Six months for paperwork and six hours for an exploit. That was the reality under the old Risk Management Framework (RMF).
The Department of War, the new name for the Department of Defense after a September 5, 2025 directive, knew this had to change. On September 24, 2025, it introduced the Cybersecurity Risk Management Construct (CSRMC), a framework designed for speed, automation, and continuous defense.
Read the official Department of War release here.
CSRMC replaces RMF, which had governed military cybersecurity since 2014 and was updated in 2022 under DoDI 8510.01. RMF brought discipline, but it also slowed down progress. By the time a system was authorized, the threat picture had already shifted.
CSRMC is designed to close that gap. It makes risk management dynamic and continuous, aligning defenses with the speed of modern threats across air, land, sea, space, and cyberspace.
Katie Arrington, acting CIO, described it as:
A cultural fundamental shift in how the Department approaches cybersecurity.
The Problem With RMF
To understand why CSRMC matters, you first have to look at what came before it. RMF was meant to improve consistency and accountability. It aligned with FISMA and NIST standards and standardized controls across the military.
But in practice:
- Approvals took months.
- Reviews leaned heavily on paperwork and checklists.
- Authorizations reflected a single point in time.
- Testing was infrequent and often disconnected from real threats.
While RMF looked good on paper, adversaries moved faster in practice. That mismatch created the opening for CSRMC.
The Five Phases of the Cybersecurity Risk Management Construct
CSRMC is not just a new policy. It is a new way of building and operating systems with security at every stage.
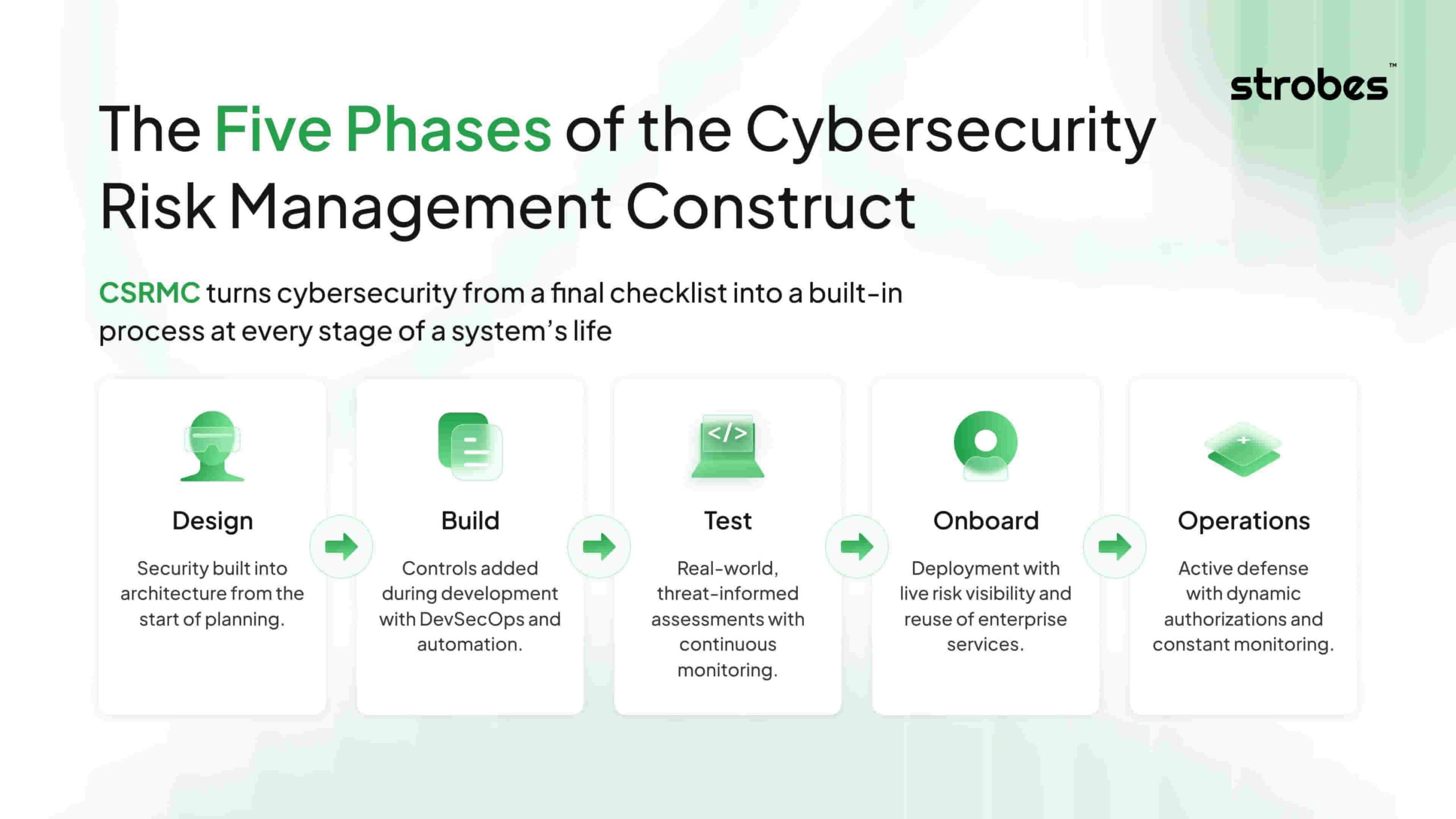
These phases make cybersecurity continuous, not an afterthought.
Ten Strategic Tenets of the CSRMC Framework
If the lifecycle is the “when,” the tenets are the “how.” They set the rules for carrying out cybersecurity across every phase.
| Tenet | What It Means |
| Automation | Machines handle routine tasks like scanning and reporting, cutting errors and delays. |
| Critical Controls | Attention goes to the protections that matter most, such as patching exploitable vulnerabilities. |
| Continuous Monitoring and ATO | Approvals adapt to real-time conditions instead of being locked at one point. |
| DevSecOps | Security integrated directly into development so systems are delivered quickly and securely. |
| Cyber Survivability | Systems built to keep functioning even when under attack. |
| Training | Personnel trained to spot threats, handle tools, and act effectively. |
| Enterprise Services and Inheritance | Shared services and existing approvals reused to save time. |
| Operationalization | Risk data made visible to leaders in real time for informed decisions. |
| Reciprocity | Validated assessments reused across programs, avoiding duplication. |
| Cybersecurity Assessments | Testing is ongoing and shaped by real adversary tactics. |
Together, these tenets move security away from checklists and into a culture of continuous, mission-focused defense.
Direct Impact of CSRMC on the Defense Industry
CSRMC is not just a Pentagon framework. Its ripple effects will spread quickly across the defense industrial base. Contractors, suppliers, and integrators will be expected to meet the same standards of speed and automation that the Department of War is now enforcing internally.
For industry, that means three big shifts:
- Continuous Monitoring Becomes Mandatory – No more point-in-time audits. Systems and services connected to defense networks will need real-time visibility and reporting, with data flowing continuously.
- Reciprocity Replaces Duplication – Vendors will have to prove and reuse validated evidence instead of submitting duplicative assessments. This will save time but demands higher accuracy and trust in testing.
- Automation as the Baseline – Manual vulnerability scans, compliance paperwork, and siloed reporting won’t scale in CSRMC. Vendors will need automated workflows that handle vulnerability ingestion, deduplication, and prioritization without human bottlenecks.
Defense suppliers that adapt early will be better positioned to deliver faster, more secure services under the new expectations.
Potential Challenges for Industry Under the CSRMC Model
Adopting CSRMC principles will not be simple for the defense supply chain. While the framework promises speed and resilience, the transition comes with hurdles that vendors and partners will need to address head-on.
- Legacy Systems and Technical Debt – Many defense contractors still rely on outdated infrastructure built for checklist-style audits under RMF. Converting these environments into continuously monitored, automation-friendly systems will require significant investment.
- Culture Shift – CSRMC pushes for real-time collaboration and constant visibility. For suppliers used to periodic assessments and siloed reporting, this will mean rethinking how teams operate, how they share data, and how fast they respond.
- Economic Pressure – Automation tools, continuous monitoring platforms, and advanced testing capabilities are not free. Small and mid-sized contractors may struggle to fund the transition unless the government provides incentives or shared services.
- Integration Across Programs – Reciprocity only works if evidence is trusted and standardized. For suppliers, this means aligning testing methods, reporting formats, and security metrics across multiple programs, which has rarely happened in the past.
These challenges do not erase CSRMC’s value, but they highlight the scale of change required. Vendors who modernize early will be positioned to thrive, while those who delay may struggle to compete.
How CSRMC Fits Broader Trends
The lifecycle and tenets explain how CSRMC works inside the Department of War. But the bigger picture is that these ideas are not unique to defense. They reflect the same direction enterprise security has already taken.
Organizations worldwide are adopting Continuous Threat Exposure Management (CTEM). CTEM emphasizes always-on visibility, automated workflows, risk-based prioritization, and testing against real adversary techniques. CSRMC uses different terminology, but the principles align closely.
| CSRMC Pillar | Parallel in Modern Security Practice |
| Continuous Monitoring and Dynamic ATO | Live dashboards instead of static approvals. |
| Critical Controls and Mission Assurance | Risk-based prioritization that directs resources to the most impactful issues. |
| Automation | Workflow orchestration that eliminates manual bottlenecks. |
| Cybersecurity Assessments | Continuous, adversary-informed validation of defenses. |
| Reciprocity and Inheritance | Reuse of trusted evidence and shared services to speed delivery. |
This is exactly what leading enterprise platforms already do. CTEM platforms like Strobes CTEM apply the same principles in business environments with always-on visibility, automated risk handling, adversary-informed testing, and prioritization based on impact. The difference is scale. Enterprises use these practices to protect continuity, while CSRMC applies them to safeguard mission assurance in contested domains.
Why Cybersecurity Risk Management Construct Matters
When you zoom out, the reason for this shift becomes clear. In modern conflict, a cyberattack on logistics, satellites, or communications can be as disruptive as a physical strike. CSRMC reduces that risk by making sure:
- Systems are monitored continuously, not occasionally.
- The most dangerous vulnerabilities are fixed first.
- Automation speeds up defense instead of slowing it.
- Testing uses real adversary tactics.
- Proven controls are reused, not repeated.
In enterprise environments, the same practices bring down breach costs and shorten response times. In defense, they ensure readiness and operational superiority.
What Comes Next
CSRMC is not limited to internal defense systems. Contractors, suppliers, and integrators will need to adapt as well. That means:
- More automation in compliance.
- Greater reliance on reciprocity across programs.
- Higher demand for continuous monitoring tools.
- Security built into every DevSecOps pipeline.
Just as RMF influenced cybersecurity across government, CSRMC will ripple outward into the defense industrial base.
Conclusion
The Cybersecurity Risk Management Construct is not a minor adjustment. It is a reset.
By embedding automation, continuous monitoring, reciprocity, and adversary-informed testing across the lifecycle, CSRMC turns risk management into a continuous practice.
Enterprises may call it exposure management. The Department of War calls it CSRMC. The purpose is the same: defenses that are automated, ongoing, and tied directly to impact. The difference lies in the stakes. In business, success means continuity. In defense, success means mission assurance.