“The difficulty lies not so much in developing new ideas as in escaping from old ones.” – John Maynard Keynes
Success can be its own trap. After our initial CTEM pilot proved its worth, blocking potential breaches, cutting detection times, and winning over leadership, the inevitable question came up: “Can we make this work across the whole enterprise?” What felt like a victory lap quickly became the most demanding phase of our CTEM journey.
Scaling security innovations from proof of concept to enterprise reality is where many well-intentioned initiatives go to die. The controlled environment of a pilot, with its dedicated resources and engaged stakeholders, bears little resemblance to the complex, politically charged landscape of enterprise-wide transformation.
Scaling CTEM: The Challenge Emerges
Our pilot had focused on our most critical infrastructure – a few dozen servers hosting our core applications. Scaling meant expanding to thousands of endpoints across multiple business units, cloud environments, operational technology networks, and legacy systems that some teams preferred to forget existed.
The numbers were daunting:
- 14 different business units with varying risk appetites and operational priorities
- 7 cloud environments across AWS, Azure, and GCP with inconsistent security configurations
- 23 legacy applications that hadn’t been updated in years but remained business-critical
- 156 different vulnerability scanners, assessment tools, and security agents already deployed (yes, we counted)
Each environment brought unique challenges. The manufacturing division worried about operational disruption. The development teams feared CTEM would slow their already aggressive release cycles. The compliance organization questioned whether our new approach would satisfy regulatory requirements they’d spent years fine-tuning.
The Resistance Grew
If Part 2 was about overcoming skepticism, Part 3 was about navigating organizational inertia at scale. The resistance we faced wasn’t the intellectual pushback of early doubters – it was the passive resistance of established processes, entrenched tools, and competing priorities.
“We’re already doing continuous monitoring,” insisted the network security team, pointing to their SIEM dashboards that generated thousands of alerts daily.
“Our business unit has different risk requirements,” argued various division heads, each convinced their environment was too unique for a standardized approach.
“This will break our compliance audit trail,” worried the GRC team, concerned about explaining CTEM methodologies to auditors who barely understood traditional vulnerability management.
The most insidious resistance came from tool vendors protecting their installed base. Suddenly, every security vendor claimed their solution included “CTEM capabilities” – usually meaning they’d added the word “continuous” to their marketing materials without fundamentally changing their approach.
The Architecture of Scale
Scaling CTEM required rethinking our entire security architecture. We couldn’t simply deploy our pilot approach 50 times across different environments. Instead, we needed to build a federated system that could adapt to diverse requirements while maintaining consistency in core principles.
The Hub-and-Spoke Model
We developed what we called the “CTEM Orchestration Hub”—a centralized intelligence platform that coordinated exposure management across distributed environments while allowing each business unit to maintain operational autonomy.
Central Hub Responsibilities:
- Threat intelligence correlation and distribution
- Cross-environment attack path analysis
- Executive reporting and risk aggregation
- Policy framework and compliance mapping
- Tool integration and data normalization
Spoke Autonomy:
- Environment-specific exposure discovery methods
- Localized remediation workflows
- Business-context risk prioritization
- Custom validation procedures
This model allowed us to maintain CTEM’s core philosophy while respecting the operational realities of different business units.
The Integration Nightmare
Perhaps our biggest technical challenge was integrating the diverse security tools already deployed across the organization. Rather than ripping and replacing existing investments, we built translation layers that could normalize data from different sources into our CTEM framework.
This meant creating connectors for:
- 12 different vulnerability scanners
- 8 cloud security posture management tools
- 15 endpoint detection and response agents
- 6 network monitoring solutions
- 4 application security testing platforms
Each integration brought unique data formats, API limitations, and operational constraints. We learned that successful CTEM scaling isn’t about finding the perfect tools—it’s about making imperfect tools work together intelligently.
Cultural Transformation in Scaling CTEM
The technical challenges paled in comparison to the cultural shift required. Scaling CTEM meant transforming how hundreds of people thought about and acted on security information.
The Champion Network
We established a network of “CTEM Champions” – security-minded individuals in each business unit who could translate between centralized security policies and local operational needs. These weren’t necessarily security professionals; often, they were system administrators, DevOps engineers, or application owners who understood both the technical details and business context of their environments.
The champion network became our secret weapon. When the compliance team worried about audit implications, our champion in legal helped craft documentation that satisfied both CTEM principles and regulatory requirements. When development teams pushed back on continuous validation, our champion in engineering designed automated testing that actually improved their deployment pipeline reliability.
Training at Scale
Traditional security training doesn’t prepare teams for CTEM thinking. We had to develop entirely new educational content that helped people understand:
- Why exposure validation matters more than vulnerability counting
- How to think in attack paths rather than individual weaknesses
- When to prioritize business context over technical severity scores
- How continuous processes differ from periodic ones
We created role-based training programs: CTEM for executives focused on risk communication and business impact; CTEM for operators emphasized workflow integration and tool utilization; CTEM for analysts deep-dive into threat intelligence correlation and validation methodologies.
Metrics That Matter at Scale
Our pilot metrics detection times, prevented breaches, and exposure reduction—remained important but proved insufficient for scaling CTEM to the enterprise level. We needed metrics that could communicate value across diverse stakeholders while driving the right behaviours.
The CTEM Scorecard
We developed a multi-dimensional scorecard that tracked: Exposure Metrics, Operational Metrics & Business Metrics as shown in the image down below.
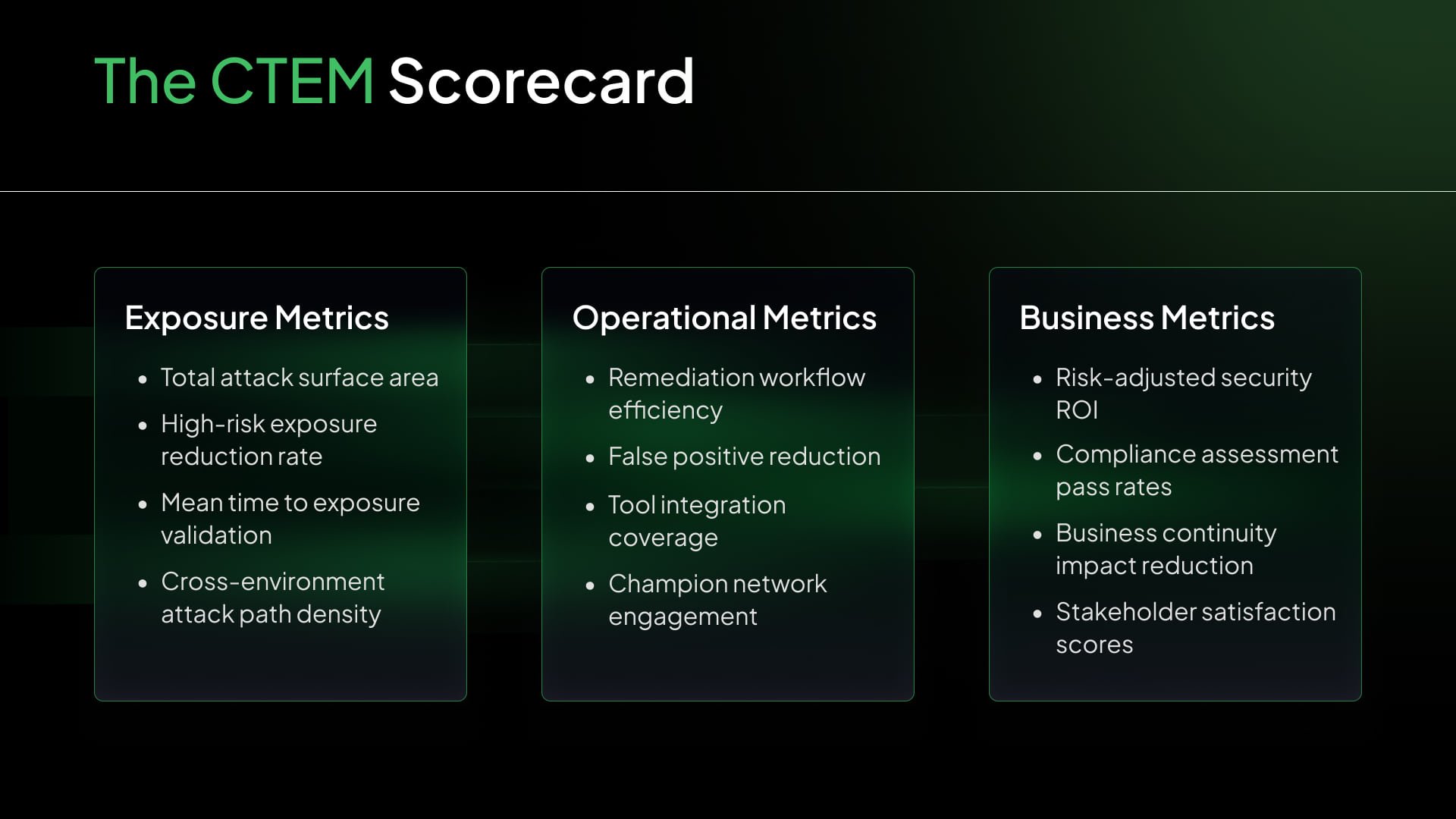
The key insight was that different audiences cared about different metrics. Executives wanted business risk reduction. Operations teams focused on workflow efficiency. Compliance cared about audit readiness. Our scorecard provided relevant views for each stakeholder while maintaining underlying data consistency.
Innovation Through Necessity
Scaling CTEM forced us to innovate in ways our pilot never required. Limited resources, diverse environments, and competing priorities became catalysts for creative solutions.
Automated Exposure Orchestration
Manual processes that worked fine for our pilot became bottlenecks at scale. We developed automated orchestration workflows that could:
- Correlate threat intelligence across multiple sources
- Trigger exposure validation based on threat actor activity
- Automatically adjust remediation priorities based on business context
- Generate stakeholder-specific communications without human intervention
AI-Powered Risk Contextualization
With thousands of potential exposures across our enterprise, human analysts couldn’t provide the contextual risk assessment that made our pilot successful. We implemented machine learning models that could:
- Learn from historical remediation decisions to predict priority
- Understand business context from asset relationships and data flows
- Identify exposure patterns that indicate coordinated attack campaigns
- Recommend optimal remediation strategies based on similar past scenarios
Community-Driven Validation
Perhaps our most successful innovation was crowdsourcing exposure validation across our champion network. We built a platform where champions could share validation methodologies, report false positives, and collaborate on remediation approaches.
This community-driven approach not only improved our validation accuracy but created a sense of shared ownership that traditional top-down security programs never achieved.
The Breakthrough Moment
Nine months into our scaling CTEM journey and enterprise-scale implementation, we faced our ultimate test: a supply chain compromise that affected multiple vendors across our ecosystem. Traditional security programs would have scrambled to understand which systems might be impacted, what data could be at risk, and how to prioritize remediation across thousands of potential exposure points.
Our CTEM-enabled response was dramatically different. Within hours, we had:
- Identified all potentially affected systems across our enterprise
- Validated which exposures were actually exploitable in our specific configurations
- Prioritized remediation based on business impact and attack path analysis
- Coordinated response activities across 14 business units through our champion network
- Communicated risk-appropriate updates to executives, operations teams, and external stakeholders
The incident that could have paralyzed our organization for weeks was contained within 48 hours. More importantly, we prevented the breach entirely—not through luck or heroic effort, but through the systematic application of CTEM principles at enterprise scale.
Lessons from the Scale Journey
Scaling CTEM taught us that transformation at enterprise scale requires different strategies than pilot success:
- Embrace Federated Authority: Centralized vision with distributed execution proved more effective than either pure centralization or complete autonomy.
- Invest in Integration: The ability to make existing tools work together intelligently matters more than finding perfect new solutions.
- Build Communities, Not Just Processes: People drive transformation; technology enables it.
- Measure What Motivates: Metrics must align with stakeholder incentives to drive sustainable behavioral change.
- Automate Ruthlessly: Manual processes that work in pilots become failure points at scale.
Setting the Stage for Maturity
By the end of our scaling phase, CTEM had evolved from an innovative pilot to the foundation of our enterprise security posture. But success at scale brought new challenges: maintaining innovation momentum, continuous improvement, and preparing for the next evolution in threat management.
In Part 4, I’ll share how we matured our CTEM program, the advanced techniques we developed, and the lessons learned from two years of enterprise-scale continuous threat exposure management.
Scaling innovation requires more than multiplying success—it demands reimagining what success looks like at every level of the organization.
Next: Part 4 – CTEM Maturity: Advanced Techniques and Hard-Won Wisdom






