Cyber threats don’t take a break, and February 2025 proved just that. This month, we saw some serious vulnerabilities that could cause major problems if not patched quickly. From remote code execution flaws in Windows to security gaps that could give hackers control of your systems, it’s clear that the danger is real and urgent.
In this roundup, we’re breaking down the most impactful CVEs disclosed this month, highlighting their risks, affected systems, and why security teams need to act fast.
1. CVE-2025-0108 | Palo Alto Networks PAN-OS Management Web Interface Authentication Bypass Vulnerability
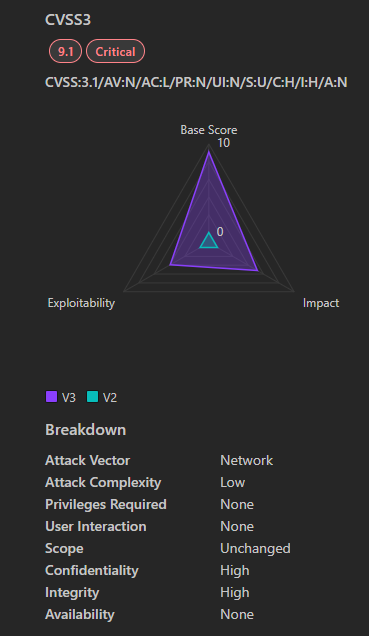
CVE-2025-0108 is a critical authentication bypass vulnerability in the management web interface of Palo Alto Networks’ PAN-OS software. This flaw allows unauthenticated attackers with network access to the management interface to bypass authentication and invoke specific PHP scripts, potentially compromising the system’s integrity and confidentiality.
Details of the Vulnerability
The vulnerability arises from improper handling of web requests by the management interface, enabling attackers to bypass authentication mechanisms and access certain PHP scripts. While this does not permit remote code execution, it poses significant risks to the system’s integrity and confidentiality.
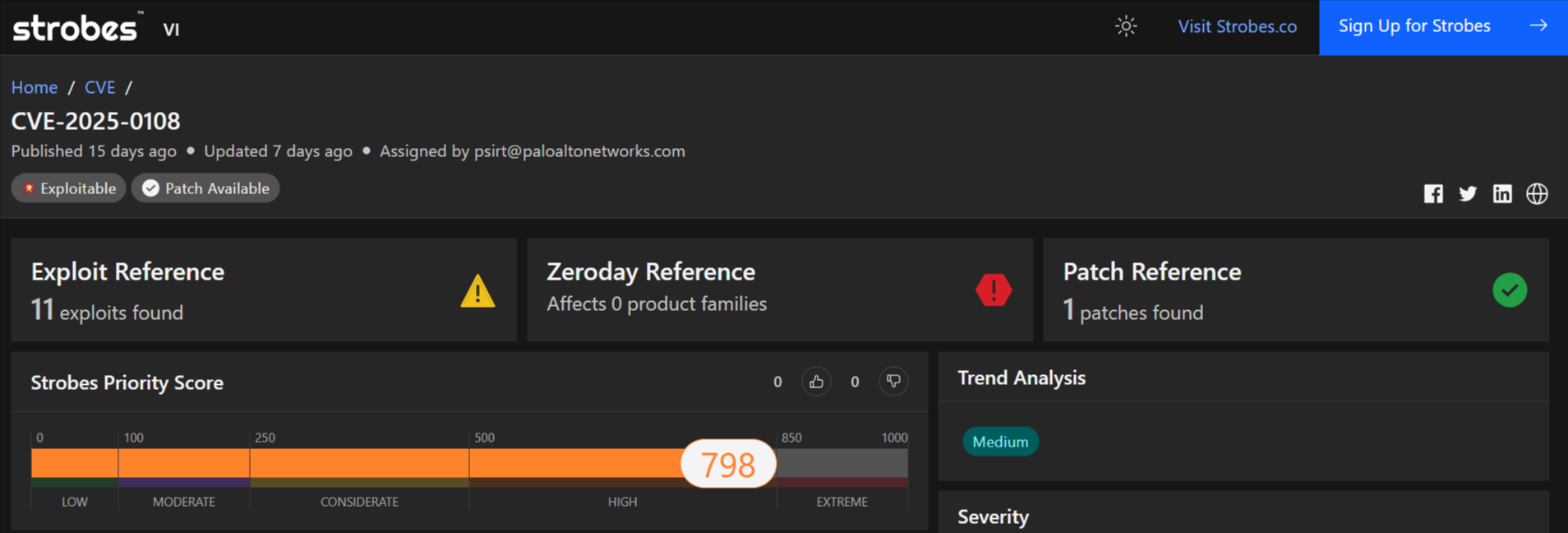
- Severity: High
- CVSS Score: 9.1 (Critical)
- Impact: High (affecting Integrity and Confidentiality)
- Affected Products: PAN-OS versions 10.1.0 to 10.1.14, 10.2.0 to 10.2.13, 11.1.0 to 11.1.6, and 11.2.0 to 11.2.4
- Vulnerability Type: Authentication Bypass
- Exploitability: Functional; exploitation has been observed in the wild.
- Authentication: None required for exploitation.
Exploitation
Attackers with network access to the management web interface can exploit this vulnerability to bypass authentication and invoke specific PHP scripts. Successful exploitation can lead to unauthorised access, potentially compromising the system’s integrity and confidentiality. Notably, there have been observed attempts to chain this vulnerability with others, such as CVE-2024-9474 and CVE-2025-0111, to enhance the attack’s impact.
Mitigation
To mitigate this vulnerability, it is essential to:
1. Restrict Access: Limit access to the management web interface to trusted internal IP addresses, following Palo Alto Networks’ critical deployment guidelines.
2. Apply Patches: Upgrade to the fixed PAN-OS versions:
- 11.2.4-h4 and later
- 11.1.6-h1 and later
- 10.2.13-h3 and later
- 10.1.14-h9 and later
Additional Information
This CVE has been added to CISA’s Known Exploited Vulnerabilities Catalog, underscoring the urgency for remediation. Organisations using affected PAN-OS versions should apply the recommended patches promptly and ensure that management interfaces are not exposed to untrusted networks.
Timeline
- February 12, 2025: CVE disclosed and advisory published.
- February 18, 2025: Added to CISA’s Known Exploited Vulnerabilities Catalogue.
- February 21, 2025: Updated fix availability and clarifications on recommended remediation.
References
- Palo Alto Networks Security Advisory: CVE-2025-0108
- CISA Known Exploited Vulnerabilities Catalogue: CVE-2025-0108
- Help Net Security Article: PAN-OS Authentication Bypass Vulnerability
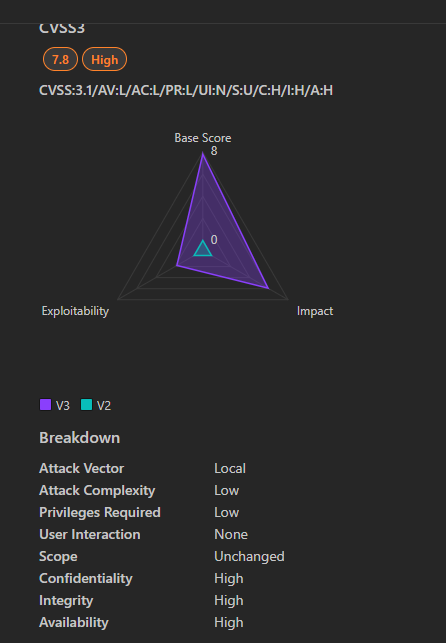
2. CVE-2025-21418 | Windows Ancillary Function Driver for WinSock Elevation of Privilege Vulnerability
CVE-2025-21418 is a significant elevation of privilege vulnerability in the Windows Ancillary Function Driver (AFD.sys) for WinSock. This flaw allows authenticated attackers to execute code with SYSTEM privileges, potentially leading to full system compromise.
Details of the Vulnerability
The vulnerability resides in the AFD.sys driver, which interfaces with the Windows Sockets API to facilitate network communications for Windows applications. An authenticated user can exploit this flaw by running a specially crafted program, enabling the execution of arbitrary code with SYSTEM-level privileges. This type of vulnerability is often combined with a code execution exploit to achieve complete system takeover.
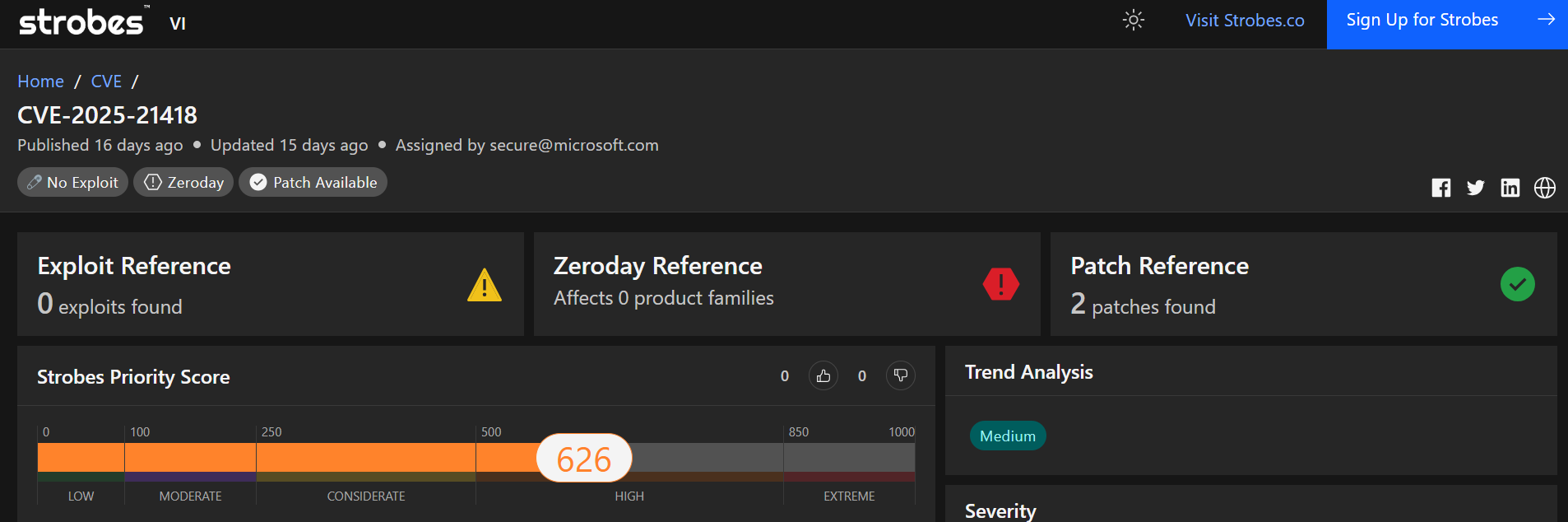
- Severity: High
- CVSS Score: 7.8
- Impact: High (affecting Confidentiality, Integrity, and Availability)
- Affected Products: Various versions of Microsoft Windows
- Vulnerability Type: Elevation of Privilege (EoP)
- Exploitability: Exploited in the wild; active exploitation has been observed.
- Authentication: Requires local authenticated access.
Exploitation
To exploit this vulnerability, an attacker must have local authenticated access to the target system. By executing a specially crafted program, the attacker can elevate their privileges to SYSTEM level, gaining complete control over the system. This vulnerability has been actively exploited in the wild, underscoring the urgency for remediation.
Mitigation
To mitigate this vulnerability, it is essential to:
- Apply Security Updates Promptly: Microsoft has released patches addressing this issue. Ensure all affected systems are updated with the latest security patches.
- Limit Privilege Exposure: Adhere to the principle of least privilege by restricting administrative rights to essential users and processes only.
- Monitor Systems Proactively: Utilize security tools to monitor network activity and system logs for signs of abnormal behavior, enabling early detection and response to potential exploitation attempts.
Additional Information
This CVE has been added to CISA’s Known Exploited Vulnerabilities Catalog, highlighting its significance and the necessity for immediate action. Organizations are strongly advised to apply the recommended patches and follow mitigation strategies to protect their systems from potential exploitation.
Timeline
- February 11, 2025: CVE disclosed and advisory published.
- February 12, 2025: Mitigation steps released.
- March 4, 2025: Deadline for remediation as per CISA guidelines.
For more detailed information, refer to Microsoft’s official security advisory and the National Vulnerability Database entry for CVE-2025-21418.
References
- National Vulnerability Database: CVE-2025-21418
- Microsoft’s official security advisory: CVE-2025-21418
3. CVE-2025-21400 | Microsoft SharePoint Server Remote Code Execution Vulnerability
CVE-2025-21400 is a remote code execution (RCE) vulnerability in Microsoft SharePoint Server. This vulnerability allows authenticated attackers with user interaction to execute arbitrary code on the affected server.
Details of the Vulnerability
An attacker with valid credentials can exploit this vulnerability by convincing a user to connect to a malicious server. Successful exploitation enables the attacker to execute arbitrary code within the context of the SharePoint application pool or server farm account.
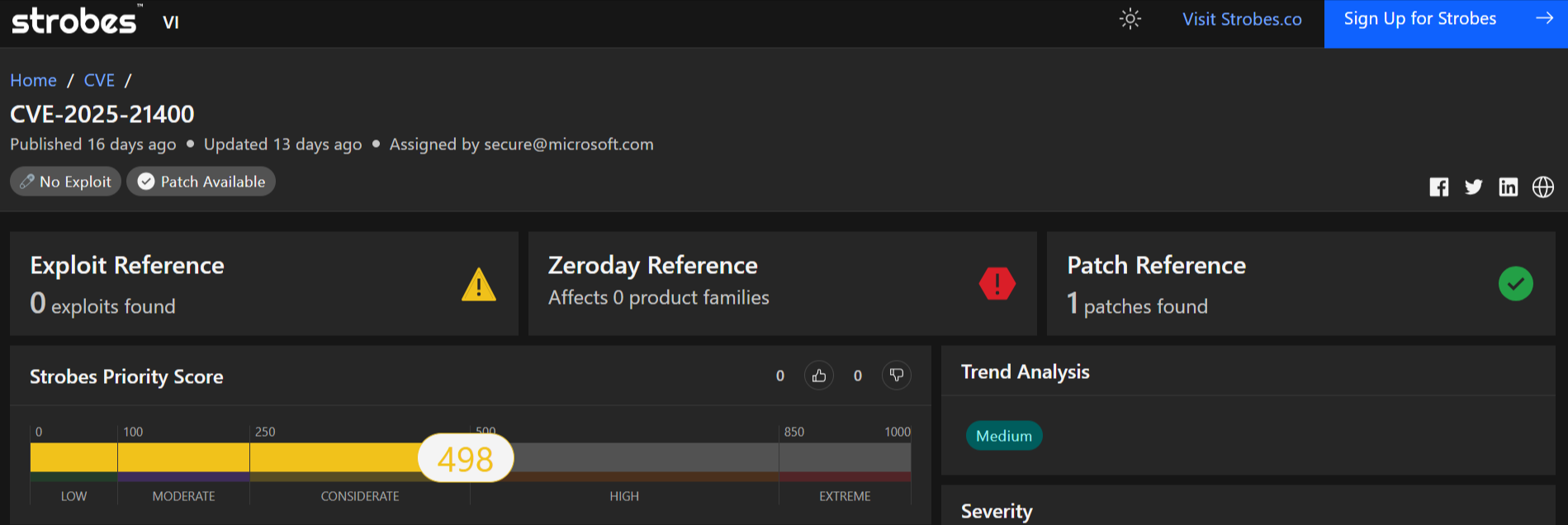
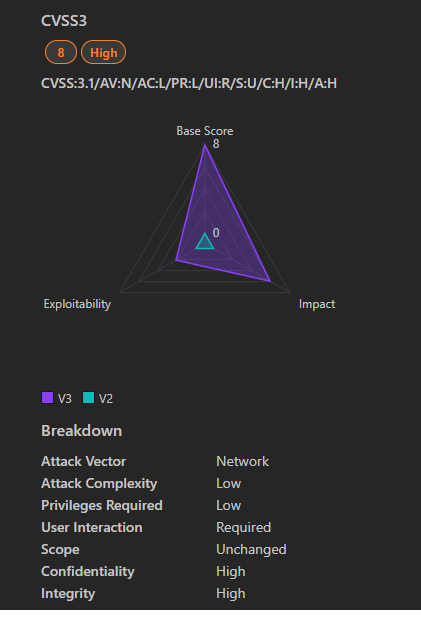
1. Severity: High
2. CVSS Score: 8.0
3. Impact: High (affecting Confidentiality, Integrity, and Availability)
4. Affected Products:
- Microsoft SharePoint Server Subscription Edition (versions prior to 16.0.17928.20396)
- Microsoft SharePoint Server 2016
- Microsoft SharePoint Server 2019
5. Vulnerability Type: Remote Code Execution (RCE)
6. Exploitability: Exploitation requires valid credentials and user interaction.
7. Authentication: Required for exploitation.
Mitigation
To mitigate this vulnerability, it is essential to:
- Apply Security Updates: Install the latest security updates provided by Microsoft for the affected SharePoint Server versions.
- Restrict Access: Limit user permissions to the minimum necessary to reduce potential attack surfaces.
- Educate Users: Inform users about the risks of connecting to untrusted servers and opening unsolicited links or files.
Additional Information
This vulnerability was addressed in Microsoft’s February 2025 Patch Tuesday release. Administrators are strongly advised to prioritize the deployment of the relevant patches to prevent potential exploitation.
Timeline
- February 11, 2025: CVE-2025-21400 disclosed and advisory published.
- February 14, 2025: Mitigation steps released.
Reference
- Microsoft Security Response Center: CVE-2025-21400
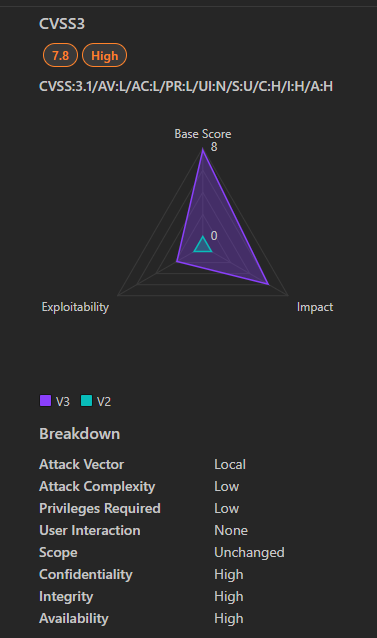
4. CVE-2025-21420 | Windows Disk Cleanup Tool Elevation of Privilege Vulnerability
CVE-2025-21420 is a significant elevation of privilege vulnerability in the Windows Disk Cleanup Tool (cleanmgr.exe). This flaw allows attackers to gain SYSTEM-level privileges on affected Windows systems by exploiting the tool’s improper handling of symbolic links.
Details of the Vulnerability
The vulnerability arises from the Disk Cleanup Tool’s failure to correctly resolve symbolic links before accessing files. An attacker with local access can create a malicious symbolic link that the tool processes, leading to unauthorised file operations and potential elevation to SYSTEM privileges.
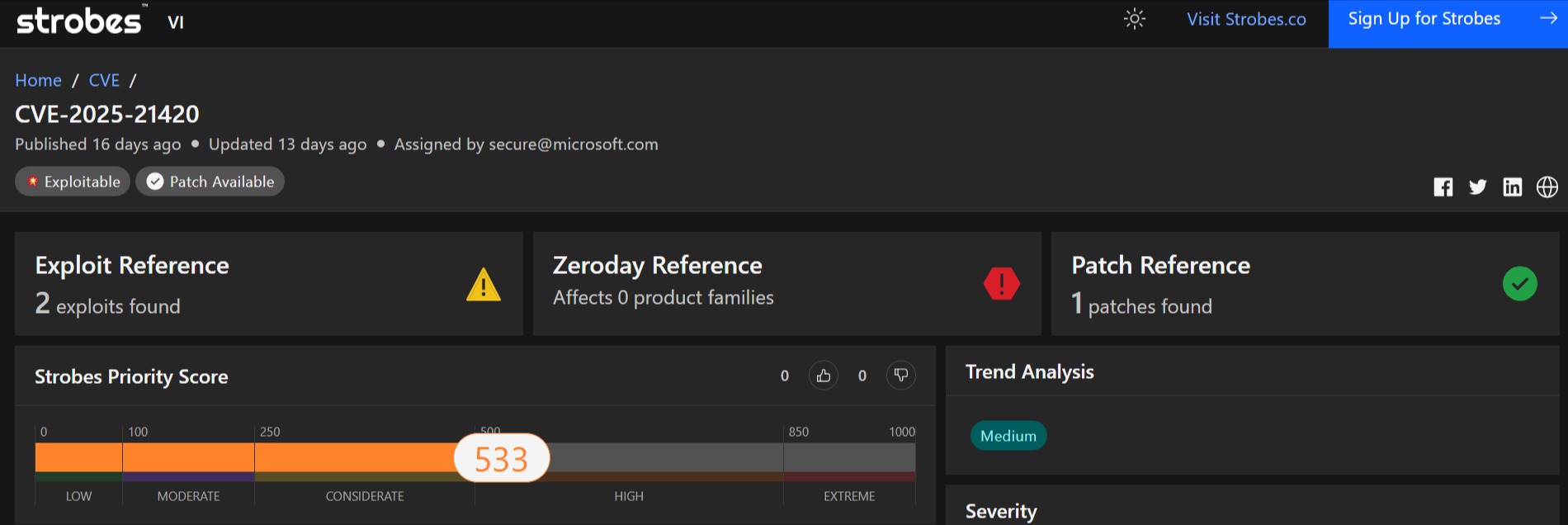
- Severity: High
- CVSS Score: 7.8 (High)
- Impact: Compromise of Confidentiality, Integrity, and Availability
- Affected Products: Various versions of Windows 10, including versions 1507, 1607, and 1809
- Vulnerability Type: Elevation of Privilege
- Exploitability: Proof-of-concept exploit available; exploitation requires local access
- Authentication: Requires local authenticated user access
Exploitation
An attacker with local access can exploit this vulnerability by creating a crafted symbolic link that the Disk Cleanup Tool processes. This manipulation can lead to unauthorised file operations, allowing the attacker to execute arbitrary code with SYSTEM privileges.
Mitigation
To address this vulnerability:
- Apply Patches: Install the security updates released by Microsoft in February 2025. These updates rectify the improper link resolution in the Disk Cleanup Tool.
- Restrict Access: Limit local access to trusted users only, reducing the risk of exploitation.
- Monitor Systems: Regularly audit systems for unauthorised symbolic links and unusual activities related to cleanmgr.exe.
Additional Information
This vulnerability was addressed in Microsoft’s February 2025 Patch Tuesday updates. A proof-of-concept exploit demonstrating the flaw was published, underscoring the importance of prompt patch application. Organisations are urged to update their systems immediately to prevent potential exploitation.
Timeline
- February 11, 2025: CVE-2025-21420 disclosed and advisory published.
- February 14, 2025: Proof-of-concept exploit released publicly.
- February 20, 2025: Microsoft releases security patch addressing the vulnerability.
Reference
- National Vulnerability Database: CVE-2025-21420
- Microsoft Security Response Center: CVE-2025-21420
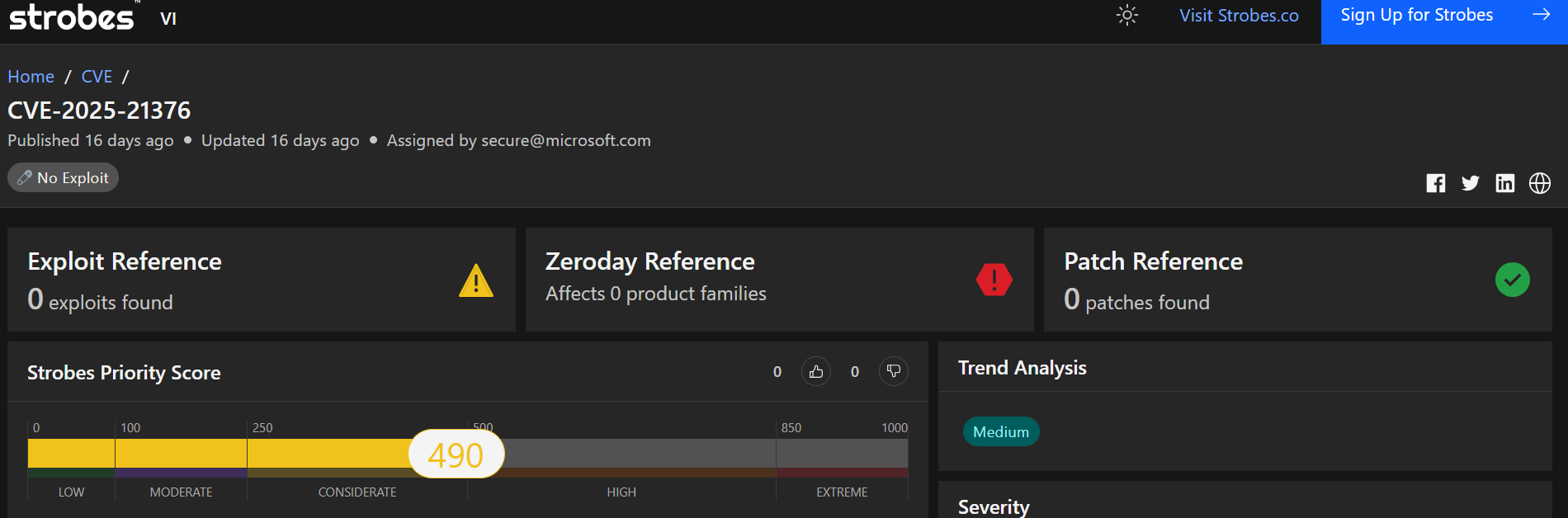
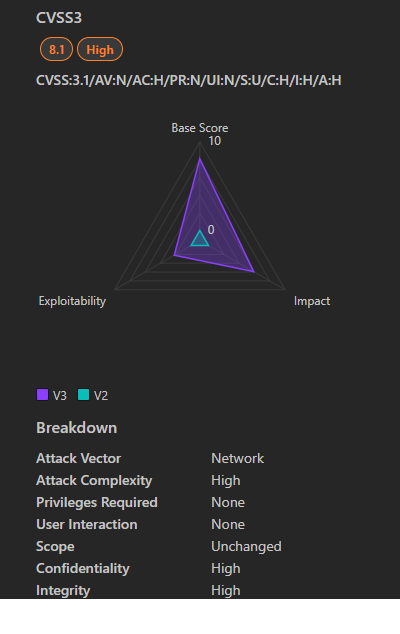
5. CVE-2025-21376 | Windows Lightweight Directory Access Protocol (LDAP) Remote Code Execution Vulnerability
CVE-2025-21376 is a critical remote code execution vulnerability in Microsoft’s Windows Lightweight Directory Access Protocol (LDAP) implementation. This flaw allows attackers to execute arbitrary code remotely by sending specially crafted requests to a vulnerable LDAP server, potentially leading to unauthorised system control.
Details of Vulnerability
1. Severity: High
2. CVSS Score: 8.1
3. Impact: High (affecting Confidentiality, Integrity, and Availability)
4. Affected Products:
- Windows Server 2019
- Windows 10 Version 1809
- Potentially other versions
5. Vulnerability Type: Remote Code Execution (RCE)
6. Exploitability: The vulnerability is considered “wormable,” meaning it can propagate across networks without user interaction.
7. Authentication: None required for exploitation.
 Exploitation
Exploitation
An attacker can exploit this vulnerability by sending a specially crafted request to a vulnerable LDAP server, triggering a buffer overflow that allows for arbitrary code execution. Due to its wormable nature, the exploit can spread rapidly across networks, similar to past outbreaks like WannaCry.
Mitigation
To mitigate this vulnerability, it is essential to:
- Identify Affected Systems: Check your inventory for systems running Windows Server 2019, Windows 10 Version 1809, or other potentially affected versions.
- Apply Patches: Use Windows Update or your enterprise patch management system to download and install the February 2025 security updates.
- Verify Updates: After applying updates, ensure that the patches have been successfully installed by reviewing system update histories.
- Enhance Security Measures: Implement additional security measures such as firewalls, intrusion detection systems, and network segmentation to limit potential exposure.
- Monitor Networks: Keep an eye on network traffic and system logs. Rapid detection of anomalies can help halt an attempted exploit before it escalates.
Additional Information
Microsoft disclosed this vulnerability on February 11, 2025, as part of its February 2025 Patch Tuesday release. Due to its critical nature and potential for rapid propagation, it is imperative to apply the provided security updates promptly to protect systems from potential exploitation.
Timeline
- February 11, 2025: CVE-2025-21376 disclosed by Microsoft.
- February 26, 2025: NVD last modified the CVE entry.
References
- National Vulnerability Database: CVE-2025-21376
- Windows Forum: CVE-2025-21376
Final Takeaway
February 2025’s top CVEs highlight the constant evolution of cyber threats. From critical exploits to stealthy privilege escalation flaws, these risks demand swift action. Prioritizing the most severe vulnerabilities can make all the difference in keeping systems secure. For deeper insights and practical strategies to tackle these threats, explore Strobes’ Vulnerability Intelligence platform.

 Exploitation
Exploitation