If you’re relying on vulnerability scanning alone to keep your organization safe, it’s time to ask a critical question: Is it enough?
Many organizations scan their systems regularly, get lists of vulnerabilities, and patch what they can. But with the increasing complexity of cyberattacks, can you confidently say that this approach truly secures your business?
Vulnerability scanning may seem like a solid security measure, but it only scratches the surface. Sure, it identifies known weaknesses, but does it help you understand which vulnerabilities actually pose the greatest risk?
Does it tell you what attackers are most likely to target or how much damage a breach could cause?
If your cybersecurity strategy ends at vulnerability scanning, you’re leaving your organization exposed. This blog reveals why vulnerability scanning is no longer enough and what you should do instead. Let’s break it down.
What is Vulnerability Scanning?
Vulnerability scanning is a systematic process used to identify and evaluate security weaknesses in an organization’s systems, networks, and applications. The primary objective is to detect vulnerabilities that could be exploited by attackers, enabling organizations to take proactive measures to mitigate risks.
Vulnerability scanning involves the following key steps:
- Automated Scanning: Specialized tools (vulnerability scanners) perform automated scans of the systems and networks. These tools use databases of known vulnerabilities, often based on Common Vulnerabilities and Exposures (CVEs), to assess the security posture of the environment.
- Identification of Weaknesses: The scanning tools identify potential vulnerabilities, such as unpatched software, misconfigurations, outdated protocols, and insecure services. This results in a pentesting report detailing the discovered vulnerabilities, their severity, and potential remediation steps.
- Reporting: After the scan, detailed reports are generated, which outline the vulnerabilities found, categorized by risk levels. This allows security teams to prioritize which vulnerabilities need immediate attention.
- Remediation Guidance: Many scanning tools provide suggestions for remediating identified vulnerabilities, which may include applying patches, reconfiguring settings, or implementing compensating controls.
| What Vulnerability Scanning is | What Vulnerability Scanning is Not |
| An automated process to identify security weaknesses | A comprehensive security solution |
| A means to detect known vulnerabilities based on databases | A substitute for thorough penetration testing |
| A tool that generates reports outlining vulnerabilities and risks | A one-time assessment or check-up |
| A component of a broader vulnerability management strategy | An all-encompassing fix for security issues |
| A method to provide an overview of system security status | A guarantee against all cyber threats |
| A practice that helps prioritize remediation efforts based on risk | A replacement for security policies and procedures |
| A way to improve security posture over time with regular scans | An infallible process that catches every vulnerability |
| A tool used by security teams to maintain compliance standards | A means to eliminate the need for manual security reviews |
| A way to identify misconfigurations and outdated software | A final step in the security process; it must be part of ongoing efforts |
| A foundational step in understanding an organization’s risk profile | A complete assessment of the organization’s overall security strategy |
Understanding the Limitations of Vulnerability Scanning

While vulnerability scanning is an essential part of a security strategy, it has significant limitations that organizations must acknowledge. Here are some key drawbacks:
1. Static Snapshot
Vulnerability scanning gives a one-time view of your security at a specific moment. This means it only reflects the state of your systems when the scan was conducted. If your organization doesn’t scan frequently, new vulnerabilities may arise between scans, leaving you unprotected against risks that were not identified in the last assessment.
For example, if a major software update introduces new weaknesses, and your last scan was weeks ago, you could be at risk without knowing it.
2. False Positives and False Negatives
- False Positives: These happen when the scanner flags something that isn’t a real threat. For instance, it might indicate that a system is vulnerable when it’s not. This can lead to wasted time and resources, as teams end up fixing things that aren’t even real threats., potentially ignoring more serious vulnerabilities that need attention.
- False Negatives: These occur when the scanner misses an actual vulnerability. This could be due to limitations in the scanner’s programming or how it is set up. If a vulnerability is overlooked, the organization may believe that their systems are secure when they are not, leaving them open to attacks.
3. Lack of Contextual Awareness
Vulnerability scanners identify weaknesses but often don’t explain why these weaknesses matter to your specific organization.
For example, if a scanner flags a vulnerability in a non-essential system, it might not be a priority to fix. However, if it overlooks a vulnerability in a critical system, that can lead to significant risks.
Without understanding the context, security teams might waste time on low-risk vulnerabilities while missing those that could cause serious harm.
4. Exploitability Assessment
Vulnerability scanners generally do not evaluate how easy it is to exploit a vulnerability. Just because a scanner finds a weakness doesn’t mean it can be easily attacked. Scanners often lack current information about real-world attacks, making it hard for organizations to identify which vulnerabilities are truly dangerous. This means organizations might focus on fixing vulnerabilities that are less likely to be exploited while ignoring those that pose a higher risk.
5. Volume of Results
Organizations often receive a large number of vulnerability reports from scans, sometimes in the hundreds or thousands. This overwhelming amount of information can lead to “analysis paralysis,” where security teams struggle to prioritize which vulnerabilities to address first. Without clear guidance, critical issues might remain unaddressed while teams chase down less important ones.
6. Limited Remediation Guidance
Vulnerability scanners might give you suggestions for fixing issues, but they’re often pretty generic. They might not consider your organization’s specific environment or circumstances. This can make it challenging for teams to implement fixes effectively, as they may not fully understand the implications of the suggested changes on their systems.
7. Neglect of Non-Technical Factors
Vulnerability scanning primarily focuses on technical flaws and often ignores other important aspects. It doesn’t consider operational processes, human errors, or compliance requirements. Good cybersecurity involves more than just technology; it also includes policies and procedures that guide how security is managed across the organization. Without this holistic view, some risks may go unaddressed.
8. Resource-Intensive Process
Regular vulnerability scanning requires a significant investment of time and resources. Organizations must dedicate staff, technology, and effort to run scans, analyze results, and take corrective action. For smaller organizations, this can be particularly challenging, as they may have limited personnel and budgets to manage these demands effectively.
Why Vulnerability Scanning Can’t Keep Up with an Expanding Attack Surface?
As organizations grow and adopt more advanced technologies, their attack surface expands. With cloud services, IoT devices, remote work, and increasingly interconnected systems, the number of potential entry points for attackers multiplies. This rapid growth makes it increasingly difficult for vulnerability scanning to provide comprehensive protection. Here’s why:
- New Technologies, New Gaps: As organizations introduce new cloud applications, devices, and digital platforms, each addition creates a fresh set of vulnerabilities. Vulnerability scanning tools are often limited to identifying known weaknesses, and may not cover newer technologies or emerging attack vectors effectively. This leaves room for unseen risks that aren’t accounted for in traditional scans.
- Constantly Shifting Environment: Modern environments are highly dynamic. With frequent updates, patches, and changes to system configurations, vulnerabilities can emerge and evolve quickly. Vulnerability scanning offers a static snapshot at a particular moment in time, but it doesn’t adapt to these constant changes. By the time your next scan happens, new risks may have already taken root.
- Overlooked Assets: As the attack surface grows, vulnerability scanning often struggles to capture every asset. Unmanaged devices, shadow IT, or remote endpoints may fly under the radar, meaning you could miss significant vulnerabilities. These blind spots leave your systems open to attacks from overlooked entry points.
- Increased Complexity: The more complex your infrastructure becomes, the harder it is for vulnerability scanners to prioritize real threats. With the rising number of connected devices and services, the output from vulnerability scans grows, flooding your teams with data that’s difficult to sift through. When everything looks critical, it’s easy for truly high-risk vulnerabilities to get buried in the noise.
Simply put, as your attack surface expands, vulnerability scanning on its own can’t keep pace with the changing threats’ dynamics.
The Transition to Vulnerability Management
To address these limitations, organizations have turned to vulnerability management. This approach goes beyond just scanning; it involves a systematic process of identifying, evaluating, treating, and reporting on vulnerabilities in systems and software.
Comprehensive Assessment
Vulnerability management encompasses not only vulnerability scanning but also ongoing assessments of vulnerabilities. It integrates various data sources to provide a more comprehensive view of your security posture. This includes analyzing past incidents, threat intelligence, and even insights from previous scans.
Regular Updates and Patching
While vulnerability scanning might identify vulnerabilities, vulnerability management implements processes for prioritizing and remediating those vulnerabilities through timely patching and configuration changes. This proactive approach is crucial, but it still has its own challenges.
Prioritization Challenges
One of the most significant issues with traditional vulnerability management is the overwhelming number of vulnerabilities. Security teams often find themselves inundated with lists of vulnerabilities without clear guidance on which to address first. This can lead to critical vulnerabilities being overlooked while minor ones are prioritized, resulting in a false sense of security.
Why Vulnerability Management Falls Short
While vulnerability management is an improvement over simple scanning, it still falls short in several key areas:
Resource Intensive
Vulnerability management can be resource-intensive, requiring dedicated teams to constantly monitor, assess, and remediate vulnerabilities. This often leads to burnout and inefficiency, particularly in smaller organizations with limited security staff.
Fragmented Approach
Many organizations adopt a siloed approach to vulnerability management, treating vulnerabilities as isolated issues rather than part of a broader risk landscape. This can result in a lack of communication and coordination between security teams and other business units, ultimately weakening overall security efforts.
Limited Focus on Real Risk
Despite improvements, traditional vulnerability management still often focuses on technical fixes without fully considering the broader business implications of vulnerabilities. This can lead to a reactive approach that does not align with the organization’s strategic goals.
What’s the Solution?
To address the limitations of both vulnerability scanning and traditional vulnerability management, organizations should adopt Risk-Based Vulnerability Management (RBVM). This method emphasizes a risk-focused strategy that prioritizes vulnerabilities based on their potential impact and the likelihood of exploitation.
As per Gartner – Organizations that adopt risk-based vulnerability management experience up to 80% fewer breaches.
By shifting the focus from simply identifying vulnerabilities to understanding their context within the organization, RBVM offers a more effective approach to cybersecurity.
Contextual Risk Assessment
RBVM involves assessing vulnerabilities within the specific context of an organization’s environment. This means taking into account several critical factors:
- Asset Criticality: Not all assets hold the same value to an organization. Some may be essential for operations or contain sensitive data, while others might be less critical. RBVM helps identify which assets require more attention and protection.
- Exposure: Understanding how exposed an asset is to potential threats is crucial. Assets that are more accessible to attackers (e.g., those exposed to the internet) should be prioritized over those that are well-protected.
- Potential Business Impact: Each vulnerability carries a different risk based on its potential impact on the organization. RBVM evaluates how the exploitation of a vulnerability could affect business operations, reputation, and compliance.
Image: Strobes RBVM
By incorporating these factors, RBVM enables organizations to prioritize vulnerabilities that are not only present but also pose a significant threat, ensuring that resources are directed where they are needed most.
Dynamic Prioritization
One of the key features of RBVM is its dynamic prioritization of vulnerabilities. Unlike traditional methods that rely on periodic scans, RBVM continuously assesses vulnerabilities based on real-time threat intelligence. This dynamic approach allows organizations to:
- Focus on Active Threats: By monitoring emerging threats and vulnerabilities that are currently being exploited in the wild, organizations can concentrate their efforts on issues that pose an immediate risk.
- Adapt Quickly: As the threat landscape changes, so do the vulnerabilities that require attention. RBVM enables organizations to adjust their priorities swiftly, ensuring they are always addressing the most pressing security challenges.
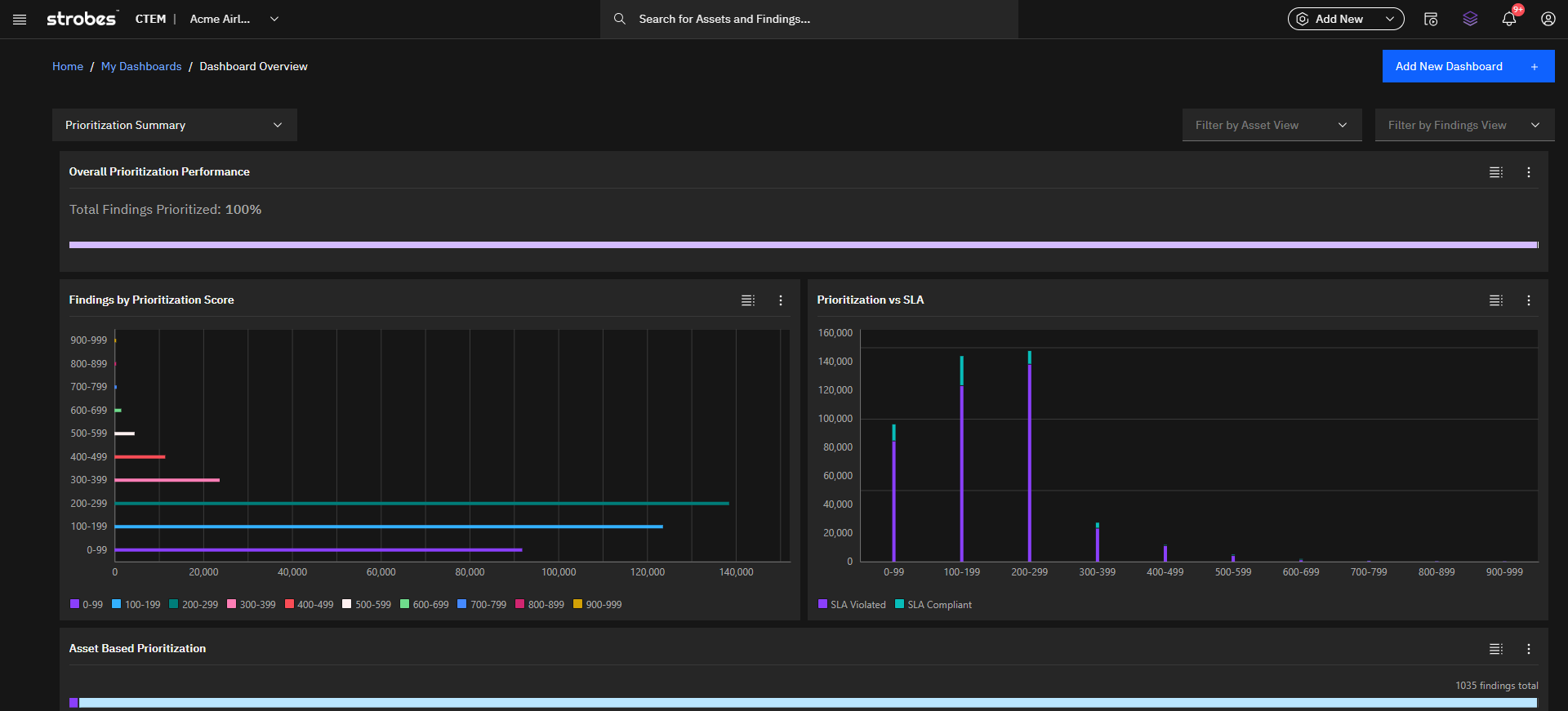
This proactive stance significantly enhances an organization’s ability to manage risk effectively.
Integration with Business Objectives
RBVM aligns vulnerability management with the overall business objectives of an organization. This alignment ensures that security efforts support the organization’s goals rather than operate in isolation. Key aspects of this integration include:
- Understanding Business Impact: By assessing how vulnerabilities could impact business objectives, security teams can prioritize issues that threaten critical operations, compliance, or reputation.
- Informed Resource Allocation: Security teams can make better decisions about where to allocate resources based on the potential impact of vulnerabilities. This strategic approach ensures that security measures are not just reactive but also aligned with business needs.
By integrating RBVM with business objectives, organizations can enhance their overall security posture while ensuring that their cybersecurity efforts contribute to organizational success.

Real-World Application: RBVM in Action
Consider a financial institution that has implemented a traditional vulnerability management program. Despite regular vulnerability scanning and patching, they experienced a significant data breach due to a vulnerability that had been identified but not prioritized effectively.
Upon switching to an RBVM approach, the institution began to assess vulnerabilities in the context of their critical assets such as customer data, payment systems, and regulatory requirements. By utilizing real-time threat intelligence and focusing on vulnerabilities that were actively being targeted, they were able to remediate high-risk vulnerabilities swiftly.
As a result, the institution not only improved its security posture but also reduced incident response times, ultimately enhancing its overall resilience against future attacks.
Final Words
Relying solely on vulnerability scanning is no longer an option. While traditional vulnerability management has its merits, it falls short in tackling the complexities of modern cyber risks.
Risk-Based Vulnerability Management (RBVM) is the solution. By focusing on vulnerabilities through the lens of contextual risk and aligning security efforts with business objectives, organizations can significantly strengthen their security posture and effectively address the most critical threats.
It’s time to move past outdated methods and adopt a risk-based strategy. Invest in RBVM to protect your vital assets, streamline your resources, and ensure your organization is resilient against emerging threats.
Don’t let outdated methods put your organization at risk. Join the leaders who are adopting RBVM and see the difference it can make. Book your demo now!
Related Reads
- CVSS Score: A Comprehensive Guide to Vulnerability Scoring
- Top 15 Vulnerability Management Tools for Your Business
- Continuous Threat Exposure Management (CTEM) – The Ultimate Guide for CISOs
- The Ultimate Guide to Vulnerability Assessment
- CISO’s Solution for Better Vulnerability Management
- Why the Demand for Vulnerability Management Platforms Is Rising?
- Solving the Biggest Vulnerability Management Challenges with Strobes
- Solution: Risk Based Vulnerability Management







