When it comes to cybersecurity, it’s not just the technology that evolves, it’s the threats too. Every month brings its own set of challenges, and December 2024 has been no different. But what really stood out? The vulnerabilities that had everyone talking or scrambling.
In this blog, we’ll explore the top 5 CVEs (Common Vulnerabilities and Exposures) of December. Whether you’re a seasoned security expert or just curious about what’s been keeping CISOs on their toes, we’ll break it all down for you; no jargon, no fluff. Just clear, actionable insights on what these vulnerabilities mean and why they matter.
Ready to find out what made the list? Let’s jump in.
CVE-2024-43602: Critical Remote Code Execution Vulnerability in Azure CycleCloud
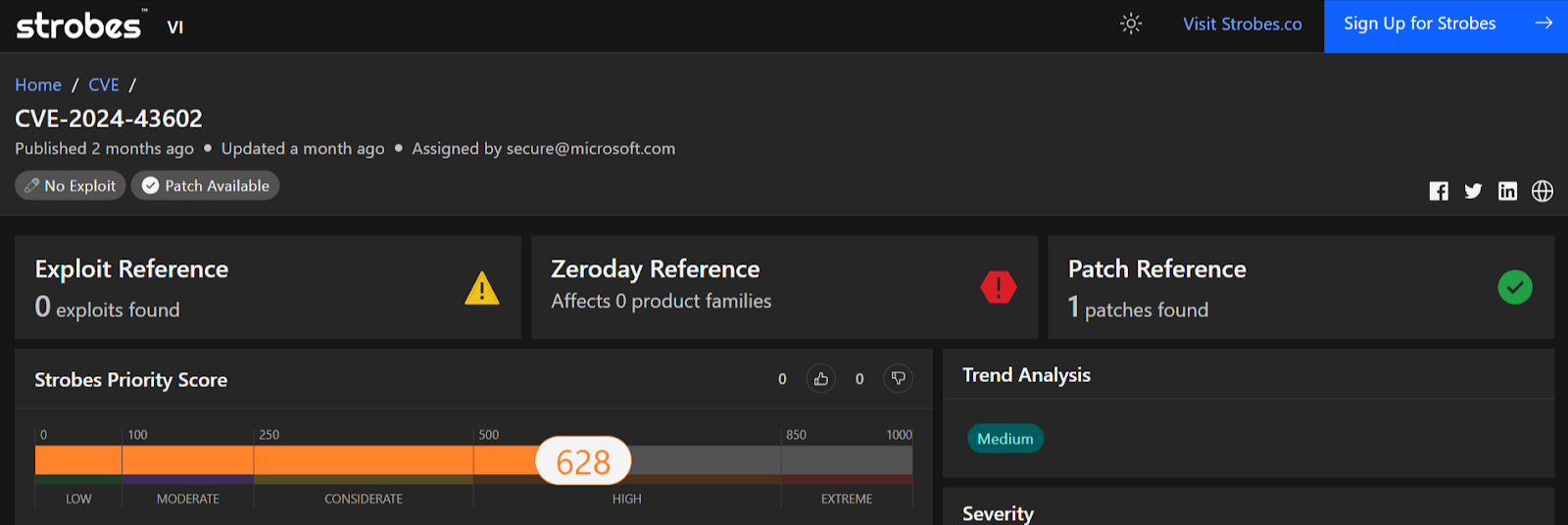
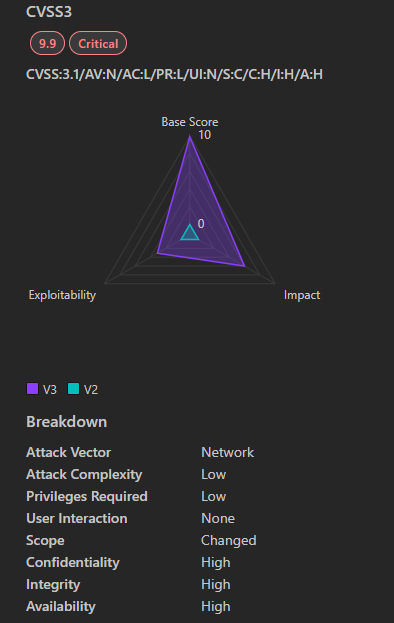
CVE-2024-43602 is a critical security vulnerability that affects Microsoft Azure CycleCloud. CycleCloud is a tool used for orchestrating and managing High-Performance Computing (HPC) environments in the Azure cloud. This vulnerability allows for Remote Code Execution (RCE), meaning an attacker could potentially run malicious code on a vulnerable system from a remote location.
Impact
Successful exploitation of CVE-2024-43602 can have severe consequences:
- Full System Compromise: Attackers could gain complete control over the affected Azure CycleCloud instance.
- Data Breach: Sensitive data stored within the HPC environment could be accessed, stolen, or manipulated.
- Service Disruption: Critical HPC workloads could be disrupted, leading to operational downtime and financial losses.
- Lateral Movement: Attackers could use the compromised system to pivot and attack other resources within the Azure environment.
Details of the Vulnerability
- Severity: Critical
- CVSS Score: 9.9
- Affected Products: Microsoft Azure CycleCloud
- Vulnerability Type: Remote Code Execution (RCE)
- Exploitability: Remote, Low attack complexity, Low privileges required, No user interaction
Mitigation
Microsoft has addressed this vulnerability with a security update. The primary mitigation is to:
- Apply Updates Immediately: Install the latest security updates for Azure CycleCloud provided by Microsoft. This is the most crucial step to protect against this vulnerability.
In addition to patching, consider these security best practices:
- Principle of Least Privilege: Ensure that users and applications have only the necessary permissions to perform their tasks.
- Network Segmentation: Isolate HPC environments from other parts of the network to limit the potential impact of a breach.
- Network Monitoring: Implement robust network monitoring to detect and respond to suspicious activity.
- Strong Authentication: Enforce strong passwords and multi-factor authentication (MFA) for all user accounts.
It’s important to act quickly to apply the necessary patches and implement these security measures to minimize the risk of exploitation.
Source: National Vulnerability Database (NVD):
https://nvd.nist.gov/vuln/detail/cve-2024-43602
CVE-2024-49112: Windows LDAP Remote Code Execution Vulnerability
CVE-2024-49112 is a critical remote code execution (RCE) vulnerability affecting the Windows Lightweight Directory Access Protocol (LDAP). LDAP is a widely used protocol for accessing and managing directory information services, like Active Directory. This vulnerability allows an unauthenticated attacker to potentially execute arbitrary code on a vulnerable system by sending specially crafted LDAP requests.
Impact
Successful exploitation of CVE-2024-49112 can have severe consequences:
- Complete System Compromise: Attackers could gain full control over the affected system, potentially compromising the entire domain in the case of a Domain Controller.
- Data Breach: Sensitive information stored within the directory service could be accessed, exfiltrated, or manipulated.
- Service Disruption: Critical services relying on LDAP could be disrupted, leading to significant business impact.
- Lateral Movement: Attackers could use the compromised system to move laterally within the network, targeting other systems and resources.
Details of the Vulnerability
- Severity: Critical
- CVSS Score: 9.8 (Critical)
- Affected Products:
- Windows Server 2012 R2
- Windows Server 2016
- Windows Server 2019
- Windows Server 2022
- Windows 10
- Windows 11
- Vulnerability Type: Remote Code Execution (RCE) due to an integer overflow.
- Exploitability:
- Remote: The vulnerability can be exploited remotely over the network.
- Low Attack Complexity: Exploitation is relatively straightforward.
- No User Interaction: No user interaction is required for successful exploitation.
Mitigation
Microsoft has released security updates to address this vulnerability as part of their December 2024 Patch Tuesday. The primary mitigation is to:
- Apply Security Updates Immediately: Install the latest security updates from Microsoft as soon as possible. This is the most effective way to protect against this vulnerability.
In addition to patching, Microsoft has provided the following guidance:
- Restrict Inbound RPC Traffic: Configure firewalls to block inbound RPC connections from untrusted networks to Domain Controllers. This can help reduce the attack surface.
It is crucial to prioritize patching Domain Controllers due to their critical role in network infrastructure.
Source: National Vulnerability Database (NVD)
https://nvd.nist.gov/vuln/detail/CVE-2024-49112
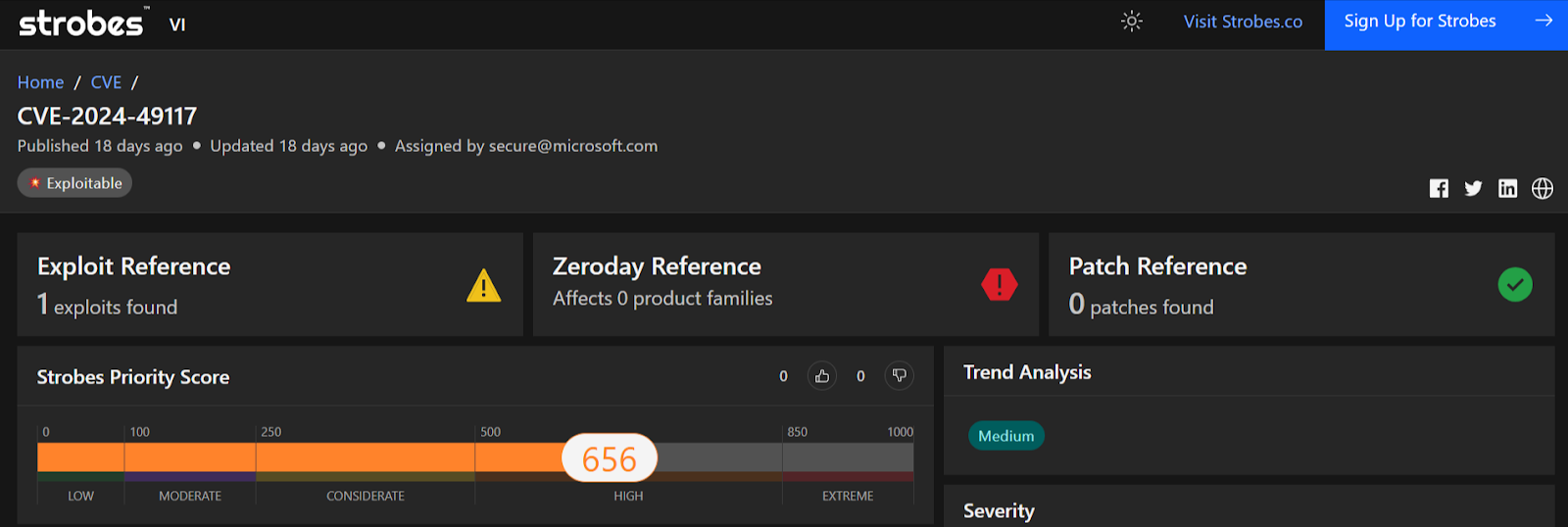
CVE-2024-49117: Windows Hyper-V Remote Code Execution Vulnerability
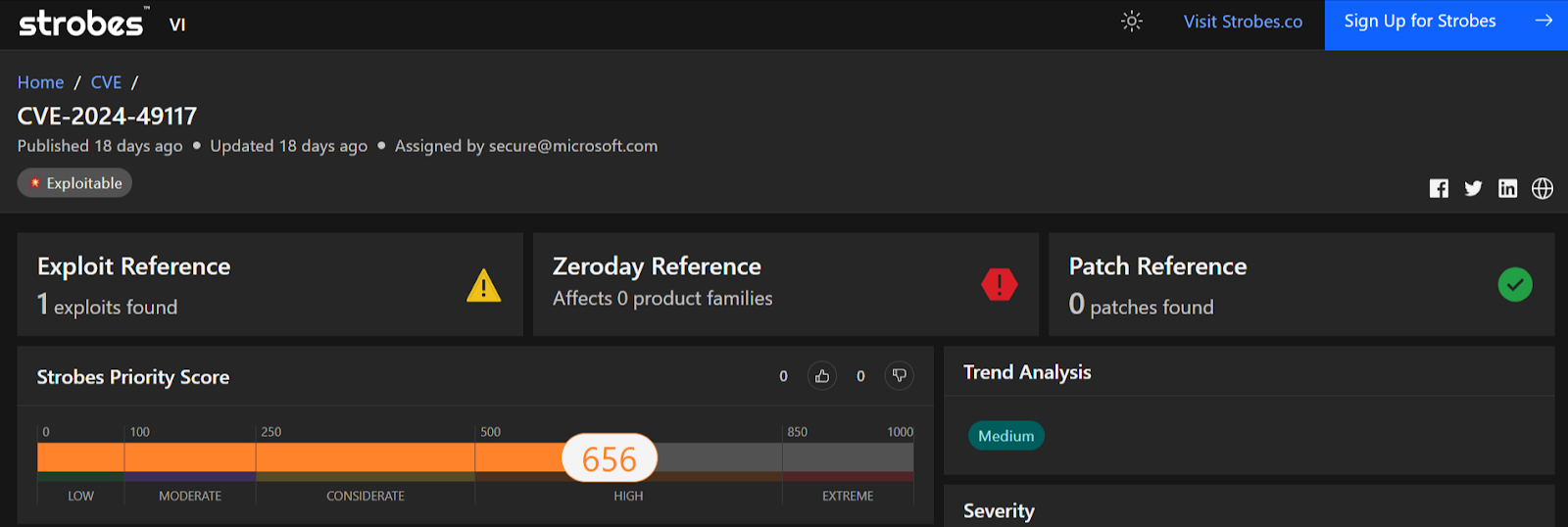
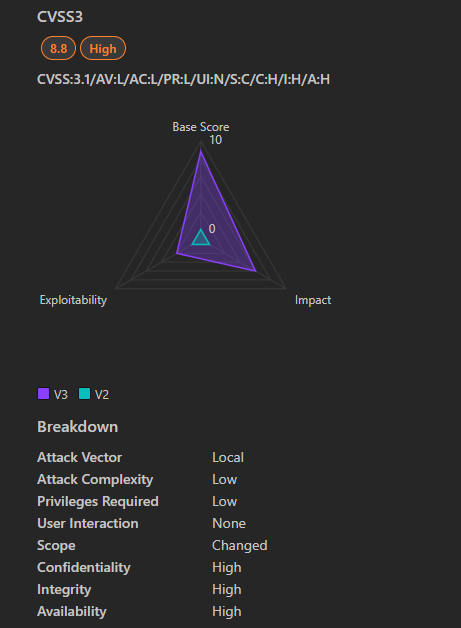
CVE-2024-49117 is a critical vulnerability affecting Microsoft’s Hyper-V, a virtualization technology that allows users to create and run virtual machines (VMs) on a physical host. This vulnerability could allow an attacker with access to a guest VM to execute code on the host operating system.
Impact
Successful exploitation of this vulnerability could have significant consequences:
- Host System Compromise: An attacker could gain control of the host operating system, potentially compromising all other VMs running on it.
- Data Breach: Sensitive data stored on the host or other VMs could be accessed or exfiltrated.
- Denial of Service: The attacker could disrupt the availability of the host system and all its VMs.
Details of the Vulnerability
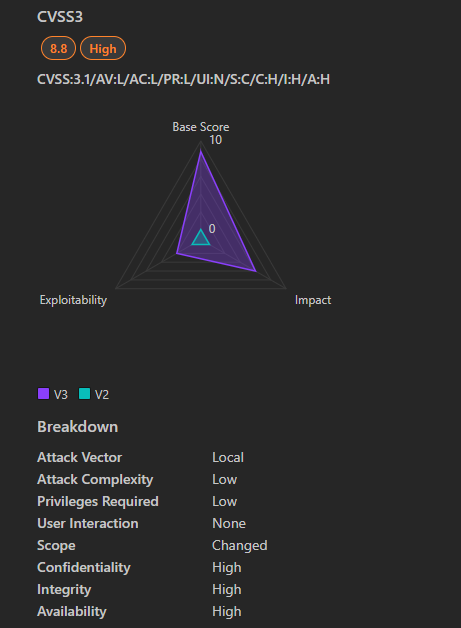
- Severity: Critical
- CVSS Score: 8.8
- Affected Products: Windows Hyper-V
- Vulnerability Type: Remote Code Execution (RCE)
- Exploitability: Requires an authenticated attacker with local access to a guest VM. The attacker needs to send specially crafted file operation requests from the VM to trigger code execution on the host.
Mitigation
Microsoft has released security updates to address this vulnerability as part of their December 2024 Patch Tuesday. It is crucial to:
- Apply Updates Immediately: Install the latest security updates from Microsoft as soon as possible to patch the vulnerability.
- Follow Security Best Practices: Implement general security best practices, such as strong passwords, multi-factor authentication, and network segmentation, to minimize the risk of exploitation.
- Monitor for Suspicious Activity: Monitor Hyper-V hosts for any unusual activity that could indicate an attempted exploitation.
Source: National Vulnerability Database (NVD): https://nvd.nist.gov/vuln/detail/CVE-2024-49117
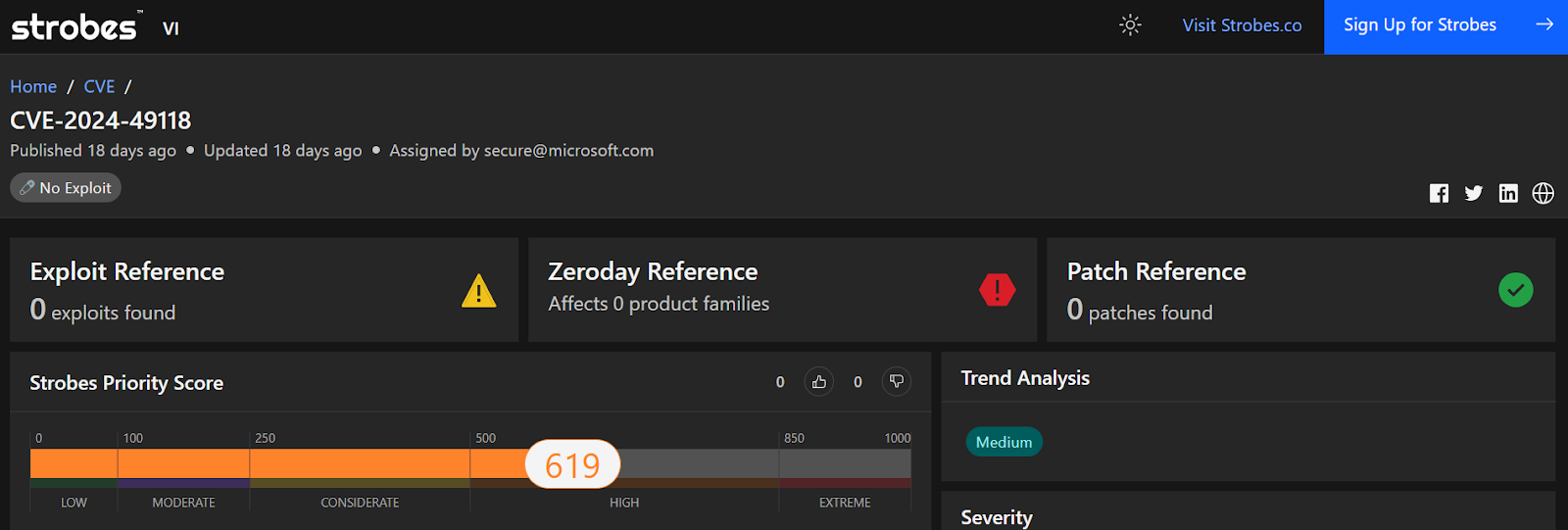
CVE-2024-49118: Remote Code Execution Vulnerability in Microsoft Message Queuing
Microsoft Message Queuing (MSMQ) is a technology that allows applications running on different computers to communicate with each other by sending and receiving messages. CVE-2024-49118 describes a vulnerability within MSMQ that could allow an attacker to execute code remotely on a target system.
Impact
Successful exploitation of this vulnerability could allow an unauthenticated attacker to execute arbitrary code on the target system in the context of the MSMQ service. This could lead to:
- Complete System Compromise: An attacker could gain full control of the affected system.
- Data Breach: Sensitive information stored on the system could be accessed and stolen.
- Denial of Service: The attacker could disrupt critical services or cause the system to crash.
- Lateral Movement: The compromised system could be used as a stepping stone to attack other systems on the same network.
Details of the Vulnerability
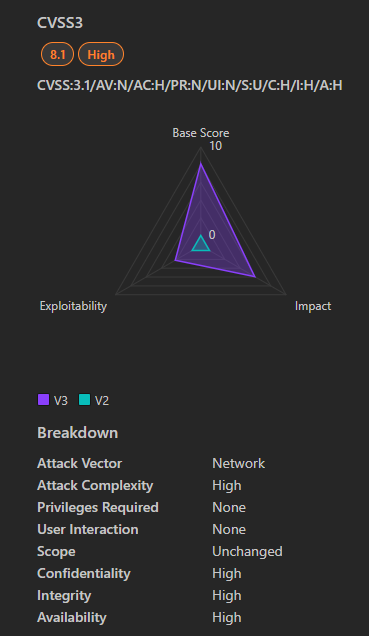
- Severity: Critical
- CVSS Score: 8.1 (HIGH)
- Affected Products: Microsoft Windows systems with the MSMQ service enabled.
- Vulnerability Type: Remote Code Execution (RCE)
- Exploitability:
- Remote: The vulnerability can be exploited remotely over a network.
- Race Condition: Exploitation requires the attacker to win a race condition, making it slightly more complex to exploit. This means the attacker needs to perform certain actions within a specific timeframe or sequence to succeed.
- Exploitation Less Likely: Microsoft has assessed this vulnerability as “Exploitation Less Likely” because the race condition needs to occur “during the execution of a specific operation that recurs in a low frequency on the target system.”
Mitigation
The primary mitigation is to install the security updates released by Microsoft as part of their December 2024 Patch Tuesday. It is crucial to:
- Apply Updates Immediately: Install the latest security patches from Microsoft as soon as possible.
- Disable MSMQ if Not Needed: If MSMQ is not required, disable the service to eliminate the attack vector.
- Network Segmentation: Implement network segmentation to limit the potential impact of a successful exploit.
- Monitor Network Traffic: Monitor network traffic for suspicious activity that may indicate an attempted exploit.
Sources:
- National Vulnerability Database (NVD): https://nvd.nist.gov/vuln/detail/CVE-2024-49118
CVE-2024-11667: Zyxel Firewall Directory Traversal Vulnerability
CVE-2024-11667 is a directory traversal vulnerability found in the web management interface of Zyxel ZLD firewall firmware. This flaw allows attackers to bypass security measures and potentially upload or download files via specially crafted URLs.
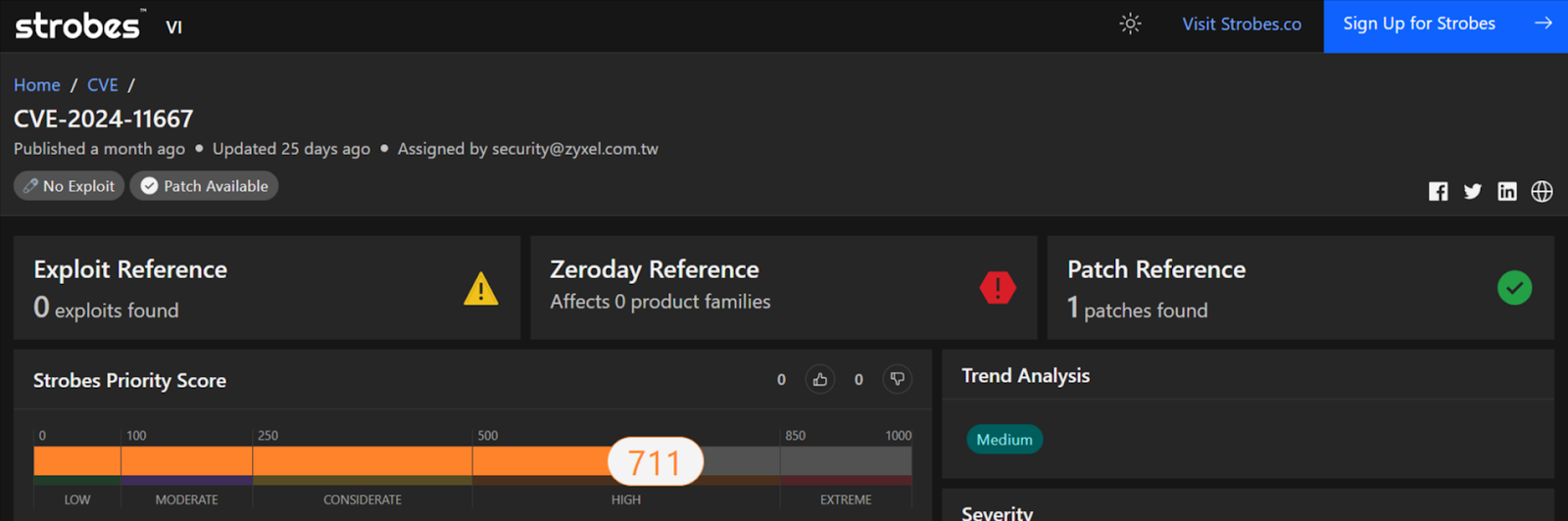
Impact
Successful exploitation of this vulnerability can have serious consequences:
- Unauthorized Access: Attackers can gain unauthorized access to the firewall’s system.
- Data Breach: Sensitive information, such as credentials, could be stolen.
- Backdoor Creation: Attackers might establish backdoor VPN connections for persistent access.
- Ransomware Deployment: This vulnerability has been actively exploited to deploy the Helldown ransomware.
Details of the Vulnerability
- Severity: High
- CVSS Score: 9.8
- Affected Products:
- Zyxel ATP series firmware versions V5.00 through V5.38
- Zyxel USG FLEX series firmware versions V5.00 through V5.38
- Zyxel USG FLEX 50(W) series firmware versions V5.10 through V5.38
- Zyxel USG20(W)-VPN series firmware versions V5.10 through V5.38
- Vulnerability Type: Directory Traversal (Path Traversal)
- Exploitability: Exploitation is considered relatively easy, especially for internet-facing firewalls.

Mitigation
The primary mitigation is to update the ZLD firewall firmware to the latest version (5.39 or later). Zyxel has released patches to address this vulnerability, and it’s crucial to apply them promptly.
Important Notes:
- This vulnerability is actively being exploited in the wild.
- The Cybersecurity and Infrastructure Security Agency (CISA) has added CVE-2024-11667 to its Known Exploited Vulnerabilities Catalog.
- Devices managed through the Nebula cloud management system are not affected.
It’s strongly recommended that organizations using affected Zyxel firewalls take immediate action to update their firmware and protect their networks from potential attacks.
Source: CVE Details
https://www.cvedetails.com/cve/CVE-2024-11667
Final Words
December 2024’s top CVEs highlight the ongoing challenges of securing systems. Each vulnerability underscores the importance of prioritizing critical flaws, updating systems promptly, and maintaining strong security practices.
The takeaway is simple; effective vulnerability management is essential. By focusing on risk-based approaches and addressing vulnerabilities quickly, organizations can reduce exposure and mitigate potential damage. For a closer look at these CVEs and smart strategies for managing them, visit Strobes’ Vulnerability Intelligence platform.







