In February, hearts weren’t the only things feeling vulnerable. The cyber arena saw a variety of critical exposures across multiple platforms and applications. While patching might not be as romantic as chocolates or roses, organizations and individuals alike must stay protected. Here, we highlight the most significant vulnerabilities reported during the month, emphasizing the importance of patching and mitigation strategies for organizations and individuals alike.
Fortinet FortiOS Critical Vulnerabilities
Fortinet released security updates to address critical remote code execution vulnerabilities in FortiOS, specifically CVE-2024-21762, and CVE-2024-23313. CVE-2024-21762, in particular, was noted as potentially being exploited in the wild, highlighting the urgent need for system administrators to apply necessary updates promptly.
To get details about CVE-2024-21762, visit our VI platform.
Microsoft’s February 2024 Patch Tuesday
Microsoft’s Patch Tuesday for February addressed 73 vulnerabilities, including two actively exploited zero-days, CVE-2024-21412 and CVE-2024-21351, both security feature bypass flaws. Among these vulnerabilities, CVE-2024-21413, a critical remote code execution (RCE) vulnerability in Microsoft Outlook, and CVE-2024-21380, a critical information disclosure vulnerability in Microsoft Dynamics Business Central, were particularly notable.
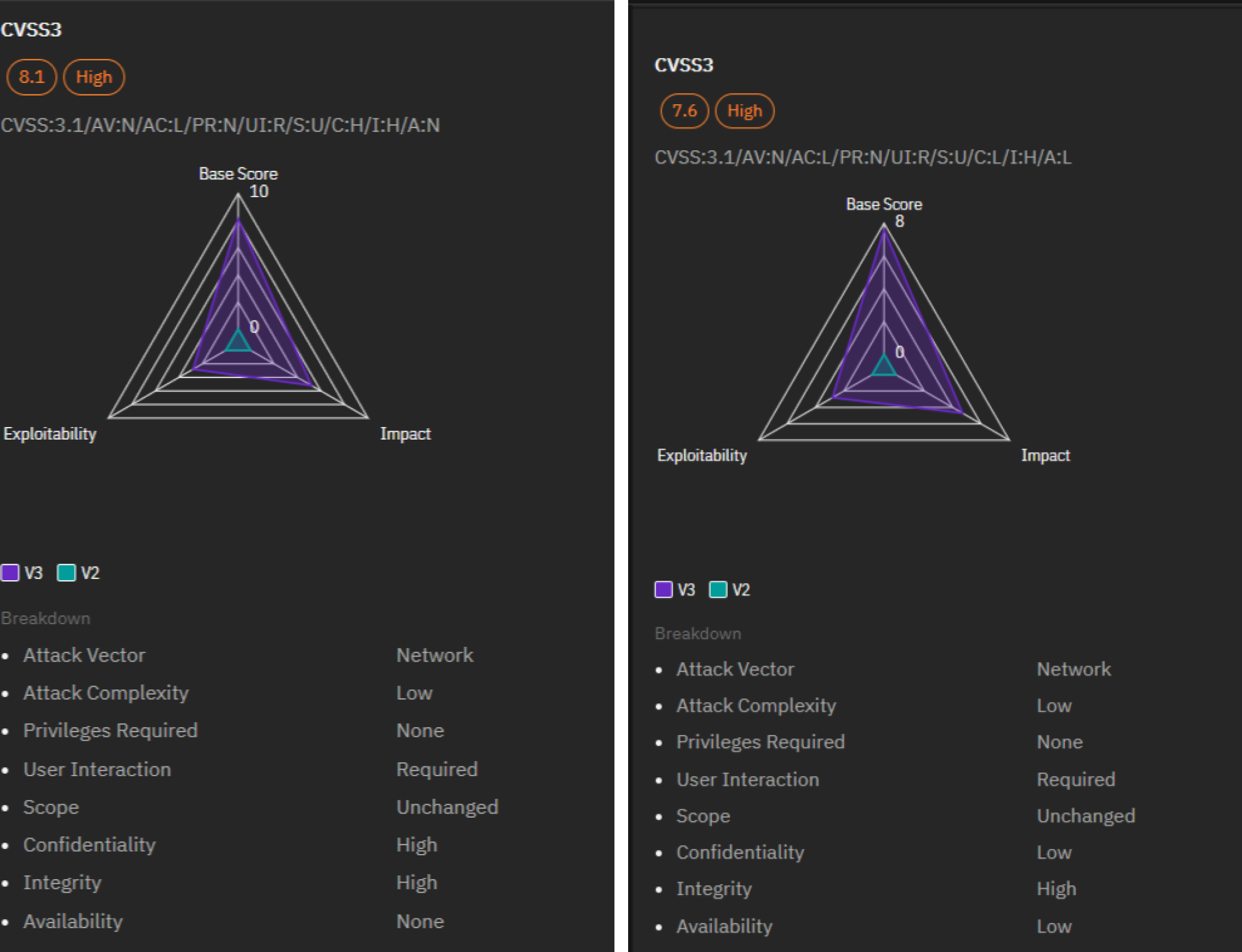
To get details about CVE-2024-21412 and CVE-2024-21351, visit our VI platform.
Android Security Bulletin
The Android Security Bulletin for February 2024 detailed security vulnerabilities affecting Android devices, with security patch levels of 2024-02-05 or later addressing these issues. The bulletin highlighted a critical security vulnerability in the System component that could lead to remote code execution without additional execution privileges.
Ivanti Connect Secure and Policy Secure Gateways
Ivanti disclosed vulnerabilities in its Connect Secure and Policy Secure Gateways, including CVE-2023-46805, CVE-2024-21887, CVE-2024-21888, and CVE-2024-21893. These vulnerabilities were subject to increased exploitation activity and the release of exploit code, emphasizing the need for vigilance and timely application of patches.
Get details of CVE-2023-46805, CVE-2024-21887, CVE-2024-21888, and CVE-2024-21893 on our VI platform.
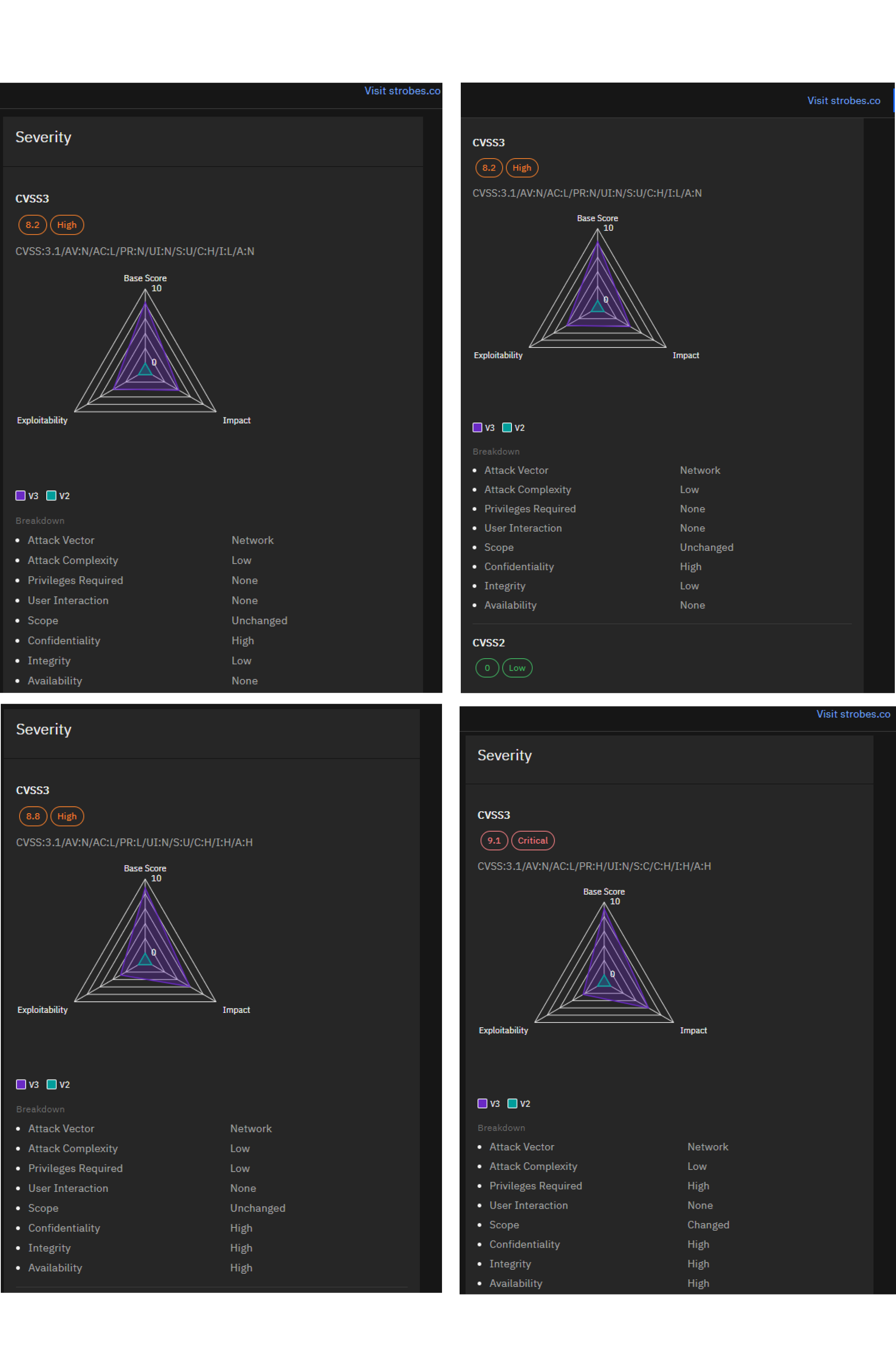
Atlassian Vulnerabilities
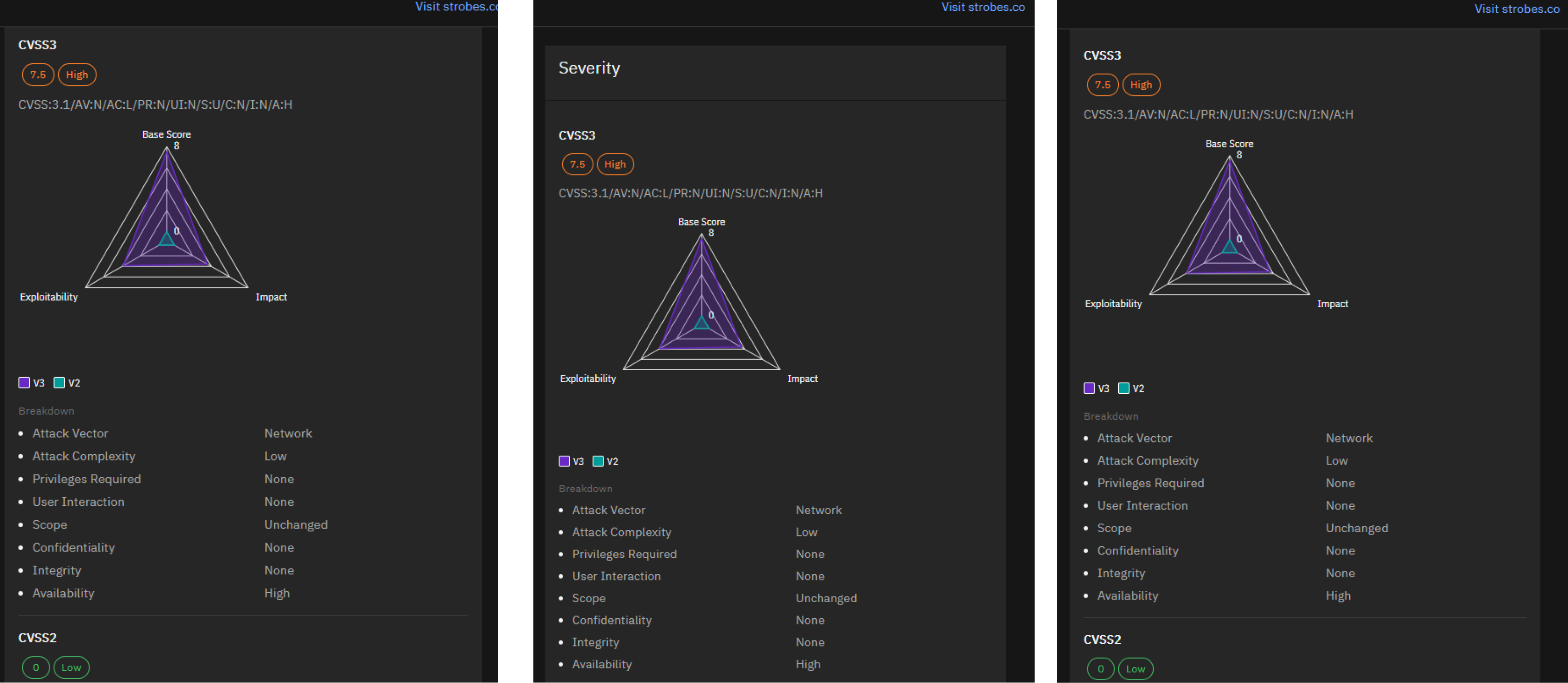
Atlassian reported multiple vulnerabilities across its products, including Confluence Data Center and Server. CVE-2024-21678, a Stored XSS vulnerability, and several Denial of Service (DoS) vulnerabilities, such as CVE-2023-5072, CVE-2023-6481, and CVE-2023-6378, were among the high-severity issues disclosed. Atlassian recommended updates to mitigate these vulnerabilities.
Get details of CVE-2023-5072, CVE-2023-6481, and CVE-2023-6378 on our VI platform.
Conclusion
February 2024 underscored the continuous challenges in cybersecurity, with critical vulnerabilities emerging across widely used platforms and applications. The disclosed vulnerabilities span a range of attack vectors, including remote code execution, information disclosure, and denial of service, underlining the importance of comprehensive vulnerability management practices. Organizations and individuals are urged to review the provided advisories and apply necessary updates to safeguard their systems against potential exploits.