Attack Surface Management
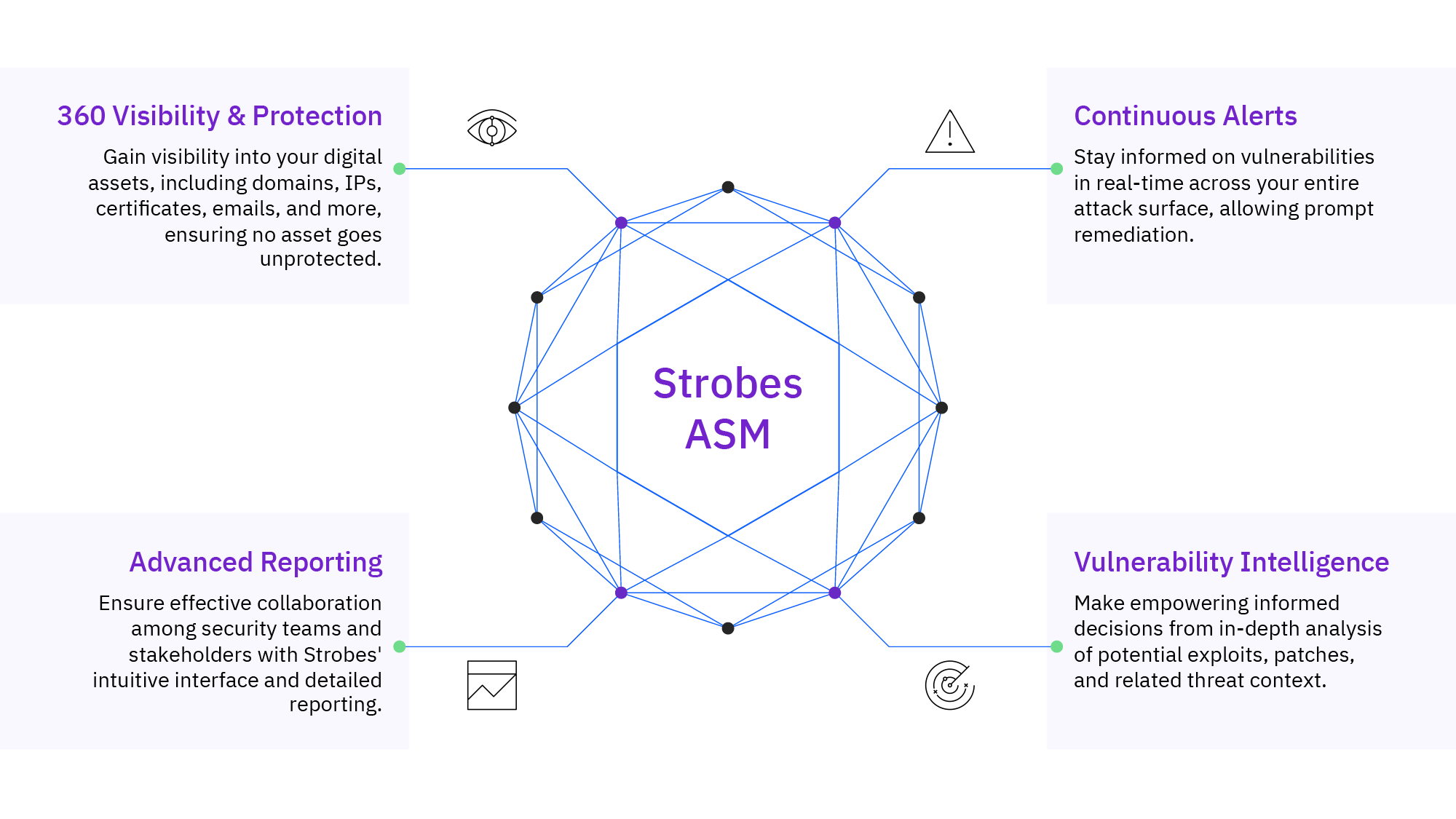
- Comprehensive Overview: Understand the core principles behind Strobes ASM and how it delivers unparalleled visibility and protection.
- Features Breakdown: Explore Strobes ASM’s robust features, from asset discovery to domain protection, and understand how they work together seamlessly.
Download Now
Assessing High-Velocity Exploit Impact
- Establishing a readily searchable inventory of the entire technology ecosystem.
- Implementing real-world applications through targeted assessments for products susceptible to Log4j vulnerabilities.
- Automated correlation of vulnerability data with known exploit patterns to prioritize addressing critical vulnerabilities.
- Alignment with recognized databases such as NIST National Vulnerability Database (NVD) and CISA
Shadow IT Inclusion
- Continuous monitoring to identify and manage unapproved or unknown assets
- Discovery of applications, services, hosts, and operating systems operating outside official channels
- Implementation of measures for real-time detection and response to Shadow IT activities
- Conducting periodic audits and assessments to uncover unauthorized tools and applications
- Establishing clear policies and guidelines to discourage the use of unauthorized IT resources
Real-World Coverage
- Evaluating security in mergers and acquisitions scenarios
- Dynamic correlation of vulnerability data with real-world exploitability metrics
- Cross-referencing vulnerability data with historical threat patterns for predictive analysis
- Integration with DNS monitoring and domain protection measures to prevent unauthorized domain hijacking and mitigate phishing risks
- Generating dynamic lists of external assets and systems
- Continuously monitoring for post-acquisition integration
You can’t fix what you can’t see!