October wasn’t short on headlines, but these CVEs did more than make the news. They reshaped how organizations view exposure, privilege, and trust across their environments. Top CVEs of October 2025 spotlights the vulnerabilities that drove real-world exploits, privilege abuse in the cloud, and system-level compromises that matter to every enterprise. If patch fatigue has crept in, this list will remind you why urgency still wins.
1. CVE-2025-59287| Microsoft WSUS Remote Code Execution via Deserialization Bug
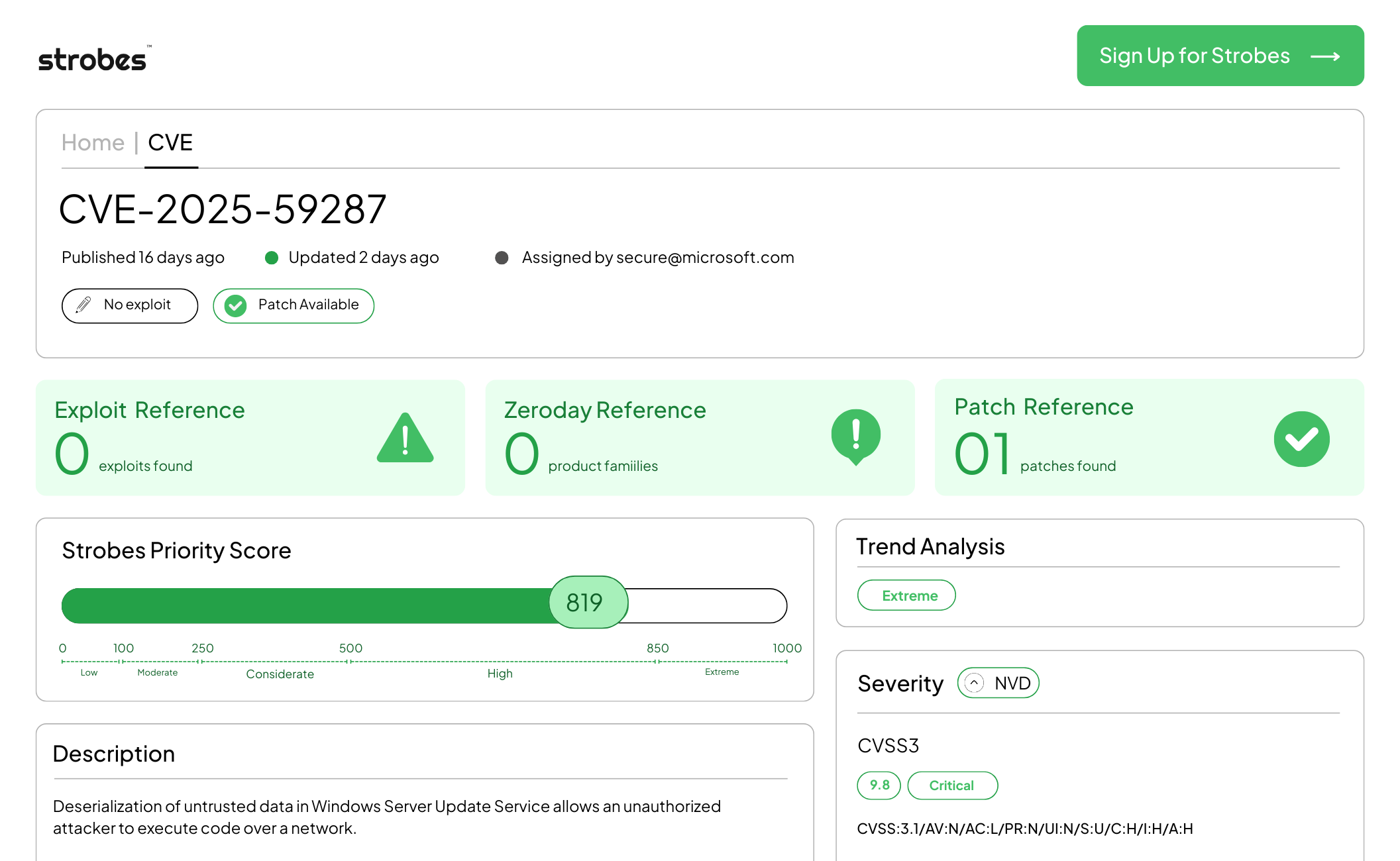
CVE-2025-59287 is a critical vulnerability in Microsoft Windows Server Update Services (WSUS) that permits unauthenticated attackers to trigger unsafe deserialization of WSUS data and achieve remote code execution with SYSTEM privileges. Microsoft released an out-of-band update after proof-of-concept exploit code was made public and multiple security vendors observed active exploitation in the wild.
CVE-2025-59287 Overview
Vulnerability Breakdown
CVE-2025-59287 stems from insufficient validation when WSUS processes certain serialized objects (AuthorizationCookie and related data) delivered to WSUS web services. An attacker can send crafted input that the WSUS service deserializes without proper checks. The unsafe deserialization primitive provides a reliable path to execute code on the server process. Because WSUS runs with high privilege and is often reachable from administrative networks, exploitation yields SYSTEM-level execution, and an attacker can manipulate update artifacts or use the server as a pivot to other assets. Observed attack chains leverage unauthenticated network requests to invoke the deserialization vector, followed by payload staging and execution.
Impact of Exploitation
If an attacker succeeds, likely outcomes include:
- Remote Code Execution: Arbitrary code running as SYSTEM on WSUS servers.
- Supply-chain style risk: Compromised WSUS servers can be abused to distribute malicious updates or tamper with patch delivery to many endpoints.
- Lateral Movement: SYSTEM-level control on a central management server enables broad lateral access across the estate.
- Operational Disruption: Tampering with update workflows or blocking patch telemetry, increasing attack surface and detection gaps.
Mitigation & Patching
Why is this CVE in Our Top Picks of the Month?
CVE-2025-59287 combines a high-severity remote code execution primitive with two enterprise factors that amplify risk. First, WSUS is a centralized update service that touches many endpoints, so a compromised WSUS server can affect large portions of an environment. Second, active exploitation and public PoC code accelerated attacker activity and scanning. Finally, the initial patch required an out-of-band update after the Patch Tuesday release, which increased the window of exposure for organizations that had not yet applied the emergency fixes. These traits make it a top priority for CISOs and security leaders.
Strobes Recommendation
- Immediately identify all Windows servers that have the WSUS server role enabled. Inventory them and mark them high priority.
- Apply Microsoft’s Oct 23, 2025, out-of-band updates that correspond to your Server builds as soon as change windows allow. Validate successful patching and service restart.
- If you cannot patch immediately, block access to WSUS from untrusted networks and restrict management access to a trusted admin VLAN or VPN only. Document and accept operational impact.
- Hunt for IoCs and anomalous activity on WSUS servers now. If compromise is suspected, isolate the server, preserve evidence, and plan a rebuild from clean images. Rotate any credentials or signing keys that may have been exposed.
- Review the update delivery architecture and consider adding additional integrity checks on updates, as well as tighter controls on which systems can pull from internal WSUS servers. Consider out-of-band monitoring rules for WSUS IIS endpoints.
Bottomline
Critical unauthenticated deserialization RCE in WSUS. Active exploitation was observed and added to CISA’s KEV catalog. Prioritize immediate patching with Microsoft’s Oct 23, 2025, out-of-band updates or apply strict network restrictions until patches are installed. Treat WSUS servers as high-value assets during incident response and hunting.
2. CVE-2025-49708 | Microsoft Graphics Use-After-Free Enables Privilege Escalation
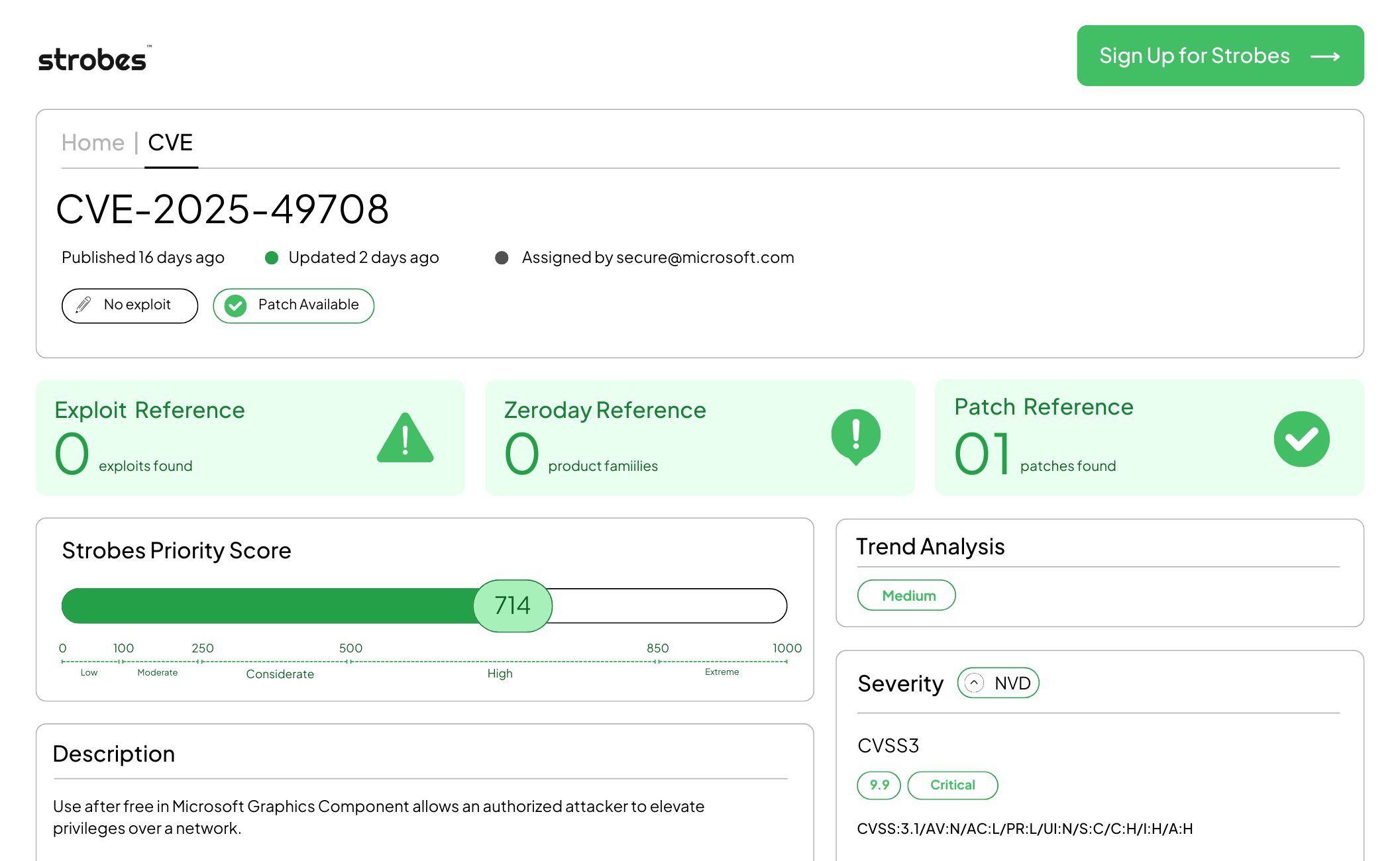
CVE-2025-49708 is a critical memory corruption vulnerability in the Microsoft Graphics Component. The flaw arises from a use-after-free condition that allows an attacker to manipulate memory and gain SYSTEM-level privileges. Microsoft classified this as an elevation of privilege vulnerability with a network attack vector and a CVSS score of 9.9. It was addressed in the October 2025 Patch Tuesday release.
CVE-2025-49708 Overview
| Field | Details |
| CVSS v3.1 | 9.9 (Critical) |
| Strobes Priority Score | 714 |
| Exploit Availability | No confirmed active exploitation at the time of disclosure |
| Patch Available | Yes, included in Microsoft’s October 2025 security updates |
| Vulnerability Type | Use-After-Free (Memory Corruption) → SYSTEM Privilege Escalation / Potential RCE |
| Affected Versions | Multiple supported Windows versions (Windows 10, 11, and Server builds before October 2025 updates) |
| CISA KEV Catalog | Not listed as of October 2025 |
Vulnerability Breakdown
CVE-2025-49708 exists due to improper memory handling in the Microsoft Graphics Component. When processing specially crafted graphics or rendering data, the component frees memory prematurely and later reuses the same pointer. This can lead to arbitrary memory manipulation.
A successful attacker can use this to elevate privileges to SYSTEM or, in specific configurations, achieve remote code execution if combined with other vulnerabilities or attack vectors.
Impact of Exploitation
If exploited, attackers could:
- Gain SYSTEM-level access on the affected Windows host.
- Escalate from a low-privileged user or sandboxed context to full administrative control.
- Perform credential theft, persistence setup, and lateral movement across endpoints.
- Compromise hypervisor hosts if the flaw is triggered from virtual machines, enabling potential guest-to-host escapes.
Mitigation & Patching
| Mitigation Step | Status / Action |
| Patch Availability | Apply Microsoft’s October 2025 security updates immediately. Confirm KB installation per system build. |
| Exploit Activity | No public exploit confirmed yet, but treat as high-risk due to technical exploitability. |
| Immediate Workaround | Restrict the exposure of systems running graphical workloads from untrusted networks. Disable unnecessary rendering or remote desktop services until patched. |
| Hardening Tip | Implement least-privilege policies, isolate high-risk workloads, and enforce virtualization boundary protections. |
| Detection | Monitor for unexpected crashes of graphics-related processes, abnormal SYSTEM-level process creation, and memory access anomalies detected by EDR tools. |
Why is this CVE in Our Top Picks of the Month?
This vulnerability stands out because it targets a fundamental Windows subsystem used across client and server devices. Its combination of local privilege escalation, possible remote exploitation, and potential VM escape makes it a critical threat for large enterprise environments. Even without confirmed active exploitation, its exploitability score and attack surface exposure justify immediate attention.
Strobes Recommendation
- Prioritize patching across all Windows assets that include the Microsoft Graphics Component.
- Begin rollout with virtualization hosts, VDI infrastructure, and high-value endpoints.
- If patching is delayed, enforce strict network isolation and minimize access to services handling graphical data.
- Continuously monitor telemetry for privilege escalation anomalies or unexpected SYSTEM-level process activity.
Bottomline
A high-severity use-after-free vulnerability in the Microsoft Graphics Component can allow SYSTEM-level privilege escalation or remote code execution. Microsoft’s October 2025 updates remediate this issue. Patch immediately and treat unpatched systems as high-risk until verified secure.
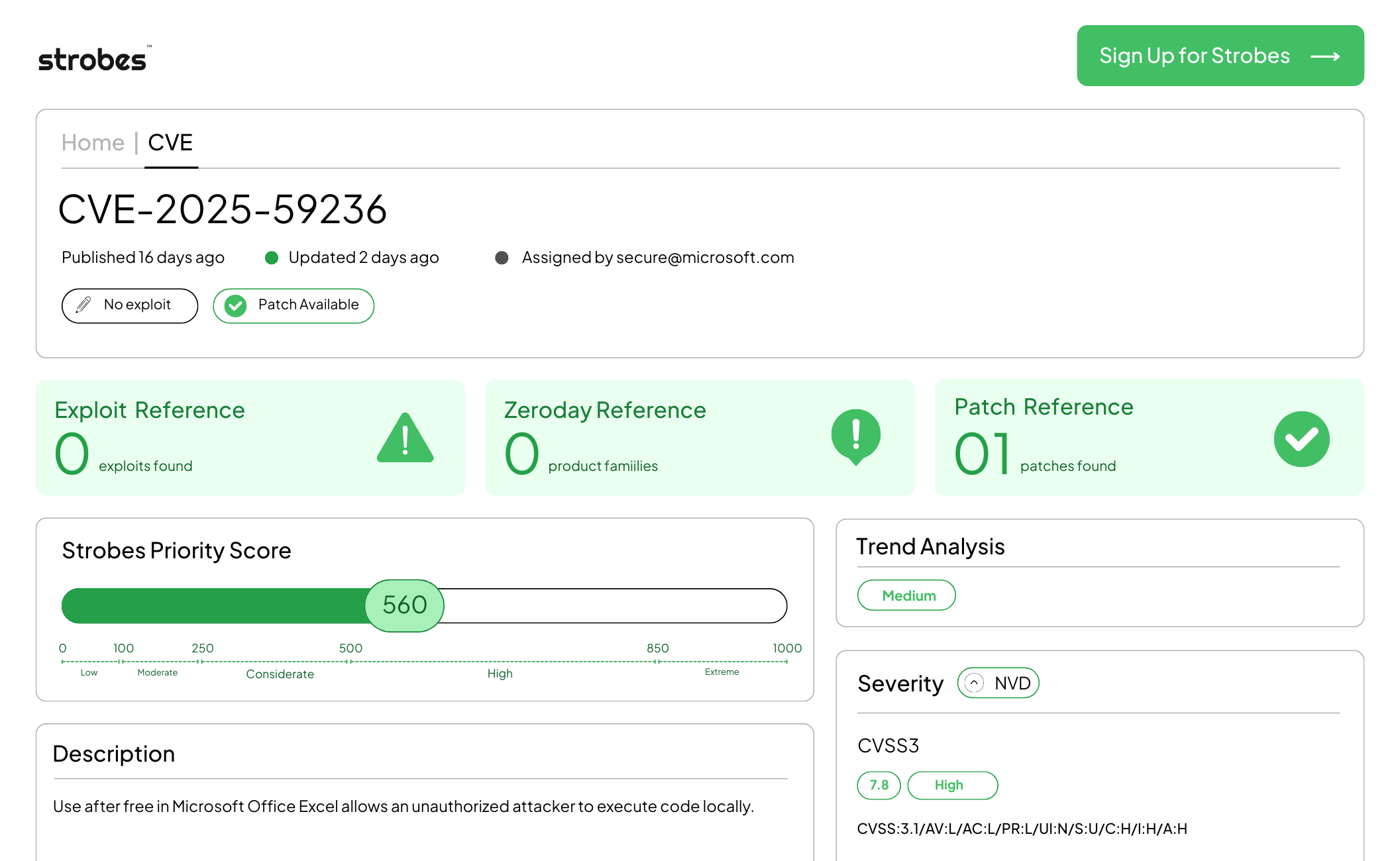
3. CVE-2025-59236 | Microsoft Excel Use-After-Free Vulnerability Leading to Remote Code Execution
CVE-2025-59236 is a critical use-after-free vulnerability in Microsoft Excel that allows a specially crafted spreadsheet to trigger memory corruption and achieve remote code execution when a user opens or previews the file. Successful exploitation can result in code running with the privileges of the logged-on user. Exploit chains observed in the wild combine phishing with malicious document delivery to gain initial footholds.
CVE-2025-59236 Overview
| Field | Details |
| CVSS v3.1 | 8.4 (High) |
| Strobes Priority Score | 655 |
| Exploit Availability | Proof of concept and exploit patterns circulating; weaponization observed in opportunistic phishing campaigns |
| Patch Available | Yes, Microsoft’s monthly security update includes the fix; deploy Office security updates promptly |
| Vulnerability Type | Use-After-Free → Remote Code Execution |
| Affected Versions | Microsoft Office Excel for Windows versions prior to patched releases; affected builds vary by channel |
Vulnerability Breakdown
CVE-2025-59236 arises from improper memory management when Excel parses certain object types inside spreadsheets. A crafted file can cause Excel to free memory prematurely and later reference that memory, creating a use-after-free condition. An attacker crafts a spreadsheet that triggers the condition and embeds payloads that get executed when the application processes the malformed object. The attack vector is user interaction, typically opening or previewing a file delivered by email or downloaded from a web location.
Impact of Exploitation
If exploited, likely outcomes include:
- Remote Code Execution: Execution of arbitrary code under the context of the user who opened the document.
- Credential Theft and Account Compromise: If the user has high privileges or saved credentials, attackers can escalate further.
- Lateral Movement: From an initial desktop foothold, adversaries can move across the network using harvested credentials and accessible services.
- Persistent Access: Malicious macros, scheduled tasks, or dropped binaries can provide long-term presence.
Mitigation & Patching
| Mitigation Step | Status / Action |
| Patch Availability | Fix included in Microsoft Office security update. Apply Office updates across endpoints quickly. |
| Exploit Activity | Exploit code and phishing campaigns reported. Treat as a high priority to remediate. |
| Immediate Workaround | Disable Office file preview in email clients and block common malicious attachment types at the mail gateway. Quarantine suspicious attachments. |
| Hardening Tip | Enforce application control for Office processes, disable macros by default, enable Protected View, and apply least privilege to user accounts. |
| Detection | Monitor for anomalous child processes spawned from Excel, unexpected network connections originating from user desktops, new persistence mechanisms, and unusual file creation in user profiles. |
| Hunt Suggestions | Search email gateway logs for deliveries of suspicious Excel files, inspect endpoint telemetry for Excel spawning cmd.exe or PowerShell, and look for recently created scheduled tasks or autorun entries tied to Office processes. |
Why is this CVE in Our Top Picks of the Month?
This vulnerability remains a priority because Office documents are a primary vector for initial compromise through phishing. The combination of a reliable exploitation primitive and active delivery in email campaigns means many organizations face immediate risk. The user interaction requirement makes user-focused controls and mail gateway defenses effective compensating measures while patches are deployed.
Strobes Recommendation
- Roll out the Microsoft Office update that contains the Excel fix to all managed endpoints without delay.
- Configure mail gateway rules to block or sandbox incoming Excel attachments unless explicitly allowed.
- Disable document preview in mail clients and webmail interfaces where feasible.
- Enforce Protected View and block unsigned macros by default. Use application control to restrict what Excel can spawn or execute.
- Hunt for indicators of compromise related to Excel-based delivery now. If you find evidence of exploitation, isolate affected hosts and perform endpoint forensics.
Bottomline
Use-after-free in Excel enables remote code execution via malicious spreadsheets. Exploit activity observed in phishing campaigns. Patch Office, tighten mail gateway and endpoint controls, and hunt for signs of compromise.
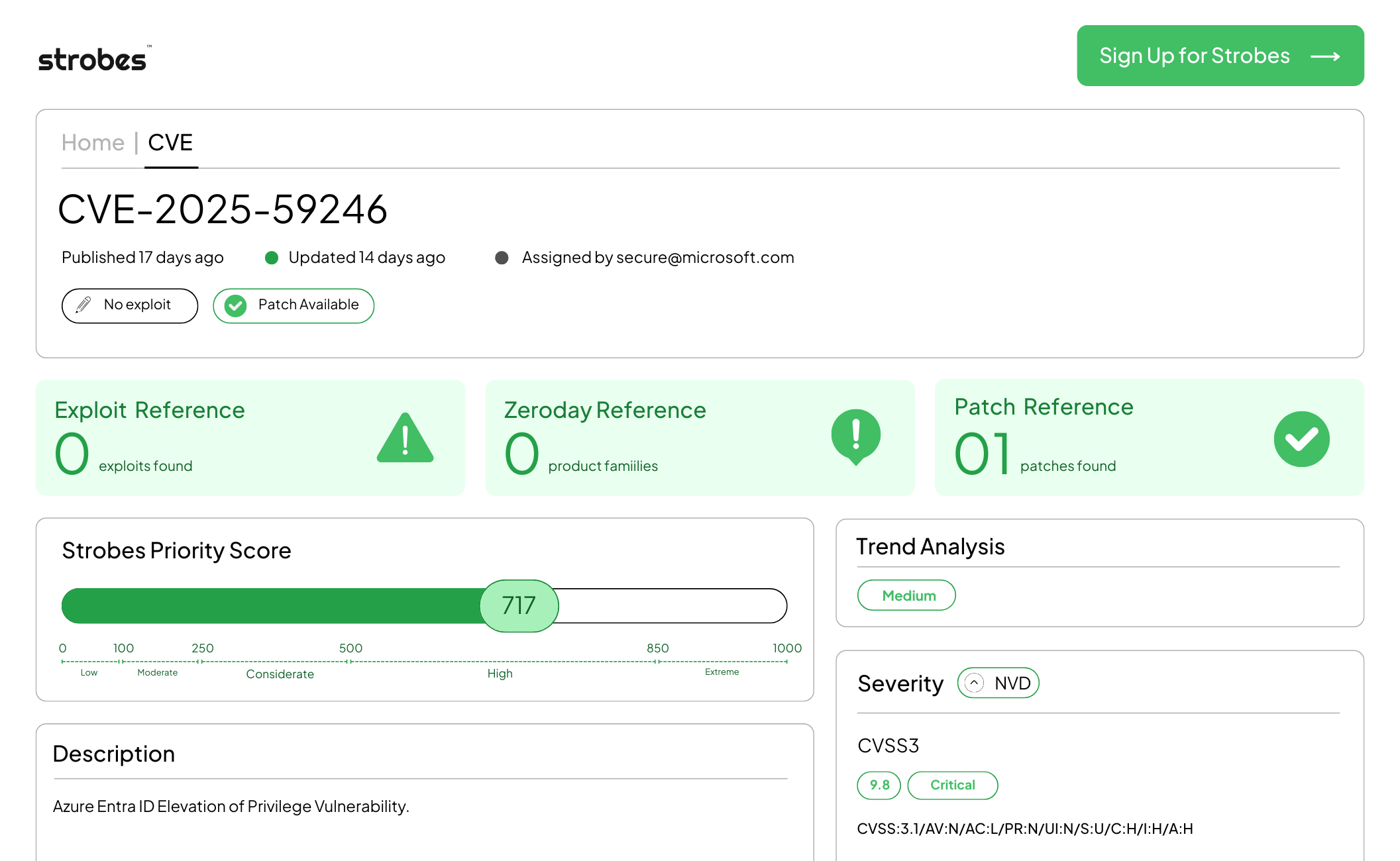
4. CVE-2025-59246 | Azure Entra ID Elevation of Privilege
CVE-2025-59246 is an elevation-of-privilege flaw in Azure Entra ID that lets an attacker gain higher permissions than intended within a tenant under specific conditions. The issue abuses weak authorization checks in a service path tied to identity management flows. A successful attack can convert low-privileged access into directory-level control.
CVE-2025-59246 Overview
| Field | Details |
| CVSS v3.1 | 9.8 (High) |
| Strobes Priority Score | 717 |
| Exploit Availability | No public exploit confirmed at publication time |
| Patch Available | Yes. Microsoft has addressed the issue in the October 2025 cycle |
| Vulnerability Type | Authorization logic flaw leading to privilege escalation |
| Affected Versions | Azure Entra ID tenants with impacted configurations prior to Microsoft’s fix |
| CISA KEV Catalog | Not listed as of October 2025 |
Vulnerability Breakdown
The vulnerability centers on insufficient authorization checks in a backend identity workflow. Under certain sequences of API calls and token contexts, the service accepts operations that should require higher privileges. An attacker with basic access inside a tenant can chain calls to elevate rights, assign privileged roles, or modify critical objects without proper approval gates.
Impact of Exploitation
If exploited, this vulnerability can lead to:
- Tenant-level privilege escalation with role assignment or directory write access
- Administrative access to user, app, and service principal objects
- Conditional Access policy tampering and MFA enrollment changes
- Persistence via rogue app registrations, consent grants, and service principals
Mitigation & Patching
| Mitigation Step | Status |
| Patch Availability | Addressed by Microsoft in the October 2025 updates |
| Configuration Review | Audit role assignments, group-based role eligibility, and privileged app consents |
| Immediate Workaround | Enforce Conditional Access for all admin actions, restrict legacy auth, and require MFA for privileged operations |
| Hardening Tip | Enable Privileged Identity Management for eligible roles and require just-in-time elevation with approval |
| Detection | Monitor Entra audit logs for unexpected role assignments, consent grants, policy edits, and anomalous app credential changes |
Why is this CVE in Our Top Picks of the Month?
Identity control failures are high-impact because one successful escalation can unlock broad access. This issue targets the core of cloud access governance. Even without a public exploit, low-noise abuse through legitimate APIs makes detection harder and increases risk for large tenants.
Strobes Recommendation
- Confirm whether your tenant was within scope before Microsoft’s fix and validate remediation status
- Review all permanent Global Administrator and Privileged Role Administrator assignments and convert them to eligible via PIM
- Require step-up authentication for role activation and sensitive operations
- Hunt for indicators using Entra audit logs: new privileged role assignments, new app consent grants, changes to Conditional Access, and unexpected service principal updates
- Lock down app registration and consent. Restrict who can create enterprise apps and who can grant tenant-wide consent
Bottomline
Cloud identity is a prime target. Treat CVE-2025-59246 as a priority by validating patch coverage, tightening privileged access flows, and reviewing directory changes for silent privilege creep.
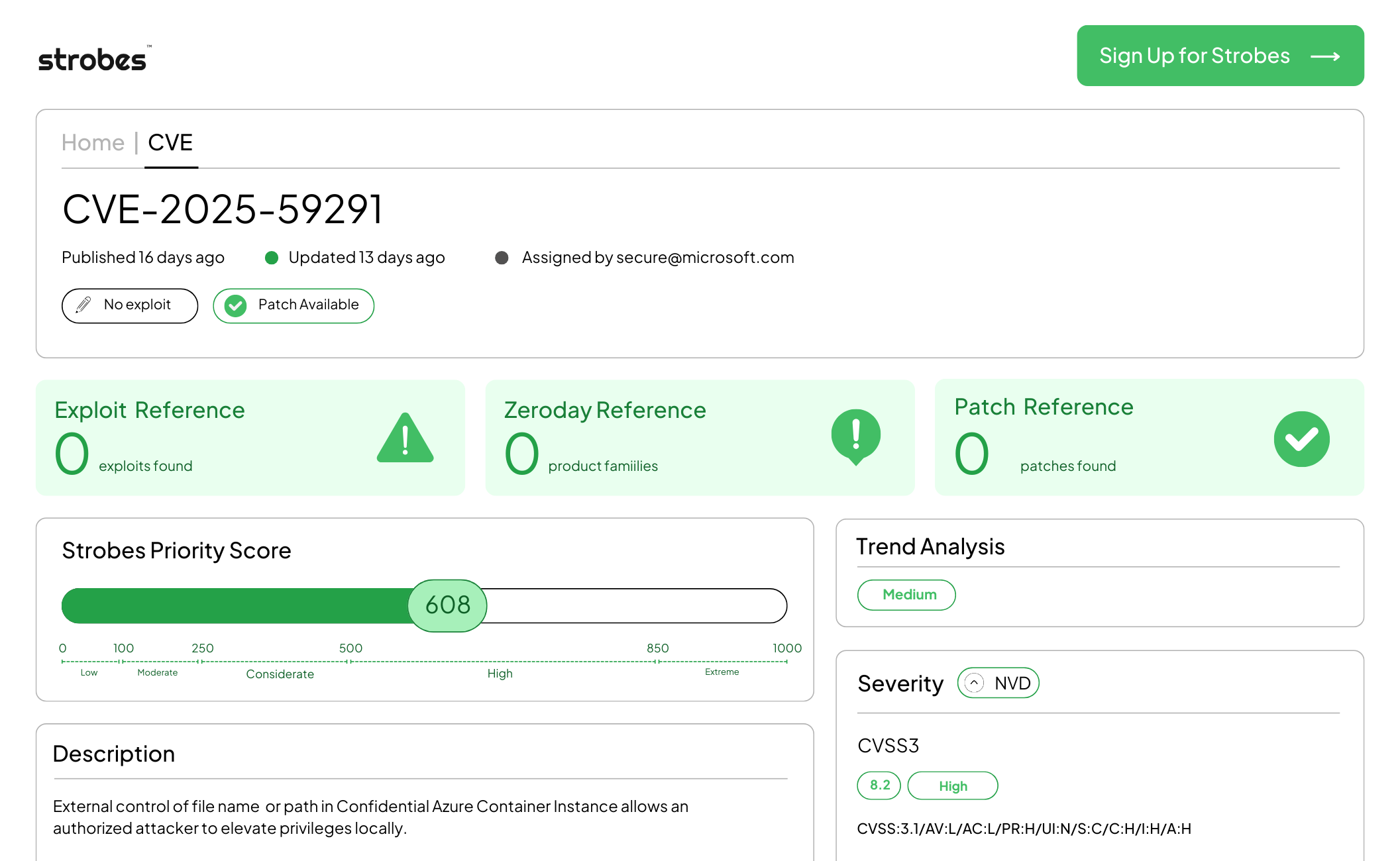
5. CVE-2025-59291| Azure Confidential Container Instances Privilege Escalation via Path Control Weakness
CVE-2025-59291 is a high-severity privilege escalation vulnerability in Azure Confidential Container Instances (CCI) that allows authenticated attackers to gain elevated privileges within the container environment. The flaw stems from improper path handling when mounting resources in confidential container workloads, enabling attackers to escape the container boundary or execute code with elevated permissions on the host.
CVE-2025-59291 Overview
| Field | Details |
| CVSS v3.1 | 8.2 (High) |
| Strobes Priority Score | 608 |
| Exploit Availability | No public exploit confirmed, but exploitation is considered feasible with local access |
| Patch Available | Yes – addressed in Azure’s October 2025 security updates |
| Vulnerability Type | Privilege Escalation (Container Escape via Path Control) |
| Affected Versions | Azure Confidential Container Instances prior to the October 2025 patch |
| CISA KEV Catalog | No |
Vulnerability Breakdown
CVE-2025-59291 occurs due to insufficient validation of file paths during resource mounting within Azure Confidential Container Instances. A user with access to a compromised or misconfigured container can craft symbolic links or manipulate mount points to access restricted directories on the host or adjacent containers. This flaw effectively breaks isolation guarantees and allows an attacker to escalate privileges from a confined environment to higher levels of control, including potential root-level access within the CCI host context.
Impact of Exploitation
If exploited, this vulnerability can result in:
- Privilege Escalation: Attacker gains elevated permissions within or beyond the container.
- Data Exposure: Access to confidential workloads and encryption keys meant to remain isolated.
- Container Escape: Breach of isolation between containers or between the container and host.
- Disruption of Confidential Workloads: Potential tampering with sensitive workloads or data in protected enclaves.
Mitigation & Patching
| Mitigation Step | Status |
| Patch Availability | Patched in Azure’s October 2025 update rollout for Confidential Containers |
| Exploit Activity | None publicly observed, but risk deemed high for insider or compromised container contexts |
| Immediate Workaround | Re-deploy updated container images; apply isolation policies to limit inter-container communication; verify configuration integrity |
| Hardening Tip | Enable strict host isolation, enforce minimal privilege for container users, and leverage Azure Defender for Containers for runtime anomaly detection |
| Detection | Monitor container logs for unauthorized mount operations, symlink creation attempts, or unexpected access to protected host paths |
Why is this CVE in Our Top Picks of the Month?
CVE-2025-59291 stands out because it challenges the integrity of confidential computing environments that are designed to safeguard sensitive workloads. Compromise of isolation boundaries in Azure CCI could lead to unauthorized access to encrypted data or confidential applications running in trusted execution environments. While no active exploitation has been confirmed, the nature of this flaw makes it a significant concern for organizations adopting confidential containers for regulated workloads.
Strobes Recommendation
- Confirm that your Azure Confidential Container Instances are running the patched version from the October 2025 update.
- Rebuild and redeploy affected workloads to ensure patched base images and configurations are in use.
- Review access policies and ensure that containers are not running with excessive privileges.
- Use Azure Policy to restrict the creation of privileged or noncompliant containers.
- Implement runtime monitoring to detect abnormal file system activity or container escapes.
Bottomline
A privilege escalation vulnerability in Azure Confidential Container Instances was caused by improper path validation. Enables container breakout and access to sensitive workloads. Patch applied in the October 2025 update. Validate that all confidential container workloads are rebuilt and redeployed after applying the fix.
Final Words
October’s CVEs are a reminder that unpatched systems quickly become entry points. The difference between being breached and being secure often comes down to hours, not weeks. Speed, context, and prioritization must now drive every vulnerability decision.
For continuous updates on new CVEs, threat activity, and severity scoring, visit the Strobes VI Platform.