Among the most debated questions in the constantly changing mobile application development, whether to include root detection in the application is a seemingly important choice to both developers and security teams. This is not just a technical option, but it has far-reaching consequences in terms of user experience, security, and compliance.
On the one hand, root detection can ensure that a compromised device is not used to execute sensitive data and operations. Conversely, bad implementation would cause users to be chased away or end up bypassing the implementation, making the whole exercise useless. This problem is further complicated by considering the compliance requirements, risks unique to the industry, and a variety of user demographics.
Compliance: A Key Factor in the Debate
Applications that deal with sensitive data tend to impose strict security controls on applications in industries such as finance, healthcare, and e-commerce as compliance schemes. For instance:
- Payments application PCI DSS suggests keeping sensitive data out of the hands of unauthorized users, as rooted devices can penetrate.
- To ensure that healthcare apps are HIPAA compliant, effective measures are required to ensure that patient information is not breached.
- Vulnerabilities in rooted devices are a possible compliance threat because GDPR focuses on the security of personal data.
- The enabled root detection also contributes to the security and enables the organization to enable UPI on its platform, which is in line with the RBI and NPCI recommendations.
Although compliance does not necessarily imply the explicit requirement to detect the root, it implies the provision of privacy, integrity, and availability of the data, which is not easily achieved without considering the risks of rooted machines.
Who Should Implement Root Detection?
Organizations that should prioritize root detection:
- Financial Apps: Banks, wallets, and payment apps are the best targets of fraud and data theft.
- Healthcare Apps: Concerns: It is very important to safeguard sensitive patient data in regulations such as HIPAA.
- Corporate Apps: Enterprise applications with access to proprietary or sensitive organizational data.
- Gaming Apps with Microtransactions: To prevent tampering and fraudulent purchases.
- E-Commerce Apps: Processing payment-related information and user-sensitive data.
Who Might Forego Root Detection?
While root detection can benefit most apps, there are cases where it might not be necessary:
- Apps with Low Security Requirements: For instance, casual games or apps that don’t process sensitive data.
- Apps Targeting Developers: Developer-focused apps often require access to advanced features that may conflict with root detection.
- Open-Source or Customizable Apps: Apps designed to be modified or extended by users may not prioritize root restrictions.
Pros of Implementing Root Detection
| Advantages | Description |
| Enhanced Security | Protects sensitive data and app functionality from malicious tampering. |
| Compliance Readiness | Helps align with security requirements in regulated industries like finance and healthcare. |
| Fraud Prevention | Deters financial fraud, credential theft, and API abuse by reducing attacker capabilities. |
| User Trust | Reinforces confidence in the app’s security for end-users. |
Cons of Implementing Root Detection
| Disadvantages | Description |
| User Experience Impact | Legitimate users on rooted devices may face app restrictions or an inability to use the app. |
| Bypass Risk | Advanced attackers can circumvent poorly implemented root detection. |
| Development Overhead | Adds complexity to app development and maintenance. |
| Potential Market Exclusion | Could exclude users in markets where rooting is common for device customization. |
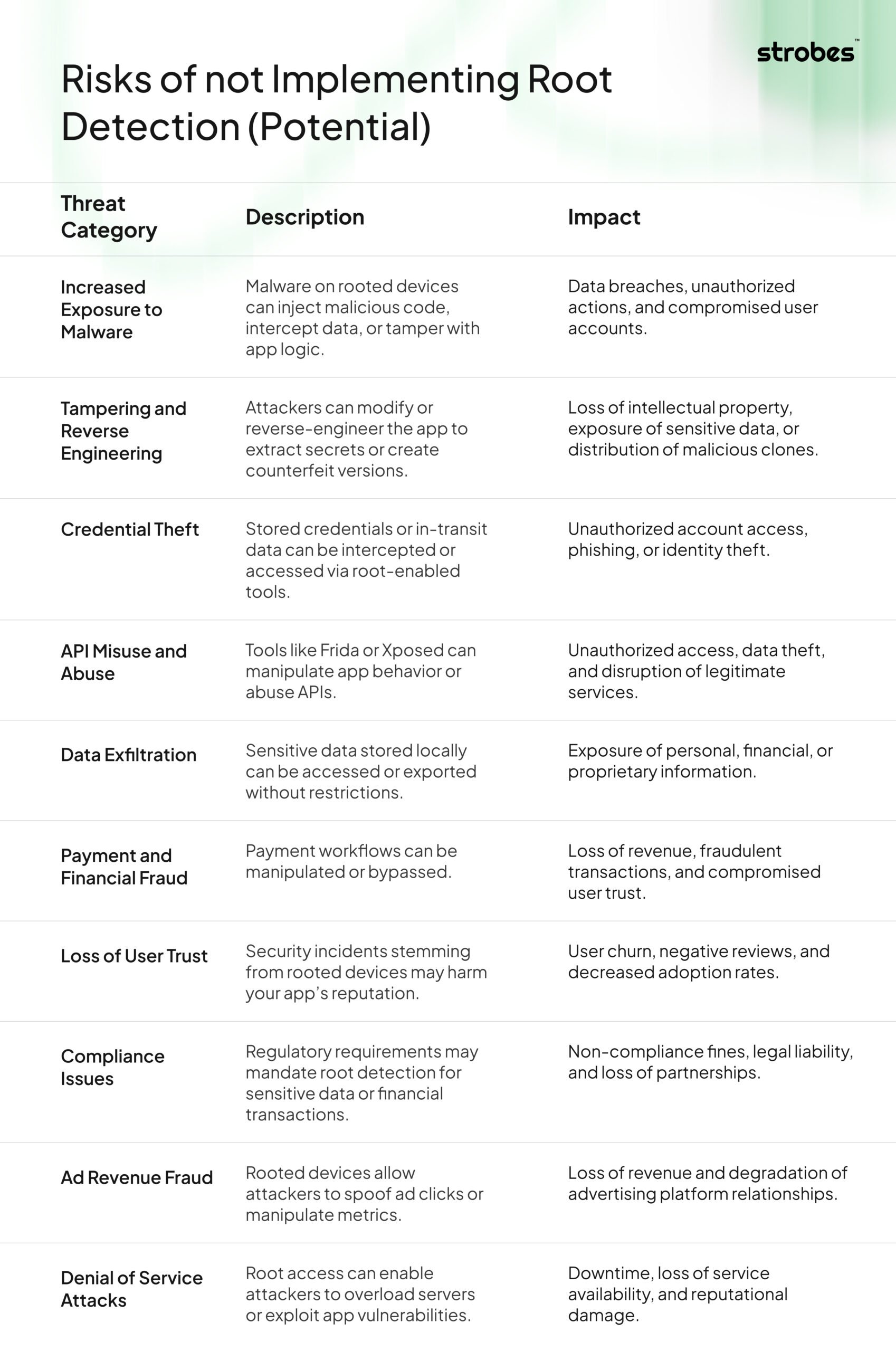
Risks of not Implementing Root Detection (Potential)
 Optional Partial Implementation of Root Detection: A UPI Case Study
Optional Partial Implementation of Root Detection: A UPI Case Study
Although root detection on a system-wide basis, as implemented in an application that is UPI-based, could lead to increased security, it can equally pose a usability problem to legitimate users of the rooted device, like those who use the same to customize or develop applications. A particular implementation plan can be a trade-off, where the essential elements of payments are preserved, but the functionality of non-sensitive parts of the application is not lost.
How Partial Root Detection Works in UPI Apps
- Sensitive Modules containing root detection.
- Payment Authorization: Prevent the occurrence of fraudulent activities through the detection of root status prior to the initiation and authorization of a transaction.
- Data Encryption and Storage: Make sure that the sensitive user information, including the details of the bank accounts and UPI PINs, is not visible on rooted devices.
- API Requests to Payment Gateways: Protect API calls involved in transaction validation to prevent tampering or replay attacks.
- Non-Sensitive Modules Without Root Detection
- User Interface Features: The features of the application where the UPI is not enabled or it is not mandatory that the user should access these features.
- General Information Access: Allow users to browse tutorials, FAQs, or promotional content without triggering root-related restrictions.
Root detection partial implementation would be a realistic method of balancing security and user experience in the UPI context. By taking control over the fact that high-risk modules such as payment authorization and sensitive data may be compromised without interfering in the lower-risk areas, UPI apps can potentially prevent fraud in rooted devices without disrupting the accessibility of their services to a wider user base. This practice is in line with regulatory requirements by authorities such as the Reserve Bank of India (RBI), and it makes UPI systems reliable.
Conclusion:
Root detection is an essential measure that can be deployed to protect sensitive information and avoid fraud, particularly in applications that involve financial transactions, health care, or corporate information. Its use within the entire app may, however, affect user experience, especially when it has been applied to rooted devices.
The balance is found in a partial implementation plan that involves the application of root detection to important modules, such as payment processing, and leaving non-sensitive ones free to all. This can be used to increase security without affecting usability, and it is therefore suited to the apps that are required to pass the regulations and secure high-risk zones, as is the case with UPI apps in India.
Finally, this will depend on the purpose of the app, the intended audience, and regulations. Thoughtfully implemented root detection helps maintain both security and user experience.

 Optional Partial Implementation of Root Detection: A UPI Case Study
Optional Partial Implementation of Root Detection: A UPI Case Study