It started like any other Monday morning.
Coffee cups steamed beside keyboards, servers hummed gently in climate-controlled rooms, and email inboxes pinged with weekend catch-up. But within minutes, that ordinary day at one of the world’s largest logistics firms spiraled into chaos. Files wouldn’t open. Systems froze. And then came the chilling message, glowing on every monitor:
“Your files have been encrypted. Pay $10 million in Bitcoin, or lose everything.”
This wasn’t fiction. It was NotPetya – one of the most devastating ransomware attacks in history. What started as a seemingly contained cyber incident in Ukraine in 2017 quickly morphed into a global crisis, crippling multinational corporations like Maersk, Merck, and Rosneft. The cost? Over $10 billion in damages and weeks of disrupted operations.
But NotPetya wasn’t alone. From the WannaCry outbreak that locked down the UK’s National Health Service to the Colonial Pipeline attack that halted fuel supplies across the U.S. East Coast, ransomware has evolved into a weapon of mass disruption. The year 2024 alone has seen Ascension Health, Change Healthcare, and CDK Global buckle under digital siege.
These aren’t just cautionary tales; they’re wake-up calls.
Ransomware doesn’t knock. It breaks in silently, waits patiently, and strikes ruthlessly. Which is why forward-thinking organizations now turn to ransomware simulation- a proactive strategy that replicates the mechanics of an attack without the catastrophic consequences. Think of it as a cybersecurity fire drill: you don’t wait for flames to learn how to use the extinguisher.
In this guide, we’ll understand into how Strobes Security is redefining the way organizations prepare for ransomware. Through simulated attacks grounded in real-world tactics, they help uncover blind spots, test resilience, and train your teams before the stakes become real.
What is Ransomware Simulation?
Ransomware simulation is a controlled cybersecurity exercise that emulates real ransomware attack behaviors, such as data encryption, privilege escalation, lateral movement, and persistence techniques, within an organization’s environment. The goal is not to cause damage, but to test how well the organization can detect, respond to, and recover from a ransomware event.
These simulations use safe, non-malicious scripts and tools that replicate the tactics, techniques, and procedures (TTPs) of actual ransomware groups. They’re conducted by security experts and tailored to an organization’s infrastructure, business risks, and threat landscape.
What Does It Mean for Security Leaders?
For CISOs, CIOs, and other security decision-makers, ransomware simulation is not just a technical test- it’s a strategic imperative that provides critical insights into:
- Risk Visibility: Understand the real-world impact of a ransomware breach and which parts of the business are most exposed.
- Control Validation: Evaluate whether existing security investments (SIEM, EDR, backups) are performing as intended.
- Crisis Readiness: Measure how prepared teams are to contain, communicate, and recover from an attack.
- Board-Level Reporting: Convert technical findings into executive-friendly metrics and risk narratives.
- Strategic Alignment: Justify budget needs, prioritize security roadmaps, and drive cross-departmental security awareness.
- Regulatory Proofing: Demonstrate to regulators, auditors, and insurers that the organization is actively validating its security controls.
In essence, ransomware simulation allows security leaders to shift from reactive defense to proactive resilience, transforming unknown risks into actionable intelligence.
Is Ransomware Simulation Mandatory?
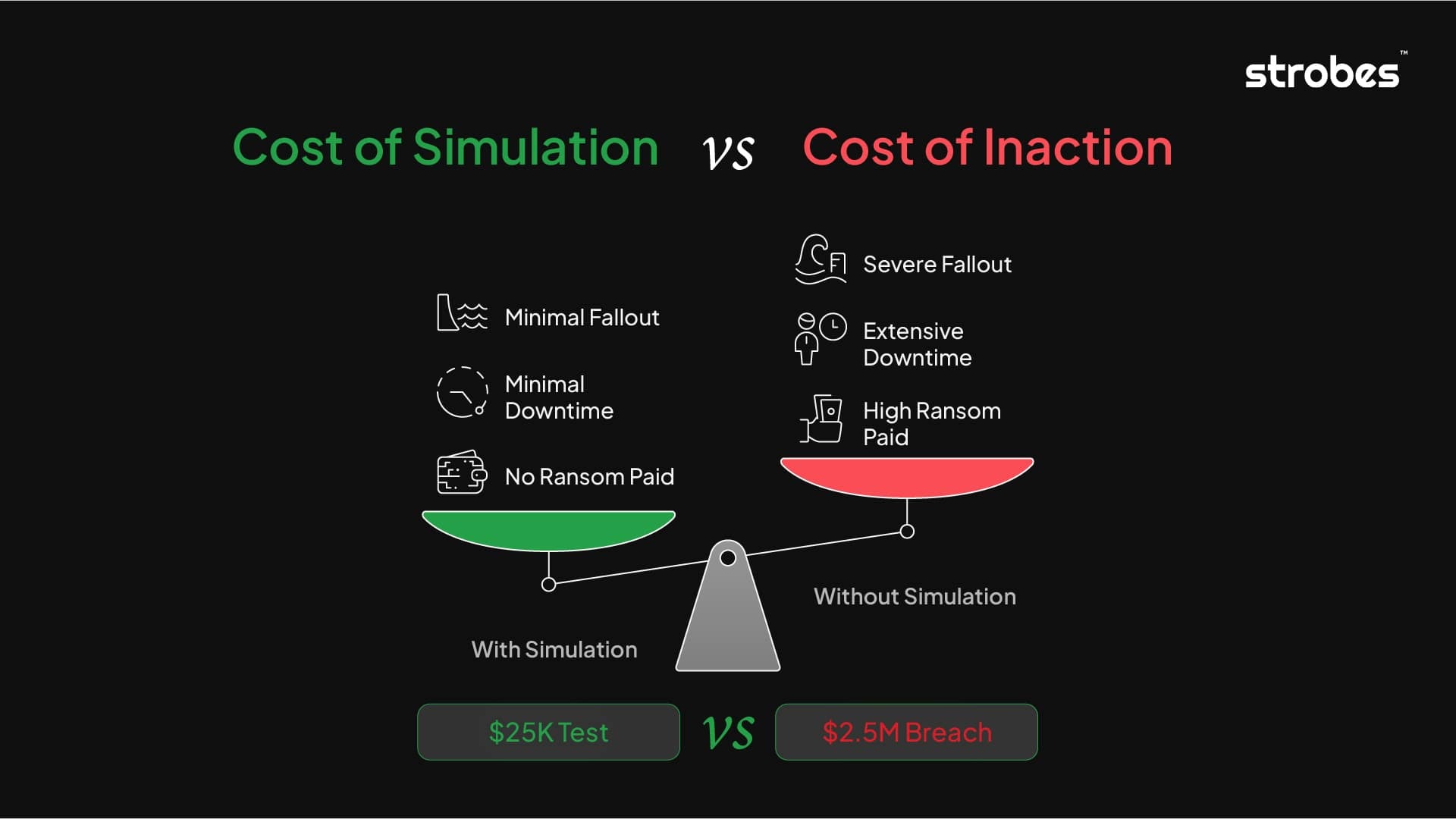
Strictly speaking, ransomware simulation is not a legally mandated requirement under most national or international cybersecurity regulations. However, in practice, it has become a critical expectation for organizations serious about cyber resilience.
While frameworks such as NIST Cybersecurity Framework, ISO/IEC 27001, HIPAA, and PCI-DSS do not explicitly require ransomware simulation, they do mandate regular testing of incident response plans, validation of controls, and risk-based security assessments. Ransomware simulation is one of the most effective and realistic ways to meet those requirements.
Moreover, cyber insurance providers increasingly look for evidence that an organization is prepared for a ransomware event. Conducting ransomware simulations can significantly improve eligibility for coverage and reduce premiums by demonstrating due diligence and response readiness.
In high-risk industries, such as finance, healthcare, energy, and government, ransomware simulation is often considered a de facto standard. Boards, regulators, and even enterprise clients are demanding clear proof that organizations can not only prevent ransomware but respond quickly and effectively when it happens.
In summary, ransomware simulation may not be “mandatory” in legal terms, but it is rapidly becoming a necessity in operational, regulatory, and reputational contexts.
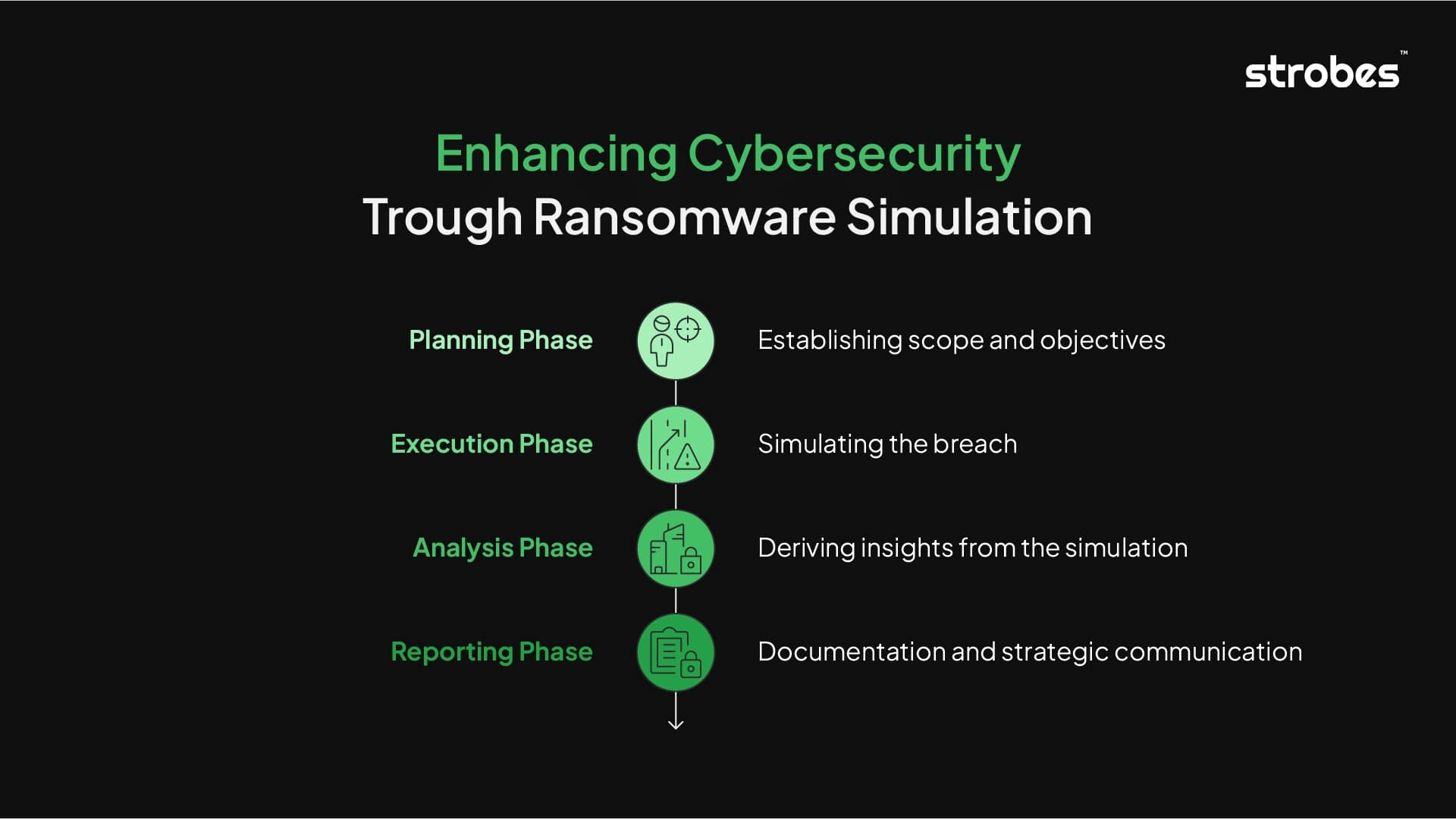
Methodology of Ransomware Simulation
1. Planning Phase: Establishing Scope and Objectives
The simulation begins with a detailed planning stage that aligns organizational goals with technical objectives. It is here that cybersecurity consultants and stakeholders define the purpose of the simulation. Common goals include testing endpoint detection and response (EDR) systems, evaluating containment protocols, or measuring the readiness of incident response teams.
This phase includes determining the simulation’s scope—specifying which systems, networks, and applications will be part of the test. It also involves identifying potential attack vectors to emulate. All activities must be well-documented and authorized through formal approvals to avoid legal or operational repercussions.
Objectives are laid out clearly, with predefined success metrics and key performance indicators (KPIs) for evaluating results.
2. Execution Phase: Simulating the Breach
The execution stage is where the real action begins. Ransomware simulations are not random; they are carried out using carefully designed benign scripts and tools that mimic the behavior of actual ransomware. These simulations test critical paths attackers might use, such as privilege escalation, lateral movement, and file encryption, without inflicting real damage.
For instance, the simulation may include:
- Process Injection: Emulating how malware might inject code into legitimate processes.
- Privilege Escalation: Testing if attackers can move from low-privileged accounts to administrative levels.
- Environment Misconfigurations: Abusing misconfigured services or exposed credentials for payload delivery.
- PsExec Exploitation: Using remote execution techniques to spread simulated ransomware laterally.
- Self-Morphing Scripts: Mimicking polymorphic malware to evaluate if endpoint protection can detect evolving threats.
During this phase, cybersecurity teams monitor detection tools to observe how quickly and accurately alerts are triggered. The organization’s blue team (defensive team) may or may not be aware of the simulation beforehand, depending on whether the exercise is intended as a blind test or a collaborative drill.
3. Analysis Phase: Deriving Insights from the Simulation
Once the simulation concludes, the gathered data is meticulously analyzed to extract actionable insights. This involves reviewing logs, alert timelines, team responses, and the effectiveness of containment strategies. One of the core outcomes of this phase is the identification of security gaps—both technological and procedural.
For example, if the simulation reveals that the EDR system failed to flag a known pattern of behavior, or if the incident response team took too long to contain a simulated encryption process, these become areas of concern. Lessons learned from these failures inform improvements in playbooks, policies, and infrastructure.
The analysis phase also offers an opportunity to assess organizational readiness across dimensions such as:
- Mean Time to Detect (MTTD) and Mean Time to Respond (MTTR)
- Coordination among IT, legal, communications, and executive stakeholders
- Effectiveness of isolation techniques and recovery mechanisms
- Compliance with regulatory requirements for breach management
All these insights contribute to a stronger, more resilient cybersecurity posture.
Also Read: Key CTEM Metrics: Measuring the Effectiveness of Your Continuous Threat Exposure Management Program
4. Reporting Phase: Documentation and Strategic Communication
The final phase culminates in a comprehensive technical report. This is not merely a checklist of what went wrong and what worked. Instead, it’s a roadmap for evolving cybersecurity maturity. The report typically includes:
- Detailed findings on exploited vulnerabilities
- Screenshots or logs illustrating key simulation events
- Technical evidence of weaknesses and their potential consequences
- Recommendations for remediation, including prioritization based on risk severity
- A gap analysis comparing existing controls against industry best practices
Equally important is the communication of these findings. The report is tailored for diverse stakeholders—from technical teams to executive leadership. It aims to foster alignment on cybersecurity priorities and drive informed investment in tools, training, and strategy.
Top Misconfigurations and Vulnerabilities Explored in Ransomware Simulations
One of the most valuable aspects of a ransomware simulation lies in its ability to identify hidden misconfigurations and security gaps that would otherwise remain dormant until exploited by a real attacker. These are often not limited to software flaws but extend to how systems are set up, how access rights are provisioned, and how policies are enforced (or ignored) across the infrastructure.
Let’s explore some of the critical vulnerabilities typically examined during a ransomware simulation:
Process Injection Vulnerabilities
Process injection is a technique often used by real ransomware to evade detection. By injecting malicious code into legitimate processes (such as explorer.exe or svchost.exe), ransomware can mask its behavior and avoid triggering endpoint detection systems. Simulations test whether such activity can bypass current monitoring systems and whether security personnel are able to recognize this stealthy behavior through heuristic patterns or behavioral anomalies.
Privilege Escalation Pathways
A common first step for any ransomware campaign is privilege escalation. Attackers often begin with limited access—say, a compromised low-level user account—and then attempt to move laterally or vertically to gain administrative control.
Simulations evaluate whether weaknesses in group policies, misconfigured file permissions, or unpatched software allow this elevation of privileges. These findings are crucial for implementing or tightening the Principle of Least Privilege (PoLP) and further supporting a zero-trust security architecture.
PsExec-Based Exploitation
PsExec is a legitimate Windows Sysinternals tool often abused by attackers to execute commands and move laterally across a network. In ransomware simulations, this tool can be used to mimic how a malicious actor might deploy ransomware to multiple systems in rapid succession.
By simulating PsExec-based attacks, organizations can observe how lateral movement is detected (or missed) by their defense systems and whether segmentation and endpoint controls are sufficiently robust to prevent widespread compromise.
Self-Morphing Malware Simulations
Real-world ransomware frequently utilizes polymorphic techniques—changing its code structure while keeping its functionality intact—to evade signature-based antivirus systems. Simulated self-morphing scripts test whether endpoint detection solutions can detect threats based on behavior, rather than relying solely on known signatures. This provides insight into the effectiveness of heuristic and AI-based detection capabilities.
Abusing Misconfigurations for Payload Delivery
Misconfigurations are one of the most fertile grounds for attackers. From overly permissive firewall rules and exposed administrative interfaces to improperly configured cloud storage buckets, these gaps provide easy access points for threat actors.
Simulations actively test such misconfigurations by attempting payload delivery through email phishing, drive-by downloads, or exploitation of open ports. The goal is to determine whether preventive controls are in place—and more importantly, whether they work under real conditions.
Zip and Archive-Based Payloads
Compressed files are a favorite vector for ransomware payloads. Malicious archives can contain executables disguised as documents or use obfuscation to hide ransomware code. Simulations test how well endpoint protection systems scan and analyze such files and whether security policies appropriately restrict execution from user directories or temporary folders. If the simulated payload can be delivered and activated without triggering alarms, it indicates a serious gap in layered defenses.
By deliberately testing these areas, ransomware simulations go beyond surface-level vulnerability assessments. They replicate the tactics, techniques, and procedures (TTPs) used by real attackers, allowing organizations to measure how well they can detect and respond under pressure.
How Does Strobes Security Help You with Ransomware Simulation?
Strobes Security empowers organizations to proactively defend against ransomware by delivering customized, controlled, and comprehensive ransomware simulation services. Their approach goes far beyond generic testing—it mirrors the real-world tactics used by today’s most advanced ransomware groups, all within a safe and business-friendly framework.
Here’s how Strobes Security supports you through the entire ransomware simulation journey:
1. Tailored Simulation Design
Strobes Security customizes each ransomware simulation based on the organization’s architecture, industry threats, and regulatory landscape. Whether it’s a financial institution worried about compliance risks or a healthcare provider dealing with patient data protection, the simulation is adapted to suit the unique environment.
2. Multi-Vector Attack Emulation
Strobes doesn’t restrict simulations to one method of attack. They simulate a range of vectors, including phishing emails, exploit kits, privilege escalation chains, and lateral movement, to provide a full-spectrum assessment of how ransomware could penetrate and propagate within the network.
3. Team Collaboration and Feedback Loops
Real-time collaboration with Blue Teams ensures that the exercise is both educational and diagnostic. Immediate feedback and post-incident debriefs help teams understand gaps and learn from their responses during the simulation.
Also Read: How PTaaS Enhances Collaboration Between Security Teams and Developers
4. Actionable Remediation Guidance
Beyond identifying problems, Strobes provides strategic remediation plans tailored to organizational capabilities. These plans prioritize vulnerabilities by severity, exploitability, and business impact, helping security leaders implement quick wins and long-term fixes.
5. Compliance Reporting and Audit Readiness
For regulated industries, the ability to generate detailed documentation that aligns with compliance frameworks like HIPAA, PCI-DSS, and ISO/IEC 27001 is invaluable. Strobes’ reports include logs, screenshots, attack maps, and recommendations formatted to aid in audit preparation and executive briefings.
Strategic Benefits Beyond Technical Metrics
While ransomware simulations are technical in nature, their strategic value is immense. They elevate cybersecurity from a technical function to a board-level concern and empower organizations to:
- Quantify Risk in Business Terms: Instead of vague threats, simulations show the real-world business impact of ransomware—from lost revenue to halted operations.
- Strengthen Interdepartmental Coordination: Legal, HR, PR, and IT must work in concert during a ransomware event. Simulations help these departments rehearse and improve collaboration.
- Justify Cybersecurity Budgets: Demonstrating actual vulnerabilities and potential impact gives CISOs the evidence they need to request funding for tools, training, and staff.
- Build Customer and Partner Confidence: Organizations that conduct and publicize simulation testing signal their commitment to cybersecurity, increasing trust among stakeholders.
20 In-Depth FAQs About Ransomware Simulation
1. What is ransomware simulation?
A ransomware simulation is a controlled cybersecurity exercise that mimics the behaviors of real-world ransomware to evaluate an organization’s detection, response, and recovery capabilities.
2. Why simulate ransomware attacks?
To identify hidden vulnerabilities, validate the effectiveness of security controls, train response teams, and improve overall resilience before facing a real attack.
3. Does ransomware simulation involve real malware?
No. It uses benign tools and scripts that simulate ransomware behavior without causing harm or encrypting actual data.
4. Who typically conducts these simulations?
Cybersecurity firms like Strobes Security with expertise in adversary emulation and safe, controlled attack techniques.
5. Is this service only for large enterprises?
No. Small and medium-sized businesses benefit significantly, especially since they’re increasingly targeted by ransomware gangs.
6. How disruptive is a ransomware simulation?
When professionally managed, simulations are non-intrusive and safe, with minimal to no impact on daily operations.
7. How often should ransomware simulations be performed?
Quarterly or biannually, depending on your industry, compliance requirements, and risk exposure.
8. Can ransomware simulations help with compliance?
Yes. They support frameworks like NIST, ISO/IEC 27001, PCI-DSS, HIPAA, and others requiring ongoing security testing.
9. Which teams should be involved?
IT and cybersecurity teams, executive leadership, legal, communications, and compliance staff should all be engaged.
10. Does Strobes Security offer custom simulations?
Yes. They tailor simulations based on the client’s specific infrastructure, threats, and industry requirements.
11. What tools are used during simulations?
Custom scripts, ethical hacking tools, and administrative utilities like PsExec, all used safely and without damaging systems.
12. What deliverables come after a simulation?
A detailed report with logs, timelines, evidence, risk assessments, and prioritized remediation strategies.
13. Will the simulation test our backup systems?
Yes, especially if backup resilience is part of your scope. Simulations can verify whether backups are segmented and secure from ransomware.
14. Does the simulation include phishing attacks?
It can, particularly if phishing is identified as a common attack vector in your threat landscape.
15. Is ransomware simulation part of red teaming?
It can be integrated with red team operations or run as a standalone test focused exclusively on ransomware tactics.
16. What if our team performs poorly?
That’s part of the learning process. The purpose is to uncover weaknesses and improve response, not to assign blame.
17. Do we need insurance for this testing?
Not necessarily, but simulation results can support better terms in cyber insurance negotiations.
18. How long does the entire process take?
From planning to final reporting, it usually spans 1–3 weeks, depending on the complexity and scope.
19. What’s the ROI of ransomware simulation?
It prevents potentially multi-million-dollar breaches. The cost of simulation is far less than ransom payments, recovery, or reputation loss.
20. Why choose Strobes Security for this service?
Their tailored approach, industry experience, comprehensive reporting, and integration with your business context make them a leader in ransomware readiness solutions.
Related Reads:
- Continuous Threat Exposure Management (CTEM) – The Ultimate Guide for CISOs
- How Strobes Penetration Testing Supports Compliance Audits and Assessments
- Strobes Security Scanners: Modern Enterprise Static Application Security Testing | Strobes
- Services: Breach & Attack Simulation Services
- Compliance: SEBI Cybersecurity and Cyber Resilience Framework