The firewall was set up. Scanners were running. Everything looked fine.
Until a routine network penetration test found an old staging server no one remembered. It was still connected, still exposed, and still using a weak password from two years ago. RDP (Remote Desktop Protocol) was open, and within an hour, the tester had domain admin access.
That forgotten system could have triggered a full-scale breach.
This is exactly what network penetration testing is meant to catch. Not just weak spots on the surface, but the actual routes someone could take to move through your network. It uncovers what your tools quietly skip over.
Scanners will flag open ports or outdated software. But they can’t tell you how an attacker would chain those gaps together, pivot between systems, or steal credentials to reach something sensitive.
A network penetration test fills in that missing piece. It asks:
- What happens if someone gets inside?
- How far can they go before anyone notices?
- Can they reach your most critical data from a single misstep?
And it looks in places your tools often overlook. Outdated systems in hidden VLANs. Shared drives with weak access controls. Old credentials that still work long after they should have been removed.
For most teams, these issues stay hidden until it’s too late. Network penetration testing gives you a chance to find them first and do something about it while you still can.
What is Network Penetration Testing?
Network penetration testing is a controlled, simulated attack on your internal or external network infrastructure. The purpose is to uncover vulnerabilities that an attacker could exploit to gain access, move laterally, or compromise sensitive systems.
It goes beyond what scanners can detect. A network pentest tests what is actually exploitable, not just what looks risky on paper.
The goals are clear:
- Identify weaknesses before someone else does.
- Assess business risk by connecting technical flaws to real consequences.
- Verify detection and response by observing how your systems and teams react under pressure.
Pentesters follow a defined scope and safe testing protocols, but the mindset mirrors that of a real attacker. The objective is to simulate how someone would get in, what they would find, and how far they could go if no one stopped them.
Whether it’s a publicly exposed VPN, an unsecured database, or an over privileged internal account, network penetration testing helps you understand how secure your environment really is and what could happen if a real threat actor came looking.
Types of Network Penetration Testing
Network penetration testing is commonly grouped based on two criteria: the attacker’s position (inside or outside the network) and the amount of access or knowledge shared with the tester. Understanding both helps in simulating realistic attack scenarios and selecting the right combination of tests for your environment.
1. Based on Network Positioning
A. External Network Penetration Testing
- Simulates an attacker operating entirely from outside the organization’s infrastructure
- Targets public-facing assets such as VPN gateways, exposed APIs, web applications, email servers, and DNS
- Involves discovery of open ports, banner grabbing, and service enumeration without insider knowledge
- Explores exploits like default credentials, outdated software, weak authentication, and insecure configurations
- Helps evaluate how well perimeter controls such as firewalls, intrusion prevention systems, and DMZ isolation hold up under real-world pressure
- Often used to identify entry points that attackers could use as the first step into the internal environment
Solution: External Network Pentesting
B. Internal Network Penetration Testing
- Assumes the attacker already has internal access due to compromised credentials, a rogue device, or phishing
- Begins within the internal LAN or over a corporate VPN connection, operating from the perspective of a malicious insider
- Focuses on lateral movement across systems, accessing sensitive resources, and privilege escalation
- Tests common weaknesses such as shared passwords, insecure SMB shares, misconfigured ACLs, and exposed internal services
- Actively probes for opportunities to compromise key systems like Active Directory, file servers, or internal web apps
- Helps assess whether network segmentation, endpoint protection, and identity-based controls are effective once an attacker is inside
Solution: Internal Network Pentesting
2. Based on Information Provided
A. Black Box Testing
- The tester receives no internal information before starting the risks assessment
- Mimics a real-world external threat actor who must discover everything from scratch
- Focuses on reconnaissance, enumeration, and public exposure
- Typically reveals what an attacker could learn and exploit just from scanning public infrastructure
- May not uncover deep internal flaws due to lack of access, but valuable for validating internet-facing risks
B. White Box Testing
- The tester receives full internal visibility including network diagrams, source code (in some cases), admin credentials, and configuration files
- Enables in-depth review of how systems behave under controlled exploitation attempts
- Reduces time spent on discovery and focuses directly on validation of controls, escalation paths, and business logic flaws
- Often used in high-assurance environments or when testing applications or privileged user access scenarios
- Maximizes test coverage but is less reflective of how a real attacker would operate
C. Grey Box Testing
- The tester is given limited internal knowledge or a low-privileged account to simulate a compromised user or vendor
- Balances realism and efficiency by allowing faster enumeration while still revealing real-world privilege abuse scenarios
- Common in enterprise networks where testing every segment from scratch is not feasible
- Useful for mapping out horizontal access, weak identity boundaries, and lateral movement opportunities
- Offers a practical middle ground for both internal and external assessments with controlled scoping
How to Choose the Right Network Penetration Testing Type?
Testing Type | Simulates | Best Used For |
| External Pentest | Unknown attacker from outside | Perimeter security testing |
| Internal Pentest | Compromised device or insider | Lateral movement and privilege testing |
| Black Box | Attacker with no information | Realistic surface attack simulation |
| White Box | Attacker with full internal knowledge | Deep system validation |
| Grey Box | Attacker with partial information | Enterprise-wide security assessments |
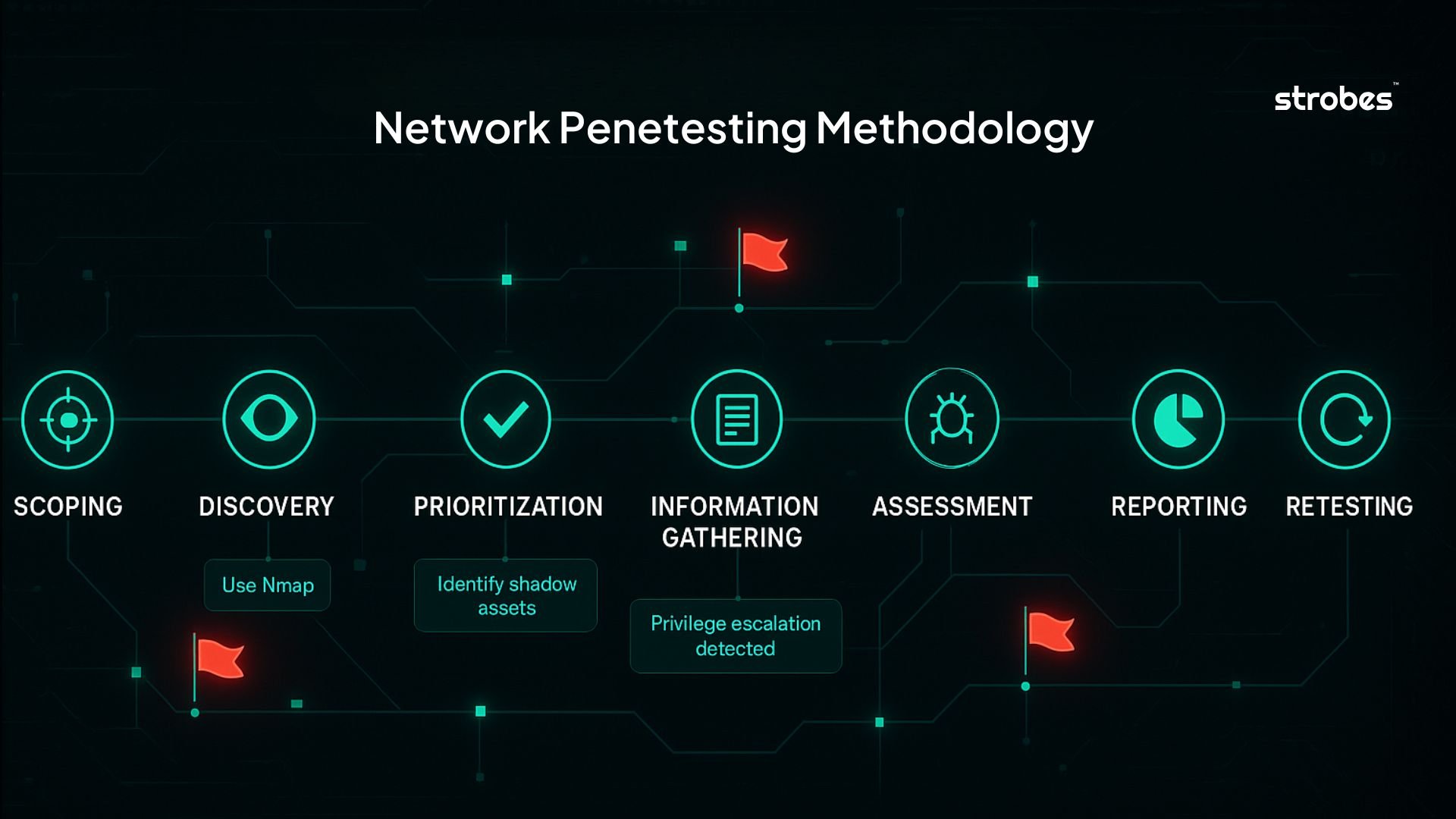
Network Penetration Testing Methodology
This methodology reflects how real-world attackers operate, but with structured planning, scoped execution, and clear pentesting reporting. Each step is designed to simulate attacker behavior while keeping the process controlled, measurable, and aligned with business risk.
A. Scoping
This is the foundational phase where everything is aligned between the security team and the client.
- Defines in-scope assets such as IP ranges, domains, cloud endpoints, and VPNs
- Sets expectations on testing depth, timelines, retesting, and reporting formats
- Establishes rules of engagement including restrictions on denial-of-service or social engineering
- Documents contact points for coordination or emergency communication
- Ensures the assessment avoids unintended downtime in production environments
This phase also maps technical goals to business outcomes, whether it is validating segmentation, testing third-party access, or verifying exposure of critical assets.
B. Discovering
Once scoped, the next step is to identify live assets and enumerate everything reachable.
- Tools: Nmap, Masscan, Netdiscover, Unicornscan
- Identifies active hosts and services across the defined network range
- Maps subnets and detects live systems using ICMP, TCP SYN, and UDP probes
- Classifies devices based on response behavior and port analysis
- Flags potentially unmanaged or undocumented systems that could pose hidden risk
This stage builds a clear picture of the network’s visible attack surface, including forgotten or shadow assets.
C. Prioritizing Assets
All identified assets are not equal. This step focuses effort where it matters most.
- Highlights internet-facing systems, legacy machines, and services exposed to unauthenticated users
- Flags systems running unsupported operating systems or outdated software stacks
- Identifies assets tied to sensitive business functions such as finance, HR, or production
- Avoids spending time on irrelevant or decoy infrastructure
- Vulnerability Prioritization helps align testing effort with potential business impact.
D. Information Gathering
This phase deepens the understanding of target systems and their relationships.
- Tools: Nmap, SMBclient, Enum4linux, Dig, SNMPwalk
- Retrieves service banners and version details to identify known vulnerabilities
- Queries internal DNS servers and explores trust relationships across hosts
- Probes Active Directory using LDAP queries and NetBIOS resolution
- Identifies misconfigured file shares, web interfaces, and exposed development endpoints
Each data point contributes to building an attack plan based on the real posture of the environment.
E. Assessment (Vulnerability Identification and Exploitation)
This is the hands-on testing phase where real attack scenarios are simulated.
- Tools: Metasploit, Nessus, CrackMapExec, ExploitDB, Responder, Burp Suite
- Matches service versions to known CVEs using both automation and manual research
- Executes controlled exploitation to demonstrate access, privilege escalation, or data exposure
- Simulates attacks such as RDP brute-force, NTLM relay, SMBGhost, and credential reuse
- Collects evidence such as hashes, screenshots, and session tokens to support findings
- Operates within the defined scope and avoids destabilizing production systems
The goal is not to test everything, but to prove what is actually possible within attacker reach.
F. Reporting
The reporting phase translates technical findings into clear, actionable insight.
- Breaks down each issue with affected assets, impact level, exploitation method, and remediation guidance
- Includes visual proof, relevant CVE references, and command output for reproducibility
- Summarizes risk at both executive and technical levels for cross-team understanding
- Aligns findings with frameworks like MITRE ATT&CK for threat modeling and SOC response
- Prioritizes high-impact issues over low-severity noise
A strong report is not just a list. It is a roadmap for fixing what matters.
G. Remediation and Retesting
Testing is not complete until fixes are verified.
- Repeats exploitation attempts to confirm that vulnerabilities are fully resolved
- Confirms services are hardened, accounts secured, and insecure access paths blocked
- Marks findings as resolved, partially fixed, or still present
- Updates the report to reflect remediation status and highlight remaining risk
- Provides technical support or advisory for incomplete or unsuccessful fixes
Retesting validates that progress was made and helps close the loop between discovery and resolution.
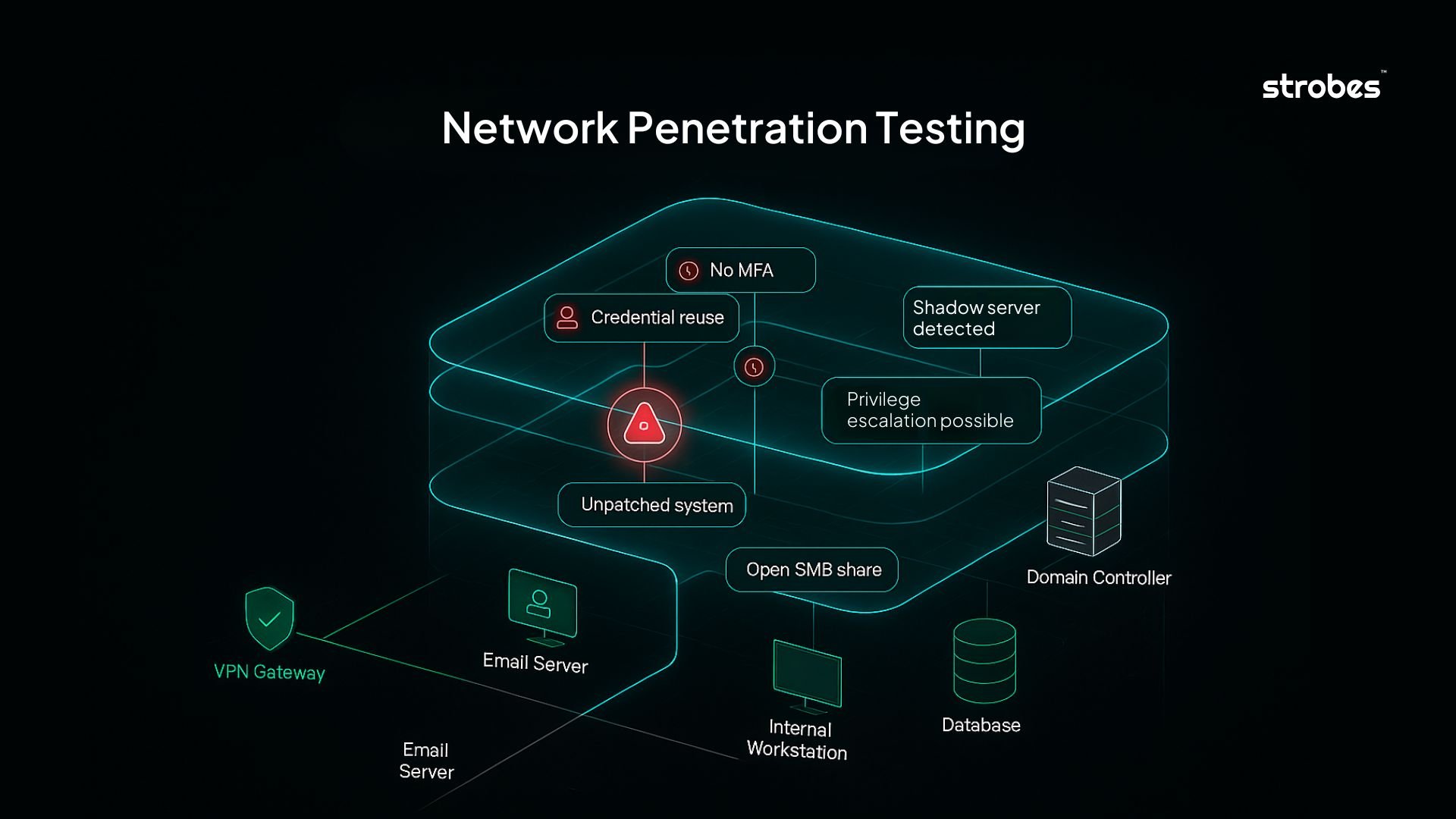
Common Findings in Network Penetration Tests
Network penetration testing often reveals the same critical issues across many environments. These are not advanced zero-day exploits or sophisticated attacks. Most real-world breaches begin with simple, overlooked problems that compound when left unaddressed.
Here are some of the most common findings from network penetration testing:
- Exposed remote access services
Services like RDP (Remote Desktop Protocol), SSH, or VPN are often accessible over the internet without proper restrictions or multi-factor authentication. Weak passwords and default configurations make these services easy entry points.
- Flat network architecture
Internal networks frequently lack segmentation. Once a low-privileged machine is compromised, attackers can move freely between business-critical systems, development servers, and administrative tools.
- Credential reuse and weak authentication
Local administrator passwords are often reused across systems. Password policies may allow simple or easily guessable combinations, increasing the risk of brute-force attacks or password spraying.
- Unpatched or unsupported systems
Legacy operating systems, unmaintained web applications, and old database services often remain in production. These are vulnerable to publicly known exploits and cannot be secured without proper updates.
- Insecure file shares
Shared folders accessible to all domain users may contain sensitive data like passwords, scripts with embedded credentials, or configuration backups. Write access to shared drives can also aid in malware propagation.
- Misconfigured Active Directory
Weak Kerberos configurations, over-privileged service accounts, and legacy authentication protocols like NTLMv1 open multiple paths to domain compromise. Network penetration testing often finds unprotected domain controllers and unmonitored privilege escalation paths.
- No alerting or visibility
Exploitation activities like privilege escalation or lateral movement often go unnoticed. Endpoint detection tools may not trigger alerts during simulated attacks, revealing gaps in detection and response.
- Lack of authentication controls
Internal tools, dashboards, and administrative panels often lack strong access control. Password-only logins without session timeouts or rate limits increase the risk of compromise.
Network penetration testing brings these issues to the surface. It validates how exposed your internal systems really are and whether basic security hygiene is in place.
Business and Compliance Benefits of Network Penetration Testing
Network penetration testing does more than find vulnerabilities, it proves you’re taking security seriously. For many organizations, especially those under regulatory scrutiny, it’s a required part of doing business.
- Testing supports major compliance frameworks like ISO 27001, PCI DSS, SOC 2, and NIST SP 800-53. These standards require organizations to assess risks, validate controls, and document security testing on a recurring basis.
- When a vulnerability cannot be fixed immediately, testing helps demonstrate that compensating controls are in place. For example, if a legacy system can’t be patched, a pentest can show that it’s properly segmented and monitored.
- It enables security teams to track mean time to remediate (MTTR) across different asset types. Over time, this helps show whether your vulnerability management program is improving or stagnating.
- You can also measure residual risk, the exposure that remains even after initial fixes. For example, a misconfigured service may be patched, but another system may still accept reused credentials. Pentesting reveals those gaps.
- Most importantly, it gives auditors, customers, and board members evidence that your systems were tested, findings were addressed, and your team isn’t just checking boxes but actively reducing risk.
Key Considerations When Choosing a Network Pentest Provider
Choosing a pentest vendor is not just about who can run tools. It’s about whether they understand your business, your infrastructure, and what actually matters.
Here’s what you should ask before signing up:
- Are the findings actually validated by humans?
Many providers just run automated scans and hand over unverified results. This creates noise and wastes time. You need a team that manually confirms exploitability.
- Is retesting included in the engagement?
Fixing vulnerabilities is only half the job. Without retesting, there’s no way to know if the fix worked or if the issue reappeared. Always check if validation is part of the package.
- Do they use both manual and automated testing?
Automation helps with coverage, but critical issues like chaining misconfigurations or exploiting trust relationships require human judgment. A good provider combines both.
- Can they explain how each issue ties to business risk or compliance requirements?
Raw vulnerabilities aren’t helpful unless they’re mapped to systems that affect customers, finance, or operations. Business context should never be an afterthought.
- Do they integrate with your workflows?
If the report just lives in a PDF, remediation slows down. Look for vendors who can push findings to Jira, alert on Slack, or plug into your SIEM to enable faster triage and tracking.
Choosing the right provider is not about the cheapest quote. It’s about who gives you clarity, depth, and support when it actually counts.
Final Thoughts
Network penetration testing isn’t just about checking off a compliance task. It’s how you find out what’s really exposed in your environment.
Your internal network isn’t isolated anymore. Cloud tools, remote access, and legacy systems have blurred the lines.
Attackers look for the easiest way in. Pentesting shows you if they’d find one.
Want to see what’s actually at risk?
Frequently Answered Questions (FAQ’s)
Q.1 What gaps can remain after even well-executed network penetration tests?
Situations such as incomplete asset inventories, inaccessible network segments, or changes introduced after scoping may leave some vulnerabilities undetected. Engaging testers early in network mapping and maintaining up-to-date inventories help minimize these blind spots and provide more thorough risk assessments.
Q.2 What should be included in a network pen test report?
A thorough report includes an executive summary, detailed vulnerability descriptions with evidence, risk ratings, business impact, exploitation scenarios, and clear remediation steps. It provides actionable guidance aligned to compliance standards and audit requirements, enabling efficient risk mitigation and ongoing security management.
Q.3 How does network penetration testing differ from vulnerability scanning?
Vulnerability scanning identifies known issues via automated tools but cannot confirm exploitability. Penetration testing simulates attacker behavior, exploiting vulnerabilities to assess real-world risks. This hands-on approach reveals practical threat exposure, reducing false positives and guiding prioritized remediation beyond scanning capabilities.
Q.4 What are the key phases of a network penetration test?
Key phases are planning and scoping, reconnaissance, vulnerability assessment, exploitation, and reporting. This stepwise process ensures identified weaknesses are validated through attack simulation and documented with prioritized recommendations that drive improved security and regulatory compliance.
Q.5 How often should network penetration testing be conducted to maintain strong security and compliance?
Frequency varies by industry and risk profile, but best practices recommend at least annual pentesting, with additional tests after major infrastructure changes or security incidents. Some compliance standards, such as PCI DSS, explicitly define testing cadence; others leave it to the organization’s risk policy and exposure profile.
Related Reads:
- Decoding the Penetration Testing Process: A Step-by-Step Guide
- Strobes 2023 Pentesting Recap: Trends, Stats, and How PTaaS is Transforming Cybersecurity
- Penetration Testing Explained: Safeguarding your Online Presence
- 3 Reasons Why Penetration Testing Is Needed and Why Traditional Pentesting Isn’t Working for You
- How much does a penetration test cost?
- Why Penetration Testing Is Important: Enhancing Security & Reducing Cyber Risks
- Solution: Network Security
- Solution: Internal Network Pentesting
- Solution: External Network Pentesting