Traditionally, organizations have often relied on a standardized SLA for vulnerability management, imposing identical remediation timelines across all teams and vulnerabilities. This approach suffers from several shortcomings:
- Overwhelm and Discouragement: Teams with limited resources struggle to meet unrealistic deadlines, leading to discouragement and potential burnout.
- Misaligned Priorities: Critical vulnerabilities requiring immediate attention get buried under less severe but time-sensitive issues.
- Ineffective Resource Allocation: Highly skilled personnel waste time addressing low-risk vulnerabilities, hindering their ability to tackle more pressing security concerns.
The Power of Adaptive SLAs
A more effective strategy lies in adopting adaptive SLAs. This approach tailors remediation timelines to factors such as:
- Vulnerability Severity: High-risk vulnerabilities warrant swifter remediation compared to those posing a lower threat.
- Team Maturity: Newer teams may require more flexible deadlines to establish efficient workflows.
- System Criticality: Breaches in mission-critical systems demand faster response times.
By considering these elements, organizations can create a tiered SLA structure, prioritizing the most critical vulnerabilities and ensuring teams have achievable goals
Why Set an SLA for Vulnerability Management?
Service Level Agreements (SLAs) are crucial for effective vulnerability management because they establish clear expectations and timelines for addressing security weaknesses.
- Ensuring timely identification and remediation of vulnerabilities
By setting an SLA for vulnerability management, organizations establish clear targets for identifying and resolving vulnerabilities promptly. This ensures that potential risks are addressed in a timely manner, minimizing the window of opportunity for attackers.
- Improving priority management for vulnerabilities
An SLA provides guidelines on prioritizing vulnerabilities based on their severity, impact, and likelihood of exploitation. This enables organizations to allocate resources effectively and focus on critical vulnerabilities first, reducing the overall security risk.
- Enhancing communication and collaboration between teams
An SLA fosters collaboration between vulnerability management teams, IT personnel, and other stakeholders. By clearly defining roles, responsibilities, and communication channels, an SLA promotes effective information sharing and coordination, leading to smoother vulnerability management processes.
Also Read: How PTaaS Enhances Security Collaboration Between Security Teams and Developers
- Meeting compliance requirements and regulatory standards
SLAs play a crucial role in meeting compliance requirements and regulatory standards. Organizations in industries such as finance, healthcare, and government must adhere to specific security standards. An SLA ensures that vulnerability management lifecycle align with these requirements.
Strobes Vulnerability SLA Widget
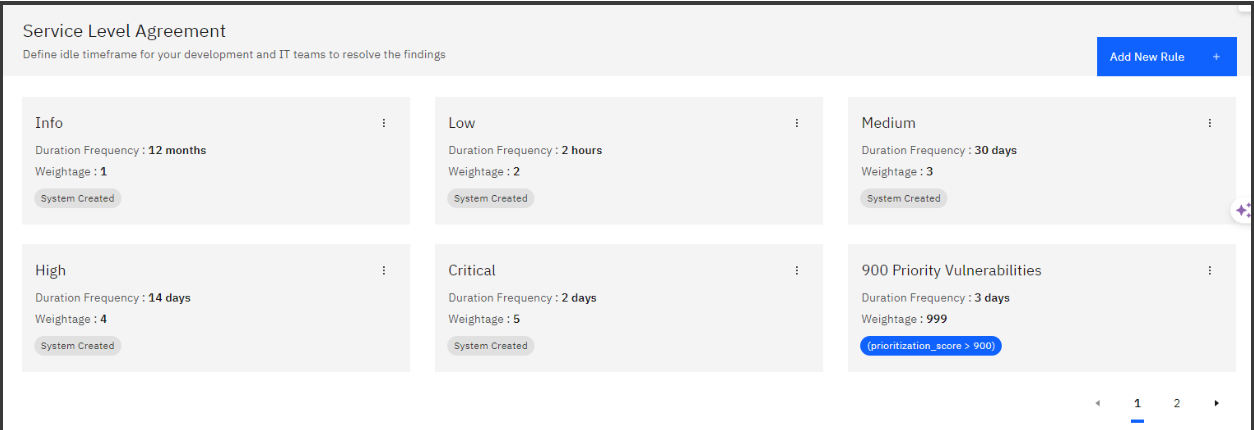
Strobes allows you to set up Service Level Agreements (SLAs) for fixing vulnerabilities based on their severity and risk. This helps ensure your development, infrastructure, and patching teams address them within a specific timeframe. Users can not only filter based on SLA status but also:
- Establish custom SLA policies: Define the desired remediation timeframes for vulnerabilities of varying severity levels (e.g., Critical: 2 days, High: 15 days, Medium: 30 days).
- Monitor SLA adherence: Strobes meticulously tracks deadlines and generates alerts for SLA violations, keeping security teams informed and accountable.
This widget provides insights into the Service Level Agreement (SLA) status of your findings. The SLA indicates the expected timeframe for addressing and resolving vulnerabilities. Green indicates that findings are within the SLA timeframe, while red signifies breaches of the SLA. Use this information to track and manage your Finding response times effectively.
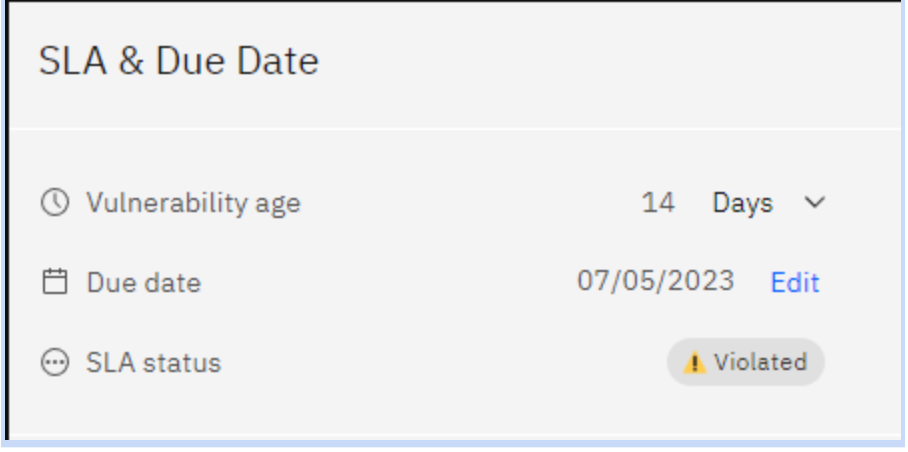
Benefits:
- Clear expectations: Everyone knows how quickly vulnerabilities should be addressed.
- Improved security posture: Faster patching reduces the window of opportunity for attackers.
- Proactive monitoring: Strobes sends weekly reports and alerts you if an SLA is violated.
This helps your organization prioritize and remediate vulnerabilities efficiently, ultimately improving your overall security posture.
Filtering SLA Status in Strobes
Strobes’ advanced filtering capabilities extend beyond SLA status.Users can combine SLA filters with additional criteria such as CVSS severity level, asset group, or date discovered. This multifaceted approach enables the construction of highly targeted queries, ensuring a comprehensive understanding of the most pressing security concerns demanding immediate attention.
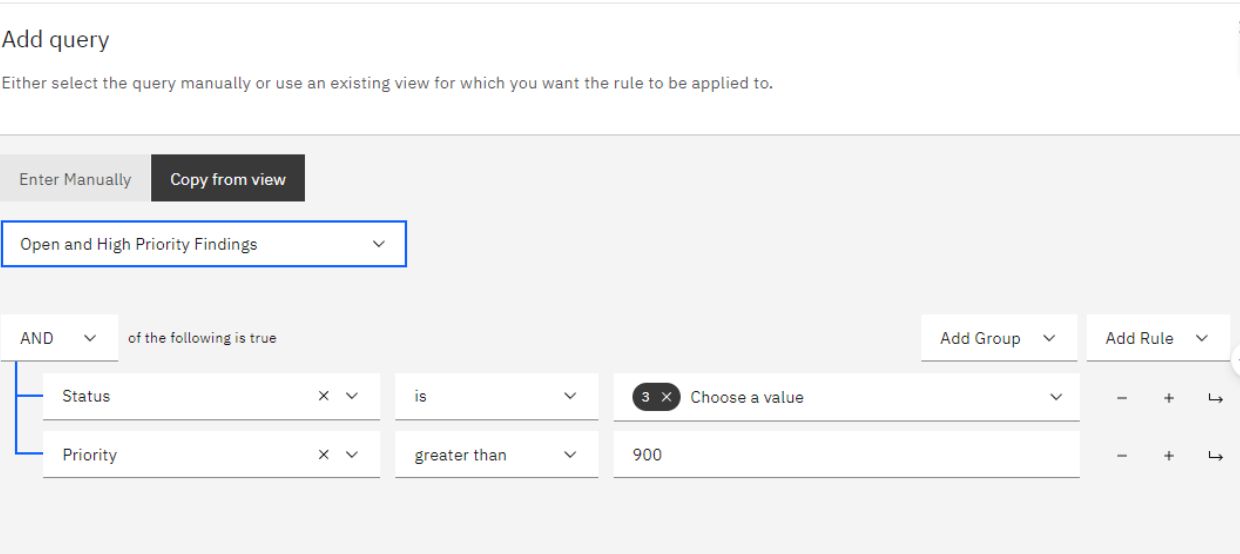
By filtering vulnerabilities based on SLA compliance and regulations (e.g., “Compliant” or “Violated”), security teams can achieve laser focus on high-risk vulnerabilities exceeding their designated remediation timeframes. This targeted approach streamlines communication and fosters collaboration between development, infrastructure, and patching teams, resulting in expedited vulnerability resolution.
Trusted by leading enterprises like, GHX, Zoho, Darwinbox, Tricenties, and SHL
Strobes helped organizations continuously manage threats, reduce vulnerabilities, and stay compliant, powered by AI-driven security expertise.
Reporting and SLA Dashboard
The dashboard delivers a snapshot of essential metrics that illuminate your current patch management landscape.
- New Vulnerabilities: This card signifies the total number of vulnerabilities identified but not yet assigned an SLA. Prioritize addressing these promptly to prevent exploitation.
- Unassigned Vulnerabilities: This metric highlights vulnerabilities lacking designated owners. A prompt assignment ensures timely remediation.
- Critical SLA Violations (>90 Days): This critical metric pinpoints vulnerabilities exceeding the 90-day SLA resolution window. Investigate these cases to expedite resolution and mitigate security risks.
- Reopened Vulnerabilities: This card emphasizes the number of vulnerabilities re-surfacing after resolution. Analyze root causes to prevent recurrence.
Charts for Deeper Insights
The dashboard empowers you to delve deeper with informative charts.
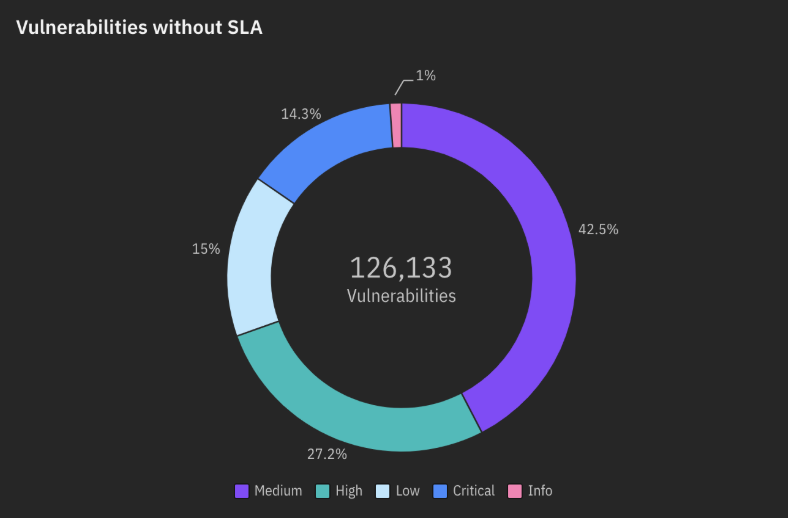
- Vulnerabilities without SLA: This chart categorizes vulnerabilities lacking SLAs based on severity (critical, high, medium, low). This distribution helps prioritize patching efforts by focusing on critical vulnerabilities first.
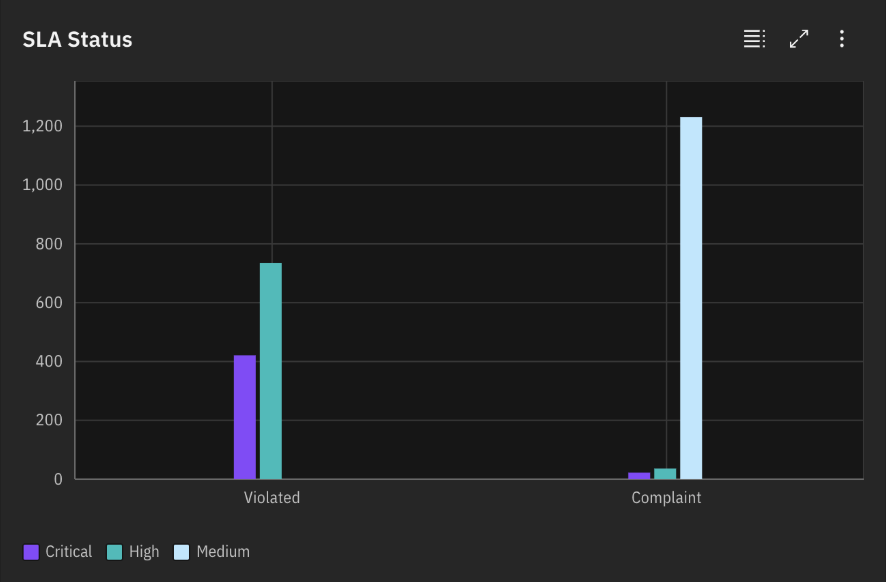
- SLA Status: This chart unveils the distribution of vulnerabilities across various SLA states (met, breached, not applicable) based on severity. This visualization enables you to identify areas for improvement in SLA adherence.
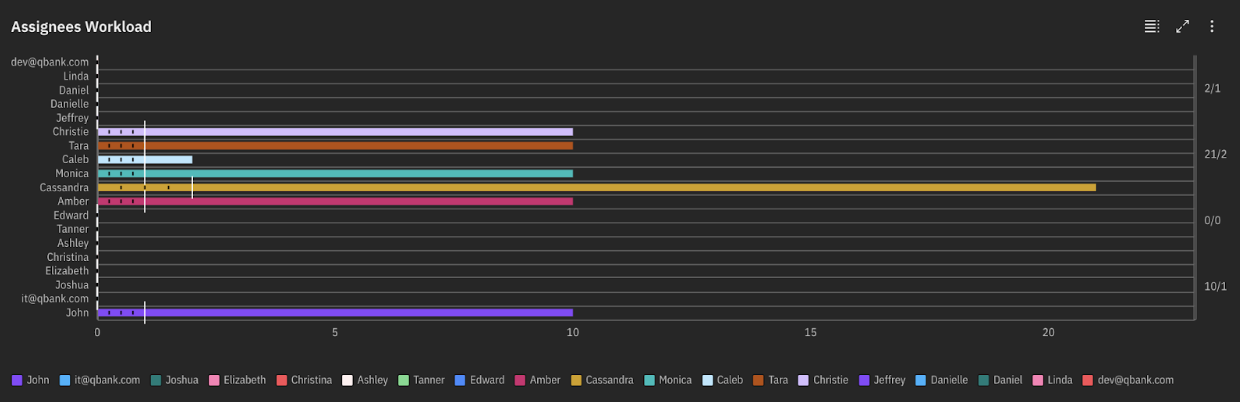
- Assignees Workload: This chart grants valuable insights into your team’s workload. It depicts the total number of vulnerabilities assigned to each team alongside the number successfully closed. This data empowers you to optimize team allocation and ensure balanced workloads.
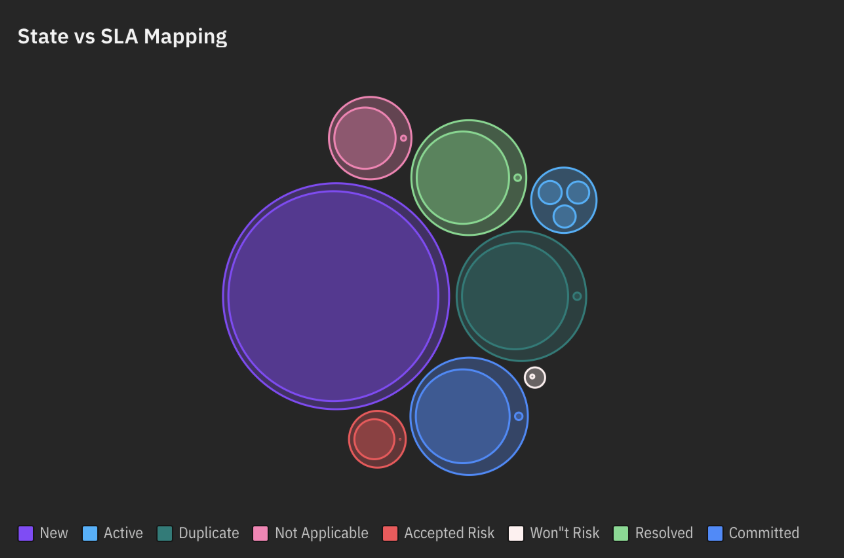
- State vs SLA Mapping: This interactive chart visually maps SLA statuses with vulnerability states. Hovering over the data points reveals additional details, facilitating comprehensive analysis of your patch application progress.
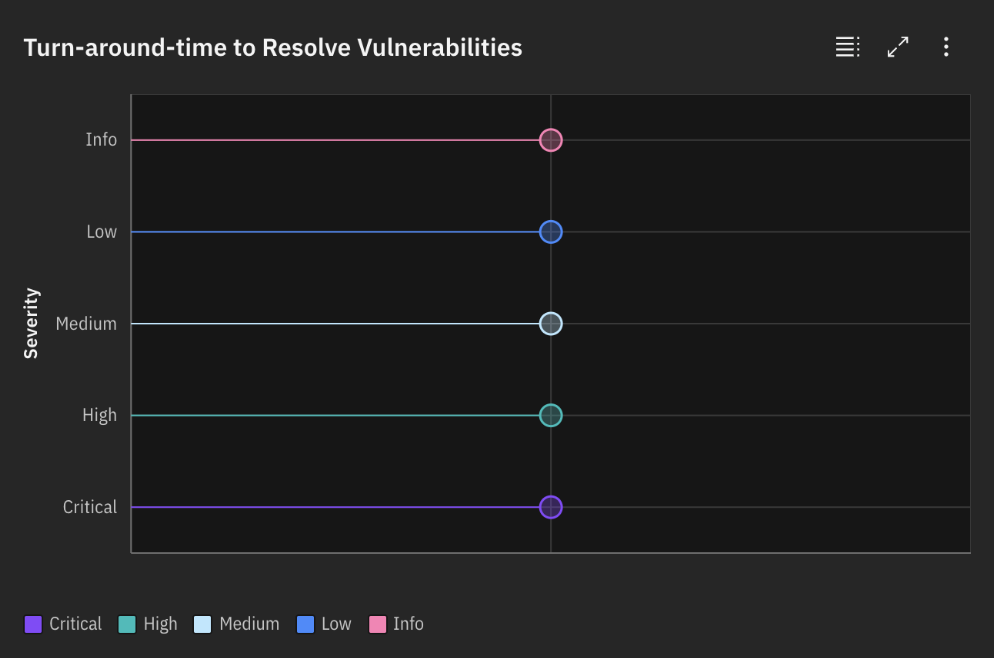
- Turn-around-time to Resolve Vulnerabilities: This chart exposes the average time taken by your teams to resolve vulnerabilities. Analyzing trends over time can expose areas for improvement in streamlining your remediation process.
Key Takeaways
Implementing sla for vulnerability management that align with team maturity levels requires a strategic approach. In summary, here are the key takeaways:
- Assess team maturity using a vulnerability management SLA Maturity Roadmap.
- Prioritize vulnerability remediation based on likely threats and real-world risks.
- Focus SLAs on systems with severe consequences in case of breaches.
- Implement SLAs step-by-step, starting with achievable goals.
- Regularly review and update SLAs to ensure their long-term effectiveness.
- Leverage automation technology for accurate and efficient SLA management.
- Customize SLAs based on team contexts and maturity levels.
By following these best practices and tailoring your vulnerability management SLAs to your team’s maturity level, you can enhance your security posture, protect critical assets, and ensure a culture of continuous improvement. Implementing well-structured SLAs is not an easy task, but the benefits far outweigh the challenges.
Embrace the potential of Service Level Agreements (SLAs) and transform your vulnerability management processes for optimal security outcomes.
Ready to streamline your vulnerability management with SLA-driven workflows? Book a free demo with Strobes and see how we can help.
Related Reads
- How to Prove the ROI of Your Vulnerability Management Metrics to the Board?
- Top 5 Vulnerability Management Mistakes Companies Make (Plus a Bonus Mistake to Avoid)
- What is Vulnerability Management? Compliance, Challenges, & Solutions
- Top 15 Vulnerability Management Tools for Businesses in 2025 (Reviewed & Ranked)
- Vulnerability Management Lifecycle: The Ultimate Guide to Business Security
- Strobes Solution: Risk Based Vulnerability Management