verifiably dangerous. It also aligns remediation efforts with business goals, making security more measurable and efficient.
| Aspect | CTEM | ASM |
| Primary Objective | Maintain a continuous, validated, and prioritized understanding of all exploitable exposures, aligned with business risk. | Maintain continuous visibility into all known and unknown assets and their exposures, primarily external-facing. |
| Scope | Full‑spectrum coverage: external, internal, cloud, applications, endpoints, supply chain, identities, and configurations. | Primarily external-facing assets (domains, IPs, APIs, cloud resources), with some solutions expanding to internal assets. |
| Key Capabilities | 1. Targeted scoping of focus areas 2. Continuous discovery of assets and vulnerabilities 3. Exploit validation (manual or automated testing) 4. Risk-based prioritization 5. Remediation coordination & tracking 6. Measurement of risk reduction over time | 1. Continuous discovery of internet-facing assets 2. Asset inventory creation & maintenance 3. Exposure detection (open ports, weak services, misconfigurations) 4. Change detection & alerting 5. Optional external threat intelligence feeds |
| Methodology | 5-phase continuous cycle: 1. Scoping – Decide which parts of the environment to assess in each cycle. 2. Discovery – Find assets, vulnerabilities, misconfigurations, identity risks. 3. Validation – Test if vulnerabilities can actually be exploited. 4. Prioritization – Rank based on exploitability and business impact. 5. Mobilization – Assign fixes, track closure, and measure results. | Continuous loop: 1. Discovery – Identify assets exposed to the internet. 2. Inventory – Maintain an accurate, updated list. 3. Exposure Detection – Flag risky services or configurations. 4. Alerting – Notify when changes or exposures occur. |
| Risk Context | Aligns exposures with business-critical processes and compliance requirements. | Focuses more on asset and exposure presence than on their operational impact. |
| Validation of Risk | Actively validates exploitability through automated testing, attack simulations, or pentesting. | Typically detects exposures but doesn’t confirm exploitability. |
| Prioritization | Prioritizes based on exploitability, potential impact, regulatory risk, and remediation cost. | Often prioritizes based on severity ratings or exposure type without deep business alignment. |
| Integration Points | Vulnerability management, pentesting platforms, threat intelligence, remediation workflows, ticketing systems. | Threat intelligence, vulnerability scanners, and external monitoring tools. |
| Primary Consumers | Security operations teams, vulnerability management teams, risk management, and compliance. | Security operations teams, asset management teams, IT operations. |
| Outcome / Deliverable | 1. Risk-prioritized exposure list 2. Exploitation evidence 3. Remediation roadmap 4. Risk reduction metrics over time | 1. Asset inventory 2. Exposure alerts 3. Asset change history |
When Should You Choose ASM?
ASM is ideal as a first step in maturing your proactive security efforts.
It’s especially useful when:
- You’re starting from scratch and need a clear inventory of external assets.
- You’re trying to identify misconfigured cloud buckets, forgotten subdomains, or unmanaged services.
- You need visibility across subsidiaries, acquired entities, or distributed teams.
It helps build a baseline. Without that, it’s hard to do anything else effectively.
When Does CTEM Make More Sense?
CTEM becomes critical when visibility alone isn’t enough. If your team is already receiving a flood of alerts from scanners and tools, CTEM brings clarity. It helps answer:
- Which exposures are worth addressing now?
- What threats are real and exploitable?
- How can we prove the impact to the business?
It’s especially effective in environments with:
- Multiple cloud platforms
- CI/CD pipelines
- Complex third-party dependencies
- A need to tie risk reduction to business outcomes
CTEM ensures security isn’t just detecting issues it’s solving the right ones.
How CTEM and ASM Can Work Together
This isn’t an either/or decision. In fact, CTEM often begins with ASM.
Here’s how the flow can look:
- ASM scans your external attack surface and finds an exposed S3 bucket.
- CTEM kicks in and:
- Checks if it contains sensitive data.
- Validates whether it’s publicly accessible.
- Determines if threat actors have been scanning similar buckets.
- Aligns remediation with the asset owner and criticality.
- Checks if it contains sensitive data.
The result? Instead of sending a generic “close this bucket” ticket, the security team sends a prioritized action item with full context and urgency. And remediation doesn’t stop at fixing it. Includes retesting to confirm the risk is resolved.
Conclusion:
Choosing between CTEM and ASM isn’t a question of which is better; it’s about recognizing how they complement each other. ASM ensures you have complete, continuous visibility into every asset and exposure across your environment. CTEM takes that foundation and adds the context, validation, and vulnerability prioritization needed to focus efforts on the exposures that truly matter.
On their own, each approach offers value. Together, they form a continuous cycle: discover everything, validate the real risks, fix with precision, and confirm the outcome. This shifts security from chasing alerts to running a structured, measurable program that addresses the right risks at the right time.
If your goal is to strengthen your security posture while making remediation efforts more effective, combining CTEM and ASM is a proven way forward.
Book a demo with Strobes Security to see how we bring both into one unified program, helping you turn visibility into verified, measurable risk reduction.
Frequently Answered Questions (FAQ’s)
Q.1 How does CTEM differ from ASM in practical enterprise use?
CTEM is a structured, continuous process that helps enterprises prioritize threats and align remediation with business risk, while ASM focuses on discovering external assets. Enterprises use CTEM to translate findings into measurable outcomes such as reduced mean time to remediation (MTTR) and stronger compliance posture, making it more actionable than pure discovery.
Q.2 Which organizations benefit most from adopting CTEM over ASM alone?
Large enterprises with complex IT environments see the most value from CTEM because it integrates risk scoring, compliance alignment, and remediation tracking. Mid-market organizations also benefit when they need measurable security outcomes rather than raw asset lists.
Q.3 What ROI can enterprises expect from CTEM compared to ASM?
CTEM delivers ROI by reducing time wasted on low-priority issues and ensuring resources are allocated to risks with the highest business impact. Organizations often measure improvements through faster remediation cycles, reduced audit preparation time, and better alignment with NIST and ISO frameworks. ASM on its own rarely provides these quantifiable benefits.
Q.4 Can CTEM integrate with the ASM tools already in place?
Yes. CTEM can ingest asset discovery data from ASM tools and layer prioritization, validation, and remediation planning on top. This ensures enterprises maximize existing investments while improving efficiency and reducing duplicate effort.
Q.5 How does CTEM handle zero-day vulnerabilities compared to ASM?
CTEM incorporates real-time threat intelligence and validation steps to highlight which zero-day vulnerabilities require immediate action. By aligning this intelligence with business impact, enterprises can measure reduction in exposure to zero-days as a key security metric. ASM cannot provide this prioritization.