Each month brings new vulnerabilities, and some aren’t just bugs, they’re invitations. The CVEs of May 2025 made headlines not just for their technical depth, but for how quickly they were exploited. From remote code execution flaws in widely used enterprise platforms to privilege escalation bugs in core Windows components, these aren’t issues you can afford to ignore.
This blog breaks down the top CVEs from May 2025 that demand your attention, complete with technical context, exploitation details, and mitigation steps. If you’re tracking real-world threats or planning your next patch cycle, this list is your shortlist. Let’s get into it.
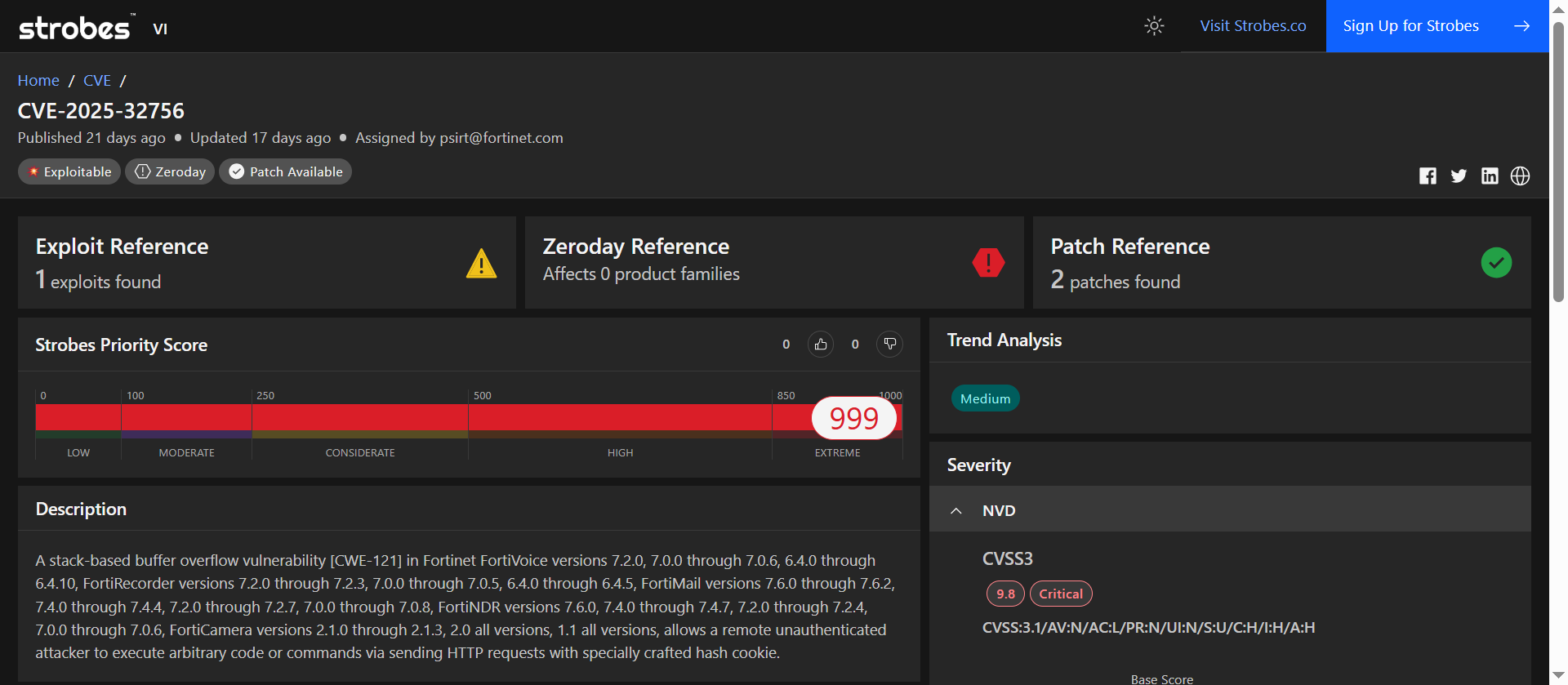
1. CVE-2025-32756: Remote Code Execution via Stack-Based Buffer Overflow in Multiple Fortinet Products
CVE-2025-32756 is a critical stack-based buffer overflow vulnerability affecting several Fortinet products, including FortiVoice, FortiMail, FortiNDR, FortiRecorder, and FortiCamera. This flaw allows remote, unauthenticated attackers to execute arbitrary code by sending specially crafted HTTP requests with malicious cookies.
The vulnerability arises from improper bounds checking during HTTP request processing, leading to a stack overflow that can overwrite critical memory addresses. Fortinet has confirmed active exploitation of this vulnerability in the wild, particularly targeting FortiVoice systems.
At a Glance
| Attribute | Value |
| Severity | Critical |
| CVSS v3.1 Score | 9.8 (AV:N/AC:L/PR:N/UI:N/S:U/C:H/I:H/A:H) |
| Exploitation Status | Actively exploited in the wild |
| Attack Vector | Network (Remote) |
| User Interaction | None |
| Privileges Required | None |
| Scope | Unchanged |
| Vulnerability Type | Stack-based Buffer Overflow (CWE-121) |
| Affected Products | FortiVoice, FortiMail, FortiNDR, FortiRecorder, FortiCamera |
Impact of Exploitation
- Full Remote Code Execution: Attackers can execute arbitrary code on the affected devices, potentially gaining full control.
- System Compromise: Successful exploitation may lead to complete system compromise, including data theft and unauthorized access.
- Persistence & Lateral Movement: Attackers may deploy malware, install cron jobs for credential theft, and scan internal networks.
- Service Disruption: Exploitation can disrupt services provided by the affected Fortinet products.
Technical Root Cause
The vulnerability stems from improper bounds checking during the processing of HTTP requests, specifically involving the handling of hash cookies. Attackers can exploit this flaw by sending specially crafted HTTP requests with malicious cookies, causing a stack overflow that allows overwriting critical memory addresses and executing arbitrary code with root-level privileges.
Affected Products & Versions
- FortiVoice: 6.4.0 through 6.4.10, 7.0.0 through 7.0.6, 7.2.0
- FortiMail: 7.0.0 through 7.0.8, 7.2.0 through 7.2.7, 7.4.0 through 7.4.4, 7.6.0 through 7.6.2
- FortiNDR: 7.0.0 through 7.0.6, 7.2.0 through 7.2.4, 7.4.0 through 7.4.7, 7.6.0
- FortiRecorder: 6.4.0 through 6.4.5, 7.0.0 through 7.0.5, 7.2.0 through 7.2.3
- FortiCamera: 1.1 (all versions), 2.0 (all versions), 2.1.0 through 2.1.3
Mitigation Guidance
- Apply Patches Immediately: Fortinet has released updates addressing this vulnerability. It’s imperative to upgrade affected products to the latest versions as specified in Fortinet’s advisory FG-IR-25-254.
- Disable HTTP/HTTPS Administrative Interfaces: If immediate patching isn’t feasible, disable the HTTP/HTTPS administrative interfaces to mitigate the attack vector.
- Review System Logs and Configurations: Check for unusual HTTP request patterns, unexpected system processes, or unauthorized user accounts. Specifically, review the ‘fcgi debugging’ setting, which, if enabled, could indicate compromise.
- Monitor for Indicators of Compromise (IoCs): Stay vigilant for any signs of exploitation and monitor systems for known IoCs associated with this vulnerability.
- Implement Network Segmentation and Access Controls: Restrict access to critical systems and services to minimize potential attack surfaces.
Why It Ranks Among the Top CVEs of May 2025?
- Confirmed Zero-Day: Actively exploited before the vendor issued a fix.
- High-Impact RCE: Enables full remote control of affected servers without user interaction.
- Wide Product Impact: Affects multiple Fortinet products commonly used in enterprise environments.
- Post-Exploitation Visibility: Incidents have shown real-world abuse with backdoors and full system compromise.
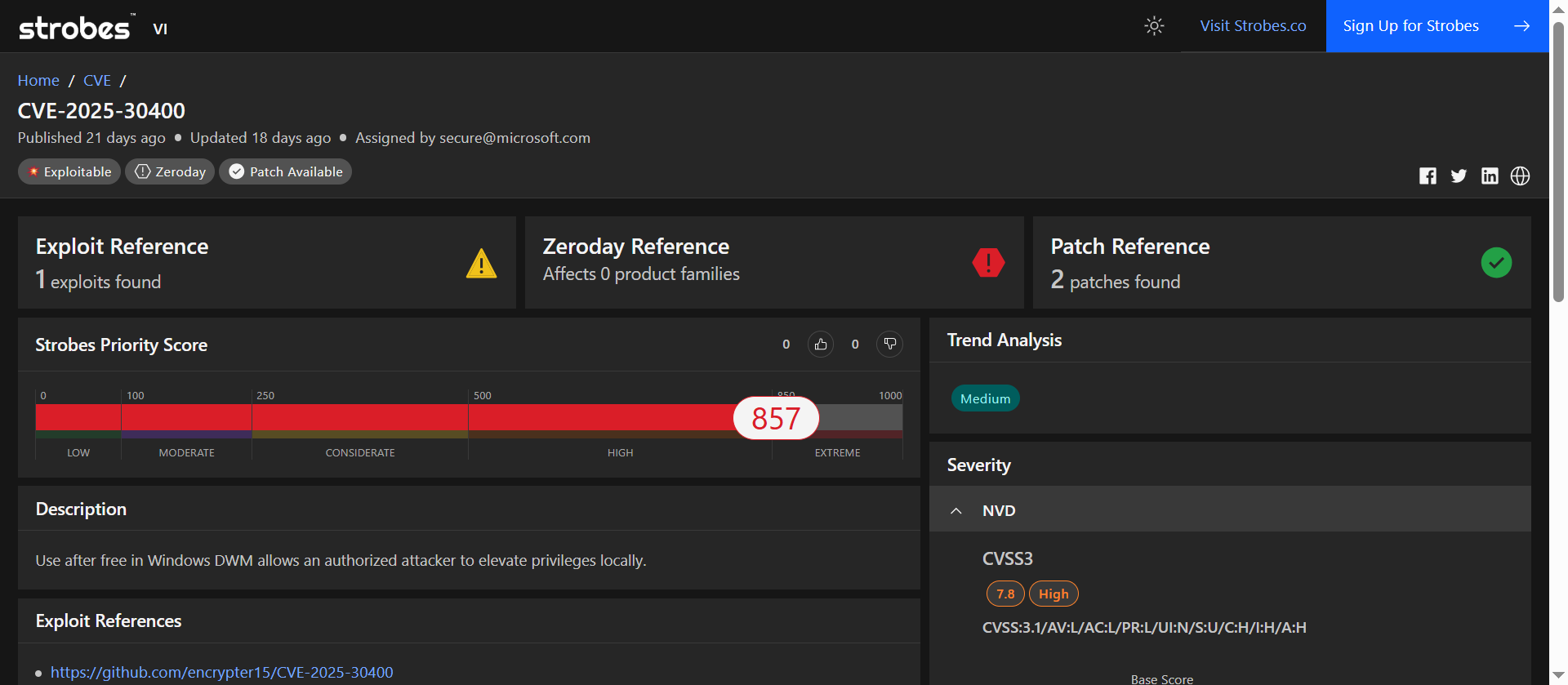
2. CVE-2025-30400: Privilege Escalation via Use-After-Free in Windows Desktop Window Manager (DWM) Core Library
CVE-2025-30400 is a critical elevation of privilege (EoP) vulnerability identified in the Desktop Window Manager (DWM) Core Library of Microsoft Windows. This flaw arises from a use-after-free condition within the dwmcore.dll component, which is responsible for managing graphical rendering in Windows environments. By exploiting this vulnerability, an authenticated local attacker can execute arbitrary code with SYSTEM-level privileges, potentially leading to full system compromise.
At a Glance
Attribute | Value |
| Severity | High |
| CVSS v3.1 Score | 7.8 (AV:L/AC:L/PR:L/UI:N/S:U/C:H/I:H/A:H) |
| Exploitation Status | Actively exploited in the wild |
| Attack Vector | Local (Authenticated user) |
| User Interaction | None |
| Privileges Required | Low |
| Scope | Unchanged |
| Vulnerability Type | Use-After-Free (CWE-416) |
| Affected Products | Windows 10 (versions before 10.0.17763.7314), Windows 11 (versions before 10.0.22621.5335), Windows Server 2022 (versions before 10.0.20348.3692), Windows Server 2025 (versions before 10.0.26100.4061) |
Impact of Exploitation
- Privilege Escalation: Attackers can elevate their privileges from a standard user to SYSTEM, granting them full control over the affected system.
- System Compromise: With SYSTEM-level access, attackers can install programs, view, change, or delete data, and create new accounts with full user rights.
- Persistence: Exploitation may allow attackers to maintain persistent access to compromised systems, facilitating further malicious activities.
Technical Root Cause
The vulnerability stems from improper handling of memory references in the DWM Core Library (dwmcore.dll). Specifically, the flaw is a use-after-free condition where the program continues to use a pointer after it has been freed, leading to memory corruption. This can be exploited by an attacker to execute arbitrary code in the context of the SYSTEM account.
Mitigation Guidance
- Apply Patches Immediately: Microsoft has released security updates addressing this vulnerability. Affected systems should be updated to the latest versions:
- Windows 10: Update to version 10.0.17763.7314 or later
- Windows 11: Update to version 10.0.22621.5335 or later
- Windows Server 2022: Update to version 10.0.20348.3692 or later
- Windows Server 2025: Update to version 10.0.26100.4061 or later
- Monitor for Indicators of Compromise (IoCs):
- Unusual behavior of dwm.exe processes
- Unexpected privilege escalations
- Anomalous system activities that could indicate exploitation
- Implement Endpoint Detection and Response (EDR) Solutions: Deploy EDR tools capable of detecting and alerting on suspicious activities related to DWM and privilege escalation attempts.
Why It Ranks Among the Top CVEs of May 2025?
- Active Exploitation: The vulnerability has been actively exploited in the wild, indicating a clear and present danger to unpatched systems.
- High Impact: Successful exploitation grants attackers SYSTEM-level privileges, leading to complete system compromise.
- Wide Affected Base: The flaw affects multiple versions of Windows, including both client and server editions, increasing the potential attack surface.
- Integration into Attack Chains: The vulnerability has been incorporated into post-exploitation toolchains, facilitating lateral movement and persistence within networks.
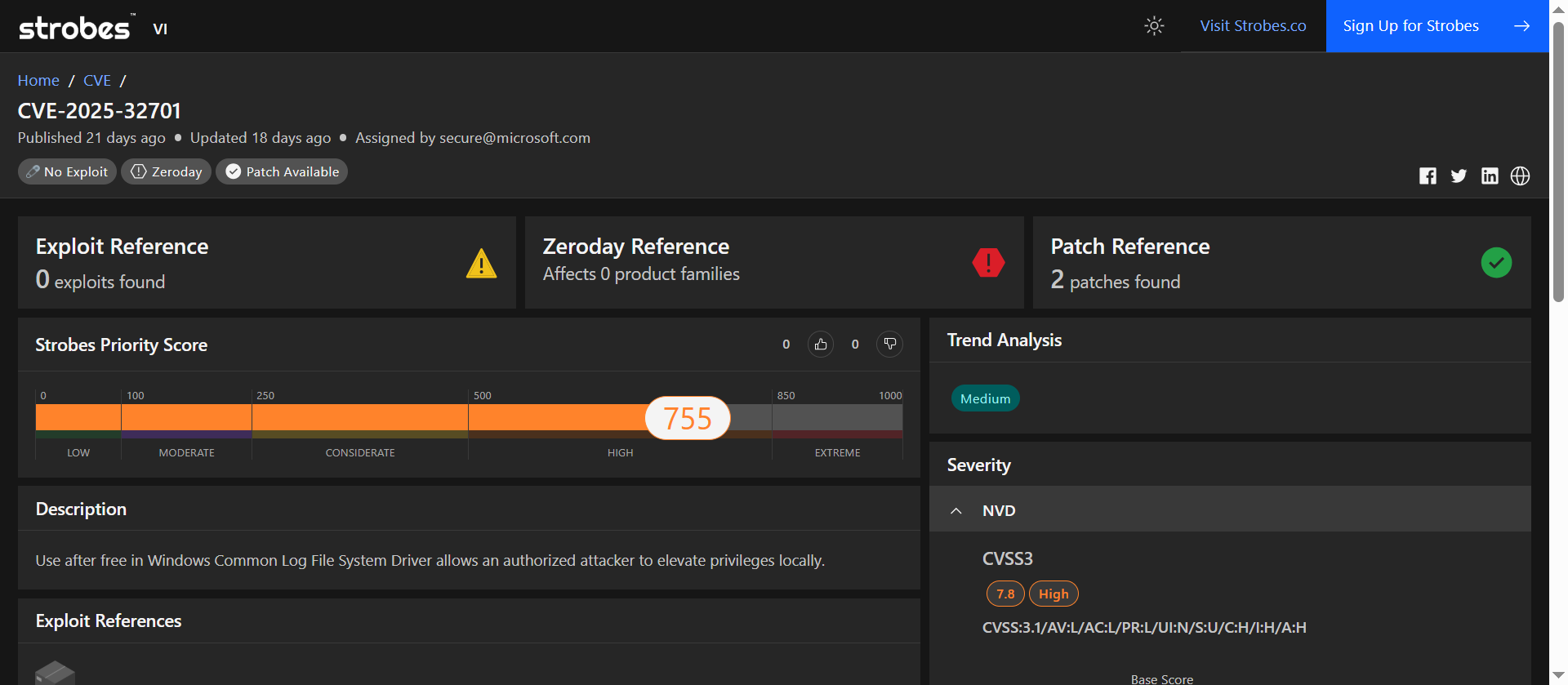
3. CVE-2025-32701: Privilege Escalation via Use-After-Free in Windows CLFS Driver
CVE-2025-32701 is a critical vulnerability identified in the Windows Common Log File System (CLFS) driver. This flaw arises from improper memory management, specifically a use-after-free condition, which can be exploited by local attackers to elevate privileges to SYSTEM level. The vulnerability has been actively exploited in the wild, prompting its inclusion in CISA’s Known Exploited Vulnerabilities Catalog.
At a Glance
| Attribute | Value |
| Severity | High |
| CVSS v3.1 Score | 7.8 (AV:L/AC:L/PR:L/UI:N/S:U/C:H/I:H/A:H) |
| Exploitation Status | Actively exploited in the wild |
| Attack Vector | Local |
| User Interaction | None |
| Privileges Required | Low |
| Scope | Unchanged |
| Vulnerability Type | Use-After-Free (CWE-416) |
| Affected Products | Multiple Windows versions prior to May 2025 updates |
Impact of Exploitation
- Privilege Escalation: Allows attackers with low-level access to gain SYSTEM-level privileges.
- Ransomware Deployment: Facilitates the installation of ransomware, as observed in attacks linked to the PipeMagic malware.
- System Compromise: Enables attackers to execute arbitrary code in kernel mode, leading to full system control.
- Persistence and Lateral Movement: Attackers can maintain long-term access and move laterally within networks.
Technical Root Cause
The vulnerability stems from a use-after-free condition in the CLFS driver. Specifically, the driver improperly handles memory deallocation, allowing attackers to:
- Trigger specific log operations (e.g., CreateLogFile, AddLogContainer) to free memory.
- Reallocate the freed memory with controlled data via heap spraying.
- Exploit the dangling pointer to execute arbitrary code with elevated privileges.
This exploit bypasses kernel protections like Kernel Address Space Layout Randomization (KASLR) due to predictable object layouts .
Mitigation Guidance
- Apply Patches Immediately: Microsoft has released patches addressing this vulnerability in the May 2025 security updates. Ensure all systems are updated accordingly.
- Monitor for Indicators of Compromise (IoCs):
- Unusual svchost.exe interactions with clfs.sys.
- Unexpected CLFS API usage.
- Presence of the PipeMagic malware.
- Implement Endpoint Detection and Response (EDR): Utilize EDR solutions to detect and respond to suspicious activities related to this vulnerability.
- Restrict Access: Limit user permissions to the minimum necessary to reduce potential exploitation avenues.
Why It Ranks Among the Top CVEs of May 2025?
- Active Exploitation: Confirmed zero-day with real-world attacks observed.
- High Impact: Enables attackers to gain full control over affected systems.
- Wide Affected Range: Impacts multiple versions of Windows, including both client and server editions.
- Facilitates Ransomware Attacks: Exploitation has been linked to ransomware deployments, increasing its severity.
Trusted by leading enterprises like, GHX, Zoho, Darwinbox, Tricenties, and SHL
Strobes helped organizations continuously manage threats, reduce vulnerabilities, and stay compliant, powered by AI-driven security expertise.
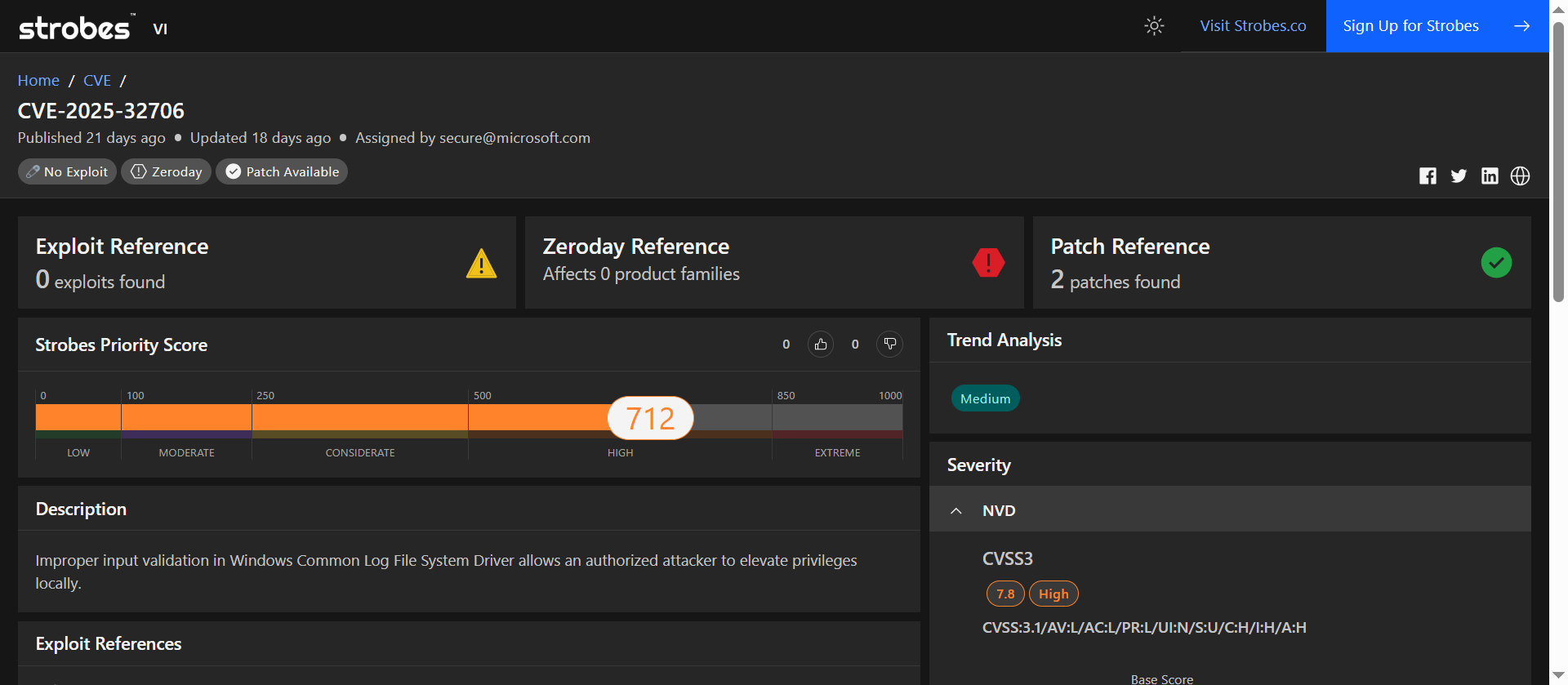
4. CVE-2025-32706: Heap-Based Buffer Overflow in Microsoft Windows CLFS Driver Enables Privilege Escalation
CVE-2025-32706 is a heap-based buffer overflow vulnerability discovered in the Common Log File System (CLFS) driver used across multiple versions of Microsoft Windows. The CLFS driver is a low-level system component responsible for maintaining transaction logs for applications and system services.
The vulnerability arises from improper memory handling during the processing of specially crafted log file operations. An attacker with local access can exploit this flaw to trigger a heap buffer overflow, leading to memory corruption and eventually execution of arbitrary code with elevated privileges.
This vulnerability was observed being actively exploited in the wild, primarily as part of privilege escalation chains used by ransomware and espionage-focused threat actors. It was added to CISA’s Known Exploited Vulnerabilities (KEV) catalog in May 2025.
At a Glance
| Attribute | Value |
| Severity | High |
| CVSS v3.1 Score | 7.8 (AV:L/AC:L/PR:L/UI:N/S:U/C:H/I:H/A:H) |
| Exploitation Status | Actively exploited in the wild |
| Attack Vector | Local (Requires access to a vulnerable system) |
| User Interaction | None |
| Privileges Required | Low |
| Scope | Unchanged |
| Vulnerability Type | Heap-Based Buffer Overflow (CWE-122) |
| Affected Products | Microsoft Windows 10, 11, and Windows Server versions |
Impact of Exploitation
- Privilege Escalation: Allows attackers to execute code in kernel mode, enabling full system control.
- Persistence Mechanism: Post-exploitation, attackers can install rootkits or bypass security controls like EDR.
- Evasion of User-Level Restrictions: Even low-privileged users can gain SYSTEM-level access if the exploit succeeds.
- Support for Chained Attacks: Commonly used in combination with browser or phishing-based initial access to gain a deep foothold.
Technical Root Cause
The vulnerability resides in how the CLFS driver allocates and manages heap memory when processing specific log file records. Insufficient boundary checks allow an attacker to supply data that exceeds expected size limits, causing a heap-based buffer overflow.
When this overflow occurs, the attacker can manipulate adjacent memory, overwrite control structures, and redirect execution flow. Since the CLFS driver operates in kernel space, a successful exploit leads to code execution with NT AUTHORITY\SYSTEM privileges.
This class of vulnerability is particularly dangerous because:
- It does not require user interaction.
- It can bypass user-mode protections.
- It can evade detection without proper kernel-level monitoring.
Mitigation Guidance
Apply Security Updates Immediately:
Microsoft has released security patches addressing this vulnerability in the May 2025 Patch Tuesday rollout. Organizations should prioritize updating affected Windows systems, especially in high-risk environments like virtualized infrastructure or shared endpoints.
Harden Local Access:
- Implement User Account Control (UAC) restrictions to minimize unnecessary local privilege access.
- Disable or restrict access to legacy log management APIs or features reliant on CLFS where feasible.
Detection and Monitoring:
- Look for anomalous behavior such as:
- Unexpected execution of signed Microsoft binaries with unusual parameters.
- Kernel-level process injections.
- Use of signed drivers to load unsigned kernel code.
- Deploy kernel telemetry and behavior-based EDRs capable of detecting memory tampering or privilege escalation attempts.
Isolate High-Value Assets:
- Segment endpoints with administrative tools.
- Disable unnecessary services that interface with CLFS if operationally permissible.
Why It Ranks Among the Top CVEs of May 2025?
- Confirmed Exploitation: Incorporated in active attacker toolkits with widespread use.
- High Privilege Impact: Converts local access into SYSTEM control, a key step in ransomware and persistent APT operations.
- Trusted Component Abuse: Targets a core Windows driver trusted by the OS, making detection and mitigation more complex.
- Silent Weaponization: Exploited without user action, and difficult to identify without advanced monitoring.
- Historical Relevance: Follows a trend of CLFS driver bugs (e.g., CVE-2023-28252), underlining a systemic weak spot.
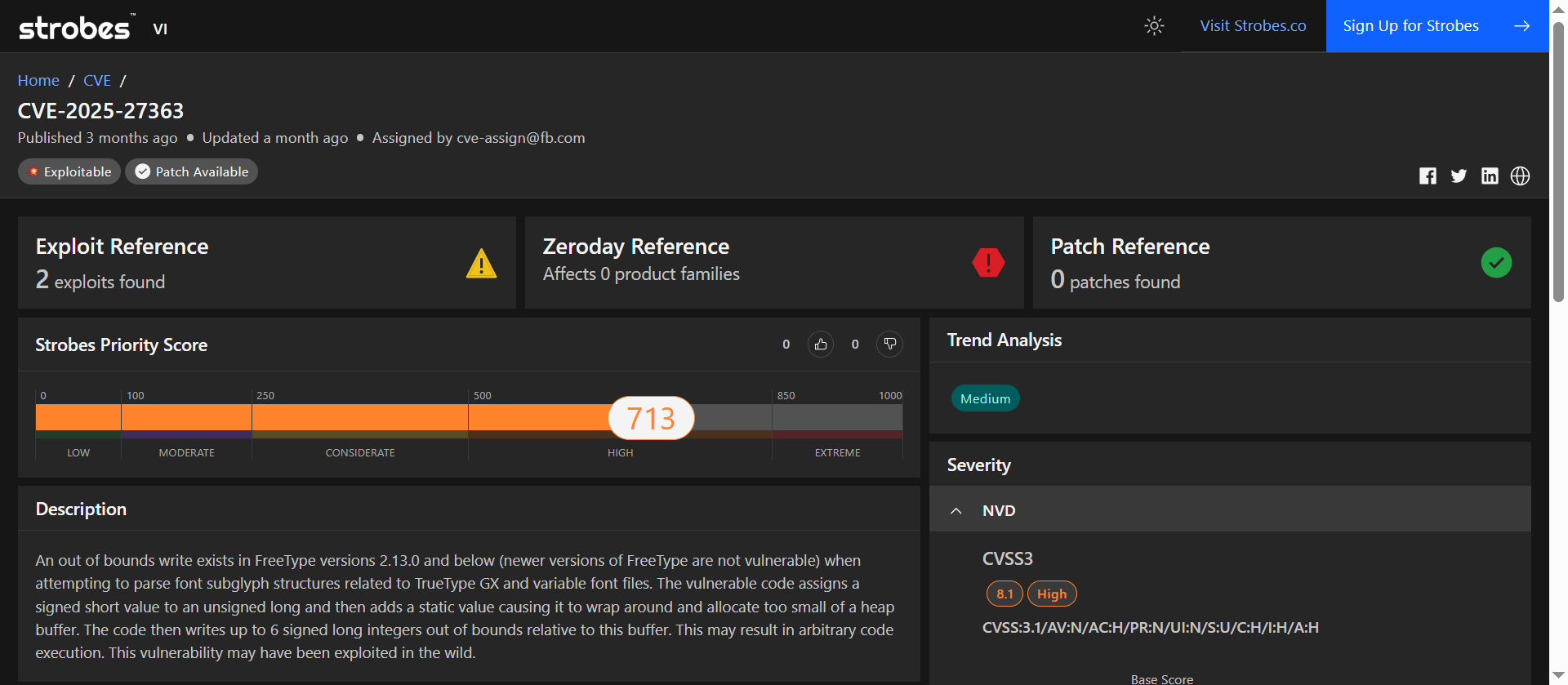
5. CVE-2025-27363: Heap Buffer Overflow in FreeType Library
CVE-2025-27363 is a high-severity vulnerability identified in FreeType versions up to 2.13.0. The flaw arises from improper memory allocation during the parsing of font subglyph structures, particularly in TrueType GX and variable font files.
Specifically, a signed short value is incorrectly assigned to an unsigned long, leading to an integer wraparound. This miscalculation results in the allocation of an undersized heap buffer, into which up to six signed long integers are subsequently written out of bounds. Such a condition can be exploited to achieve arbitrary code execution.

At a Glance
| Attribute | Value |
| Severity | High |
| CVSS v3.1 Score | 8.1 (AV:N/AC:H/PR:N/UI:N/S:U/C:H/I:H/A:H) |
| Exploitation Status | May have been exploited in the wild |
| Attack Vector | Network (Remote) |
| User Interaction | None |
| Privileges Required | None |
| Scope | Unchanged |
| Vulnerability Type | Out-of-Bounds Write (CWE-787) |
| Affected Products | FreeType versions ≤ 2.13.0 |
Impact of Exploitation
- Arbitrary Code Execution: Attackers can execute malicious code on systems utilizing vulnerable FreeType versions.
- Potential for Zero-Click Exploits: Exploitation can occur without user interaction, making it particularly dangerous in scenarios like rendering malicious fonts in documents or web pages.
- Wide Attack Surface: Given FreeType’s integration into various platforms, including Android, Linux distributions, and major browsers, the vulnerability poses a significant risk across multiple systems.
Technical Root Cause
The vulnerability is rooted in the load_truetype_glyph function within FreeType’s ttgload.c file. Here, a signed short value is erroneously assigned to an unsigned long variable. When a static value is added to this variable, it causes an integer wraparound, leading to the allocation of an inadequately sized heap buffer.
Subsequent operations write multiple signed long integers beyond the bounds of this buffer, culminating in a heap buffer overflow.
Mitigation Guidance
- Upgrade FreeType: Update to FreeType version 2.13.3 or later, where this vulnerability has been addressed.
- Apply Vendor Patches: Ensure that operating systems and applications incorporating FreeType have applied the necessary patches. For instance, Debian and Ubuntu have released updates to rectify this issue.
- Monitor for Indicators of Compromise (IoCs): Be vigilant for unusual activities, such as unexpected font rendering behaviors or crashes, which may indicate exploitation attempts.
Why It Ranks Among the Top CVEs of May 2025?
- Potential Active Exploitation: Reports suggest that this vulnerability may have been exploited in the wild, underscoring its severity.
- Zero-Click Exploitation Possibility: The flaw can be triggered without any user interaction, increasing its potential impact.
- Extensive Impact Across Platforms: FreeType’s widespread use means that a vast array of systems and applications are at risk.
- Delayed Patch Adoption: Despite the availability of fixes, some distributions and applications may still be running vulnerable versions, prolonging exposure.
Conclusion
The CVEs of May 2025 proved that attackers aren’t waiting around for slow patch cycles or missed updates. The vulnerabilities highlighted in this roundup weren’t just theoretically dangerous, they were actively used to gain access, escalate privileges, and deploy persistent threats across environments that thought they were covered.
If any of these CVEs match software in your stack, it’s not a question of priority, it’s a question of exposure. Patch fast, audit configurations, and revisit your threat detection rules. Because in cases like these, reacting late often costs more than staying prepared.
Want the full picture? Explore Strobes’ Vulnerability Intelligence platform for deeper insights into trending exploits, active threats, and how they map to your environment.
Sources
1. CVE-2025-32756 – Fortinet Multiple Products Stack-Based Buffer Overflow
- NVD Entry: Provides technical details and CVSS score.
nvd.nist.gov
2. CVE-2025-30400 – Microsoft Windows DWM Core Library Use-After-Free
- Microsoft Security Update Guide: Official advisory with patch information.
msrc.microsoft.com - NVD Entry: Detailed vulnerability information and CVSS score.
nvd.nist.gov
3. CVE-2025-32701 – Microsoft Windows Common Log File System (CLFS) Driver Use-After-Free
- Microsoft Security Update Guide: Official advisory with remediation steps.
msrc.microsoft.comnvd.nist.gov+11msrc.microsoft.com+11msrc.microsoft.com+11 - NVD Entry: Comprehensive vulnerability details.
nvd.nist.govcvedetails.com - CISA KEV Catalog: Inclusion in Known Exploited Vulnerabilities list.
cisa.gov
4. CVE-2025-32706 – Microsoft Windows CLFS Driver Heap-Based Buffer Overflow
- Microsoft Security Update Guide: Official patch and vulnerability information.
msrc.microsoft.combalbix.com+2blog.qualys.com+2zeropath.com+2 - NVD Entry: Technical details and CVSS metrics.
nvd.nist.gov - CISA KEV Catalog: Listing among actively exploited vulnerabilities.
cisa.govcve.mitre.org
5. CVE-2025-27363 – Heap Buffer Overflow in FreeType Library
- NVD Entry: Detailed vulnerability description and impact assessment.
nvd.nist.govtenable.com+17nvd.nist.gov+17nvd.nist.gov+17 - Red Hat Advisory: Impact on Red Hat products and recommended actions.
access.redhat.com
Related Reads: