For most, the term “offensive” evokes images of aggression and harm. But in cybersecurity, offensive security takes on a whole new meaning: proactive, strategic, and ultimately, robust security.
That’s the essence of offensive security, a practice that’s rapidly evolving from a niche expertise to a crucial component of any robust security posture. It’s not about launching cyberattacks – far from it. Instead, it’s about emulating the tactics of real-world attackers to expose your vulnerabilities before they can be exploited.
Offensive security flips the script. Instead of building walls, it probes defences to find and fix vulnerabilities before attackers exploit them. No matter if you’re a seasoned security pro or just dipping your toes into cyberspace, understanding offensive cybersecurity is no longer optional. It’s about staying ahead of the curve, anticipating attacker tactics, and proactively bolstering your security.
What is Offensive Security?
Offensive Security, often abbreviated as OffSec, is not about malicious hacking. It’s a proactive methodology and set of practices employed to strengthen an organization’s cybersecurity posture by actively seeking out and remediating vulnerabilities before malicious actors can exploit them. It’s about identifying weaknesses before the attacker does.
Benefits of Offensive Security
1. Reduced Risk of Cyber Attacks
The most immediate benefit of offensive security is the significant reduction in the risk of successful cyberattacks. By actively identifying and patching vulnerabilities, organizations essentially remove the footholds that attackers rely on to gain access to sensitive data and systems. This proactive approach is akin to preemptively plugging holes in your security, making it much harder for malicious actors to breach.
2. Enhanced Security Posture
Offensive security exercises go beyond simply patching vulnerabilities. They expose weaknesses in your overall security posture, including areas like incident response, access controls, and social engineering defences. By simulating real-world attack scenarios, you gain valuable insights into how your defences hold up under pressure, allowing you to address critical gaps and strengthen your overall security posture.
3. Improved Incident Response
Understanding how attackers operate is crucial for effective incident response. Offensive cybersecurity professionals learn the tactics, techniques, and procedures (TTPs) of various threat actors, equipping organizations to better anticipate and respond to attacks. This knowledge allows for faster detection, containment, and mitigation of security breaches, minimising damage and downtime.
4. Increased Security Awareness
Offensive security exercises not only improve technical defences but also raise awareness of cybersecurity risks within an organization. By engaging employees in simulated attacks and vulnerability demonstrations, you cultivate a culture of security, encouraging everyone to adopt safe practices and become vigilant against potential threats.
5. Cost Savings and Efficiency
While investing in offensive security may seem like an upfront cost, it pales in comparison to the potential financial losses caused by successful cyberattacks. Data breaches, system disruptions, and reputational damage can cost millions, not to mention the time and resources required for remediation. Offensive cybersecurity, by preventing such incidents, offers significant cost savings and improves operational efficiency in the long run.
6. Competitive Advantage
In today’s data-driven world, a strong security posture is a competitive advantage. Implementing OffSec demonstrates to clients, partners, and investors that you prioritize data protection and take proactive measures to safeguard your systems. This builds trust and confidence, potentially attracting new business opportunities and partnerships.
7. Regulatory Compliance and Risk Management
Many industries and regulations mandate specific cybersecurity controls and risk assessments. Offensive cybersecurity exercises help organizations comply with these requirements by providing evidence of their proactive approach to vulnerability management and risk mitigation. This can prevent hefty fines and reputational damage associated with non-compliance while demonstrating a commitment to responsible data security practices.
Offensive Security VS Defensive Security
| Feature | Offensive Security | Defensive Security |
| Goal | Proactively identify and exploit vulnerabilities to strengthen security. | Protect against and respond to cyberattacks. |
| Method | Penetration testing, vulnerability assessments, social engineering, exploit development. | Firewalls, intrusion detection/prevention systems, security monitoring, data encryption, incident response. |
| Tools | Kali Linux, Metasploit, Burp Suite, Nmap. | SIEM, IDS/IPS, DLP |
| Perspective | Attacker (simulates malicious actors). | Defender (bolsters organizational defenses) |
| Focus | Specific vulnerabilities, finding weaknesses in existing systems. | Broad range of threats, preventing attacks through layered security. |
| Initiation | Usually initiated by an organization or individual to test their own security or that of others. | Usually initiated in response to a perceived threat or to prevent an attack. |
| Timeline | Reactive, typically focused on specific vulnerabilities or attack simulations. | Proactive, ongoing effort to maintain security posture. |
| Scope | Often focused on testing one particular system or network. | Concerned with protecting the entire organization’s infrastructure and data. |
| Roles | Penetration testers, ethical hackers, security consultants. | Security analysts, incident responders, system administrators, security architects. |
| Skills | Deep understanding of vulnerabilities, exploit development, technical hacking skills, creative problem-solving. | Risk assessment, security controls implementation, incident response procedures, threat intelligence, security awareness training. |
Key Concepts of Offensive Security:
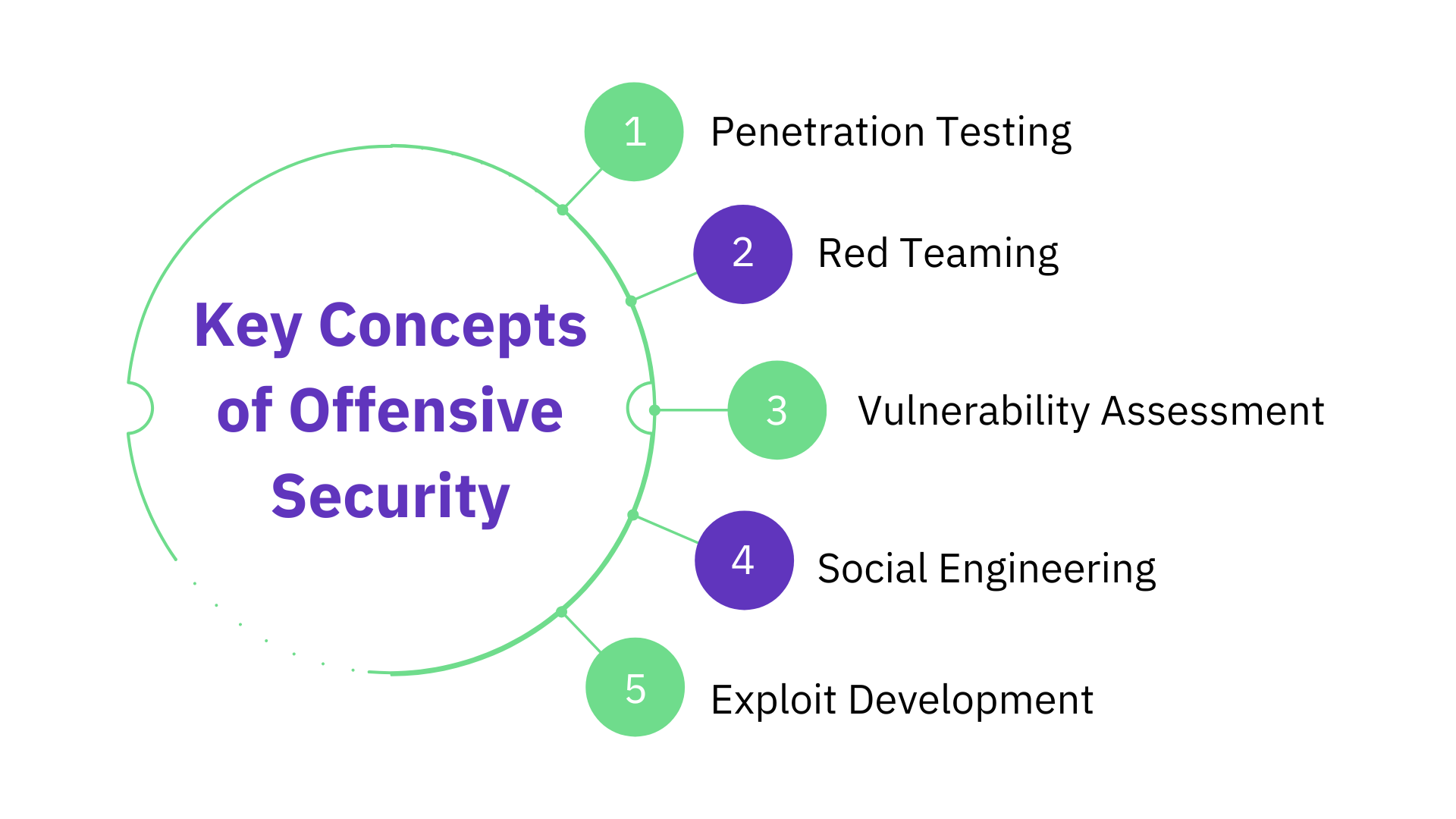
1. Penetration Testing
Penetration testing involves simulating real-world attacks on a controlled environment to identify vulnerabilities in networks, systems, and applications. It mimics the methods and motivations of malicious actors to uncover weaknesses before they can be exploited by adversaries.
Process
- Information Gathering: Initial research on the target system, including network topology, software versions, and user information.
- Vulnerability Scanning: Automated tools identify potential weaknesses in hardware, software, and configurations.
- Exploitation: Manual attempts to exploit discovered vulnerabilities using known exploits or custom-made tools.
- Privilege Escalation: Gaining higher access levels within the system to expand control and reach sensitive data.
- Post-Exploitation: Maintain access, cover tracks, and simulate attacker’s objectives (data exfiltration, system disruption).
- Reporting & Remediation: Documenting findings, prioritizing vulnerabilities, and recommending mitigation strategies.
2. Red Teaming
Red teaming takes penetration testing a step further. It involves a team of ethical hackers mimicking the tactics, techniques, and procedures (TTPs) of specific threat actors or scenarios to thoroughly test an organization’s security posture. This goes beyond penetration testing by:
- Simulating real-world attacker tactics: Including social engineering, physical attacks, and supply chain attacks.
- Testing the entire security ecosystem: Including personnel, procedures, and technology.
- Providing actionable recommendations: For improving security posture and preventing future attacks.
3. Vulnerability Assessment
Vulnerability assessment is a systematic process of identifying, classifying, and prioritizing vulnerabilities in systems and networks. It helps organizations understand their security posture and focus remediation efforts on the most critical weaknesses.
Process
- Scanning & Detection: Automated tools scan for known vulnerabilities in software, configurations, and network devices.
- Manual Verification: Security professionals manually assess the detected vulnerabilities to confirm their validity and potential impact.
- Risk Prioritization: Vulnerabilities are ranked based on their severity, exploitability, and potential impact on the organization.
- Reporting & Remediation: A report is generated detailing the identified vulnerabilities and recommendations for mitigation.
4. Social Engineering
Social engineering exploits human vulnerabilities, such as trust, curiosity, or fear, to gain access to systems or information. Attackers use various techniques, like phishing emails, pretexting calls, and baiting, to trick users into revealing sensitive information or performing actions that compromise security.
Common Techniques
- Phishing: Emails or text messages disguised as legitimate sources to trick users into clicking malicious links or revealing personal information.
- Pretexting: Creating a false persona or scenario to gain someone’s trust and elicit confidential information.
- Baiting: Offering attractive incentives, like free software or prizes, to lure users into downloading malware or clicking malicious links.
5. Exploit Development
Exploit development involves creating software tools or code that take advantage of vulnerabilities in software or hardware. These tools allow attackers to gain unauthorized access, steal data, or disrupt operations.
Process
- Vulnerability analysis: Understanding the nature and details of the vulnerability to identify potential attack vectors.
- Proof-of-concept development: Creating a simple script or tool to demonstrate the exploitability of the vulnerability.
- Weaponization: Refining the exploit for wider use, making it more reliable, stealthy, and potentially automated.
- Testing and refinement: Continuously testing and improving the exploit to evade detection and increase its effectiveness.
These key concepts of offensive cybersecurity play a crucial role in strengthening an organization’s defense against cyberattacks. By proactively identifying and addressing vulnerabilities, organizations can significantly improve their security posture and mitigate the risks of cyber threats.
Popular Tools and Resources
1. Kali Linux: This open-source operating system is the go-to platform for many ethical hackers. It comes pre-loaded with a vast collection of security tools, including:
- Nmap: Network mapper to scan for open ports and services.
- Metasploit: Extensive framework for vulnerability exploitation and penetration testing.
- Burp Suite: Web application security testing suite for identifying vulnerabilities in web applications.
- Wireshark: Network protocol analyzer for monitoring and analyzing network traffic.
- John the Ripper: Password cracker for testing password strength and cracking weak credentials.
2. ExploitDB: This online repository contains exploits for various vulnerabilities in software and hardware. Ethical hackers use ExploitDB to understand how vulnerabilities are exploited, develop countermeasures, and test their own systems for similar weaknesses.
3. OWASP Top 10: The list, compiled by the Open Web Application Security Project (OWASP) Top 10, identifies the ten most critical web application security risks. Offensive security professionals use this list to prioritize vulnerabilities and focus their testing efforts.
4. Social Engineering Toolkit (SET): This framework automates various social engineering techniques, such as phishing emails and website cloning. Ethical hackers use SET to test an organization’s awareness and susceptibility to social engineering attacks.
5. Bug bounty platforms: Platforms like HackerOne and Bugcrowd connect organizations with ethical hackers who can discover and report vulnerabilities. This allows organizations to crowdsource their security testing and benefit from the expertise of a large pool of security researchers.
Bonus Resources:
Ethical Considerations
Responsible and ethical conduct is paramount in offensive security. Here are some key considerations:
- Legal and regulatory compliance: Always operate within the boundaries of the law and relevant regulations.
- Authorization: Only conduct OffSec activities on authorized targets with proper consent.
- Transparency: Clearly communicate the purpose and scope of your activities to stakeholders.
- Vulnerability disclosure: Responsible disclosure of vulnerabilities is crucial to avoid harming the target and ensure proper patching.
- Data privacy: Respect user data privacy and avoid collecting or using unauthorized personal information.
Remember, offensive security should be used solely for ethical purposes, to identify and address vulnerabilities, and to strengthen defences. By adhering to ethical principles and best practices, offensive security professionals can contribute significantly to a safer digital ecosystem.
By combining the power of tools and ethical practices, offensive security professionals can become valuable assets in protecting our digital world from malicious actors.
Take the next step in securing your organization—explore how OffSec can proactively safeguard your systems. Book a free demo with Strobes today and stay ahead of cyber threats!
Related Reads:
- Blog: Decoding the Pentesting Process: A Step-by-Step Guide
- Blog: Penetration Testing Explained: Safeguarding your Online Presence
- Blog: Penetration Testing Frequency: How Often Is Enough?
- Blog: How PTaaS Supports Shift-Left Security Practices?
- Blog: Cloud Pentesting 101: What to Expect from a Cloud Penetration Test
- Solution: Web Application Pentesting
- Solution: Solution: Pentesting as a Service