During our recent security assessments across multiple clients, we discovered a concerning pattern: many companies are unknowingly exposing their customers’ sensitive payment information through a simple yet critical misconfiguration in their Juspay integration. This issue stems from the improper use of dummy email domains. Here’s what we found and why it matters.
The Discovery
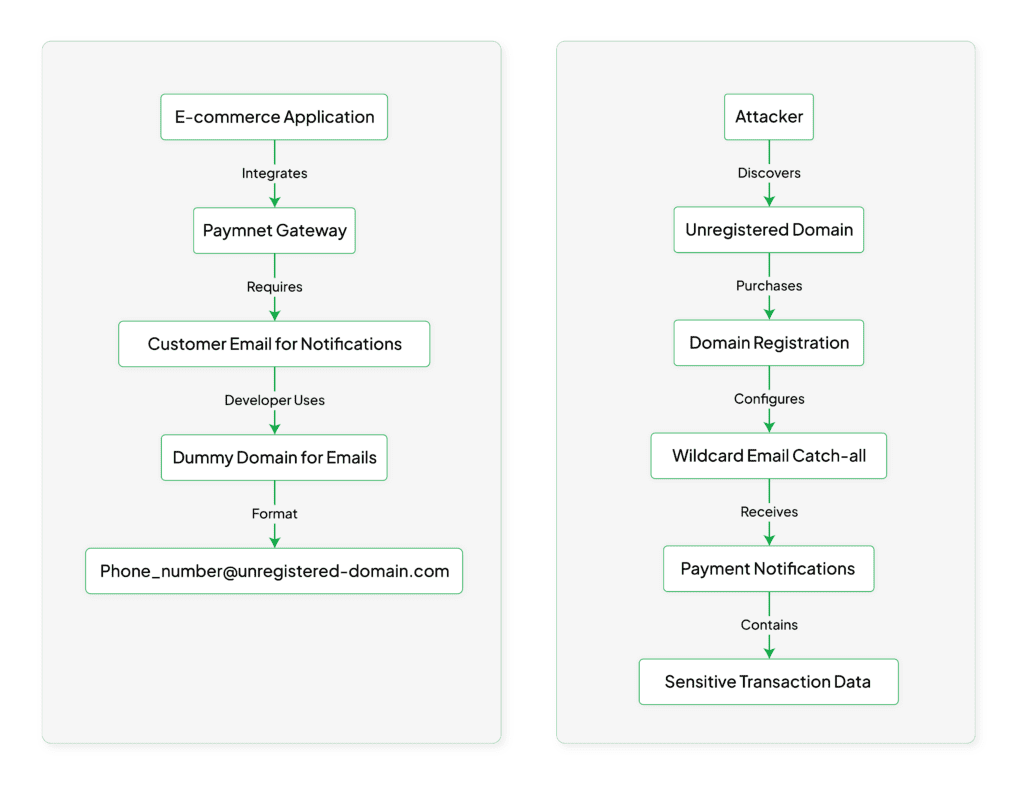
It started when we noticed something interesting – several companies were using a clever (but dangerous) workaround when integrating Juspay into their applications. Here’s the scenario: Juspay needs an email address for every transaction, but many apps only collect phone numbers from their users. The solution these companies came up with? Creating dummy email addresses using unregistered domains.
For instance, they’d take a user’s phone number like 1234567890 and automatically create an email like [email protected]. Seems harmless, right? That’s what we thought at first too. However, upon closer inspection, we discovered the real danger: these dummy email domains were often unregistered.
Why This Is a Big Deal
The issue became clear when we realized that these dummy domains weren’t actually owned by anyone. In multiple cases, we were able to:
- Purchase these unregistered domains
- Set up a catch-all email system
- Start receiving thousands of real payment notifications within hours
Let’s pause here to emphasize something important: we’ve responsibly disclosed this vulnerability to all affected companies, and they’ve taken steps to fix it. But this pattern of dummy email domains in new assessments suggests that this problem is widespread and ongoing, which is why we’re sharing this knowledge with the broader security community.
The Real Impact
In our assessments, we’ve seen this vulnerability expose:
- Complete transaction histories
- Customer phone numbers
- Booking details
- Payment success/failure notifications
- Refund information
What makes this particularly concerning is that any malicious actor could exploit this oversight to gather sensitive financial information from thousands of customers in real-time.
How to Fix This
If you’re using Juspay (or any payment gateway), here’s what you should do right now to mitigate the risks posed by dummy email domains::
- Check Your Integration: Are you using any dummy or temporary domains for payment notifications? This needs immediate attention.
Own Your Domains: Generate notification emails using domains you control. For example:
payments-{unique-id}@your-company-domain.com- Use Webhooks: Many payment gateways offer webhook notifications as an alternative to email notifications. Consider using these instead.
- Regular Audits: Make domain ownership and email configuration checks part of your regular security assessments.
A Broader Lesson
This vulnerability keeps appearing across different organizations because it stems from a common challenge: balancing user experience (not wanting to collect email addresses) with payment gateway requirements. While the workaround might seem clever in development, it creates serious security risks in production.
What We’ve Learned
After finding this issue across multiple assessments, we’ve observed that:
- This isn’t just a one-off mistake – it’s a pattern
- Development teams often implement this as a quick fix
- The security implications aren’t immediately obvious
- Once exposed, the vulnerability is relatively easy to exploit
Moving Forward
If you’re integrating any payment gateway, take a moment to review your email notification configurations. Remember, what seems like a harmless development workaround could become a serious security vulnerability in production.
The good news is that every company we’ve notified about this issue has taken it seriously and implemented fixes quickly. It’s a reminder that sometimes the simplest oversights can create the biggest vulnerabilities – and that regular security assessments are crucial for catching these issues and mitigating risks like dummy email domain misuse before they can be exploited.