As September comes to a close, we’ve seen some fresh vulnerabilities emerge that demand immediate attention. From critical flaws in widely used software to newly discovered loopholes that could impact security across industries, these CVEs have been making waves. Whether you’re securing networks or locking down sensitive systems, staying on top of these threats is crucial. Let’s break down the top five CVEs of September and why they need to be on your radar right now!
1. CVE-2024-43491 | Microsoft Windows Update Remote Code Execution Vulnerability
CVE-2024-43491 is a critical remote code execution vulnerability in Microsoft Windows Update, specifically affecting the Servicing Stack of Windows 10 Version 1507. This vulnerability allows attackers to exploit previously mitigated vulnerabilities due to a rollback of fixes in a March 2024 update.
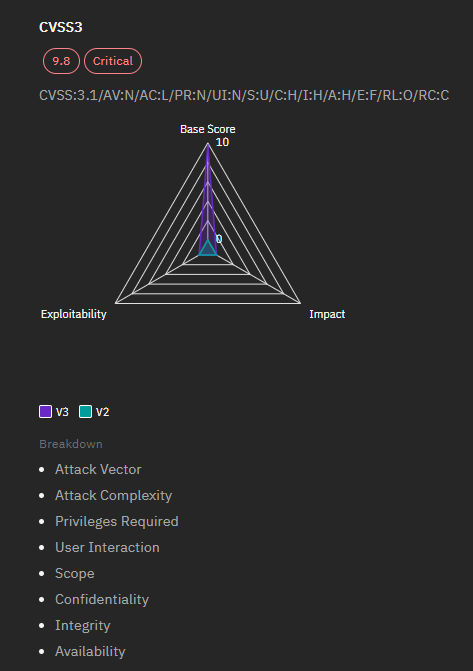
Details of the Vulnerability
By exploiting this vulnerability, an attacker can manipulate the application to process a malicious PHP file instead of the intended one. This could lead to various malicious activities, including data theft, system compromise, or denial of service.
- Severity: Critical
- CVSS Score: 9.8
- Impact: High (affecting Confidentiality, Integrity, and Availability)
- Affected Products: Windows 10 Version 1507 (including Windows 10 Enterprise 2015 LTSB and Windows 10 IoT Enterprise 2015 LTSB)
- Vulnerability Type: Remote Code Execution (RCE)
- Exploitability: Functional; exploitation is detected and has been observed in the wild.
- Authentication: None required for exploitation.
Exploitation
The vulnerability allows an attacker to exploit systems running the affected versions of Windows 10 by leveraging rolled-back fixes from previous updates. Successful exploitation could lead to remote code execution, thereby allowing attackers to execute arbitrary code on the target system without user interaction.
Mitigation
To mitigate this vulnerability, it is essential to:
- Identify if any systems are running Windows 10 Version 1507.
- Install the September 2024 Servicing Stack Update (SSU KB5043936).
- Follow up with the September 2024 Windows Security Update (KB5043083) immediately after applying the SSU.
- Verify that the system version is updated to at least 10.0.10240.20766
Additional Information
This CVE has been added to CISA’s Known Exploited Vulnerabilities Catalog, indicating its significance and the urgency for remediation. It is critical for organizations using affected versions of Windows to apply patches promptly to avoid potential exploitation.
Timeline
- September 10, 2024: CVE disclosed and advisory published.
- September 12, 2024: Mitigation steps released.
- October 1, 2024: Deadline for remediation as per CISA guidelines
2. CVE-2024-38194: Azure Web Apps Elevation of Privilege Vulnerability
CVE-2024-38194 is a Critical Remote Code Execution (RCE) vulnerability affecting Azure Web Apps, allowing authenticated attackers to exploit an authorization flaw.
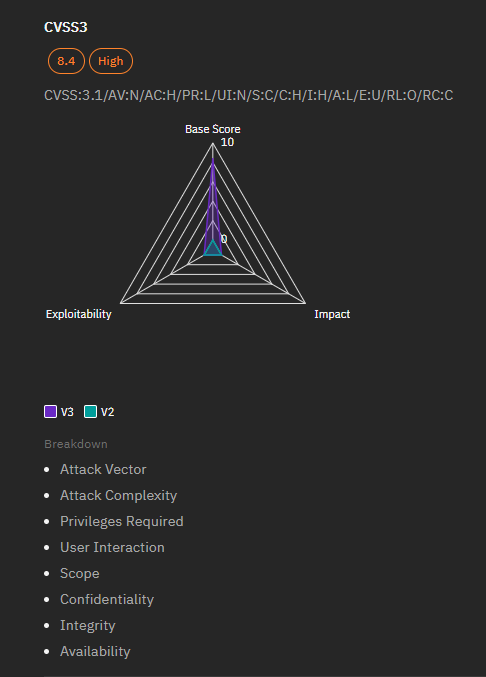
Details of the Vulnerability
- Severity: Critical
- CVSS Score: 8.4
- Impact: An attacker with valid credentials can gain elevated permissions across a network, potentially leading to unauthorized access or control.
- Affected Products: Azure Web Apps
- Vulnerability Type: Improper Authorization
- Exploitability: Requires valid credentials; can be exploited over a network.
- Authentication: Yes, valid credentials are necessary for exploitation.
Exploitation
An authenticated attacker can leverage the improper authorization vulnerability to elevate their privileges within the Azure Web Apps environment, potentially compromising sensitive data and operations.
Mitigation
Microsoft has fully addressed this vulnerability within the Azure infrastructure, and users of the affected service do not need to take further action. The publication of this CVE is intended for transparency regarding the issue and its resolution.
Additional Information
This vulnerability underscores the importance of robust authorization mechanisms in cloud services to prevent privilege escalation attacks.
Timeline
- Published Date: September 10, 2024 (during Patch Tuesday)
- Resolution Date: Addressed immediately by Microsoft in the same patch cycle.
3. CVE-2024-37341: Microsoft SQL Server Elevation of Privilege Vulnerability
CVE-2024-37341 is a Microsoft SQL Server Elevation of Privilege Vulnerability that allows unauthorized users to gain elevated access to resources.
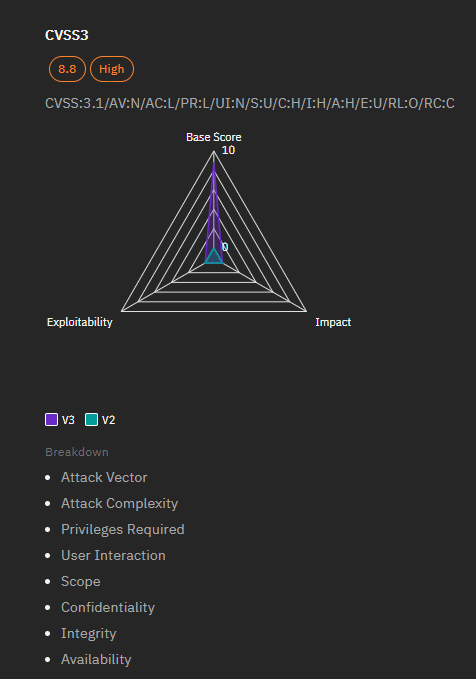
Details of the Vulnerability
- Severity: High
- CVSS Score: 8.8 (CVSS v3.0)
- Impact: Elevation of Privilege
- Affected Products: Microsoft SQL Server 2017 and 2019
- Vulnerability Type: Access Control Weakness
- Exploitability: Exploitable by unauthorized actors due to inadequate access restrictions
- Authentication: Requires authentication to exploit
Exploitation
Attackers can exploit this vulnerability by leveraging access control weaknesses, potentially allowing them to read sensitive information, execute commands, and evade detection.
Mitigation
Immediate application of security updates provided by Microsoft is recommended to address this vulnerability and prevent potential exploitation.
Additional Information
For more details, refer to the Microsoft Security Response Center and the National Vulnerability Database.
Timeline:
- Updated: September 10, 2024
- Published: September 10, 2024
4. CVE-2024-21416: Windows TCP/IP Remote Code Execution Vulnerability
CVE-2024-21416 is a Windows TCP/IP Remote Code Execution Vulnerability that allows attackers to execute arbitrary code on affected systems.
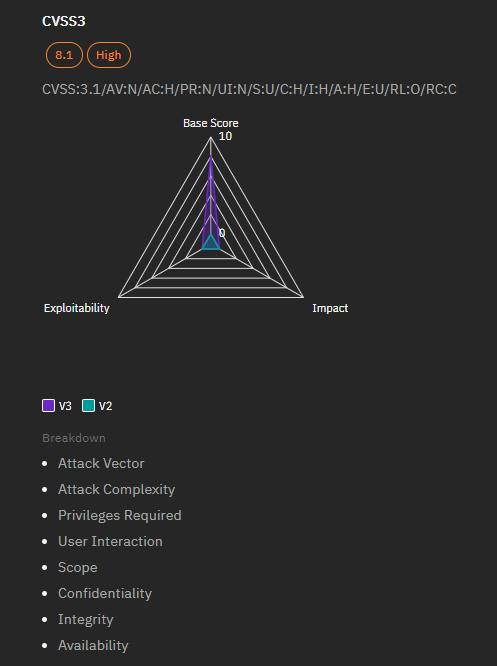
Details of the Vulnerability
- Severity: Critical
- CVSS Score: 9.8 (CVSS 3.0)
- Impact: Successful exploitation could allow an attacker to execute arbitrary code, potentially leading to full system compromise.
- Affected Products:
- Windows 10 (versions up to 10.0.17763.6293)
- Windows 11 (versions up to 10.0.22000.3197)
- Windows Server 2019 (versions up to 10.0.17763.6293)
- Windows Server 2022 (versions up to 10.0.20348.2700)
- Vulnerability Type: Remote Code Execution
- Exploitability: Low probability of exploitation activity in the next 30 days (EPSS score: 0.09%)
- Authentication: No authentication required for exploitation.
Exploitation
The vulnerability can be exploited through a heap overflow condition, allowing attackers to overwrite memory and execute arbitrary code without user interaction.
Mitigation
Microsoft has released security updates to address this vulnerability. Users are advised to apply these updates promptly to mitigate risks associated with potential exploitation.
Additional Information
For detailed information and references, users can consult the Microsoft Security Response Center and the National Vulnerability Database.
Timeline
- Published Date: September 10, 2024
- Updated Date: September 20, 2024.
5. CVE-2024-38018: Microsoft SharePoint Server RCE Vulnerability
CVE-2024-38018 is a Remote Code Execution Vulnerability in Microsoft SharePoint Server, allowing attackers to execute arbitrary code on affected systems.
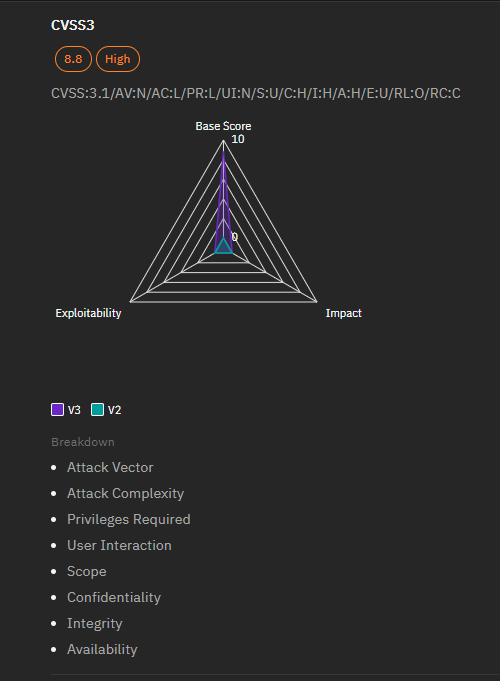
Details of the Vulnerability:
- Severity: High
- CVSS Score: 8.8 (CVSS 3.1)
- Impact: High confidentiality, integrity, and availability impact. Successful exploitation can lead to full system compromise.
- Affected Products: Microsoft SharePoint Server 2016 and 2019
- Vulnerability Type: Remote Code Execution
- Exploitability: Low complexity with low privileges required for exploitation.
- Authentication: Requires authentication to exploit.
Exploitation
The vulnerability arises from the deserialization of untrusted data without adequate validation, which can be exploited remotely by authenticated users to execute arbitrary code on the server.
Mitigation
Microsoft has released security updates to address this vulnerability. Users are advised to apply these updates promptly to mitigate risks associated with this vulnerability.
Additional Information
The vulnerability was published on September 10, 2024, and updated shortly thereafter. The exploit prediction scoring system (EPSS) indicates a low probability of exploitation activity in the near term (0.05%) but highlights the need for immediate attention due to the potential impact.
Timeline
- Published: September 10, 2024
- Updated: September 18, 2024
Final Words
These vulnerabilities highlight the importance of staying proactive and informed in the face of emerging threats. Whether you’re patching systems or enhancing your defense strategies, addressing these CVEs swiftly is critical to maintaining security. For more detailed information on these CVEs and strategies to manage them effectively, explore how Strobes VI platform can help you stay ahead of the game.