Software Bill of Materials (SBOMs) is rapidly emerging as a cornerstone for robust software supply chain security. Functioning as a comprehensive inventory of all software components, dependencies, and associated metadata, SBOMs empower organizations to gain unparalleled transparency into the intricate web of elements that constitute their applications.
This newfound visibility unlocks a multitude of benefits, ranging from vulnerability management and license compliance to enhanced risk management and streamlined supply chain security.
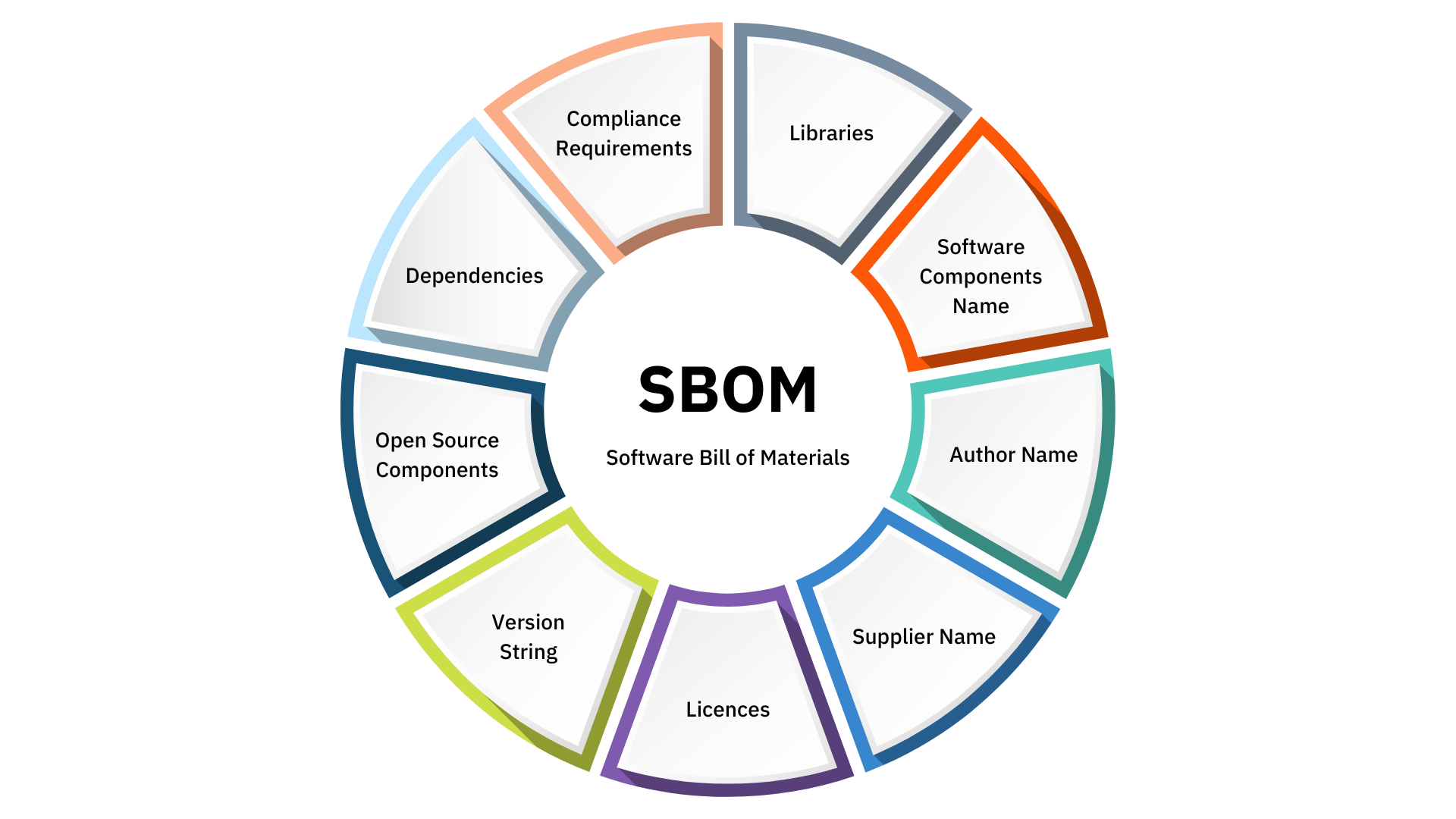
The Imperative for Software Bill of Materials (SBOMs) Adoption
Gartner predicts that by 2025, 45% of organizations worldwide will have experienced attacks on their software supply chains, a three-fold increase from 2021. The impetus behind the growing prominence of Software Bill of Materials (SBOMs) stems from the burgeoning reliance on Open Source Software (OSS) within modern software development.
While OSS offers numerous advantages in terms of cost-effectiveness, innovation, and rapid development, it also introduces inherent complexities. The intricate nesting of dependencies within software often results in a lack of comprehensive visibility into the underlying components, potentially harboring unknown vulnerabilities and license compliance issues.
Bridging the Visibility Gap with Software Bill of Materials (SBOMs)
SBOMs serve as a bridge, effectively addressing the aforementioned visibility gap. By meticulously cataloging all software components, dependencies, and associated information, they provide organizations with a clear understanding of the building blocks that constitute their software. This comprehensive picture empowers various stakeholders within the software development lifecycle to:
- Proactively identify and address vulnerabilities: By leveraging Software Composition Analysis (SCA) tools, organizations can readily scan SBOMs to pinpoint known vulnerabilities associated with specific components. This enables them to prioritize patching efforts and mitigate potential security risks before they can be exploited by malicious actors.
- Ensure license compliance: According to the OSSRA 2023 report, 31% of codebases contained open source with no license or a custom license. SBOMs provide a consolidated view of all licenses governing the various components within the software. This facilitates meticulous license compliance management, preventing inadvertent infringement and associated legal ramifications.
- Streamline risk management: SBOMs serve as a valuable asset in risk management process. By providing insights into the provenance and security posture of individual components, organizations can effectively assess and prioritize potential risks associated with their software supply chain.
- Enhance supply chain security: In the 2023 OSSRA report, 89% of codebases contained open source more than four years out-of-date. SBOMs foster transparency and collaboration throughout the software supply chain. By sharing SBOMs with vendors and partners, organizations can collectively identify and address vulnerabilities, promoting a more secure and resilient software ecosystem.
Formats of Software Bill of Materials (SBOMs)
The National Telecommunications and Information Administration (NTIA) recognizes three main acceptable standard formats for SBOMs:
- SPDX (Software Package Data Exchange): An open-source, machine-readable format managed by the Linux Foundation. It offers flexibility and rich data representation, making it suitable for diverse use cases.
- CycloneDX: Another open-source, machine-readable format gaining traction, particularly within the OWASP community. It emphasizes simplicity and ease of use, making it ideal for agile environments.
- SWID (Software Identification): An industry standard format primarily used by commercial software vendors. It provides a structured approach to identifying and tracking software components.
Beyond the Fundamentals: Advanced Applications of Software Bill of Materials (SBOMs)
The utility of SBOMs extends beyond the aforementioned core functionalities. As the technology matures, we can anticipate its application in various emerging use cases:
- Standardization and interoperability: Efforts are underway to establish standardized formats and exchange mechanisms for SBOMs. This will facilitate seamless integration with existing security tools and workflows, fostering broader adoption and enhanced interoperability within the software ecosystem.
- Continuous monitoring and automated remediation: The integration of SBOMs with vulnerability databases and automated patching tools can enable real-time monitoring for newly discovered vulnerabilities and prompt remediation actions, bolstering the overall security posture of software applications.
- Mitigating zero-day attacks: SBOMs can play a crucial role in mitigating the impact of zero-day attacks. By providing insights into the attack surface and facilitating rapid identification of affected components, organizations can expedite response and containment measures, minimizing potential damage.
Why should you integrate Software Bill of Materials (SBOMs) with Vulnerability Management Tools?
Integrating Software Bill of Materials (SBOMs) with vulnerability management (VM) tools offers a powerful synergy, significantly enhancing your ability to identify, prioritize, and address security vulnerabilities within your software supply chain.
Here are some compelling reasons why you should integrate these two critical tools:
1. Enhanced Vulnerability Identification:
- Automated Matching: SBOMs provide a comprehensive inventory of software components and their versions. Integrating them with VM tools allows for automated matching of these components against vulnerability databases, streamlining the identification of potential security weaknesses.
- Prioritization Based on Context: SBOM data enriches vulnerability information by providing context about the specific components and versions affected within your software. This enables VM tools to prioritize vulnerabilities based on their actual impact on your environment, directing resources toward the most critical issues.
2. Improved Risk Management:
- Proactive Approach: By proactively identifying vulnerabilities through SBOM-VM integration, you can address them before they are exploited by malicious actors. This proactive approach significantly reduces the risk of security breaches and associated damages.
- Informed Decision-Making: SBOM data empowers you to make informed decisions regarding vulnerability remediation. You can assess the potential impact of vulnerabilities on specific components and prioritize patching efforts based on criticality and exploitability.
3. Streamlined Workflows:
- Automated Workflows: Integrating SBOMs and VM tools facilitates the automation of various tasks, such as vulnerability identification, prioritization, and even patch deployment. This automation reduces manual effort, improves efficiency, and minimizes the risk of human error.
- Centralized Management: By consolidating vulnerability information within a single platform, you gain a centralized view of your software supply chain risks. This facilitates better coordination and collaboration between development, security, and operations teams.
4. Increased Transparency and Collaboration:
- Shared Responsibility: SBOMs foster transparency throughout the software supply chain by providing all stakeholders with a clear understanding of the components used in your software. This transparency encourages collaboration between vendors, partners, and customers in addressing vulnerabilities collectively.
- Improved Communication: Integrating SBOMs with Vulnerability Management tools facilitates the communication of identified vulnerabilities and their associated risks to relevant stakeholders. This enables timely and coordinated remediation efforts across the entire software ecosystem.
The Road Ahead: Embracing the Software Bill of Materials (SBOMs) Revolution
The adoption of SBOMs represents a significant paradigm shift in the approach to software security. By fostering transparency, collaboration, and proactive risk management, SBOMs empower organizations to navigate the complexities of the modern software supply chain with greater confidence.
As the technology continues to evolve and gain widespread adoption, we can expect Software Bill of Materials (SBOMs) to become an indispensable tool for securing the software landscape of tomorrow. Schedule Your Vulnerability Management Demo Today! Get Started.
Related Reads:








