A critical zero-day vulnerability in Oracle E-Business Suite (EBS) was exploited by the Cl0p ransomware group in mid-2025. The flaw, later tracked as CVE-2025-61882, allowed remote code execution without authentication, giving attackers complete control over affected systems.
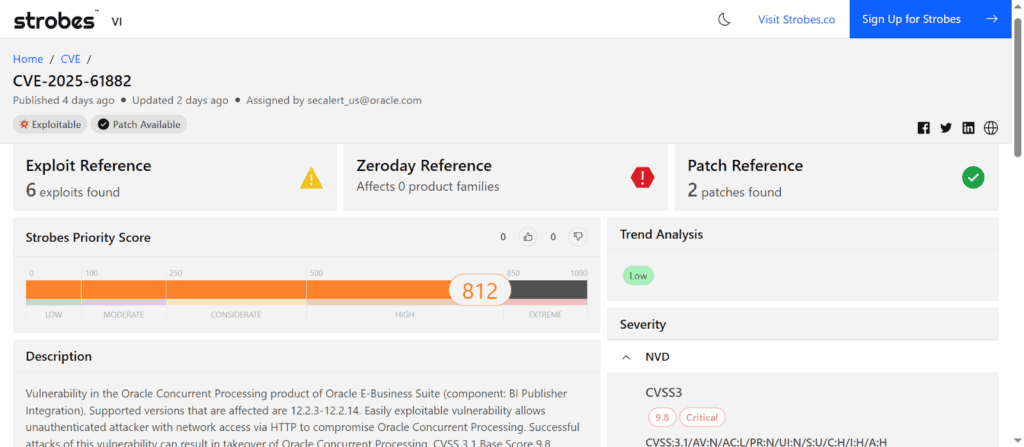
On the Strobes Vulnerability Intelligence (VI) platform, this vulnerability carries a Priority Score of 812, placing it firmly in the critical and actively exploited category that demands immediate remediation.
Cl0p quietly used this weakness for weeks to access corporate ERP servers, steal sensitive business data, and send extortion emails demanding massive ransom payments. Oracle confirmed the issue and released an emergency patch on October 4, 2025, urging every customer to update immediately.
The campaign revealed a hard truth that organized cybercriminal groups are now exploiting enterprise-grade software flaws faster than most organizations can detect or respond.
How CVE-2025-61882 Gave Attackers Full Control of EBS
The root of CVE-2025-61882 lies in Oracle EBS’s BI Publisher Integration module, exposed via its Concurrent Processing component. Because that interface accepts XML and HTTP requests, attackers could trigger malicious workflows without any valid credentials.
Successful attacks chain multiple techniques:
- SSRF (Server-Side Request Forgery): The attacker tricks the EBS server into fetching remote resources by manipulating return_url or related parameters in XML requests. Because EBS trusts its own outbound fetches, this gives the attacker control over what the server loads.
- CRLF Injection / Header Smuggling: The exploit includes control over line breaks and headers in those requests, allowing the attacker to insert headers or reframe requests to bypass authentication boundaries or internal filters.
- Auth Bypass / Internal Access Abuse: Once SSRF and header control are chained, the attacker can reach otherwise internal endpoints (e.g., on private ports) that are not meant to be public.
- Unsafe XSLT Processing: Using BI Publisher’s XSLT engine, the attacker delivers a malicious stylesheet from their server. That stylesheet then invokes extension functions (e.g., Java’s scripting APIs) to execute arbitrary system commands, often invoking Runtime.exec() under the EBS JVM.
- Privilege Escalation: The initial execution context is limited (e.g., as the Oracle application user). Attackers then chain additional exploits (often known but not patched vulnerabilities or privilege gaps) to gain root or full administrative control over the host.
Oracle confirms all versions from 12.2.3 through 12.2.14 are impacted. A prerequisite for applying the patch is that the October 2023 CPU must already be installed. Oracle assigned this flaw a CVSS score of 9.8 and pushed a rare out-of-band fix to contain ongoing exploitation.
Because EBS hosts mission-critical systems (finance, HR, procurement, supply chain), a compromise here means attackers bypass your traditional perimeter controls using your own ERP stack.
How Cl0p Carried Out the Attack
Cl0p’s playbook was surgical and stealthy:
- They scanned the internet for Oracle EBS instances that were reachable externally and running vulnerable versions. Since the exploit requires no login, the first compromise could be done over HTTP directly.
- Once inside, the exploit chain described above is triggered automatically. The attacker-controlled server hosts the malicious XSLT file. The EBS server fetches it via SSRF, processes it via the XSLT engine, and spawns a shell. That gives the attacker command execution inside the JVM or the OS.
- Attackers establish persistence via web shells, cron jobs, or account creation to maintain control even if one vector is removed. They also move laterally to adjacent systems.
- The data theft phase is stealthy. Cl0p exfiltrates sensitive records: payroll, vendor contracts, internal config files, financial ledgers, anything stored in EBS or its connected artifacts.
- Weeks later, Cl0p transitions to extortion. They send emails to C-suite or IT leadership, containing screenshots from the breached EBS, directory listings, and small sample files. The ransom demands are in the tens of millions of dollars. Some emails come from legitimate, compromised external accounts to bypass spam filters.
- In cases where an organization reacts, Cl0p sometimes falls back to secondary access paths — for instance, using local EBS login endpoints (bypassing SSO) that don’t enforce MFA, creating a survival route.
By the time Oracle published its advisory, Cl0p’s operation had already moved far beyond initial compromise, and many victims had already lost significant data.
Timeline of the Attack
To understand how the incident unfolded, here is a timeline of key events in the CVE-2025-61882 campaign and response:
- Early August 2025: Cl0p began actively exploiting the Oracle EBS zero-day in the wild. The earliest known breach via CVE-2025-61882 occurred around August 9, 2025, suggesting that Cl0p obtained or developed the exploit before this date. Throughout August, they quietly gained access to vulnerable EBS servers and harvested sensitive data without detection.
- Late September 2025: After weeks of data theft, affected organizations started receiving Cl0p’s extortion emails. Around September 29, 2025, multiple companies were contacted by the attackers claiming that their Oracle EBS data had been stolen. These emails marked the first obvious sign of compromise for many victims and kicked off incident response efforts at those organizations.
- October 2, 2025: News of the ongoing Oracle EBS breach campaign broke publicly. Security researchers (including teams at Mandiant/Google and CrowdStrike) and media outlets exposed Cl0p’s activities, warning that a widespread exploitation of Oracle EBS was underway. This public disclosure put pressure on Oracle to respond and alerted many companies that hadn’t yet been contacted by Cl0p to check their systems.
- October 4, 2025: Oracle released an emergency patch and security alert for CVE-2025-61882. This out-of-band fix was made available via Oracle Support, outside the usual quarterly Critical Patch Update schedule. Oracle’s advisory confirmed the vulnerability details (CVSS 9.8, pre-auth RCE) and included Indicators of Compromise (IoCs) – such as attacker IP addresses, filenames, and example malicious commands – gleaned from observed attacks. Oracle urged customers to apply the patch immediately and to review logs for any signs of intrusion dating back to at least August.
- October 5–6, 2025: Global cybersecurity agencies jumped into action. In the U.S., CISA added CVE-2025-61882 to its Known Exploited Vulnerabilities catalog by October 6, and in the U.K., NCSC issued an alert about active exploitation. Other national CERTs (e.g., in Singapore, Canada) also released advisories highlighting the threat. These alerts amplified the urgency for organizations to patch or isolate vulnerable systems without delay.
- October 7–9, 2025: As Oracle customers scrambled to apply the fix, exploit code for CVE-2025-61882 surfaced in public forums. A proof-of-concept script that had been leaked on a Telegram channel (apparently by a rival hacker group) became widely available. This led to a surge in copycat attacks – other threat actors (beyond Cl0p) began scanning for and targeting any unpatched Oracle EBS instances. Security researchers from WatchTowr Labs and others analyzed the leaked scripts and confirmed they could reliably compromise unpatched systems. Organizations that had not yet applied the update now faced an even higher risk of opportunistic attacks, essentially turning the zero-day into a “1-day exploit” free-for-all.
Impact on Organizations
The fallout from this campaign was extensive, affecting Oracle EBS customers across many sectors. Several key impact areas emerged:
1. Sensitive Data Exposure
Cl0p gained access to sensitive ERP data such as payroll files, vendor contracts, and financial transactions. Because the group focused on exfiltration rather than encryption, many victims were unaware of the breach until extortion emails arrived weeks later.
2. Operational Disruption
To contain the threat, many organizations shut down their ERP systems for forensic review and patching. This disrupted payroll processing, order management, and financial operations for several days.
3. Regulatory and Financial Fallout
Breached data triggered potential non-compliance under regulations like GDPR and CCPA, exposing companies to legal and financial risk. Even firms that refused ransom demands faced reputational damage.
4. Delayed Patch Adoption
Some enterprises couldn’t apply Oracle’s emergency fix immediately because they lacked the required October 2023 baseline update. This dependency created prolonged exposure windows.
5. Copycat Exploitation
Following public disclosure, exploit scripts appeared online, prompting mass scanning by opportunistic attackers targeting unpatched Oracle EBS environments.
Oracle’s Response and Mitigation Steps
Oracle responded quickly once exploitation was confirmed.
1. Emergency Patch
On October 4, Oracle released the patch for CVE-2025-61882, addressing all supported versions. The company labeled it a top-priority fix and warned that failure to patch could lead to full compromise.
2. Security Guidance and IOCs
Oracle’s advisory provided technical details, attack indicators, and instructions for log review. Customers were urged to check for suspicious activity going back to August 2025.
3. Coordination with Authorities
Agencies like CISA and NCSC flagged the vulnerability as actively exploited. This elevated its urgency for both government and private-sector organizations.
4. Continued Monitoring
Oracle continues to monitor post-patch activity and advises customers to
- Restrict external access to EBS
- Enforce MFA for all logins, including local accounts
- Conduct post-patch scans and review outbound network logs
Broader Implications for Enterprise Security
This incident highlights deeper challenges that go beyond one Oracle bug.
1. Zero-Days Are Now a Criminal Weapon
Cl0p showed that ransomware groups no longer wait for leaked exploits. They create or buy their own. Enterprise defenders must assume unknown flaws exist in core software and plan for containment, not just prevention.
2. ERP Systems Are Prime Targets
ERP platforms store the operational heart of a business. The Oracle breach proved that neglecting its security can expose an organization’s most sensitive functions.
3. Patching Speed Defines Resilience
Oracle reacted quickly, but many companies could not. Complex dependencies delayed fixes, extending exposure. Enterprises need faster patch testing and deployment pipelines for critical systems.
4. Data Extortion Is the New Ransomware
Modern attackers do not need to encrypt files. They simply steal and threaten to publish. Data classification, encryption, and egress monitoring must become top priorities.
5. Internal Visibility Is Critical
Traditional endpoint monitoring is not enough. Continuous visibility into ERP and business platforms, such as access logs, queries, and data flows, is essential to catch intrusions early.
6. Exposure Management Needs to Be Continuous
The Oracle zero-day showed how dangerous blind spots can be. Many organizations did not know their EBS instances were reachable from the internet until after the breach. Continuous exposure management, which involves discovering, assessing, and reducing externally accessible assets, would have flagged those weak points long before Cl0p found them. It is not a one-time audit. It is an ongoing process that keeps track of what is exposed and how critical it is.
7. Vendor and Customer Responsibility Must Tighten
Both vendors and users share accountability. Vendors must test and disclose faster. Customers must apply patches on time and minimize public exposure.
8. Early Collaboration Makes a Difference
Oracle’s coordination with partners and agencies helped contain the damage. Future incidents demand the same level of transparency and speed across the ecosystem.
Practical Lessons and Takeaways
For CISOs, IT leaders, and security teams, the Oracle EBS zero-day leaves several clear lessons.
- Patch immediately when an emergency update is released. Treat it as a live-fire incident, not routine maintenance.
- Assume breach and investigate logs going back months. Hunt for signs of data exfiltration, new accounts, or unexpected network connections.
- Lockdown exposure. Keep ERP systems off the open internet or behind a secure VPN.
- Enforce MFA on every login path, including local and administrative accounts.
- Monitor continuously. Watch for abnormal queries, exports, or large outbound data transfers.
- Incorporate continuous exposure management into daily operations. Regularly map internet-facing assets, identify risky configurations, and track changes over time. This helps eliminate blind spots and reduces the chance of critical systems being unintentionally exposed.
- Prepare for extortion scenarios. Update your incident response playbook to handle data-theft-based ransom cases.
Final Thoughts
The Oracle zero-day exploited by Cl0p is a reminder that even the most established enterprise platforms can become attack vectors overnight. The difference between damage and resilience often comes down to how quickly organizations detect, patch, and verify their systems.
For most companies, this incident should mark a turning point. ERP security is no longer a maintenance task. It is a critical part of exposure management and business continuity.
The Cl0p campaign made it clear that data-driven extortion is here to stay and that continuous visibility, disciplined patching, and proactive exposure management are now essential to staying ahead of attackers.