Web applications are integral to modern business operations, facilitating customer engagement, financial transactions, and internal processes. However, their widespread use and complexity make them prime targets for cyber threats. A single vulnerability can lead to unauthorized access, data breaches, or service disruptions, jeopardizing both business continuity and user trust.
Recent statistics underscore the critical need for robust web application security:
- Prevalence of Vulnerabilities: A staggering 98% of web applications were found to have vulnerabilities that could lead to malware infections, unauthorized redirections, and other malicious activities.
- Incident Resolution Time: Approximately 70% of critical security incidents take longer than 12 hours to resolve, highlighting challenges in timely threat mitigation.
- API Security Concerns: Attacks targeting Application Programming Interfaces (APIs) have more than doubled, with 29% of web attacks now directed at APIs, reflecting a significant shift in attack vectors.
- Application Security Market Growth: The application security market is projected to generate approximately $6.97 billion in 2024, indicating increased investment in security measures.
Penetration testing plays a pivotal role in identifying and addressing these vulnerabilities. By simulating real-world attack scenarios, it helps uncover weaknesses in authentication mechanisms, data handling, and overall application security. Regular assessments enable organizations to proactively address vulnerabilities, thereby reducing potential risks.
This checklist aims to guide security teams through a structured evaluation of web applications. Covering essential steps from initial reconnaissance to post-test remediation, each stage is designed to assess risks effectively and enhance application resilience.
Web Application Pentesting Checklist
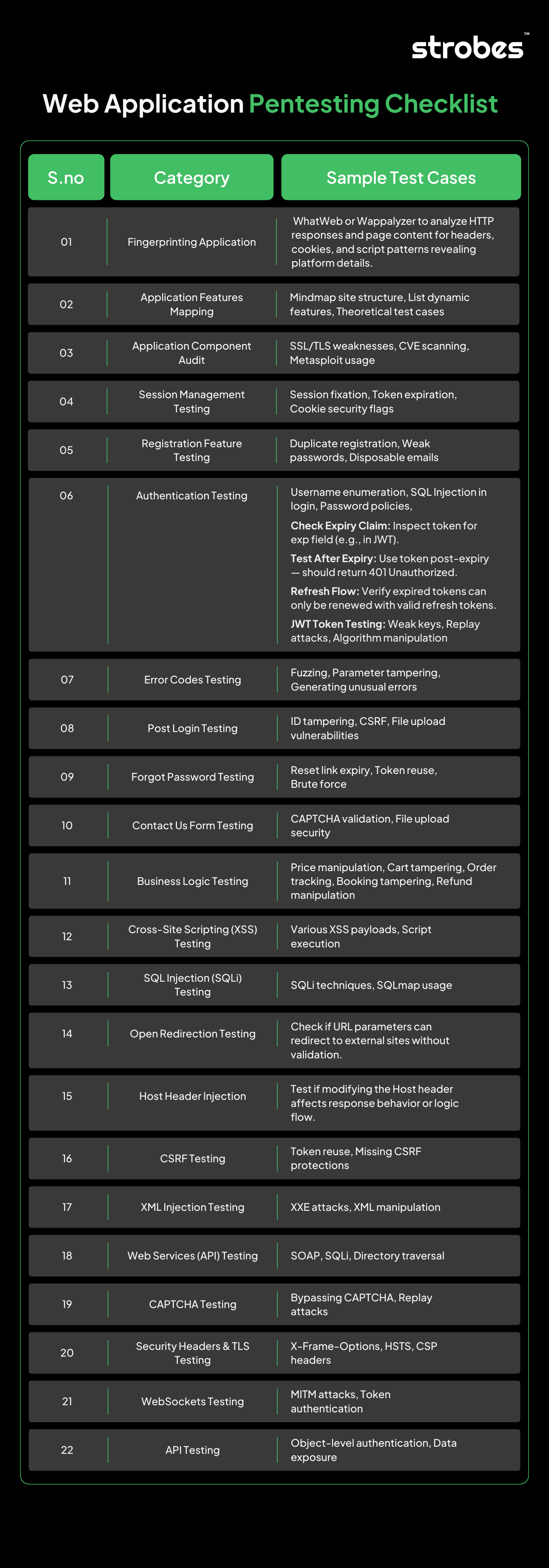
This guide provides a structured Web Application Pentesting Checklist to help security teams conduct thorough penetration tests and enhance application security.
1. Pre-Engagement Preparation
Before starting a web application penetration test, thorough planning is crucial. The pre-engagement phase ensures the testing process is structured, compliant, and aligned with business objectives. This stage involves defining the scope, gathering documentation, selecting methodologies, and obtaining the necessary permissions.
A. Define Scope
Clearly defining the scope is the foundation of any penetration test. It sets boundaries, identifies critical assets, and prevents unauthorized access to non-target systems.
- Application Components: List all components in scope, including web pages, databases, backend services, and authentication mechanisms.
- APIs: Specify internal and external APIs, authentication mechanisms (OAuth, JWT, API keys), and endpoints that require testing.
- Third-Party Integrations: Identify external services, plugins, or libraries that interact with the application. Ensure vendors are informed if their services are tested.
Rules of Engagement – Web Application Penetration Testing
Develop a rules of engagement (RoE) as agreed upon with the testing party. Here’s a sample given below that describes what the RoE shall encompass:
Category | Do’s | Don’ts |
| Scope | Test only assets explicitly listed in the scope. | Don’t test out-of-scope domains, subdomains, IPs, or third-party assets. |
| Testing Schedule | Conduct testing during approved hours (e.g., 9 AM–6 PM IST). | Don’t test outside agreed timeframes without prior approval. |
| Authentication | Use provided credentials to test authenticated areas. | Don’t brute-force logins or bypass authentication unless approved. |
| Exploitation | Use safe, non-destructive payloads to demonstrate vulnerabilities. | Don’t perform Denial of Service (DoS) or delete/modify data. |
| Tool Usage | Use industry-standard and client-approved tools. | Don’t use unvetted or high-impact automation without informing the client. |
| Data Handling | Treat all accessed data as confidential and use encrypted storage. | Don’t disclose or share data or findings with unauthorized parties. |
| Reporting | Report critical vulnerabilities immediately to the client POC. | Don’t delay notification of high-risk findings. |
| Social Engineering | Not allowed unless specifically scoped. | Don’t perform phishing, vishing, or impersonation. |
| Fuzzing & Scanning | Use controlled, throttled scanning techniques. | Don’t run high-frequency or unthrottled automated scans. |
| Pivoting & Lateral Moves | Stay within the defined testing scope and asset list. | Don’t attempt to access internal or adjacent systems unless authorized. |
| Communication | Maintain daily or regular updates with the client team. | Don’t go silent or withhold test progress and roadblocks. |
| Deliverables | Submit a detailed report with PoCs, screenshots, and remediation advice. | Don’t submit vague or incomplete reports. |
B. Gather Relevant Documentation
Understanding the application’s architecture, security policies, and compliance requirements streamlines the testing process and helps identify potential vulnerabilities. Key documentation includes:
- Application Architecture: Network diagrams, data flow models, and component interaction details help testers understand the infrastructure.
- Evaluate Security Mechanisms: Information on authentication, authorization, encryption, and data storage policies guides the testing approach.
- Compliance Requirements: Regulations such as GDPR, HIPAA, PCI-DSS, and SOC 2 define security benchmarks and dictate necessary controls.
C. Establish Testing Methodologies
Choosing the right penetration testing methodology depends on the depth of assessment required. The three primary methodologies include:
- Black-Box Testing: Testers have no prior knowledge of the application’s architecture or source code. This simulates a real-world attacker scenario.
- Grey-Box Testing: Testers have limited knowledge, such as user credentials or API documentation, allowing for more targeted testing.
- White-Box Testing: Testers have full access to source code, configurations, and application architecture, enabling in-depth security analysis.
Selecting the appropriate methodology depends on the test objectives, risk tolerance, and compliance requirements.
Standards to Follow in Web App Pentesting
When building a web application pentesting checklist, these are the key standards you should know:
- OWASP Top 10 – The must-follow list. Covers common web risks like Broken Access Control, XSS, Injection, and Insecure Design.
- SANS/CWE Top 25 – Focuses on dangerous coding flaws like buffer overflows, input validation issues, and XSS.
- NIST SP 800-115 – A step-by-step guide for planning and running technical security tests. Ideal for formal testing.
- OWASP ASVS – A detailed checklist for app security at different levels—basic, standard, and advanced.
- PCI-DSS – A must if you’re testing payment-related apps. Heavy on encryption, access control, and secure coding.
- ISO 27001/27002 – High-level controls. Useful if your client needs to meet compliance goals.
2. Reconnaissance and Information Gathering
Effective web application penetration testing begins with a thorough reconnaissance phase. This stage is critical for identifying potential entry points and assessing the overall security posture before attempting any active tests. It involves both passive and active information-gathering techniques to collect relevant data about the target application.
A. Passive Information Gathering
Passive reconnaissance involves collecting data without directly interacting with the target system. The goal is to gather as much intelligence as possible while avoiding detection. Methods include:
- WHOIS Lookup: Checking domain registration details to identify ownership, administrative contacts, and nameservers.
- DNS Records Inspection: Analyzing DNS records (A, MX, TXT, SPF, and CNAME) to uncover subdomains, mail servers, and security configurations.
- Metadata Extraction: Examining publicly available documents (PDFs, images, and office files) for metadata that may reveal usernames, software versions, or internal network structures.
- Social Media and Public Forums: Attackers often leverage fake or misleading profile picture identities to impersonate employees and gain trust during phishing or reconnaissance efforts. Reviewing discussions, employee profiles, and company announcements that might inadvertently expose sensitive details.
B. Active Information Gathering
Active reconnaissance involves interacting directly with the target application to extract more detailed information. This method provides deeper insights but may trigger security alerts. Techniques include:
- Subdomain Enumeration: Identifying subdomains using tools like Sublist3r, Amass, or online services such as crt.sh. This helps map the attack surface beyond the primary domain.
- Technology Stack Identification: Detecting the web server, content management system (CMS), programming languages, and frameworks in use. Tools like Wappalyzer and WhatWeb can automate this process.
- API Endpoint Discovery: Reviewing API documentation, inspecting web requests via browser developer tools, and using tools like Postman or Burp Suite to analyze API calls.
- Port Scanning and Service Enumeration: Running targeted scans with Nmap or Masscan to detect open ports and associated services while minimizing intrusion.
3. Authentication & Authorization Testing
Ensuring that authentication and authorization mechanisms are secure is a critical aspect of web application penetration testing. Weak implementations in these areas can lead to unauthorized access, privilege escalation, and data breaches.
A. Testing Weak Passwords and Default Credentials
One of the first steps is checking for weak passwords and default credentials. Many applications still allow common or easily guessable passwords, increasing the risk of unauthorized access. Attackers often exploit this by using credential stuffing or brute-force techniques. Testing should include:
- Attempting login with default credentials (e.g., admin/admin, user/password).
- Running automated password audits to identify weak or commonly used passwords.
- Checking for rate-limiting mechanisms to prevent excessive login attempts.
Enforcing strong password policies, including minimum length, complexity requirements, and account lockout mechanisms, can significantly reduce risks.
B. Checking for Multi-Factor Authentication (MFA) Implementation
MFA is a crucial layer of security that reduces reliance on passwords alone. Testing should include:
- Evaluating whether MFA is enforced for critical actions or high-privilege accounts.
- Assessing the strength of second-factor authentication methods (e.g., SMS-based MFA is weaker than app-based or hardware tokens).
- Checking for MFA bypass techniques, such as response replay attacks or insecure token storage.
A properly configured MFA system adds an extra step for attackers, making unauthorized access significantly more challenging.
C. Assessing Session Management
Poor session management can expose users to risks such as session hijacking or fixation attacks. Key areas to evaluate include:
- Token Expiration: Ensuring that sessions expire after a reasonable period of inactivity and that tokens are invalidated upon logout.
- Session Fixation: Checking if an attacker can force a user to use a predetermined session ID. Secure applications generate new session identifiers after authentication.
- Session Storage & Transmission: Verifying that session tokens are securely stored (e.g., HttpOnly and Secure flags set on cookies) and transmitted over encrypted channels.
Effective session management protects user authentication states from being stolen or misused.
D. Verifying Access Control Mechanisms
Access control flaws are among the most exploited vulnerabilities in web applications. Common issues include broken access control and privilege escalation. Testing should focus on:
- Horizontal Access Control: Ensuring users cannot access data or actions belonging to other users (e.g., modifying another user’s account details by changing the user ID in a request).
- Vertical Access Control: Checking if lower-privileged users can perform administrative functions by manipulating requests.
- Direct Object References: Identifying whether sensitive resources (e.g., files, database records) can be accessed directly without proper validation.
E. Cross-Site Request Forgery (CSRF) Detection
CSRF attacks trick users into performing unintended actions on a website where they are authenticated. This can lead to unauthorized transactions or data modifications.
- Check if forms have CSRF tokens: All state-changing requests should include a unique token to validate the user’s intent.
- Verify HTTP request methods: Ensure critical operations use POST instead of GET to avoid unintended executions via URLs.
- Test cookie-based authentication mechanisms: If session cookies are automatically sent with requests, CSRF vulnerabilities can be exploited.
- Use the SameSite cookie attribute: Setting cookies to SameSite=Strict or SameSite=Lax can prevent them from being sent with cross-origin requests.
- Monitor for open redirects: Attackers can exploit open redirections to execute CSRF attacks by forcing users to make unintended requests.
Mitigation Measures:
- Use CSRF tokens for state-changing actions.
- Enforce SameSite cookie attributes to restrict unauthorized cross-origin requests.
- Require multi-factor authentication for sensitive operations.
F. JWT Attacks (JSON Web Tokens)
JWTs (JSON Web Tokens) are used to prove you’re logged in. But if they’re misused? Attackers can slip right through. Here’s how:
- Weak Secrets: If the signing key is something like 123456, an attacker can guess it and create fake tokens.
- “None” Algorithm Trick: Some apps accept tokens with “alg”: “none”, which skips signature checks entirely. No validation = full access.
- Role Tampering: Change “role”: “user” to “admin” inside the token. If the server doesn’t validate properly, boom—instant admin.
- No Expiry: Tokens that never expire give attackers more time to use stolen ones.
- Info Exposure: JWTs aren’t encrypted. Anyone can decode and read what’s inside. Don’t put sensitive stuff in there.
G. Privilege Escalation Testing
Privilege escalation testing is all about checking if a regular user can perform actions meant for admins or higher-privileged users. For example, a tester might try visiting admin-only pages, changing their role in a request from “user” to “admin,” or editing another user’s data just by tweaking a user ID. If the app doesn’t block these actions, it’s a serious security issue.
These tests help find places where the app trusts user input too much or forgets to verify permissions on the server side. To prevent this, apps should always check roles on the backend, never trust data from the user, and make sure sensitive features are locked down tight.
How to Prevent It
- Always check user roles on the server
- Don’t trust info sent from the user
- Lock down admin features
H. IDOR Testing
IDOR stands for Insecure Direct Object Reference. It happens when an app lets users access data just by changing an ID in the URL or request without checking if they’re allowed to. For example, if you’re logged in and visit /invoice/1001, and then change it to /invoice/1002 and see someone else’s invoice, that’s an IDOR. Testers look for these by changing things like user IDs, order numbers, or file names to see if the app exposes unauthorized data. To prevent this, apps need to check:
“Does this user actually own this data?” every single time. It’s a simple mistake, but it can lead to big leaks.
I. OAuth Testing
OAuth lets you log in with services like Google or Facebook. But it adds complexity.
What pentesters check:
- Redirect URI manipulation: Can you change where OAuth sends tokens?
- Token leakage: Are access tokens exposed in URLs or logs?
- Poor scope control: Did the app request way more access than needed?
- CSRF with OAuth flows: Can you trick someone into granting access?
4. Input Validation & Injection Testing
Applications that do not properly validate user input create opportunities for attackers to manipulate system behavior. The following assessments help identify potential weak points in handling input.
A. SQL Injection (SQLi) Testing
SQL Injection occurs when an application allows untrusted input to be executed as part of a database query. This can lead to unauthorized access, data modification, or even database destruction.
- Test for input validation flaws: Try injecting ‘ OR ‘1’=’1 or UNION SELECT statements to see if the application returns unexpected data.
- Check for error-based and blind SQLi: Applications sometimes expose database errors that reveal vulnerabilities. Blind SQLi requires time-based or boolean-based exploitation techniques.
- Use automated tools: SQLMap and Burp Suite can help detect SQLi vulnerabilities quickly.
- Ensure proper database permissions: Applications should only have the minimum privileges required for their functionality.
- Disable verbose error messages: Generic error messages help prevent attackers from gathering intelligence about the database structure.
Mitigation Measures:
- Implement parameterized queries and stored procedures.
- Use proper input validation and allow only expected characters.
- Restrict database permissions to prevent unauthorized access.
B. Cross-Site Scripting (XSS) Assessment
XSS vulnerabilities allow attackers to inject malicious scripts into web pages viewed by users. This can lead to session hijacking, defacement, and data theft.
- Test for reflected XSS: Inject <script>alert(‘XSS’)</script> into input fields and check if it executes.
- Look for stored XSS: Verify if user-generated content is stored in the database and later rendered without sanitization.
- Assess DOM-based XSS risks: Examine how JavaScript processes user inputs within the Document Object Model.
- Use security headers: Implement X-XSS-Protection, Content Security Policy (CSP), and HttpOnly flags for cookies.
- Escape HTML output: Encode dynamic content using functions like htmlspecialchars() in PHP or equivalent methods in other frameworks.
Mitigation Measures:
- Implement proper output encoding (e.g., HTML entity encoding).
- Restrict the use of innerHTML and document.write in JavaScript.
- Enable Content Security Policy (CSP) to limit script execution sources.
C. Server-Side Request Forgery (SSRF) Checks
SSRF allows attackers to manipulate server-side requests, potentially accessing internal resources or performing unauthorized actions.
- Attempt internal network access: Check if the application allows requests to http://localhost or private IP ranges like 10.0.0.1.
- Test for cloud metadata exposure: Try requesting http://169.254.169.254/latest/meta-data/ to extract sensitive instance data.
- Restrict outbound requests: Applications should only be allowed to fetch necessary resources, preventing unauthorized internal access.
- Use allowlists for external requests: If the application needs to connect to external APIs, restrict allowed domains to a predefined list.
- Sanitize user-supplied URLs: Block redirects to internal resources and validate input against expected formats.
Mitigation Measures:
- Restrict outbound requests to trusted destinations.
- Validate and sanitize user-supplied URLs.
- Implement network segmentation to prevent unauthorized internal access.
D. Command Injection & XML External Entity (XXE) Attacks
These vulnerabilities allow attackers to execute system commands or read sensitive files through improperly handled input.
Command Injection
- Test with shell commands: Inject commands like ; ls -la, | whoami, or & cat /etc/passwd to check if the server executes them.
- Disable unnecessary system calls: If possible, avoid using functions like system(), exec(), or eval().
- Run applications with restricted privileges: Ensure that the web application runs under a non-privileged user.
- Use secure coding practices: Implement frameworks that sanitize input before passing it to system commands.
XML External Entity (XXE) Attacks
- Disable external entity parsing: Configure XML parsers to prevent processing external DTDs and entities.
- Check for XXE payload execution: Inject payloads such as <!DOCTYPE foo [ <!ENTITY xxe SYSTEM “file:///etc/passwd”> ]> and see if sensitive files are exposed.
- Restrict XML parsers to allow only necessary features: Many modern parsers offer secure modes that block external entity resolution by default.
- Use JSON instead of XML when possible: JSON-based APIs are less susceptible to XXE attacks.
Mitigation Measures:
- Disable dangerous system calls in application code.
- Use secure parsing libraries that disable external entity resolution.
- Implement input validation and restrict special characters in user input.
Trusted by leading enterprises like, GHX, Zoho, Darwinbox, Tricenties, and SHL
Strobes helped organizations continuously manage threats, reduce vulnerabilities, and stay compliant, powered by AI-driven security expertise.
5. Security Misconfigurations & Sensitive Data Exposure
Security misconfigurations and exposure of sensitive data present significant risks to web applications. Attackers often exploit these weaknesses to gain unauthorized access or extract confidential information. A structured approach is essential to identify gaps and apply corrective measures.
A. Check for Exposed Admin Panels, Directories, and Files
Admin interfaces, directories, and unprotected files can provide attackers with a direct entry point into a system. Some common risks include:
- Publicly accessible admin panels (e.g., /admin, /wp-admin, /phpmyadmin) with weak or no authentication.
- Unprotected backup files (e.g., .git, .env, config.old, db_backup.sql) containing credentials or system configurations.
- Enabled directory listing, allowing access to critical files.
- Default or easily guessable credentials on login pages.
How to Test:
- Use tools such as Dirb, Gobuster, or FFUF to identify hidden directories and files.
- Scan for publicly accessible .git repositories and environment files (.env, config.php).
- Perform login attempts using common username-password combinations.
How to Fix:
- Restrict admin panel access using IP allowlisting, VPN, or multi-factor authentication.
- Disable directory listing and remove unnecessary files from public directories.
- Change default credentials and enforce strong authentication policies.
B. Review HTTP Headers (HSTS, CSP, X-Frame-Options)
Security headers play a crucial role in preventing attacks such as clickjacking, cross-site scripting (XSS), and man-in-the-middle attacks. Missing or misconfigured headers weaken application security.
Important Headers to Check:
- HTTP Strict Transport Security (HSTS) – Ensures connections use HTTPS to prevent protocol downgrade attacks.
- Content Security Policy (CSP) – Controls which scripts, styles, and other resources can be loaded to reduce the risk of XSS.
- X-Frame-Options – Prevents clickjacking by restricting iframe embedding.
- X-Content-Type-Options – Stops browsers from interpreting files as different MIME types to avoid attacks.
- Referrer-Policy – Limits referrer data exposure to prevent information leakage.
How to Test:
- Use Burp Suite, OWASP ZAP, or securityheaders.com to analyze HTTP response headers.
- Manually inspect response headers using browser developer tools.
Also Read: Understanding the OWASP Top 10 Application Vulnerabilities
How to Fix:
- Configure web servers (Apache, Nginx) or frameworks to apply security headers correctly.
- Set HSTS with max-age=31536000; includeSubDomains; preload.
- Implement a strict CSP policy that avoids unsafe-inline for script execution.
C. Identify Default or Misconfigured Security Settings
Applications and frameworks often ship with default settings that may expose vulnerabilities if left unchanged.
Common Issues:
- Default configurations in use (e.g., generic error pages exposing stack traces, default admin accounts).
- Overly permissive CORS settings, allowing unrestricted cross-origin access.
- Excessive user permissions, giving non-administrators unnecessary access.
- Unsecured API endpoints, permitting access without proper authentication.
How to Test:
- Review publicly available files (robots.txt, .well-known/, API documentation).
- Inspect API endpoints using Postman, Burp Suite, or jwt.io for token validation.
- Analyze application configurations to identify debug settings (Django Debug=True, Spring Boot Actuator endpoints).
How to Fix:
- Disable debugging and detailed error messages in production environments.
- Implement strict access control policies based on user roles.
- Restrict CORS settings to trusted domains and avoid Access-Control-Allow-Origin: *.
D. Inspect Data Transmission Security (TLS Encryption, Mixed Content Issues)
Weak encryption configurations expose data to eavesdropping, session hijacking, and interception attacks.
Common Issues:
- Use of outdated TLS versions (e.g., TLS 1.0, 1.1) or weak cipher suites.
- Expired or self-signed SSL certificates, leading to trust warnings.
- Mixed content problems, where HTTPS pages load non-secure HTTP resources.
- Session cookies missing security attributes, increasing exposure to hijacking.
How to Test:
- Run an SSL Labs Test (ssllabs.com/ssltest/) to check TLS strength.
- Use browser developer tools to detect mixed content warnings.
- Examine cookie attributes (Secure, HttpOnly, SameSite=Strict) to ensure they meet security best practices.
How to Fix:
- Enforce TLS 1.2 or higher and disable older protocols.
- Redirect all HTTP traffic to HTTPS with proper server-side rules.
- Set secure attributes on session cookies to prevent unauthorized access.
6. API Security Testing
APIs are integral to web applications, enabling seamless data exchange and system integrations. However, their accessibility also makes them a frequent target for
cyber threats. Ensuring API security is a critical part of web application penetration testing. Here’s how to approach it effectively:
A. Assess Authentication Mechanisms
Authentication verifies the identity of users or systems interacting with an API. A thorough evaluation should include:
- API Keys: Check if API keys are properly secured and not exposed in URLs, headers, or responses. Ensure they have limited scope and expiration policies.
- OAuth & JWT Validation: Inspect the implementation of OAuth and JSON Web Tokens (JWT). Verify that tokens are securely stored, signed correctly, and have appropriate expiration settings. Weak token management can lead to unauthorized access.
- Session Management: Ensure that session tokens are invalidated after logout and that refresh tokens follow security best practices.
B. Look for Excessive Data Exposure in API Responses
APIs often process and return large amounts of data. Attackers may exploit misconfigurations to retrieve sensitive information.
- Inspect API Responses: Ensure only necessary data is returned in API responses. Excessive exposure of sensitive information—such as user details, credentials, or internal system data—can be a major risk.
- Test for Unauthorized Data Access: Use different roles (e.g., admin, user, and guest) to determine if APIs improperly expose information to unauthorized users.
- Mask Sensitive Data: Verify that sensitive fields like credit card numbers, personally identifiable information (PII), and session identifiers are properly masked or omitted.
C. Check for Rate Limiting and Abuse Prevention
APIs should have measures to prevent excessive or automated requests that could lead to service disruptions or abuse.
- Rate Limits: Validate if rate limits are enforced by sending multiple requests in a short period. APIs should block or throttle excessive requests from a single source.
- IP-Based Restrictions: Ensure APIs can detect and restrict automated attacks, such as credential stuffing, by monitoring unusual traffic patterns.
- Token Expiry & Reuse Prevention: Confirm that access tokens have appropriate lifetimes and are not reusable indefinitely.
D. Test for Insecure API Endpoints (Broken Object-Level Authorization)
Broken Object-Level Authorization (BOLA) vulnerabilities occur when APIs expose data that users should not access. Testing should include:
- IDOR (Insecure Direct Object References): Attempt accessing objects (e.g., user profiles, orders, files) by modifying request parameters, such as changing a user ID in an API call.
- Role-Based Access Control (RBAC) Testing: Check whether lower-privileged users can perform actions reserved for higher-privileged roles.
- API Endpoint Security: Review endpoints for missing authentication checks. Unprotected endpoints may allow attackers to access or manipulate data without proper validation.
7. Business Logic Testing
Business logic vulnerabilities arise when applications fail to enforce proper workflows, leading to security gaps that attackers can exploit. These issues are often difficult to detect using automated scanners, as they stem from how the application processes user interactions rather than code-level weaknesses.
A. Identifying Bypassable Workflows
A well-structured web application follows predefined workflows for account creation, authentication, transactions, and other critical functions. However, flaws in implementation may allow attackers to bypass intended restrictions.
- Account Takeover Risks: Test for weak session management, weak password recovery mechanisms, and improper access control mechanisms that allow unauthorized users to hijack accounts.
- Price Manipulation Vulnerabilities: Assess whether product prices or transaction amounts can be altered by modifying request parameters or intercepting API calls. Applications should validate pricing data on the server side to prevent unauthorized discounts or fraudulent purchases.
- Privilege Escalation Paths: Identify scenarios where a low-privileged user can gain access to administrative features due to misconfigured role-based access controls (RBAC).
B. Detecting Race Conditions and Logic Flaws
Concurrency issues can lead to unexpected behaviors when multiple requests are processed simultaneously. Attackers exploit these flaws to gain unauthorized benefits.
- Testing for Race Conditions: Analyze scenarios where submitting multiple requests at high speed may lead to unintended outcomes, such as double withdrawals from an account, duplicate discount applications, or privilege escalation.
- Session and Token Misuse: Ensure that session tokens and authorization keys cannot be reused in ways that compromise access control mechanisms.
- Multi-Step Process Manipulation: Identify whether an application properly tracks and enforces sequential workflows, such as bypassing authentication steps by directly accessing internal endpoints.
C. Validating Financial Transaction Integrity
Financial transactions require strict validation mechanisms to prevent unauthorized modifications or fraud. Weaknesses in how transactions are processed can lead to revenue loss and compliance violations.
- Server-Side Validation: Ensure that critical transaction values, such as payment amounts and recipient details, cannot be altered on the client side before submission.
- Replay Attack Prevention: Implement nonce-based validation or transaction identifiers to prevent attackers from reusing valid requests to execute unauthorized transactions.
- Authorization and Audit Trails: Confirm that only authorized users can initiate and approve transactions, and verify that logs capture essential details for forensic analysis in case of suspicious activities.
8. Third-Party Components & Dependencies
Modern web applications rely on third-party libraries, frameworks, and plugins to speed up development and enhance functionality. While these components are convenient, they also introduce security risks. A single outdated or vulnerable dependency can become an entry point for attackers. That’s why a thorough security review of third-party integrations is critical.
A. Scan for Vulnerable Third-Party Libraries and Frameworks
Attackers often exploit known weaknesses in widely used libraries. Regularly scanning for vulnerabilities helps catch issues before they become a problem.
- Use tools like OWASP Dependency-Check, Retire.js, and Snyk to identify security flaws in libraries.
- Check vulnerability databases such as CVE (Common Vulnerabilities and Exposures) and NVD (National Vulnerability Database) for known exploits.
- Automate dependency scanning in CI/CD pipelines to detect issues early.
B. Check for Outdated Plugins, Dependencies, and Security Advisories
Outdated software is a common target for attackers. Keeping dependencies up to date minimizes risks.
- Regularly review third-party components using tools like npm audit, pip-audit, or Bundler-Audit (depending on your tech stack).
- Monitor official security advisories from vendors and open-source maintainers.
- Remove unnecessary plugins and dependencies to reduce potential attack surfaces.
C. Validate the Security of Integrations (OAuth, SSO, Payment Gateways)
External integrations, such as authentication systems and payment processors, must be configured securely to prevent data leaks and unauthorized access.
OAuth & SSO Security:
- Use short-lived access tokens and refresh tokens with proper expiration policies.
- Ensure OAuth scopes follow the principle of least privilege (grant only necessary permissions).
- Validate redirect URIs to prevent open redirect attacks.
- Enforce multi-factor authentication (MFA) wherever possible.
Payment Gateways:
- Use PCI-DSS-compliant payment services to handle transactions securely.
- Never store sensitive payment details unless absolutely required.
- Implement strict API key and webhook security to prevent unauthorized access.
9. Reporting and Remediation
Effective reporting and remediation are critical steps in web application penetration testing. A well-structured report provides valuable insights into identified security weaknesses, their potential impact, and actionable recommendations for resolution.
A. Documenting Findings with Evidence
Comprehensive documentation strengthens the credibility of security assessments. Each identified issue should be recorded with detailed evidence, including:
- Screenshots: Capturing relevant screens that demonstrate vulnerabilities in action helps developers and security teams understand the issue visually.
- Payloads Used: Recording payloads used in testing ensures that the same conditions can be recreated for verification and mitigation.
- Impact Assessment: Clearly explaining how an exploit could affect the application, data, or users helps stakeholders prioritize fixes effectively.
Detailed documentation ensures that developers and security teams have all the necessary context to address vulnerabilities efficiently.
B. Prioritizing Vulnerabilities Based on Risk Severity
Not all security weaknesses pose the same level of risk. To manage remediation efforts effectively, vulnerabilities should be categorized based on:
- Exploitability: How easily an attacker can take advantage of the issue.
- Impact: The potential consequences of exploitation, such as data exposure, service disruption, or unauthorized access.
- Business Context: How the vulnerability affects critical systems and sensitive information.
Common frameworks such as the Common Vulnerability Scoring System (CVSS) can help standardize risk assessments, ensuring that high-impact threats receive immediate attention.
C. Providing Remediation Recommendations for Developers
A penetration testing report should go beyond identifying issues—it must also offer clear guidance on how to address them. Recommendations should include:
- Code-Level Fixes: When applicable, suggest secure coding practices or provide example code snippets to mitigate the risk.
- Configuration Adjustments: Identify necessary changes in security settings, permissions, or system configurations.
- Best Practices: Encourage the adoption of secure development frameworks, regular security audits, and secure authentication mechanisms.
Providing actionable insights ensures that developers can resolve issues efficiently without unnecessary guesswork.
D. Validating Fixes Through Retesting
Once remediation efforts are completed, verification is essential to confirm that vulnerabilities have been effectively resolved. Retesting involves:
- Recreating the Initial Exploit: Using the same methods to check whether the issue persists.
- Assessing for Regression Issues: Ensuring that the applied fixes have not introduced new security concerns.
- Updating the Report: Documenting successful remediation efforts and identifying any residual risks.
Conclusion
Web application security isn’t a one-time event. It’s a constant process. One that demands regular checks, continuous threat exposure management, and fast responses to new threats.
This web application pentesting checklist? It gives you a structured way to catch security gaps, stay compliant, and reduce risk. But let’s be honest, manual testing alone won’t cut it anymore.
That’s where Strobes PTaaS steps in.
It combines the best of both worlds:
- Human-led penetration testing for depth
- An intelligent platform to track, manage, and fix vulnerabilities in real-time
No more back-and-forth over email. No more digging through PDFs for findings. With Strobes, you:
- Schedule tests on demand or continuously collaborate with ethical hackers right inside the platform
- Track progress across your entire pentest lifecycle
- Generate custom reports for devs, security teams, and execs
And the best part? Every finding is tied to business context, risk severity, and clear remediation steps. So your team can focus on what actually matters.
When you pair a strong security checklist with a platform like Strobes PTaaS, you’re not just testing. You’re building a smarter, faster, and more resilient web app security strategy.
Related Reads:
- Web Application Penetration Testing: Steps & Test Cases
- Decoding the Penetration Testing Process: A Step-by-Step Guide
- Why Penetration Testing Is Important: Enhancing Security & Reducing Cyber Risks
- Penetration Testing Explained: Safeguarding your Online Presence
- How much does a penetration test cost?
- How Strobes Penetration Testing Supports Compliance Audits and Assessments
- Solution: Pentesting as a Service
- Solution: Web Application Pentesting