Between rising cyber threats, growing consumer privacy concerns, and increasingly complex regulatory expectations, financial institutions must stay ahead of the curve or risk costly consequences. That’s where FFIEC compliance comes in.
Established by a coalition of five federal agencies- including the Federal Reserve, FDIC, OCC, NCUA, and CFPB– the Federal Financial Institutions Examination Council (FFIEC) creates uniform standards for how U.S. banks, credit unions, mortgage lenders, and fintechs should manage risks, protect consumer data, and operate safely in a digital-first world.
But FFIEC compliance is more than a regulatory checkbox; it’s a comprehensive framework that touches every part of your organization, from your cybersecurity controls and third-party vendor oversight to your incident response and governance structure.
In this expanded guide, we’ll help you:
- Understand what FFIEC cybersecurity compliance entails
- Break down its core components (risk, cybersecurity, vendor risk, and more)
- Explore which laws and audits fall under FFIEC oversight (like GLBA, BSA/AML, E-SIGN, etc.)
- Learn how to build a governance framework that withstands audits
- Discover practical tips to meet requirements, whether you’re a large institution or an agile fintech startup
Why this matters: Regulatory violations don’t just lead to fines; they erode trust, disrupt operations, and can permanently damage your institution’s reputation. Following FFIEC guidelines can help you avoid those outcomes and better protect your customers and your business.
What is FFIEC Compliance?
The Federal Financial Institutions Examination Council (FFIEC) is a government-mandated body created to establish uniform standards and principles for the examination of financial institutions. It comprises five key regulatory bodies: the Federal Reserve, the FDIC, the OCC, the NCUA, and the CFPB. These agencies work collaboratively to create interagency guidance that banks and other financial entities must follow.
The FFIEC’s main objective is to ensure stability within the financial system by promoting safe and sound operations across financial services. Its guidelines are comprehensive, covering areas like cybersecurity risk management, and consumer data protection.
Purpose of FFIEC Guidelines
FFIEC guidelines serve as a roadmap for institutions to maintain regulatory integrity and reduce systemic risk. They are not merely suggestions; they form the baseline for compliance audits conducted by federal regulators. These guidelines empower institutions to anticipate and manage operational risks, particularly those related to technology and data security. The FFIEC also aims to promote transparency, accountability, and innovation while safeguarding the interests of consumers and the broader economy.
Who Must Follow FFIEC Compliance?
Financial Institutions
All federally insured financial institutions, including commercial banks, savings associations, and credit unions, are required to adhere to FFIEC cybersecurity compliance standards. These institutions are regularly evaluated through rigorous examinations conducted by their respective regulators.
The scope of cybersecurity compliance includes ensuring robust internal controls, maintaining up-to-date cybersecurity frameworks, and protecting customer information. For example, a bank that fails to implement proper encryption protocols for online transactions would likely fall short of FFIEC requirements and face regulatory consequences.
Third-party Vendors
Outsourcing IT services, payment processing, or cloud storage doesn’t remove the burden of compliance. The FFIEC emphasizes the importance of vendor risk management, meaning that any third-party company handling sensitive data or IT infrastructure on behalf of a financial institution must also operate within FFIEC parameters.
Banks are expected to perform due diligence when selecting vendors, evaluate their security posture, and include compliance clauses in contracts. If a vendor causes a data breach, the financial institution will be held accountable just as if the breach had happened internally.
Key Components of FFIEC Compliance
Risk Management
Risk management in FFIEC cybersecurity compliance goes beyond identifying threats; it includes a structured approach to risk appetite, tolerance, and controls. Financial institutions must continuously assess internal and external threats, define their risk exposure, and document mitigation strategies. A proactive risk culture is essential, where risks are not only monitored but also escalated promptly.
Institutions are also expected to evaluate emerging risks such as cryptocurrency transactions, AI usage in lending, and geopolitical cyber threats.
Cybersecurity
Given the sharp increase in cyberattacks, the FFIEC places intense focus on cybersecurity preparedness. Institutions must deploy intrusion detection systems, firewalls, endpoint protection, and user access controls. Regular penetration testing and vulnerability assessments are also required to detect and fix system flaws.
Staff awareness is equally important; human error is a leading cause of breaches. Therefore, employee training on phishing, password hygiene, and secure communication protocols is a must.
Consumer Protection
FFIEC compliance mandates transparent and fair treatment of consumers. Institutions must ensure proper disclosures on loan terms, fees, and data usage policies. Misleading practices can lead to sanctions and lawsuits.
In addition, financial institutions must protect consumer data under laws like the Gramm-Leach-Bliley Act (GLBA), which requires clear privacy policies and opt-out provisions.
Regulatory Reporting
Financial institutions are required to submit accurate and timely reports to regulatory agencies. These reports include financial condition statements, risk exposure summaries, suspicious activity reports (SARs), and customer dispute logs.
Failure to file these reports accurately can result in enforcement actions. FFIEC cybersecurity compliance emphasizes automation and review processes to ensure reporting accuracy.
Common FFIEC Regulatory Requirements
GLBA (Gramm-Leach-Bliley Act)
The GLBA is central to FFIEC compliance. It mandates that institutions provide customers with clear privacy notices and secure their personal information. The Safeguards Rule under GLBA compels institutions to develop, implement, and maintain a comprehensive information security program.
Violations of GLBA often lead to harsh regulatory penalties and consumer distrust, especially if data breaches result from poor data handling practices.
BSA/AML (Bank Secrecy Act / Anti-Money Laundering)
The BSA and its AML requirements require institutions to detect and report suspicious transactions that could involve money laundering, terrorism financing, or fraud. FFIEC guidelines align with these rules by expecting institutions to implement transaction monitoring, customer due diligence, and currency transaction reporting.
Compliance failures in this area often lead to criminal investigations and multi-million-dollar fines.
E-SIGN Act
The Electronic Signatures in Global and National Commerce (E-SIGN) Act gives legal validity to electronic contracts and records, provided certain conditions are met. Under FFIEC cybersecurity compliance, institutions must ensure the integrity, accessibility, and authenticity of electronic records and signatures.
Failure to comply can result in contract disputes or invalidated agreements.
Audit Requirements Under FFIEC Compliance
FFIEC audits are rigorous evaluations conducted by federal regulatory agencies like the FDIC, OCC, or Federal Reserve. These audits assess a financial institution’s risk management, IT controls, and compliance with applicable laws.
Key Components Auditors Examine
1. Information Security Program
Institutions must show they have implemented a written information security program per the GLBA Safeguards Rule. This includes:
- Risk assessment methodology
- Logical and physical access controls
- Encryption standards
- Change management processes
- Intrusion detection and incident response mechanisms
2. Cybersecurity Preparedness
Auditors use the Cybersecurity Assessment Tool (CAT) or other standardized models to determine:
- Risk profile: complexity of products/services, delivery channels (e.g., online banking)
- Maturity level: Baseline to Innovative in areas like threat intelligence, monitoring, and incident handling
3. Business Continuity and Disaster Recovery Plans (BCP/DRP)
Examiners expect:
- Documented and tested BCP/DRP plans
- Offsite backups
- Crisis communication strategies
- Restoration time objectives (RTOs)
4. Vendor Management and Third-Party Risk
You must demonstrate:
- Due diligence procedures for onboarding vendors
- Ongoing performance reviews
- Termination plans
- Data protection clauses in contracts
5. Board and Senior Management Oversight
Evidence must show:
- The board reviews policies annually
- Risk appetite is clearly defined
- Senior leadership is aware of threats and compliance posture
6. Incident Response Program
Auditors check for:
- A documented incident response plan (IRP)
- Chain of command and communication protocols
- Simulated testing or tabletop exercises
- Integration with legal counsel and law enforcement
What an Effective FFIEC Governance Framework Looks Like
A governance framework ensures oversight, accountability, and continuous improvement across the institution’s risk and compliance functions. It’s not just policy, it’s structure, culture, and accountability.
Core Pillars of Governance
1. Board of Directors Involvement
- Must approve and oversee the information security program
- Review risk assessments, audit findings, and strategic compliance plans
- Receive regular briefings (quarterly or semi-annual)
2. Chief Risk Officer (CRO) / Chief Compliance Officer (CCO) Role
- Should have direct reporting lines to the board or a committee
- Lead enterprise risk management (ERM) programs
- Must ensure regulatory changes are communicated across departments
3. Policies and Procedures
- Written, updated annually
- Must include guidelines for acceptable use, data classification, access control, and incident response
4. Risk Committee and Compliance Committee
- May be part of or separate from the board
- Should meet regularly and review:
- Policy updates
- Risk reports
- Internal audit findings
- Policy updates
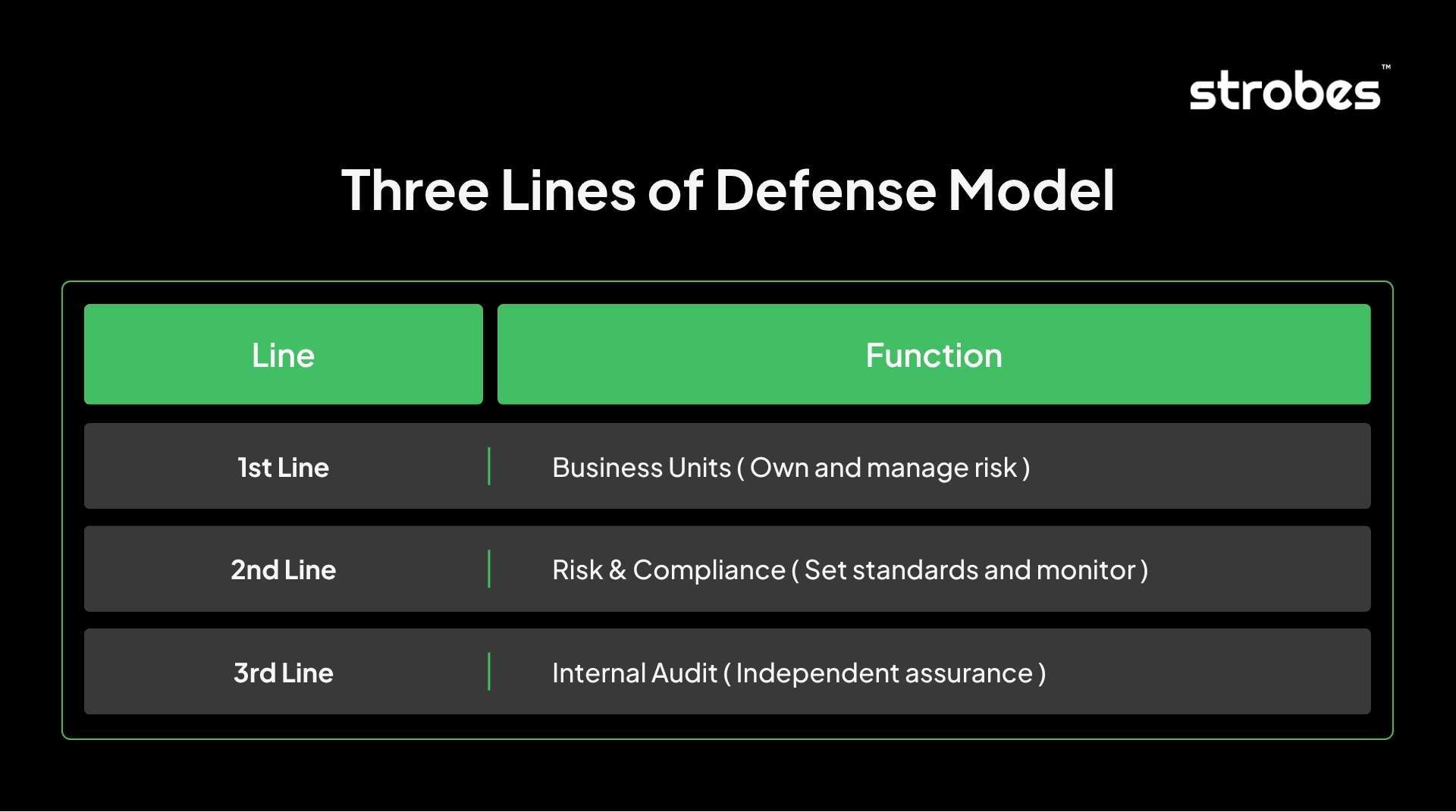
5. Three Lines of Defense Model
FFIEC on Security Assessments and Vulnerability Management
Yes, the FFIEC IT Examination Handbook and Cybersecurity Assessment Tool provide clear guidance:
Frequency of Security Assessments
- Risk-Based Approach: Institutions must determine assessment frequency based on their risk profile (e.g., size, complexity, threat landscape).
- Minimum Expectation: At least annually, or:
- When introducing new technologies (e.g., mobile banking apps)
- After a significant incident (e.g., breach or system failure)
- When regulatory changes occur
- When introducing new technologies (e.g., mobile banking apps)
Vulnerability Management Expectations
FFIEC explicitly outlines a comprehensive vulnerability management lifecycle:
1. Inventory & Asset Identification
- Keep an updated inventory of all assets (hardware, software, endpoints).
2. Vulnerability Scanning
- Conduct regular automated scans (e.g., weekly or monthly)
- Scan internal and external systems
- Prioritize systems with customer data or external exposure
3. Patch Management
- Establish SLA-based patching timelines:
- Critical patches: within 24–72 hours
- High/Medium: within 1–2 weeks
- Critical patches: within 24–72 hours
- Track and document patch status
4. Remediation and Verification
- Log vulnerabilities
- Remediate based on CVSS score
- Re-scan to verify closure
5. Reporting and Metrics
- Report vulnerabilities to senior management
- Use dashboards to track open vs. closed issues
How to Achieve FFIEC Compliance
Compliance Planning
Compliance begins with a clear, well-structured plan. This includes conducting a gap analysis to determine where current operations fall short, followed by developing a comprehensive implementation roadmap. Leadership must buy into this strategy, and budget allocations should reflect the seriousness of compliance goals.
Institutions must also integrate FFIEC compliance with broader risk management and strategic objectives to maintain a unified approach.
Staff Training
Compliance is not just a function of IT or legal departments; it requires organization-wide awareness. Regular, role-specific training ensures that staff understand how their daily activities impact compliance. For example, frontline employees should recognize phishing attempts, while IT staff need to stay current on encryption protocols.
Interactive training modules, simulations, and refresher courses are all effective strategies to build a compliance-aware culture.
Internal Audits
Internal audits serve as an early warning system. They uncover hidden vulnerabilities, assess adherence to policies, and test the effectiveness of controls. Audits should be conducted at least annually and should cover areas like cybersecurity, vendor management, and data privacy.
Audit findings should be documented in detail, with corrective action plans assigned and tracked to resolution.
Best Practices for FFIEC Compliance
Establish Governance Framework
An effective compliance program begins with clear governance. This involves assigning roles and responsibilities, establishing board-level oversight, and integrating FFIEC requirements into enterprise risk management. Institutions should develop and formalize policies for all critical areas, from data access to incident response.
Board members and senior management should be regularly briefed on compliance status and risk exposures, ensuring that regulatory requirements are integrated into strategic planning.
Conduct Regular Assessments
Periodic risk assessments are vital to ensure that security controls remain effective in light of evolving threats and operational changes. These assessments should evaluate cybersecurity controls, data handling procedures, disaster recovery capabilities, and third-party vendor performance.
Using tools like the FFIEC CAT enables institutions to measure progress and compare their cybersecurity maturity to their risk profile. The results can guide budget allocation, staff training, and technology upgrades.
Document All Processes
Regulators place a high value on documentation. Institutions must record everything from risk assessments and employee training to incident responses and audit results. Good documentation proves that the institution is proactive, compliant, and transparent.
Moreover, in the event of an exam or breach, well-maintained records can reduce liability, demonstrate due diligence, and help mitigate reputational damage.
Importance of Documentation and Recordkeeping
Audit Trails
Audit trails are detailed logs that track every action within critical systems. These trails help uncover unauthorized access, system changes, or suspicious activity. Regulators and auditors use these records to ensure that institutions are accountable and that their internal controls are functioning as intended.
A well-maintained audit trail supports investigations, dispute resolution, and compliance validation.
Compliance Reports
These include reports submitted to regulators (like SARs and CTRs) as well as internal compliance dashboards that track key performance indicators. Institutions should implement automated reporting tools to minimize human error and ensure consistency.
Timely and accurate reporting reflects an institution’s operational maturity and responsiveness, both of which are key evaluation factors in FFIEC exams.
Role of Technology in FFIEC Compliance
Automated Tools
Technology can significantly reduce the manual burden of compliance. Automation tools can manage everything from document retention and staff training logs to incident detection and reporting. Governance, Risk, and Compliance (GRC) platforms help institutions monitor their obligations, assess risks, and track mitigation efforts in real-time.
Automation also ensures consistency and accuracy, two critical factors when preparing for federal examinations.
Cloud Security
Cloud services are now integral to financial institutions, but their adoption must align with FFIEC expectations. Institutions must evaluate the security practices of cloud providers, ensuring they offer data encryption, role-based access control, and 24/7 monitoring.
A shared responsibility model must be clearly defined, with contracts specifying each party’s obligations and liabilities.
Encryption Practices
Data encryption, both at rest and in transit, is a foundational requirement under FFIEC guidelines. Institutions must use strong cryptographic algorithms, maintain up-to-date key management systems, and ensure that only authorized personnel can decrypt sensitive data.
Weak or outdated encryption practices are considered serious compliance violations and often lead to failed audits.
Impact of Non-Compliance with FFIEC
Legal Penalties
Non-compliance with FFIEC standards can trigger a series of legal consequences, including heavy fines, regulatory enforcement actions, and even criminal charges in cases involving gross negligence or fraud. For example, institutions that fail to comply with the Bank Secrecy Act (BSA) may face penalties ranging from tens of thousands to millions of dollars per violation. These penalties are not just financial; they often come with consent orders that require major operational changes and strict oversight.
Regulatory actions may also include cease-and-desist orders, limitations on business expansion, or increased scrutiny from multiple agencies, further straining resources.
Reputational Damage
Perhaps even more damaging than legal fines is the loss of public trust. In today’s digital age, news about data breaches or regulatory failures spreads quickly. Customers may lose confidence in the institution’s ability to protect their assets and switch to competitors.
Reputational damage can also impact investor confidence and reduce business opportunities. Vendors may hesitate to work with institutions labeled as high-risk, and partnerships can be lost due to perceived instability or negligence.
Operational Disruption
Institutions found non-compliant often face severe operational disruptions. These can include restricted access to critical systems, forced halting of new product launches, or mandated changes in leadership and governance structures. In some extreme cases, regulators may order the institution to shut down certain services or even revoke charters and licenses.
Operational disruptions not only lead to financial losses but also create chaos among staff and customers, undermining long-term sustainability.
FFIEC Compliance for FinTech and Startups
Scalable Compliance Programs
For fintech startups, compliance can seem overwhelming due to limited budgets and fast-paced growth. However, FFIEC compliance doesn’t require building a full-scale risk department overnight. Instead, startups can adopt scalable compliance programs, small frameworks that grow with the business.
This means starting with key risk areas like data protection, fraud prevention, and user authentication, and then layering in more controls as the company expands. Adopting tools like GRC platforms and partnering with compliance consultants can help build credibility early on.
Risk-Based Approaches
Rather than taking a blanket approach, startups should focus on risk-based compliance, prioritizing controls based on the level of threat each area poses. For instance, a mobile payment app must prioritize encryption and transaction monitoring, while a digital loan platform might focus more on consumer disclosures and underwriting transparency.
This strategic focus not only helps meet FFIEC standards but also conserves resources by investing where the risk is highest.
Solution: Risk Based Vulnerability Management
Future of FFIEC Compliance
AI and Automation
Artificial Intelligence (AI) is reshaping how institutions approach FFIEC compliance. Automated systems can now scan vast amounts of data to detect fraud, identify compliance gaps, and monitor regulatory changes in real time. For example, AI tools can flag anomalies in transaction patterns or scan contracts for missing compliance clauses.
Automation also reduces human error and speeds up response times. As regulations become more complex, integrating AI-driven compliance tools will likely become a necessity rather than a luxury.
Increased Regulatory Oversight
Looking ahead, institutions should brace for more stringent enforcement and faster regulatory changes. As technology evolves and new risks emerge, such as those related to cryptocurrency, decentralized finance (DeFi), and biometric authentication, FFIEC standards are expected to expand accordingly.
Want to see how AI can simplify your FFIEC compliance? Book a personalized demo with Strobes today.
Related Reads:
- What is Vulnerability Management? Compliance, Challenges, & Solutions
- Strobes Penetration Testing Compliance For Audits and Assessments
- Addressing Data Protection and Compliance with Mobile Application Pentesting
- Open Source Security: How Strobes Integrates Security into Your Dev Workflow
- Compliance: What is CERT-In?