Many organizations struggle with security gaps even after investing in different tools and processes. One of the most common reasons for breaches is the presence of unresolved weaknesses in systems. A report by Ponemon Institute highlights that 60% of organizations experiencing a breach in 2024 admitted the root cause was an unpatched or unresolved vulnerability.
This leads to a mention of two of the key processes that are commonly confused or interchanged: vulnerability management vs patch management. Although they are equally important, they have different purposes. Vulnerability management is concerned with the identification and prioritization of risks in all assets, and patch management is concerned with the implementation of vendor fixes to address known software vulnerabilities.
The key to developing a facilitated and effective approach to reduce exposure and enhance overall security readiness is understanding the difference between the two.
What is Vulnerability Management?
Definition and Scope
Vulnerability management is a humanized approach to identifying, assessing, prioritizing, and remediating weaknesses across IT assets. It is not a one-off program, but a process that keeps on going through to mitigate risk and ensure a proper security posture.
It is much more than the implementation of updates. It involves a malconfigured system, systems that are not supported, controls that are missing, and even third-party risks. Vulnerability management ties the vulnerability causes and business consequences together so that the teams understand what to fix initially and why it matters.
Core Functions of Vulnerability Management
1. Asset Discovery
Organizations should have a complete list of their IT assets before they can address the vulnerabilities. This comprises servers, cloud workloads, endpoints, applications, containers, and IoT devices. Unmanaged resources or Shadow IT can be some of the most dangerous resources.
2. Vulnerability Scanning
Automated scanners (SAST, DAST, SCA, container, and cloud scanners) identify weaknesses in applications and infrastructure. Scanning should be continuous to catch exposures the moment they appear.
3. Risk Prioritization
Not all vulnerabilities have the same impact. A score of 7.0 vulnerability in a CVSS could have minimal practical impact in the absence of an active exploit, whilst a medium severity problem in active weaponization could require immediate attention. The allocation of priorities focuses on the vulnerabilities that are most likely to be tapped by the resources.
4. Remediation Planning
Security teams map vulnerabilities to the right owners (IT, DevOps, or application teams) and recommend solutions. Sometimes this means applying a vendor update, other times it may involve configuration changes, network segmentation, or disabling unused services.
5. Validation and Reporting
As soon as a vulnerability is fixed, it has to be rechecked by doing rescans. Reports provide visibility to stakeholders on progress, remediation timelines, and remaining risks.
In the absence of vulnerability management, organizations tend to be caught unawares by exposures they do not even have knowledge of. It helps to create context, a list of thousands of potential flaws is narrowed down into a prioritized list that can be, in fact, implemented.
What is Patch Management?
Definition and Scope
The structured process of obtaining, testing, and implementing vendor-supplied updates to operating systems, applications, and hardware is called patch management. It is less broad than vulnerability management, but no less important.
It deals with one of the most widespread types of vulnerabilities: the lack of updated software. Given that vendors are regularly issuing fixes to bugs and security concerns, it is important to keep up with those releases to seal the known exposures.
Patch Management Process

1. Patch Identification
Patch identification refers to keeping track of new updates released by vendors via advisories, databases such as NVD, and threat feeds. Given that updates are very common, organizations need to sift through them in terms of severity and applicability to avoid missing out on important fixes.
2. Patch Testing
Organizations should test an update in staging environments before implementing it, to be sure of compatibility with business applications. Deployments made rashly and without testing may result in downtime or failure of the application.
3. Patch Deployment
Tests are then deployed to the affected systems as patches. This could be run in a script or by an enterprise tool such as SCCM, WSUS, or third-party patching software.
4. Verification
Verification is used after deployment to make sure that updates have been made successfully. Installations that fail or assets that are not installed are marked as remediation.
5. Documentation and Reporting
Documentation is essential for compliance audits, providing evidence of timely updates across the environment.
Many of the largest breaches in history trace back to missing updates, despite fixes being available. Consistent patch management reduces the attack surface and ensures compliance with frameworks like PCI DSS, HIPAA, and NIST CSF.
Key Differences: Patch Management vs Vulnerability Management
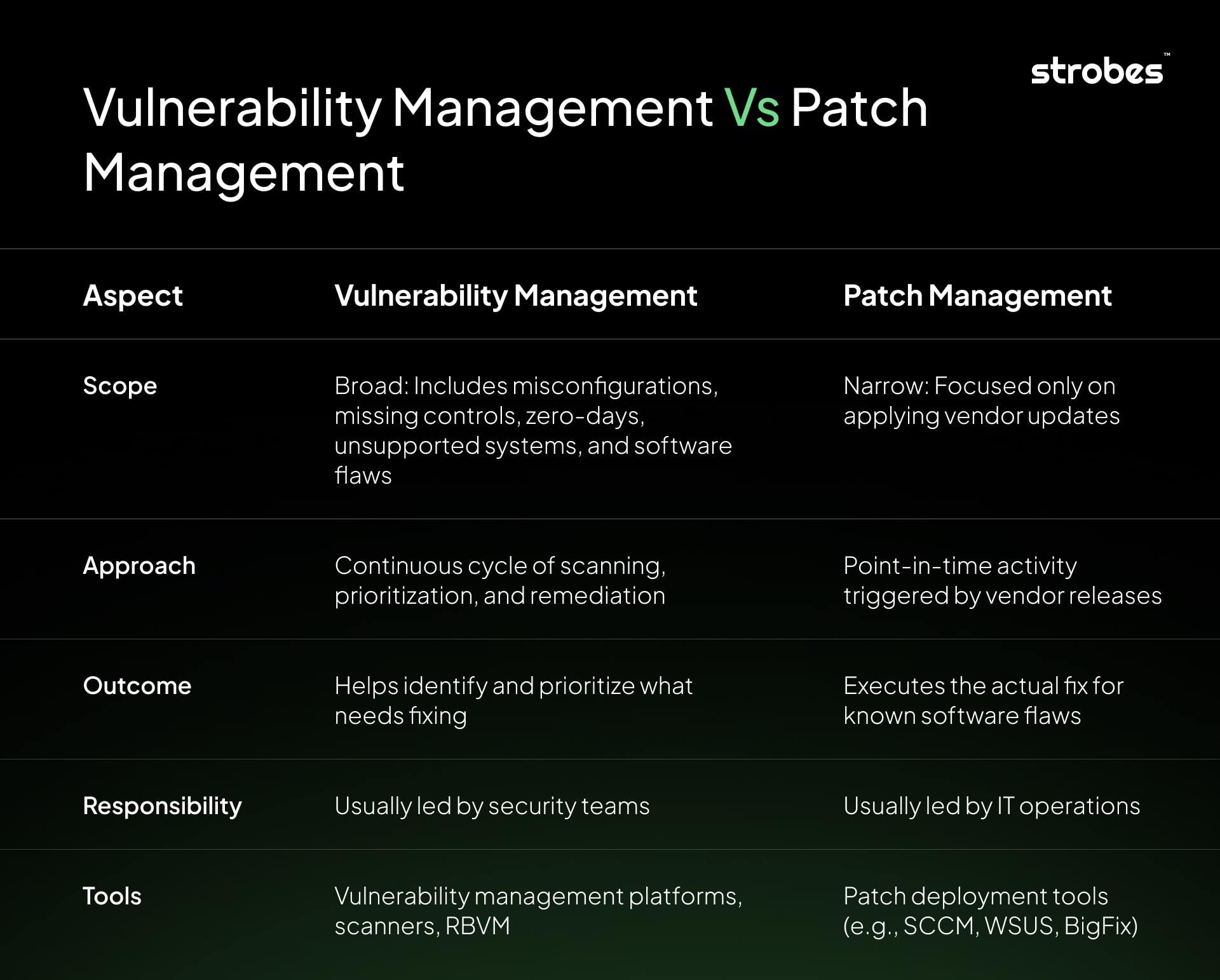
Although they are interconnected, the two processes are fundamentally different.
Simplified View
- Vulnerability management asks: “Where are the risks, and which ones matter most?”
- Patch management answers: “How do we fix the identified issues with vendor updates?”
Why Patch Management Alone is Not Enough
While essential, patch management cannot stand on its own as a complete risk reduction strategy. Here’s why:
- Limited Scope: Patches only address vendor-released software updates. They don’t cover misconfigurations, weak credentials, or unpatched legacy systems.
- Zero-Day Limitations: If no vendor fix exists, patch management cannot help. Vulnerability management ensures zero-days are tracked and mitigated with compensating controls until a fix is available.
- Prioritization Gap: Applying every available patch is resource-intensive and often impractical. Without prioritization, IT teams may waste time on low-risk issues while critical ones remain unresolved.
- Missed Coverage: Many organizations have assets outside formal patch management processes, such as shadow IT, cloud workloads, and unmanaged devices.
The 2024 Verizon DBIR found that more than 50% of breaches traced back to vulnerabilities that had known fixes available for months or even years. This highlights the need for a structured vulnerability management program to complement patching.
How Vulnerability Management Complements Patch Management
Vulnerability management identifies what to fix and why, while patch management executes how to fix. Together, they form a continuous loop:
- Scanning identifies vulnerabilities across applications, infrastructure, and cloud environments.
- Prioritization determines which exposures matter most, using exploit intelligence and business context.
- Remediation Assignment routes tasks to the right IT or DevOps owners.
- Patch Deployment applies the necessary updates.
- Validation ensures the vulnerability is closed.
This integration ensures critical vulnerabilities do not remain open simply because they are buried among thousands of lower-priority issues. It also aligns IT and security teams, creating a shared workflow where vulnerability intelligence guides patching actions.
Best Practices for Integrating Vulnerability and Patch Management
- Align Prioritization with Patch Cycles: Security teams should provide IT teams with prioritized vulnerability data, ensuring that monthly or quarterly patch cycles address the most critical risks first.
- Automate Where Possible: Automation accelerates both identification and remediation. Automated ticket creation, patch rollouts, and rescanning minimize manual work and reduce time-to-fix.
- Test Before Deployment: Even critical patches must be tested in staging environments. Testing ensures compatibility and prevents disruptions that can delay rollout.
- Track Metrics: Metrics like Mean Time to Remediate (MTTR), patch success rate, and vulnerability recurrence rate provide visibility into the effectiveness of your combined program.
- Collaborate Across Teams: Security, IT, and DevOps must work in close coordination. A siloed approach often leads to finger-pointing and unresolved risks.
Role of Strobes in Streamlining the Process
Strobes Risk-Based Vulnerability Management (RBVM) solution brings structure and clarity to this integration.
- Risk-Based Prioritization: Strobes correlates vulnerabilities with exploit intelligence and business context, ensuring patching teams know which updates truly reduce risk.
- Integration with ITSM: Automated workflows push prioritized remediation tasks into tools like Jira or ServiceNow, ensuring accountability and faster response.
- Multi-Scanner Support: From SAST and DAST to SCA, container, and cloud misconfigurations, Strobes consolidates data from multiple sources into a unified view.
- Noise Reduction: By eliminating duplicates and false positives, Strobes prevents IT teams from being overwhelmed with unnecessary tasks.
- Scalable API-First Architecture: Large enterprises can integrate vulnerability management with existing patching and remediation tools seamlessly.
With Strobes, organizations gain a single platform that connects vulnerability intelligence to remediation actions, reducing both risk and operational overhead.
Conclusion
Patch Management vs Vulnerability Management are not the same, but they are deeply interconnected. Vulnerability management provides visibility, context, and prioritization of risks, while patch management delivers the corrective action through vendor fixes. Without one, the other leaves organizations exposed.
When these two processes are aligned, organizations see measurable improvements in risk reduction, audit readiness, and faster remediation. With solutions like Strobes RBVM, security and IT teams can work in unison—focusing on the vulnerabilities with the greatest impact and closing exposures before they can be exploited.
Ready to strengthen your approach to vulnerability management and patching? Discover how Strobes RBVM helps integrate a smarter, risk-based strategy. Book a free RBVM demo with us.







